 Category's Page
Category's Page

Category: Trojan Virus | Date: 10th February 2026
Introduction Android has long been a prime target for cybercriminal due to its massive global user base and open application ecosystem. While Google Play Protect and stricter app review policies have improved platform security, malicious actors continue to find creative ways to infiltrate trusted....
Category: Trojan Virus | Date: 8th February 2026
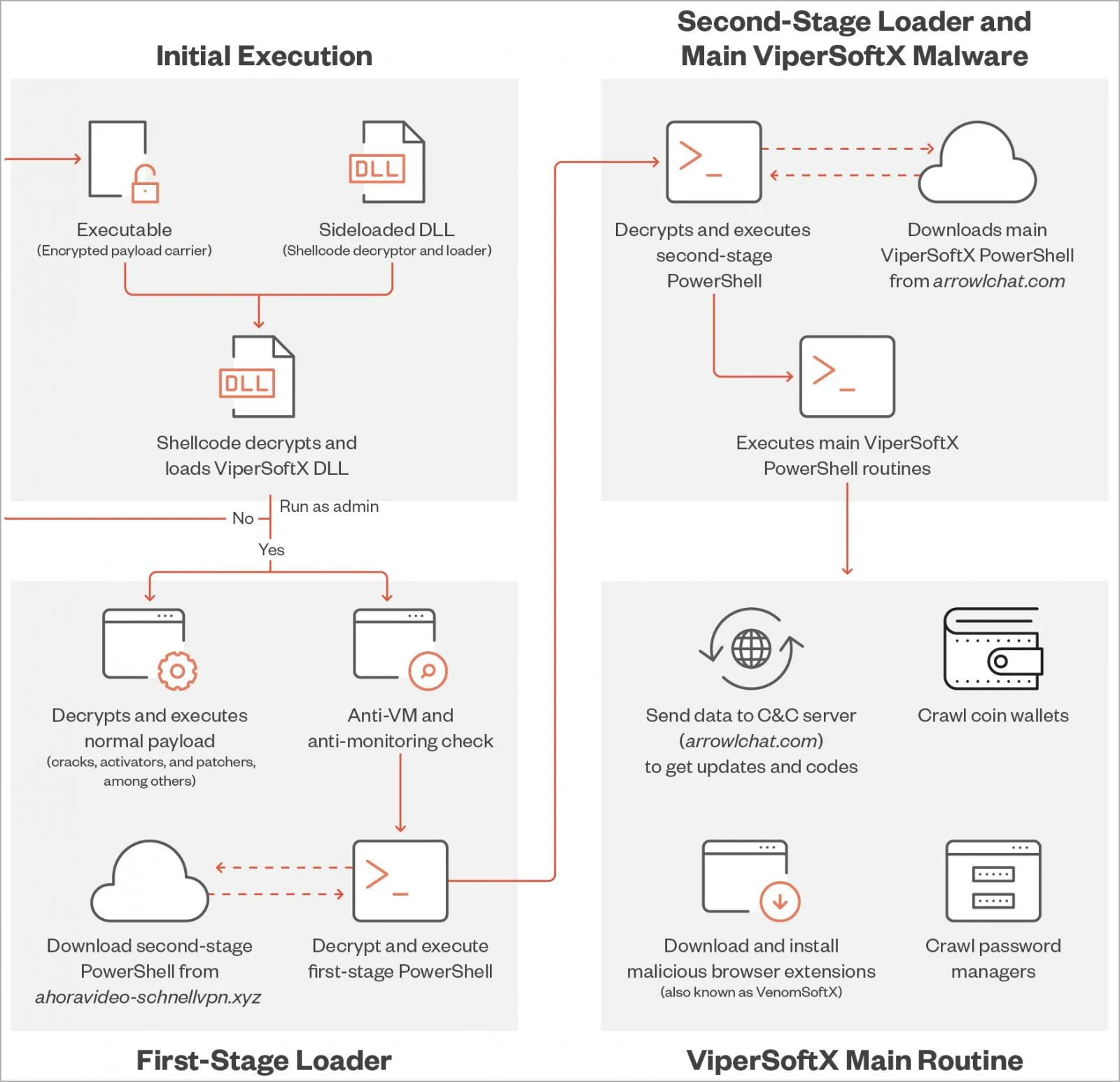
Introduction to ViperSoftX Malware Cyber threats continue to evolve, and one of the more persistent and dangerous malware strains discovered in recent years is ViperSoftX malware. Originally detected as a JavaScript-based crypto-mining malware, ViperSoftX has since evolved into a multi-stage....
Category: Trojan Virus | Date: 23rd January 2026
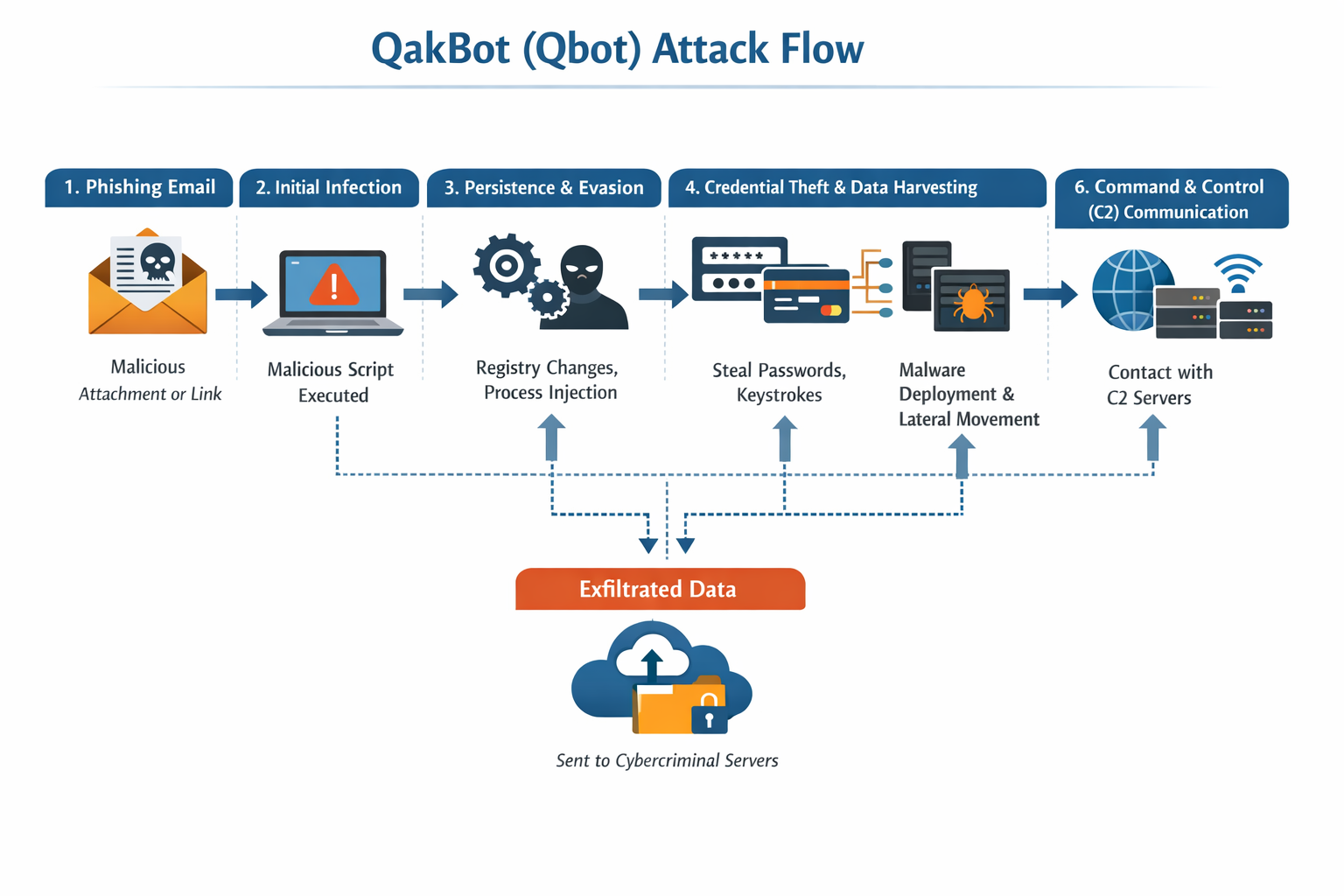
The QakBot Trojan, also known as Qbot or Pinkslipbot, is one of the most persistent and dangerous malware families in the modern cyber-threat landscape. Originally designed as a banking Trojan to steal financial credentials, QakBot has evolved into a multifunctional malware loader that enables....
Category: Trojan Virus | Date: 20th January 2026
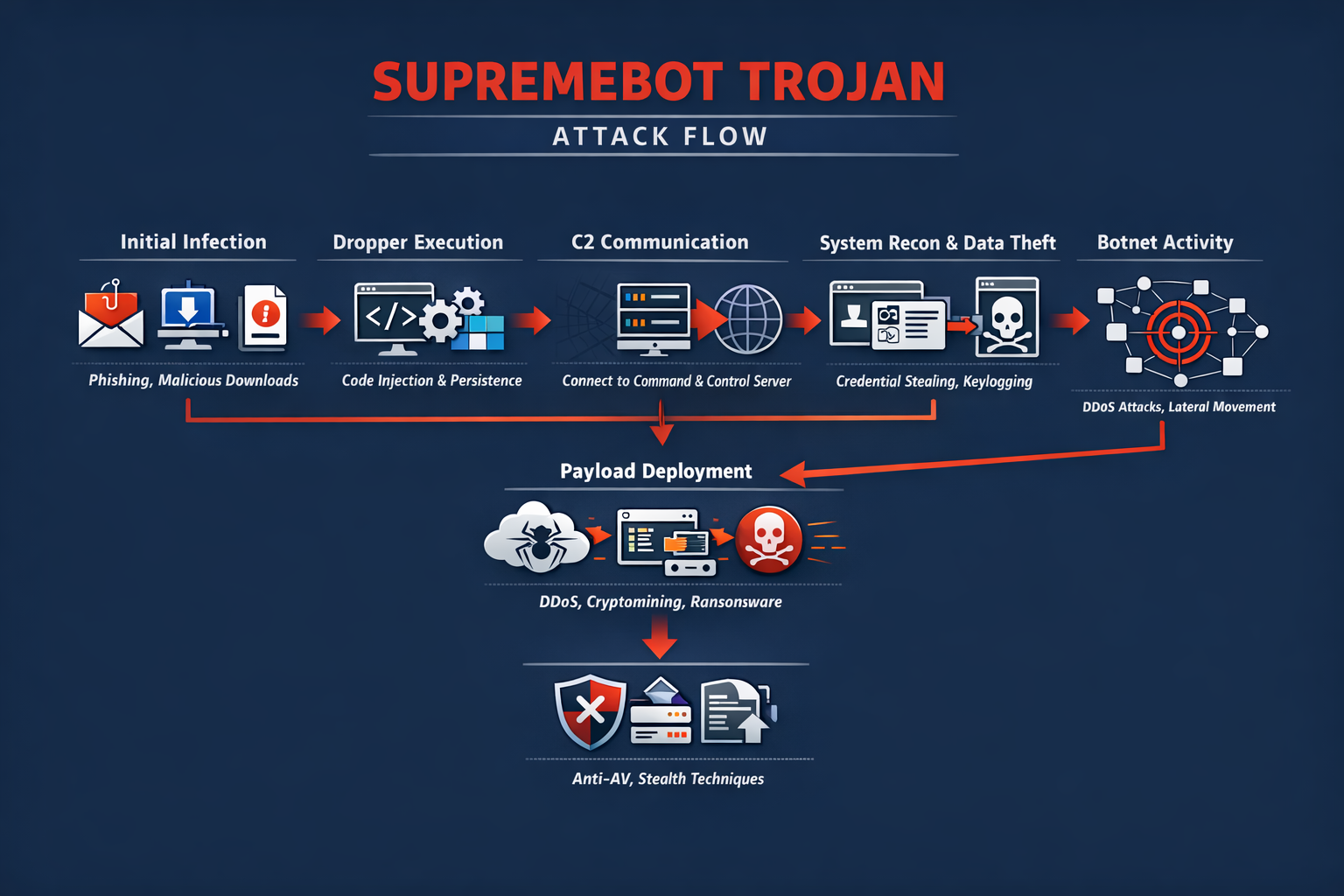
The SupremeBot Trojan is an emerging and highly adaptable malware strain that belongs to the broader category of remote access trojans (RATs) and botnet malware. Designed to silently infiltrate systems and establish persistent control, SupremeBot enables threat actors to execute commands remotely,....

