 Blog's Page
Blog's Page

Introduction
In The Digital Age, Cybersecurity Threats Have Evolved, Becoming More Sophisticated And Harder To Detect. Among These Threats, SocGholish Stands Out As A Notable Example Of A Socially Engineered malware Campaign. This Essay Explores The Origins, Mechanisms, Impact, And Mitigation Strategies Associated With SocGholish, Providing A Detailed Understanding Of Its Operation And The Broader Implications For Cybersecurity.
SocGholish Is A JavaScript-based Downloader Disseminated Via Malicious Or Compromised Websites. It Deceives Users Into Downloading The Malware By Presenting Fake Software Updates, Such As Bogus Browser Or Flash Updates.
The Malware Employs Various Methods For Traffic Redirection And Payload Delivery. It Is Known To Utilize Cobalt Strike And Is Designed To Steal Information From The Victim’s System. Furthermore, SocGholish Can Facilitate Further Exploitation By Deploying Tools Like The NetSupport Remote Access Tool, Async Remote Access Tool, And, In Some Cases, Ransomware.
assay[.]porchlightcommunity[.]org
eeatgoodx[.]com
event[.]coachgreb[.]com
funcallback[.]com
gitbrancher[.]com
libertariancounterpoint[.]com
pluralism[.]themancav[.]com
usersync[.]tiqcdn[.]net
whitedrill[.]org
81[.]94[.]150[.]21
83[.]69[.]236[.]128
88[.]119[.]169[.]108
91[.]121[.]240[.]104
185[.]158[.]251[.]240
193[.]233[.]140[.]136
Origins Of SocGholish
SocGholish, A Portmanteau Of "Social" And "Gholish" (a Play On "ghoul"), First Emerged Around 2018. It Is Primarily A Type Of Social Engineering Attack, Relying On The Manipulation Of Human Behavior Rather Than Exploiting Software Vulnerabilities. The Threat Actors Behind SocGholish Often Employ A Technique Known As "drive-by Downloads," Where Unsuspecting Users Are Tricked Into Downloading And Executing Malicious Software.
The Creators Of SocGholish Are Typically Part Of Sophisticated Cybercriminal Organizations. These Groups Meticulously Craft Their Campaigns To Target Specific Industries Or User Demographics, Increasing The Likelihood Of A Successful Attack. By Leveraging Trust And Psychological Manipulation, SocGholish Has Managed To Infiltrate Numerous Systems, Causing Significant Harm To Individuals And Organizations Alike.
Mechanisms Of SocGholish
SocGholish Attacks Are Characterized By Their Use Of Legitimate-looking Websites And Persuasive Social Engineering Tactics. The Attack Usually Begins With A Compromised Legitimate Website Or A Malicious Advertisement. When A User Visits The Compromised Site, They Are Presented With A Convincing Pop-up Message, Often Mimicking Software Update Notifications From Trusted Sources Like Web Browsers Or Media Players.
The Pop-up Message Typically Urges The User To Download And Install An Update To View The Website's Content Or Ensure Their Software Is Up To Date. If The User Complies, They Inadvertently Download A Malicious Payload. This Payload Can Vary But Often Includes Remote Access Trojans (RATs), Keyloggers, Or Other Types Of Malware Designed To Exfiltrate Data, Gain Control Over The Victim's Machine, Or Facilitate Further Malicious Activities.
One Of The Distinguishing Features Of SocGholish Is Its Ability To Tailor The Malicious Content To The User's System. By Performing A Preliminary Check On The User's Device, Such As Examining The Operating System, Browser Type, And Other Parameters, The Malware Can Deliver A Customized Payload That Maximizes Its Effectiveness And Minimizes The Chance Of Detection.
Impact Of SocGholish
The Impact Of SocGholish Can Be Profound And Far-reaching. For Individuals, Falling Victim To A SocGholish Attack Can Result In Identity Theft, Financial Loss, And Unauthorized Access To Personal Information. The Stolen Data Can Be Used For Various Malicious Purposes, Including Fraud, Blackmail, Or Resale On The Dark Web.
Organizations, Particularly Those In Industries Such As Healthcare, Finance, And Education, Face Even Greater Risks. A Successful SocGholish Attack Can Lead To Data Breaches, Operational Disruptions, And Significant Financial Costs Associated With Remediation Efforts And Legal Liabilities. The Reputational Damage From Such Breaches Can Also Be Devastating, Eroding Customer Trust And Potentially Resulting In Long-term Business Losses.
Moreover, SocGholish Can Serve As A Gateway For More Advanced And Persistent Threats. For Instance, The Initial Infection Can Pave The Way For Ransomware Attacks, Where Critical Data Is Encrypted And Held Hostage Until A Ransom Is Paid. This Multi-stage Attack Strategy Makes SocGholish Particularly Dangerous And Underscores The Importance Of Robust Cybersecurity Measures.
Mitigation Strategies
Preventing And Mitigating SocGholish Attacks Requires A Multi-faceted Approach That Combines Technical Defenses, User Education, And Proactive Threat Intelligence.
The Following Strategies Can Help Reduce The Risk And Impact Of SocGholish:
Technical Defenses: Implementing Robust Endpoint Protection Solutions, Including Anti-malware And Anti-phishing Tools, Can Help Detect And Block Malicious Activity Associated With SocGholish. Regular Software Updates And Patch Management Are Also Crucial To Address Vulnerabilities That Could Be Exploited By Such Malware.