Category: Trojan Virus | Date: 8th January 2026
Ramnit Banking Trojan: A Comprehensive Analysis of One of the Most Persistent Financial Malware Threats The Ramnit Banking Trojan is one of the most notorious and long-running malware families in the cybercrime ecosystem, known for its ability to steal banking credentials, compromise enterprise....

Category: Trojan Virus | Date: 23rd December 2025
Cybersecurity threats are constantly evolving, and among the latest and most dangerous malware families is the Bumblebee Malware. First discovered around 2022, Bumblebee quickly gained the attention of global security researchers because of its sophisticated infection techniques, strong evasion....
Category: Trojan Virus | Date: 1st August 2025
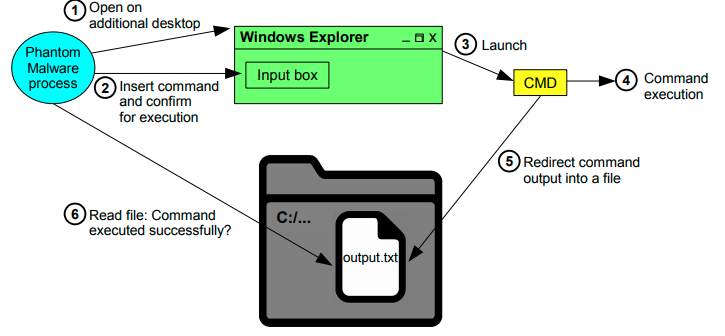
What is PhantomLayer Malware? PhantomLayer is a newly discovered, highly evasive multi-layered malware strain that uses advanced obfuscation and virtualization techniques to bypass modern security defenses. It is primarily used in targeted cyber-espionage and data exfiltration campaigns, often....
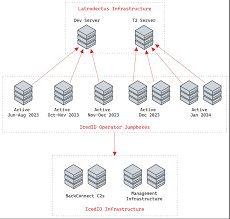
Category: Trojan Virus | Date: 31st July 2025
Introduction Latrodectus malware is an emerging cybersecurity threat that has gained attention in recent months due to its stealthy tactics and powerful capabilities. Named after the black widow spider (genus Latrodectus), this malware is designed for remote access and system manipulation,....

Category: Trojan Virus | Date: 30th July 2025
Adware\:Win32/Adposhel – Trojan Adware Threat Explained **Adware\:Win32/Adposhel** is a malicious program classified as both **adware** and a **Trojan**, meaning it not only bombards users with unwanted ads but also hides its true intent to compromise system integrity. This threat typically....
Category: Trojan Virus | Date: 7th June 2025
Bionom Query Utils Trojan Virus The Bionom Query Utils Trojan is a stealthy and malicious program that infiltrates Windows systems without user consent. Often bundled with freeware or hidden in deceptive email attachments, this Trojan disguises itself as a legitimate utility to avoid detection.....

Category: Trojan Virus | Date: 24th April 2025
Crowq Utils Sol is a dangerous Trojan virus that infects systems through malicious software downloads or phishing schemes. Once inside, it compromises the system, stealing sensitive data like passwords, banking information, and login credentials. This malware often operates in the background,....

Category: Trojan Virus | Date: 14th March 2024
The Taskbar System is a Trojan infection designed to target Windows computers, with the capability to seize control of the compromised system and carry out various destructive processes within it. Belonging to the extensive family of Trojan infections, The Taskbar System can inflict multiple forms....

Category: Trojan Virus | Date: 9th February 2024
Win32/Filecoder.Trigona.A is a heuristic detection method aimed at identifying a Trojan Horse. Win32/Filecoder.Trigona.A employs behavioral analysis to detect suspicious activities, enabling antivirus software to recognize and neutralize potential threats, even if their specific signatures are not....

Category: Trojan Virus | Date: 9th February 2024
Win32/Remtasu.O is a heuristic detection method engineered to identify a Trojan Horse with a high level of generality. A Win32/Remtasu.O Trojan Horse, in computing terms, refers to a type of malware that disguises itself as a legitimate file or program to infiltrate a user's system, subsequently....

Category: Trojan Virus | Date: 4th December 2023
StopAbit operates similarly to enticing yet dubious online offers that seem too good to resist. Unlike the forceful methods employed by computer viruses, StopAbit relies extensively on deception, enticing unsuspecting users through appealing emails or links to popular videos. The true danger....

Category: Trojan Virus | Date: 22nd November 2023
Trojan.VBS.Agent.kq is a malicious trojan infection that operates discreetly, infiltrating computer systems without detection. Once inside, it establishes a connection with a remote server, enabling the download of additional malware onto the compromised system. Trojan.VBS.Agent.kq trojan takes....

Category: Trojan Virus | Date: 22nd November 2023
Trojan-Ransom.Cidox is intricately linked to the Vundo downloader and other perilous malware infections. Trojan-Ransom.Cidox trojan is a key player in a ransomware attack, wherein it encrypts the victim's files and coerces them into paying a ransom to regain control over their own data. Acting as....

Category: Trojan Virus | Date: 22nd November 2023
Trojan.EyeStye is a malicious trojan infection that poses a significant threat to computer systems by employing sophisticated techniques to evade detection by various antivirus programs, thereby remaining concealed within the PC. Trojan.EyeStye trojan often adopts a deceptive guise, masquerading....

Category: Trojan Virus | Date: 22nd November 2023
Trojan.FakeAV!gen24 is a type of trojan malware that deceives users by posing as legitimate antivirus software. Trojan.FakeAV!gen24 often infiltrates computer systems through various deceptive means, such as malicious websites, phishing emails, fake software updates, and infected downloads. Once....

Category: Trojan Virus | Date: 9th November 2023
"Trojan.Midie." It's possible that this is a new or less common variant that has emerged after that time, or it might be a localized or specific name given by certain antivirus vendors or security researchers. If you suspect your system has been affected by a Trojan virus or any other malware,....

Category: Trojan Virus | Date: 8th November 2023
Boot.Mebromi.B is a Trojan notorious for infecting the Basic Input and Output Settings (BIOS) as well as the Master Boot Record (MBR) of a computer system. Boot.Mebromi.B malware employs cunning tactics to disguise its presence on the compromised PC and evade detection by security tools. When....