User Education: Since SocGholish Relies Heavily On Social Engineering, Educating Users About The Risks And Warning Signs Of Such Attacks Is Essential. Training Programs Should Emphasize The Importance Of Verifying The Authenticity Of Software Update Notifications And Being Cautious When Interacting With Pop-up Messages Or Unfamiliar Websites.
Threat Intelligence: Staying Informed About The Latest Cyber Threats And Attack Vectors Can Help Organizations Proactively Defend Against SocGholish. Participating In Threat Intelligence Sharing Initiatives And Leveraging Threat Intelligence Platforms Can Provide Valuable Insights Into Emerging Threats And Enable Timely Response Measures.
Incident Response Planning: Having A Well-defined Incident Response Plan In Place Can Significantly Reduce The Impact Of A SocGholish Attack. This Plan Should Include Procedures For Detecting, Containing, And Mitigating Malware Infections, As Well As Protocols For Communicating With Affected Stakeholders And Recovering Compromised Systems.
Network Security: Enhancing Network Security Through The Use Of Firewalls, Intrusion Detection/prevention Systems (IDS/IPS), And Secure Web Gateways Can Help Prevent The Initial Compromise And Limit The Spread Of Malware Within An Organization's Network. Network Segmentation And Access Controls Can Also Reduce The Attack Surface And Contain Potential Breaches.
Case Studies And Real-World Examples
To Illustrate The Effectiveness And Impact Of SocGholish, Consider The Following Real-world Examples:
Case Study 1: Healthcare Sector: A Large Healthcare Provider Fell Victim To A SocGholish Attack After An Employee Downloaded A Fake Software Update. The Malware Gained Access To Sensitive Patient Data, Leading To A Significant Data Breach. The Organization Faced Substantial Financial Penalties And Legal Consequences, Highlighting The Importance Of Cybersecurity In Protecting Patient Privacy.
Case Study 2: Financial Institution: A Major Bank Experienced A SocGholish Attack That Resulted In The Installation Of A Keylogger On Several Employee Computers. The Attackers Were Able To Capture Login Credentials And Gain Access To Internal Systems, Leading To Unauthorized Transactions And Financial Losses. The Incident Underscored The Need For Strong Authentication Measures And Regular Security Awareness Training For Employees.
Conclusion
SocGholish Represents A Formidable Cybersecurity Threat That Leverages Social Engineering To Deceive Users Into Downloading And Executing Malicious Software. Its Ability To Adapt And Deliver Customized Payloads Makes It Particularly Dangerous, With Significant Potential For Harm To Individuals And Organizations.
By Understanding The Mechanisms Of SocGholish And Implementing Comprehensive Mitigation Strategies, We Can Reduce The Risk Of Infection And Protect Against The Broader Consequences Of Such Attacks. In The Ever-evolving Landscape Of Cybersecurity, Staying Vigilant And Informed Is Crucial To Safeguarding Our Digital Lives.
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:




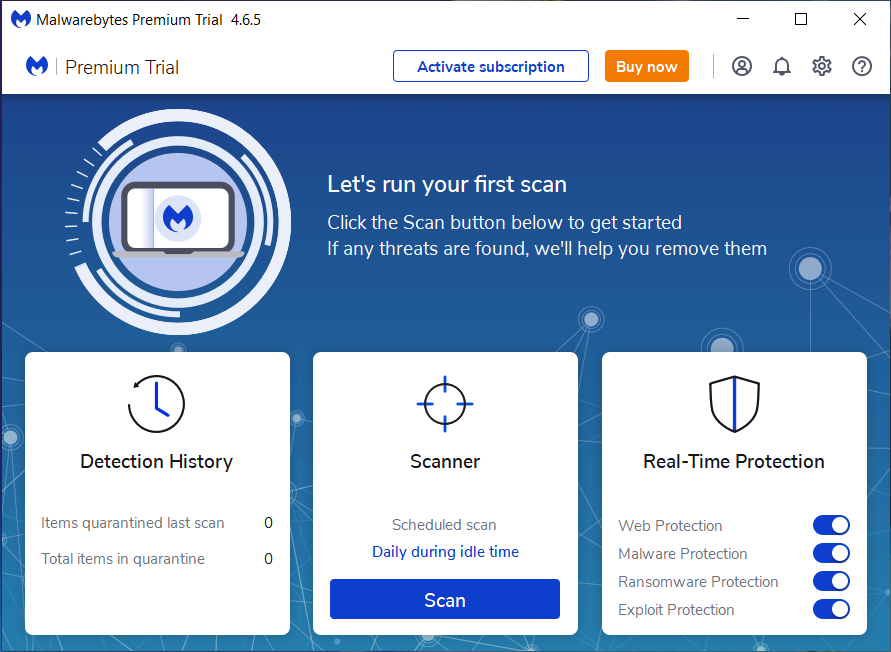
If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
SocGholish, Remove SocGholish, Uninstall SocGholish, SocGholish Removal Guide| Links1 | Links2 | Links3 | Products | Social Links |
|---|---|---|---|---|
| Home | Blog | Sitemap | Email Checker Tool | |
| About | CSI Links | ISRO Project Code: AA0802 | Offers | |
| Disclaimer | Gallery | Contact Us | Antivirus | |
| Privacy Policy | Software Downloads |