Category: Trojan Virus | Date: 8th November 2023
ChaChi is a novel Remote Access Trojan (RAT) recently uncovered by malware researchers. ChaChi Trojan stands out for being entirely written in GoLang, a choice reflecting a growing trend among cybercriminals to shift away from conventional C and C++ languages in favor of more obscure and....
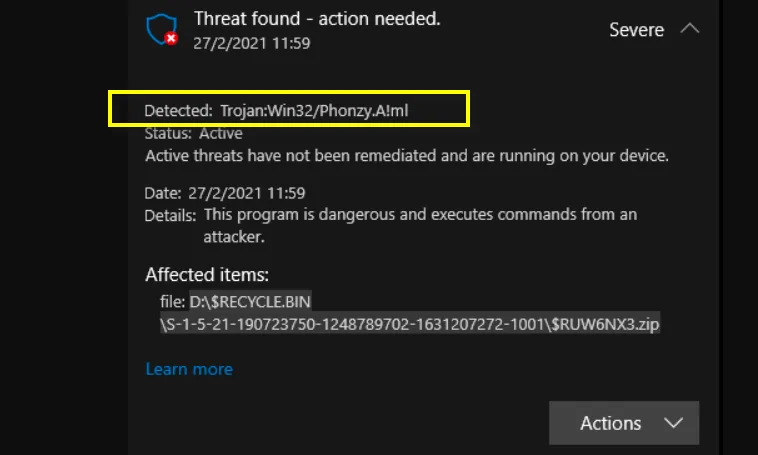
Category: Trojan Virus | Date: 8th November 2023
The Phonzy Trojan belongs to the category of banking trojans, a specialized type of malware that has surged in prevalence with the widespread adoption of online banking. Phonzy Trojan is crafted to stealthily gather your banking credentials, aiming at breaching the security protocols established by....

Category: Trojan Virus | Date: 7th November 2023
Trojan.MacOS.Ravir is a generic malware detection targeting macOS systems. As a Trojan, Trojan.MacOS.Ravir can discreetly infiltrate devices through multiple channels. Once installed, Trojan.MacOS.Ravir operates with two primary goals: executing malicious activities and remaining undetected. The....

Category: Trojan Virus | Date: 7th November 2023
Scammers are sending deceptive emails that mimic purchase invoices, aiming to deceive users into calling a fake phone number. This spam email campaign falls under various categories, including technical support, phishing, and refund scams, based on the fraudsters' specific objectives. The emails....
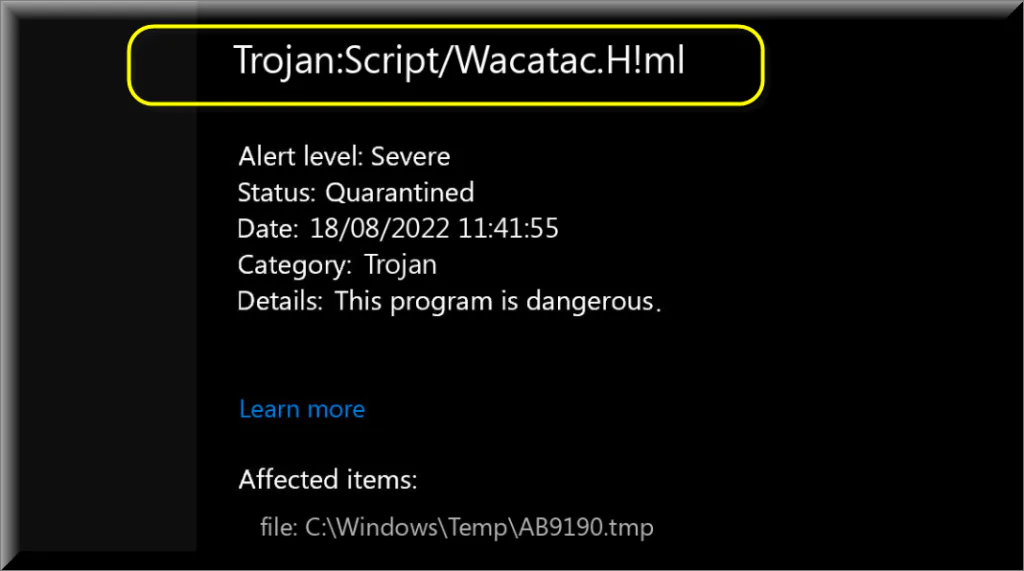
Category: Trojan Virus | Date: 7th November 2023
Trojan:Script/Wacatac.H!ml is a security alert indicating the potential presence of a Trojan on a user's device, likely belonging to the Walatac strain. Trojans are malicious software designed to gather sensitive information like login details and banking credentials. Cybercriminals exploit this....

Category: Trojan Virus | Date: 7th November 2023
Trojan.Malware.300983.susgen is a malware detection term commonly displayed by security software following heuristic analysis. Unlike traditional signature-based detection, Trojan.Malware.300983.susgen method identifies suspicious items based on their behavior. In this context, the detection....

Category: Trojan Virus | Date: 6th November 2023
QwixxRAT is a dangerous trojan virus designed to infiltrate computers, compromising their security and user privacy. QwixxRAT malicious software operates stealthily, disguising itself as legitimate files or software updates, deceiving users into unwittingly installing it. Once QwixxRAT inside a....

Category: Trojan Virus | Date: 1st November 2023
A recent wave of mobile banking malware has emerged, targeting Indian banking customers with a variant known as the SOVA Android Trojan. SOVA Android Trojan malicious software, which initially surfaced in underground markets in September 2021, possesses alarming capabilities. SOVA Android Trojan....

Category: Trojan Virus | Date: 18th October 2023
Trojan:Script/Phonzy.B!ml is a heuristic detection method created to identify a specific type of malware known as a Trojan Horse. Heuristic detection operates by analyzing the behavior and characteristics of files or programs to identify patterns common to malicious software. In this case, the....

Category: Trojan Virus | Date: 18th October 2023
VirTool:Win32/ModTool!pz is a heuristic detection method created to identify a specific type of malware known as a Trojan Horse. Heuristic detection relies on behavioral analysis and algorithms to generically recognize patterns and behaviors associated with VirTool:Win32/ModTool!pz malware,....

Category: Trojan Virus | Date: 22nd September 2023
In the ever-evolving landscape of cyber threats, banking trojans have remained a persistent menace, constantly adapting and evolving to exploit vulnerabilities in the financial sector. One such Trojan that has made waves in recent years is BBTok. This insidious malware has been responsible for a....

Category: Trojan Virus | Date: 15th September 2023
In the ever-evolving landscape of cybersecurity threats, one particularly insidious adversary is the Data-Sending Trojan, a type of malicious software that can silently infiltrate your devices and steal sensitive information without your knowledge. These stealthy threats have been responsible for....

Category: Trojan Virus | Date: 16th August 2023
In the ever-evolving landscape of cybersecurity threats, mobile devices have become prime targets for malicious actors seeking to compromise personal and sensitive information. One such threat is the SpinOk mobile malware, a sophisticated piece of malicious software designed to infiltrate and....

Category: Trojan Virus | Date: 3rd August 2023
The FrightfulPasape.exe Trojan virus is a dangerous piece of malware that can wreak havoc on your computer system and compromise your sensitive information. Trojans, like FrightfulPasape.exe, disguise themselves as legitimate files or software to infiltrate your device and perform malicious....

Category: Trojan Virus | Date: 2nd August 2023
Trojan viruses, like Zamguard64.sys, pose a significant threat to the security and integrity of your computer system. These malicious programs disguise themselves as legitimate files or software, infiltrating your system to steal sensitive information, cause damage, or create backdoors for other....

Category: Trojan Virus | Date: 1st August 2023
The digital era has brought about numerous conveniences, but it has also given rise to sophisticated cyber threats that can compromise our security and privacy. Among these threats is the Anatsa Trojan Virus, a stealthy and malicious software capable of causing significant damage to individuals....
Category: Trojan Virus | Date: 1st August 2023
In the realm of cybersecurity, the ever-evolving landscape of malware poses serious risks to the integrity and security of computer systems. Among these insidious threats is the Trojan:Win32/Wacatac.B!ml Trojan virus, a malicious software that can wreak havoc on an infected system. In this....

Category: Trojan Virus | Date: 1st August 2023
With the proliferation of smartphones and the increasing dependence on mobile devices for various tasks, cybercriminals have shifted their focus to exploit vulnerabilities in the Android ecosystem. Among these malicious threats is the FakeTrade Android malware, a deceptive and harmful software that....

Category: Trojan Virus | Date: 29th July 2023
A HotRat Trojan Virus, or simply a Trojan, is a type of malware that disguises itself as legitimate software but has malicious intent. Unlike viruses or worms, Trojans do not replicate themselves. Instead, they rely on social engineering techniques to trick users into executing them, often by....

Category: Trojan Virus | Date: 27th July 2023
AsyncRAT, short for Asynchronous Remote Administration Tool, is a malicious Trojan virus that poses a significant risk to computer systems and user privacy. This stealthy malware is designed to grant unauthorized access to cybercriminals, enabling them to remotely control the infected system and....

Category: Trojan Virus | Date: 27th July 2023
HotRat is a dangerous Trojan virus that can cause significant damage to your Windows PC. Once infected, this malware can steal sensitive information, compromise your online security, and even grant unauthorized access to cybercriminals. Removing the HotRat Trojan virus promptly is crucial to....

Category: Trojan Virus | Date: 27th July 2023
Decoy Dog is a malicious malware variant that has been wreaking havoc in the cybersecurity landscape. As a sophisticated and elusive threat, Decoy Dog is designed to evade detection and steal sensitive information from unsuspecting victims. This article aims to shed light on the nature of Decoy....
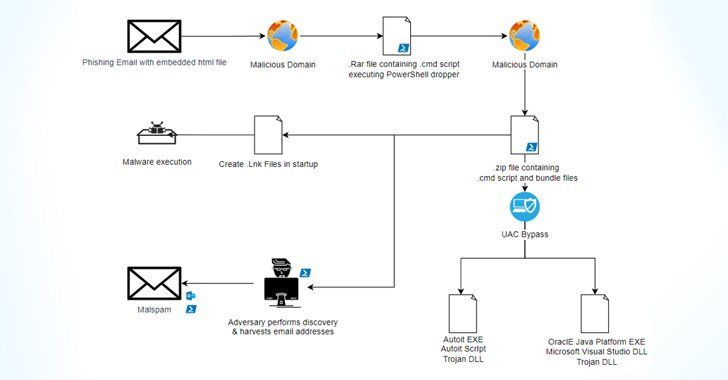
Category: Trojan Virus | Date: 27th July 2023
Casbaneiro, also known as Metamorfo, is a dangerous banking Trojan that poses a significant threat to individuals and businesses alike. This sophisticated malware is designed to steal sensitive financial information, such as login credentials and credit card details, ultimately leading to financial....
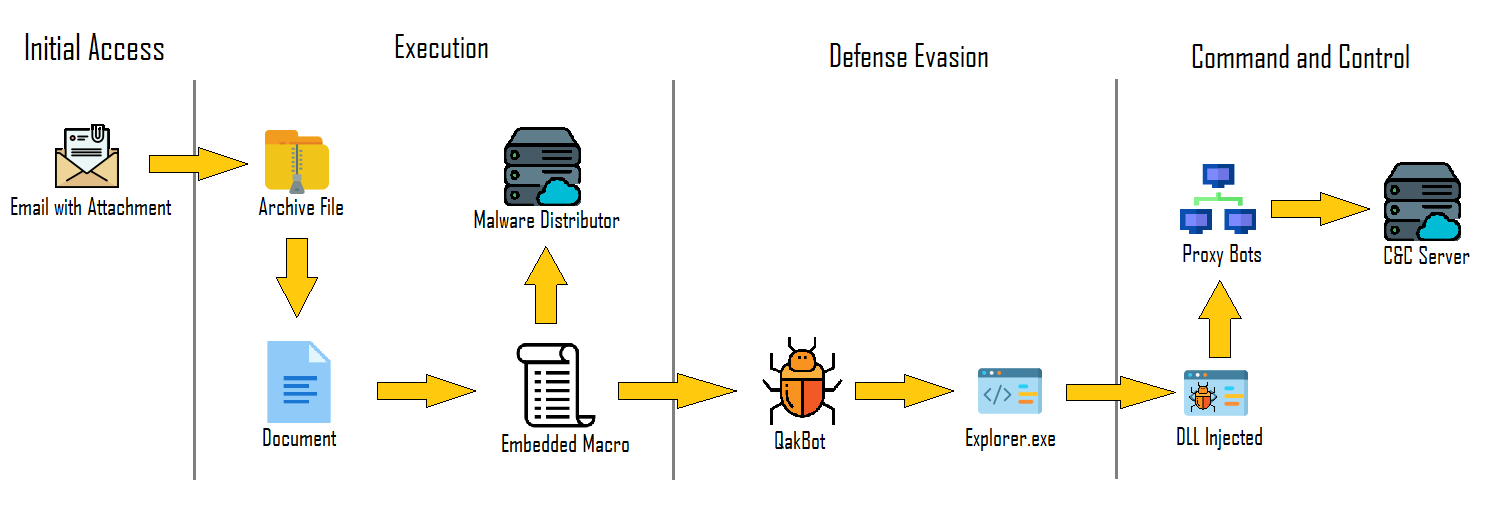
Category: Trojan Virus | Date: 27th July 2023
In the digital age, cybercriminals continually evolve their tactics to exploit vulnerabilities and gain unauthorized access to sensitive information. One such notorious threat is the Qakbot banking Trojan virus. Initially discovered in 2007, Qakbot (also known as Qbot or Pinkslipbot) has since....
Category: Trojan Virus | Date: 25th July 2023
The digital world is fraught with a wide range of cyber threats, and one of the most notorious is the Trojan:Win32/Randet.A!plock Trojan virus. Trojan:Win32/Randet.A!plock malicious software, commonly referred to as a Trojan, is designed to stealthily infiltrate your system and cause havoc,....

Category: Trojan Virus | Date: 24th July 2023
As technology advances, so do the cyber threats that seek to exploit it. In the ever-evolving landscape of malware, one particularly insidious Trojan virus stands out: BlotchyQuasar, also known as X-Force Hive0129. This sophisticated cyberweapon has gained notoriety for its stealthy and elusive....

Category: Trojan Virus | Date: 24th July 2023
In the realm of cyber threats, malicious actors continue to create sophisticated malware designed to infiltrate systems and compromise user security. One such notorious cyberweapon is the njRAT Trojan, a remote access Trojan (RAT) that grants attackers full control over infected devices. This....

Category: Trojan Virus | Date: 24th July 2023
In the ever-evolving landscape of cybersecurity threats, new malware strains continuously emerge, posing significant risks to individuals and organizations alike. One such notorious menace is WR64.sys trojan virus, a sophisticated and stealthy piece of malicious software that has wreaked havoc....

Category: Trojan Virus | Date: 16th July 2023
In the ever-evolving world of cybersecurity, new threats continue to emerge, posing risks to computer systems and sensitive information. One such threat is the Vkise.exe Trojan virus. This article aims to provide an analysis of the Vkise.exe Trojan, its potential impact on infected systems, and....
Category: Trojan Virus | Date: 16th July 2023
The threat landscape of the digital world is constantly evolving, with cybercriminals devising new ways to exploit vulnerabilities and compromise computer systems. In recent times, a new trojan virus called "Windows-Critical-KB8928948-x64.exe" has emerged, targeting Windows operating systems. This....

Category: Trojan Virus | Date: 14th July 2023
The Anubis Trojan virus has gained notoriety as a highly sophisticated and dangerous malware that poses a significant risk to computer systems and user privacy. Designed to steal sensitive information and carry out malicious activities, the Anubis Trojan has caused considerable harm to unsuspecting....

Category: Trojan Virus | Date: 7th July 2023
The BGAUPsell.exe trojan virus has emerged as a significant cybersecurity threat, causing concern among computer users and security experts alike. BGAUPsell.exe malicious program disguises itself as a legitimate system file, deceiving users and compromising the security and functionality of....

Category: Trojan Virus | Date: 27th May 2023
PowerShell itself is a legitimate scripting language and automation framework developed by Microsoft. It is a powerful tool that allows system administrators and IT professionals to automate tasks and manage Windows environments. However, like any powerful tool, it can be misused for malicious....
Category: Trojan Virus | Date: 2nd March 2023
Troj/Zbot-HTQ Is Well Known Trojan Program, Which Has Been Created For Hacking The Terminal. Troj/Zbot-HTQ May Also Collect The Data, Or Information, Which Is Very Fruitful For The Stranger. However, Troj/Zbot-HTQ Has Ability To Counter Firewall As Well As The Security Program Including....

Category: Trojan Virus | Date: 2nd March 2023
Mal/DrodZp-A is Dispersing Through A False Or Counterfeit Reservation Mail. Mal/DrodZp-A Is Categorized As A Trojan Virus Program. Mal/DrodZp-A Is Also Classified As A Malware Code. Mal/DrodZp-A May Infringe Many Cyber Laws. Mal/DrodZp-A Is Used Fake Email Campaign And Entice The Users.....

Category: Trojan Virus | Date: 2nd March 2023
Troj/NecKMem-A Will Strive To Weak The Computer System, And Infringes Numerous Data As Well As Send Them To Remote Server. Troj/NecKMem-A Is A Touch-and-go Trojan Virus Program, Which Has Been Designed By The Computer Goons Professional For Their Own Interest. However, Troj/NecKMem-A Has....

Category: Trojan Virus | Date: 2nd March 2023
Troj/ZbotMem-B Steals The Data As Well As The Significant Information From The Compromise Computer System, While User Would Visiting The Pornographic Website Or Strange Email Address. Troj/ZbotMem-B Is An Obsolete Version Of Trojan Zeus. Troj/ZbotMem-B Is Called As A Banking Trojan Virus,....

Category: Trojan Virus | Date: 2nd March 2023
Hpmal/Zbot-C Is A Trojan Virus, That Has Been Fabricated By The Computer Criminal, Which Can Utilize Hpmal/Zbot-C As A Tool For Freeze The Computer System And Do More. Hpmal/Zbot-C Is Pertaining With Zbot Trojan Program That Invades Financial Organizations In Canada. Hpmal/Zbot-C Incorporates....

Category: Trojan Virus | Date: 2nd March 2023
Trojan.Agent.MNR Is An Obfuscated Computer Trojan Virus Application, That Trojan.Agent.MNR May Infringe Many PC Barrier And Develops A Backdoor Route To Enter Feeble Computer Machine. Trojan.Agent.MNR Has Been Created By The Cyber Goons. Trojan.Agent.MNR May Embed Bitcoin Miner Code Into The....

Category: Trojan Virus | Date: 1st March 2023
Cleaner.exe is generic malware name that can prefer to any executable file on a Windows computer system. Cleaner.exe could be a licit file used by a windows operating system or application. Cleaner.exe could be malicious program masquerading as a genuine file name or normal executable file.....

Category: Trojan Virus | Date: 1st March 2023
Necurs Or Necurs Botnet Is A New Type Of Trojan Virus Program. Necurs Botnet May Infect All Version Of Windows Operating System. Necurs Botnet Is Dealing With Number Program, That Can Reveal Various Lucrative Data. Necurs Botnet Trojan Virus Has Been Coded Very Deceive Manner To Cope The....
Category: Trojan Virus | Date: 1st March 2023
Trojan.Ransomlock Is New Types Of Heuristic Detection Files For The Confused The Computer Security System, Which May Commence For Scanning The Malicious Program. However, Trojan.Ransomlock Is Also Categories As A Trojan Malware, That Deceive The User Activity. Your Internet Connection, CPU....
Category: Trojan Virus | Date: 1st March 2023
Packed.Generic.457 Is Also A Trojan Program. Packed.Generic.457 May Infringe Many Security Fence Or Barrier. Packed.Generic.457 Is Scanned By The Various Security Vendor And Detected On February 11, 2014 And Also Modified On February 11, 2014 12:37:47 PM. Packed.Generic.457 Is Categories As A....

Category: Trojan Virus | Date: 1st March 2023
Trojan.Zbot Has Been Incapacitated The Feeble Computer System. Trojan.Zbot Has Ability To Counter Security Software As Well As The Firewall Software, Which Is Already Installed In The Windows Operating System. However, Trojan.Zbot Can Infringe Numerous Laws And Flouts Privacy. Despite Of,....
Category: Trojan Virus | Date: 27th February 2023
Trojan.StolenData May Collapse The Computer Registry Files And Data From The Windows Based Computer System. Trojan.StolenData Has Been Affected To The Window Operating System. Trojan.StolenData Is Savage Trojan Code To Violate The Cyber Fence. Trojan.StolenData May Surpass The Firewall As Well....
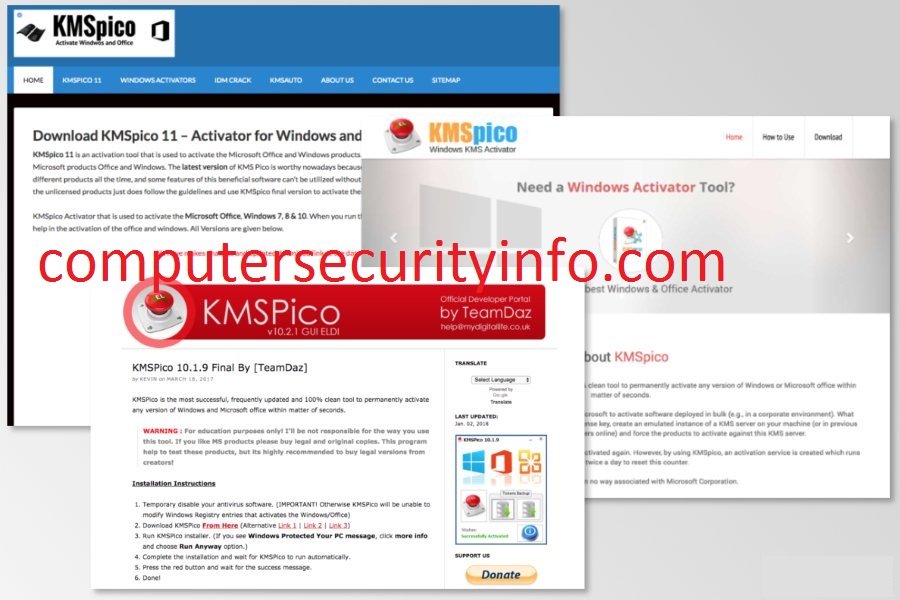
Category: Trojan Virus | Date: 27th February 2023
Kmspico Is A Terrible Trojan Virus Program To Delude The User And Display The Blue Screen On The Desktop. However, There Are Numerous Issues Raised Steps-by-steps, But You Can’t Scan Kmspico Trojan Virus Manual Process. In The Spite Of, Kmspico Has Been Coded By The Cyber Criminal, That....

Category: Trojan Virus | Date: 27th February 2023
Explorer.exe Http Kbribaki.org Is A File And URL, Both Are Incorporated With Each Other. According To The Remarks By The Victims. Numerous Remarks Has Been Created On Different Security Form Regarding Explorer.exe Http Kbribaki.org Unwanted Program. Explorer.exe Is A Windows Explorer Files,....

Category: Trojan Virus | Date: 27th February 2023
Trojan.Agent.Trace Is A Sceptical Malware Application. Trojan.Agent.Trace Is Not Very Harmful For The Vulnerable Terminal, But The Presence Of Trojan.Agent.Trace Is A Notion Of A Computer System Contamination. The Target Or Traces Can Be Leftovers From An Always Uninstall Trojan Virus Malware.....

Category: Trojan Virus | Date: 21st February 2023
Trojan.Muldrop 6.11863 Is A Trojan Code, That Has Been Crafted By Cyber Goons. Trojan.Muldrop6.11863 Is Very Baleful Application, Which Has Been Made For Various An Illegal Work, Including IP Address Details, Browser Information, Cookies History, And So On. Trojan.Muldrop 6.11863 May Be....
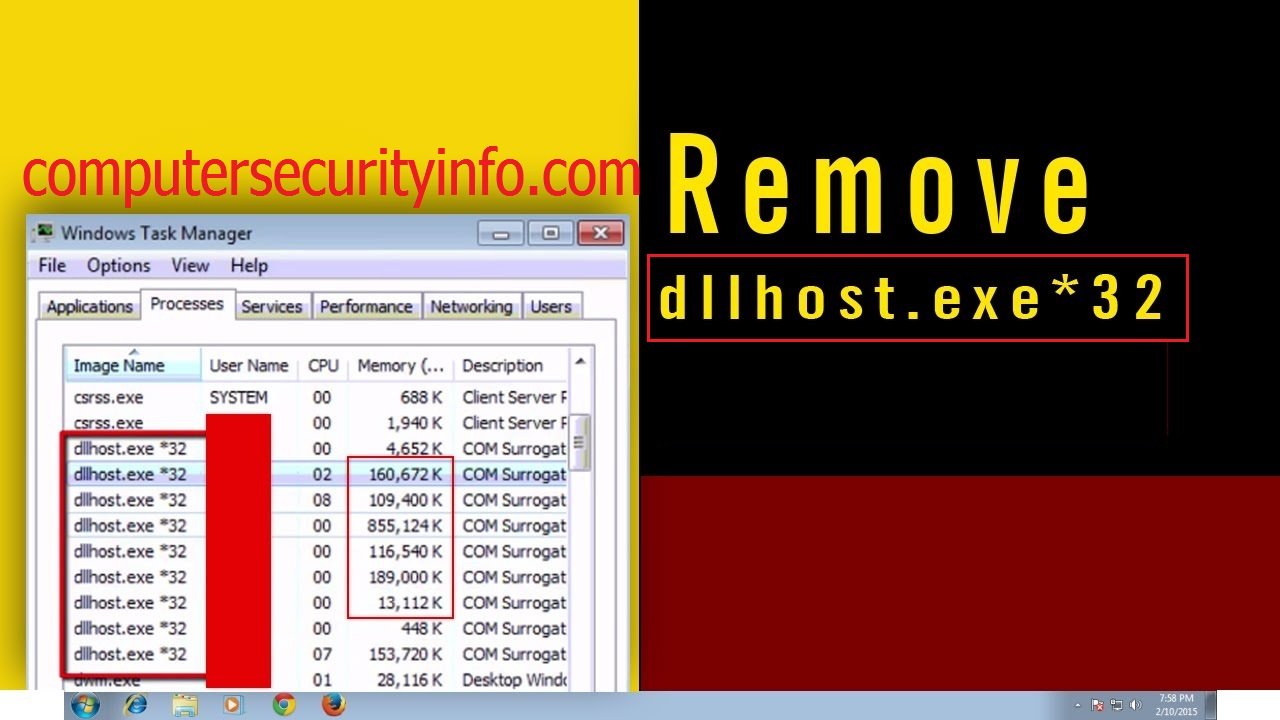
Category: Trojan Virus | Date: 16th February 2023
Dllhost.exe*32 Seems As An Executable Files, Which May Be Incorporated With Windows Operating System. Dllhost.exe Is Also Known As *32 COM Surrogate, Is A Process Applied To Run Host One Or More Operating System Services Simultaneously. Dllhost.exe *32 Is Called As A Microsoft Windows....

Category: Trojan Virus | Date: 16th February 2023
Trojan.Bhubot Is New Code Of Trojan Virus That Runs On The Vulnerable Computer System And Creates Various Issues One By One. However, Trojan.Bhubot Targets Very Feeble Terminal, Because Trojan.Bhubot Can Infiltrate Easily. Trojan.Bhubot Have Best Algorithm To Judge Which Terminal Is Safe For....

Category: Trojan Virus | Date: 16th February 2023
The User Computer Hacked By The MSIL:Agent-BUN Vicious Trojan Virus. MSIL:Agent-BUN Is A Very Cunning Trojan Program To Infiltrate Your Terminal Secretly And Steal Data From The Compromise PC As Well. However, MSIL:Agent-BUN Is Fabricated For Accumulating The Data Into Various Terminal.....

Category: Trojan Virus | Date: 16th February 2023
Trojan.Cidox.C Is A Grim Trojan Program, Which Will Endeavor To Lock Users Computer And Corrupt Essential Files And Text Files. Trojan.Cidox.C Creates Potentially Contaminated Files On The Terminal. Trojan.Cidox.C May Badly Affect The Registry Editor, Task Manger, Browser Extension, Browser....
Category: Trojan Virus | Date: 16th February 2023
Trojan:Win32/Magentos Has Been Coded By The Perpetrators To Invade The Users System And Gets Resourceful Data For Their Own Interest. Trojan:Win32/Magentos Was Scanned By The Microsoft Security Essential Software, Windows Defender As Well As Other One. Trojan:Win32/Magentos Has Contained With....
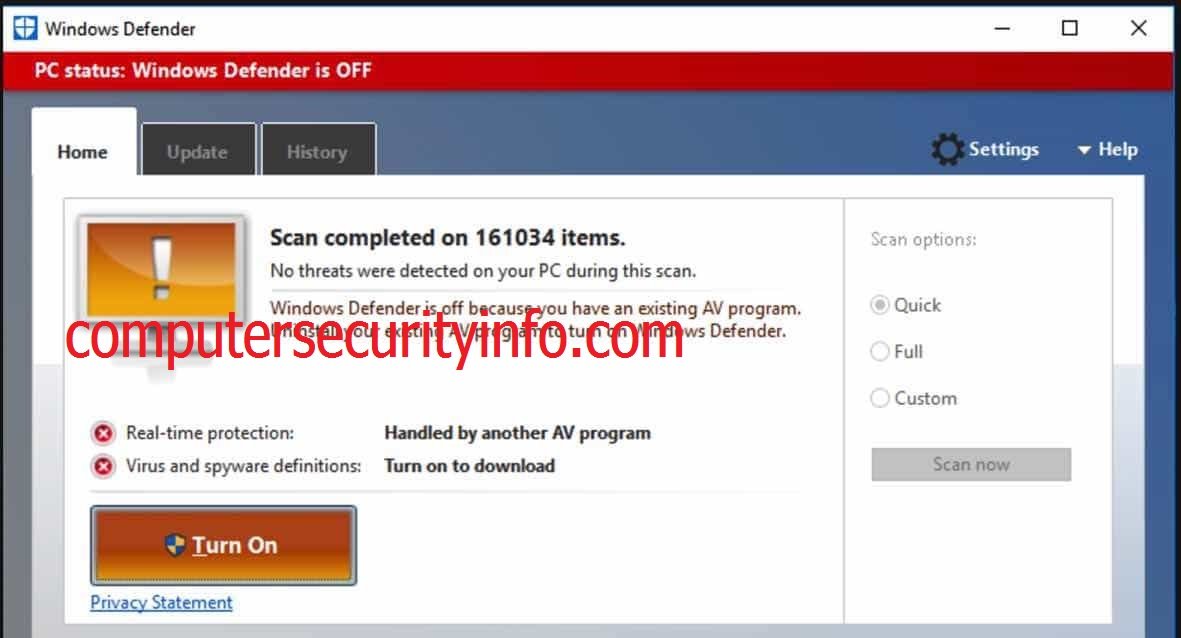
Category: Trojan Virus | Date: 15th February 2023
Trojan.Malpack.Gen Is Well Known Trojan Virus, If User Was Introduced. Whether New Computer User Are Comprehend That, Trojan.Malpack.Gen Is A Very Treacherous Trojan Program. Trojan.Malpack.Gen Will Design To Invade The System Clandestine Way. According To The Various User Reviews, There Are....

Category: Trojan Virus | Date: 15th February 2023
JS:Downloader-ZY [Trj] Is Seems To Be A Trojan Virus And Annihilate The Computer Registry Editor As Well As The Task Manager Tools. There Are Various Trouble Happen Inadvertently Due To JS:Downloader-ZY [Trj] Trojan Virus. JS:Downloader-ZY [Trj] May Affect Web Browser Such As Google Chrome,....

Category: Trojan Virus | Date: 15th February 2023
Trojan.Pandex!inf Is A Dangerous Trojan Contamination For The Computer System. Trojan.Pandex!inf Has Been Coded By The Cyber Criminal. Trojan.Pandex!inf Is Detected By The Antivirus And Anti-malware In 2014 As Well As Addresses A Severe Threat To The Computers Security And To The PC....

Category: Trojan Virus | Date: 15th February 2023
Trojan.Win32.Delf.kf Can Sabotage HTTPS And HTTP (Safe And Unsafe Internet Data) Inadvertently. However, Trojan.Win32.Delf.kf Has Been Developing A Unique Code While Reach Your System. Trojan.Win32.Delf.kf May Very Hazardous For The Computer System. Trojan.Win32.Delf.kf May Accumulate....

Category: Trojan Virus | Date: 15th February 2023
Trojan.Win32.Cosmu.xz Is A Precarious Trojan Virus Program, Which Has Been Coded By The Cyber Criminal. Trojan.Win32.Cosmu.xz Has Worked Every Operating System, Whether You Are Using Macintosh Or Windows. Trojan.Win32.Cosmu.xz Will Compromise CPU And Other Peripheral Devices.....

Category: Trojan Virus | Date: 15th February 2023
Trojan Horse Generic17.AMPT Is Appeared As A Form Of Trojan Application And It Is Non Self Replicating Parasite Active On The Internet To Invade Those Computer System Whose Security System Is Not Properly Revamp As Well As Some Loopholes In Your Security Application Which Can Take Advantage By....

Category: Trojan Virus | Date: 14th February 2023
Trojan.Dropper.Agent Is A Very Heuristic Detection Fabricated Code To Usually Scan A Trojan Virus. Trojan.Dropper.Agent Is A Generic Characters And Big Potential Threat, We Are Not Capable To Inform Diluted Data On What Trojan.Dropper.Agent Does. Trojan.Dropper.Agent Will Capacity To Freeze The....

Category: Trojan Virus | Date: 14th February 2023
Soundrec.exe Is A Precarious Trojan Virus Code, Which Is Running On The Windows System As An Executable File. However, Soundrec.exe Has Been Improved Or Tempted By The Cyber Goons To Theft Data And Vandalize Computer System Step By Step. Soundrec.exe Is Also Classified As A Mining Software.....
Category: Trojan Virus | Date: 14th February 2023
Heuristic.HEUR/AGEN.1030693 Is Scanned By Latest Anti-malware Software As A Trojan Virus. Heuristic.HEUR/AGEN.1030693 Has Capacity To Reach Enfeeble Account Through Backdoor. Heuristic.HEUR/AGEN.1030693 Is Fabricated By Computer Criminals And Rip-off Internet User Data Through Illegitimate....

Category: Trojan Virus | Date: 14th February 2023
HEUR/APC (Cloud) Is A Heuristic Cloud Program, Which Is Scanned By The Security Software Or Anti-virus Program. There Are Number Of HEUR/APC (Cloud)’s Files Detected By The Security Tools. HEUR/APC (Cloud) Has Been Created By The Goons To Manipulate The User Activity. HEUR/APC (Cloud) Will....
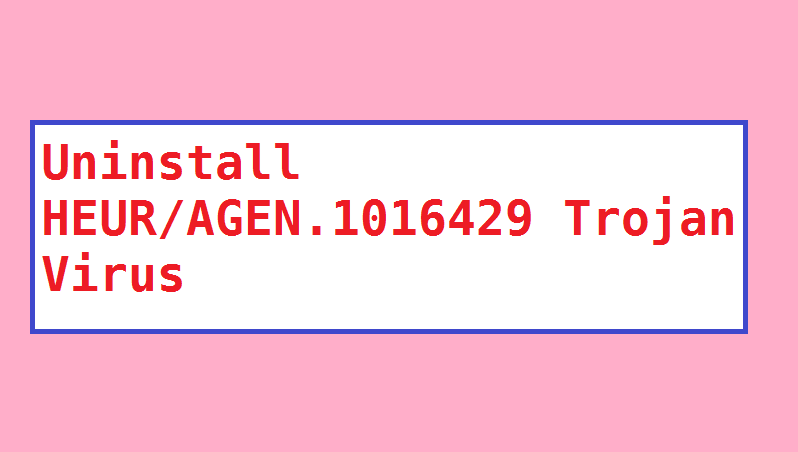
Category: Trojan Virus | Date: 14th February 2023
HEUR/AGEN.1016429 Is New Types Of Trojan Virus. HEUR/AGEN.1016429 Has Been Created By The Cyber Goons To Infiltrate Your System And Gets Indispensable Information From The Victim’s Terminal. The Various Eminent Anti-virus, Anti-malware And Internet Security Manufacture Are Recognized....
Category: Trojan Virus | Date: 14th February 2023
If Your Computer Screen Has Been Displayed With Small Rotating Bug And Other Illusive Action, That Means Your PC Has Been Affected By The TR/Patched.Ren.Gen3.16e2bc7cae!fsocap Trojan Virus. The Web Browser And Small Extension Are Also Tainted By TR/Patched.Ren.Gen3.16e2bc7cae!fsocap....

Category: Trojan Virus | Date: 14th February 2023
Heuristic.HEUR/AGEN.1024441 Is A Heuristic Trojan Virus Code, That Can Completely Cripple The Computer System. Heuristic.HEUR/AGEN.1024441 Has Been Crafted By The Cyber Goons To Sneak The Data From The Victim’s Computer System. Heuristic.HEUR/AGEN.1024441 Is Designed For Infected....

Category: Trojan Virus | Date: 7th February 2023
Win32/Skeeyah.l Trojan Is Stealing The Information From The Victim’s Terminal. Win32/Skeeyah.l Trojan May Exploit The Victim’s Computer Resource For Their Own Goal. Win32/Skeeyah.l Trojan Will Disperse Itself By Spam Mail, Fake Email Attachment And Strange Web Links.....

Category: Trojan Virus | Date: 7th February 2023
Infected By Remote Access Trojan (RAT) Is A Treacherous And Menacing Trojan Virus Program, Which Is Working For Those Terminal, Who Are Not Accessed By The Physically. With The Design And Program Development, The Number Of Malware Invasion Grow Rapidly. Infected By Remote Access Trojan (RAT)....

Category: Trojan Virus | Date: 7th February 2023
If Your Computer System Take Much More Time, Then You Should Comprehend That, Your Machine Has Been Contaminated By The Behavior:Win32/Locky.gen!B!ram Trojan Virus. Behavior:Win32/Locky.gen!B!ram Is An Insecure Computer Program. Behavior:Win32/Locky.gen!B!ram Has Been Designed By The....

Category: Trojan Virus | Date: 6th February 2023
"Trojandownload:js.vdehu.a" is a type of Trojan virus that is designed to infect a computer and download additional malware. This type of Trojan virus can spread through various means, such as through infected email attachments, compromised websites, or malicious downloads. Once a computer is....

Category: Trojan Virus | Date: 6th February 2023
Torpig, also known as Sinowal or Anserin, is a type of Trojan virus that is designed to steal personal information, such as passwords and credit card numbers, from infected computers. This Trojan virus can infect a computer through various methods, such as through infected email attachments,....

Category: Trojan Virus | Date: 6th February 2023
The "TiWorker.exe" file is a component of the Windows operating system and is typically used for background tasks and system updates. However, in some cases, a malicious file could be disguised as "TiWorker.exe" and cause harm to a computer, such as by installing additional malware, stealing....

Category: Trojan Virus | Date: 6th February 2023
A "Taskhostw.exe" Trojan is a type of malware that is disguised as the legitimate "taskhostw.exe" process, which is part of the Windows operating system. This type of Trojan virus is designed to evade detection and perform malicious actions on an infected computer, such as stealing personal....
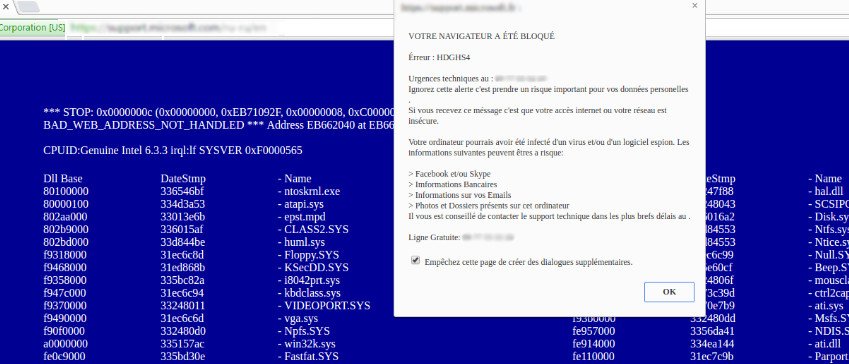
Category: Trojan Virus | Date: 4th February 2023
Cryxos Trojan Virus Is Considered As A Terrible Code, Which Will Run The Enfeeble Computer System. Cryxos Is Run With JavaScript Program. Cryxos Has Been Coded By The Cyber Goons, Which Will Annihilate The Terminal Weirdly. Cryxos Is Displaying The Alarming Message After Installed The....

Category: Trojan Virus | Date: 4th February 2023
Bitrep.A Is A Windows Based Trojan Virus Code, That May Cripple Your CPU Function, Meddler The Web Browser Function And More. Bitrep.A Trojan Virus Has Been Created By The Professional Computer Criminals. The Main Goal For Designing Of Bitrep.A To Generate The Money At Any Cost. Bitrep.A....

Category: Trojan Virus | Date: 4th February 2023
Trojan.Win32.Cromex.a Trojan Is Detected By Advance Anti-malware Software As A Virus. It Has Capability To Access Your Account Through Backdoor. The Trojan.Win32.Cromex.a Trojan Is Coded By Cyber Goons To Rip-off Internet User Through Licit Program. According To Security Experts, It Is A Very....

Category: Trojan Virus | Date: 4th February 2023
Trojan-PSW.Win32.Dybalom.L Is A Trojan Program That Can Lurk Within Another Applications. It Comes From A System Conceal Inside A Legal Application, Like Remote Server. Trojan-PSW.Win32.Dybalom.L Infections In Not Dispense All Over The World Themselves. Trojan-PSW.Win32.Dybalom.L Vicious....

Category: Trojan Virus | Date: 4th February 2023
Registry Trojan Was Present Is Detected By Advance Anti-malware Software As A Trojan Virus. It Has Capability To Access Your Account Through Backdoor. Registry Trojan Was Present Is Coded By Cyber Goons Rip-off Internet User Through Licit Program. According To Security Experts, It Is A Very....

Category: Trojan Virus | Date: 4th February 2023
GoBrut Is A Computer Botnet Program, Which Has Been Written On Go Programming Language. GoBrut Is A Pertaining With ELF (Executable And Linkable Format) Based Botnet Go Program. Today's Growing The Botnet Programming To Required Significant Information From The User Computer Details And Other....

Category: Trojan Virus | Date: 4th February 2023
Application.CoinMiner.GE Is Detected By Advance Anti-malware Software As A Trojan Virus. It Has Capability To Access Your Account Through Backdoor. Application.CoinMiner.GE Is Coded By Cyber Goons Rip-off Internet User Through Licit Program. According To Security Experts,....

Category: Trojan Virus | Date: 4th February 2023
Win32/Packed.VMProtect.ABO Is A Very Dangerous Computer File By Number Of Computer Security Experts. Win32/Packed.VMProtect.ABO Is Specially Coded For Windows Operating System. Win32/Packed.VMProtect.ABO Can Manipulate Various Other File Such As Task Manager, Registry Editor, Configuration....

Category: Trojan Virus | Date: 4th February 2023
Glupteba Is New Kind Of Trojan Virus Code, Malign Software That Downloads The System Without Any Notification. The Cyber Criminals Promote Glupteba Trojan Virus For Generating The Revenue While Stealing The Important Data. Though, Glupteba Trojan Virus Has Been Fabricated Very Notorious Way To....

Category: Trojan Virus | Date: 4th February 2023
Hacktool:Win32/Gendows Is New Type Of Trojan Virus Code To Propagate Unwanted Application As Well As Strange Web Links. Hacktool:Win32/Gendows Has Been Used By The Hacker To Engaged The Victim’s Computer System And Steal Personal Information As Well As The Financial Data. By The Help Of....

Category: Trojan Virus | Date: 4th February 2023
Trojan.BitCoinMiner Has Been Created By The Crooks For Their Financial Purpose. Trojan.BitCoinMiner Has Ability To Reside Number Of Codes, Which Is Related With Malign Program. Trojan.BitCoinMiner Is A Trojan Code And Incorporated With An Executable File, Which Is Called An....

Category: Trojan Virus | Date: 4th February 2023
TROJAN.WIN32 Looks Very Persuasive Program To Entice The Internet User. TROJAN.WIN32 Has Been Fabricated For Earning The Revenue, Which Is Completely Negative. However, TROJAN.WIN32 Trojan Virus Malware Code To Convince Other Aggressive Program Like Adware, Spyware, Ransomware, And More. No Of....

Category: Trojan Virus | Date: 4th February 2023
FakeAV.AuQD Belongs To A Notorious Trojan Virus. It Is A Kin Of Malware. FakeAV.AuQD Has Been Crafted By Some Cyber Miscreants. The Creation Of FakeAV.AuQD Is Merely For Leaking And Crippling Numbers Of Mac Machine. FakeAV.AuQD Is Contain A Stealth Character, So You Can Not Identify Manually.....

Category: Trojan Virus | Date: 3rd February 2023
Trojan.SathurBot Is Venomous Trojan Virus Application That Can Jeopardy For The Computer Security As Well As The Computer System. Trojan.SathurBot Can Obliterate The User’s File And Folders As Well As The Other Program, Which May Have Essential For The Computer System. Trojan.SathurBot Could....

Category: Trojan Virus | Date: 3rd February 2023
Trojan.Fileless.MTGen Is A Generic Trojan Virus For The Windows As Well As The Mac OS X Terminal. Trojan.Fileless.MTGen Infiltrates The Weak Computer System And Distort The Log File And Task Manager, Which Is Very Adamant To Identify This Malevolent Stuff. Trojan.Fileless.MTGen May Pretend Manifold....

Category: Trojan Virus | Date: 3rd February 2023
Trojan.FakeAV.LVT Is A Smart And Distorted Trojan Virus Program. Trojan.FakeAV.LVT Is Scanned By The Some Eminent Computer Security Experts Team And Find As A Trojan Virus Code. Trojan.FakeAV.LVT Could Deliberately Misguide The User Against The Security Status Of The Terminal Or Desktop. These....
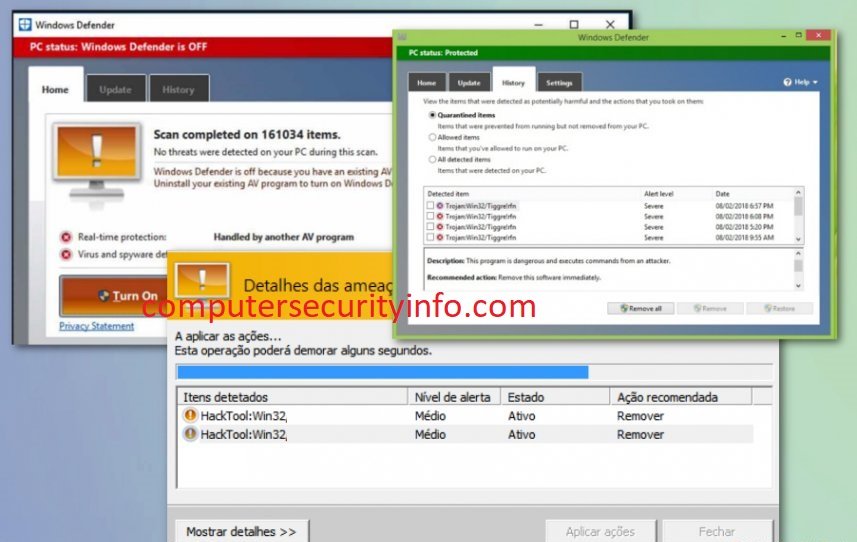
Category: Trojan Virus | Date: 3rd February 2023
HackTool:Win32/AutoKMS Is A Computer Worm, That Replicates Itself In Order To Disperse To Other System. Often HackTool:Win32/AutoKMS Uses A Computer Network To Reach Own Destination. HackTool:Win32/AutoKMS Is A Malware Program, That Can Hurt Various Significant Files, Folders, Standalone....

Category: Trojan Virus | Date: 3rd February 2023
Gen:Variant.Strictor Is A JavaScript Coded Trojan Virus Program, That Can Compromise The Several Internet Browser As Well As The Website. Gen:Variant.Strictor Is A Javascript Cryptocurrency Mining User Has Been Detected Executed By Many Web Sites, Including Steaming Audio, Video And Other Media Web....

Category: Trojan Virus | Date: 2nd February 2023
QuilMiner Is A Malicious trojan virus program. QuilMiner Is Used To Corrupt The Computer System. QuilMiner Can Corrupt Bootable Files And Registry Editor. QuilMiner May Also Pervert Music Files, Video Files And Databases Files. Your Web Browser And Other Extension Has Been Affected By The....
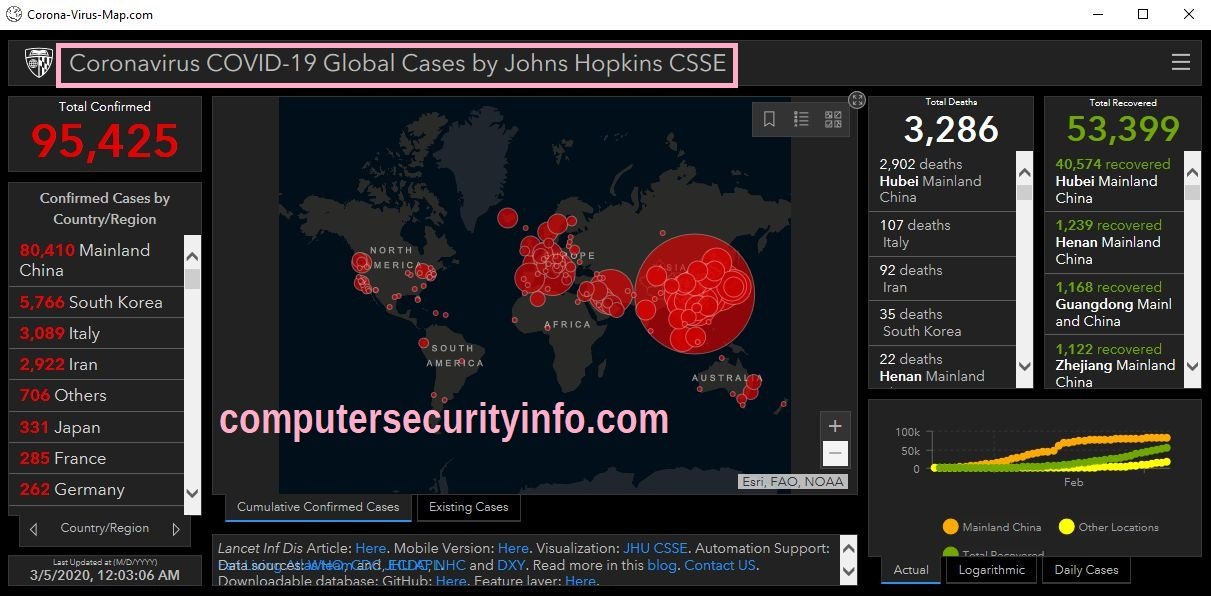
Category: Trojan Virus | Date: 29th November 2022
Corona-Virus-Map.com Seems To Be A Website Address, But In Real Condition Is Completely Different. Corona-Virus-Map.com Is A Ruthless Malign Code, Which Can Be Associated With trojan virus. The Backdoor Is The Best Name Of The Corona-Virus-Map.com. Corona-Virus-Map.com May Run As A Chain....

Category: Trojan Virus | Date: 27th November 2022
Trojan:Win32/Occamy.C Was Not A Computer Virus But Has Some Characters Pertaining With Computer Virus. Trojan:Win32/Occamy.C Is Very Unpleasant Trojan Stuff. Trojan:Win32/Occamy.C Has Been Developed To Proliferate The Other Malevolent Program. These Program Are Associated With Adware, Spyware,....

Category: Trojan Virus | Date: 27th November 2022
Trojan.Generic.KD Is A Malware Program, Which Is Categorized As A Trojan Virus Spread Via Spam Mail, Phishing Email Message That Pretends To Be A Counterfeit Notification Through Message. Trojan.Generic.KD Has Capable To Hide Itself While Firewall Could Scan The System. The Security Software May....

Category: Trojan Virus | Date: 27th November 2022
Idle Buddy Is A Terrible Trojan Horse Virus Application Program For The Computer System. IdleBuddy May Use The Compromised Computer’s Resources To Mine The Digital Currency (Bitcoin, Dash, Or Ethereum) Without Victim Consent. The Computer System’s Graphic Card, And CPU Mine By The....

Category: Trojan Virus | Date: 27th November 2022
HEUR.Trojan.Win32.Generic Is A Furtive Trojan Virus Program, That May Enter The Feeble Computer System Through Backdoor. Your Windows Registry Editor As Well As Task Manager Can Disable Due To HEUR.Trojan.Win32.Generic Trojan Virus. Moreover, The Chrome, Opera, IE, And Edge Types Web Browser Could....

Category: Trojan Virus | Date: 27th November 2022
Gen:Variant.Razy Is A Nasty Stuff That Belongs To A Trojan Virus Program. Gen:Variant.Razy May Appear In Your System As A DLL Files. Gen:Variant.Razy Can Harm The Windows Registry Editor As Well As An Operating System. However, Gen:Variant.Razy May Change The Various Default Settings But Without....
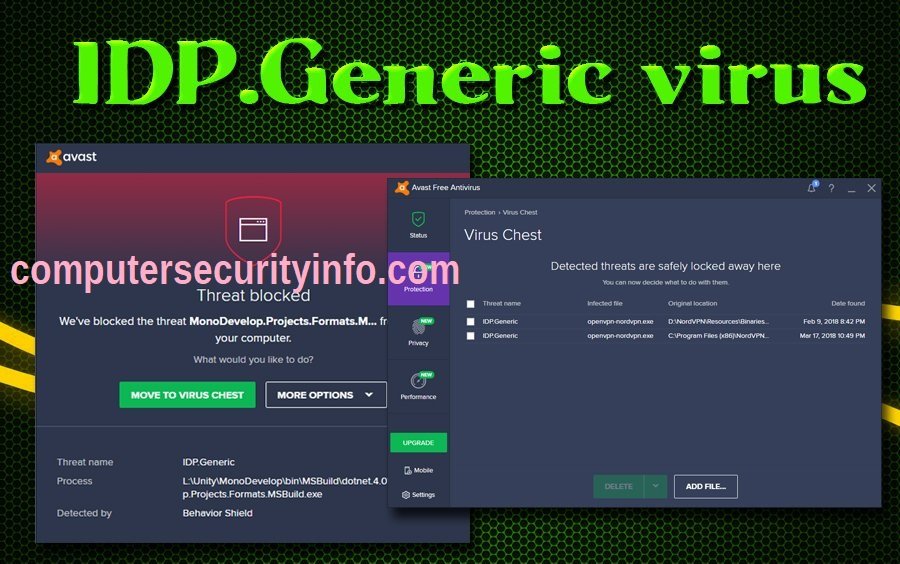
Category: Trojan Virus | Date: 27th November 2022
The Heuristic Malware Program Is Called A IDP.Generic Trojan Virus, That Can Cripple The Registry Editor Appallingly. The Task Manager, Browser Function, CPU Speed, And Data Transfer Are Inadequately Affected By The IDP.Generic Trojan Virus. However, IDP.Generic Trojan Virus Block The Files, Small....
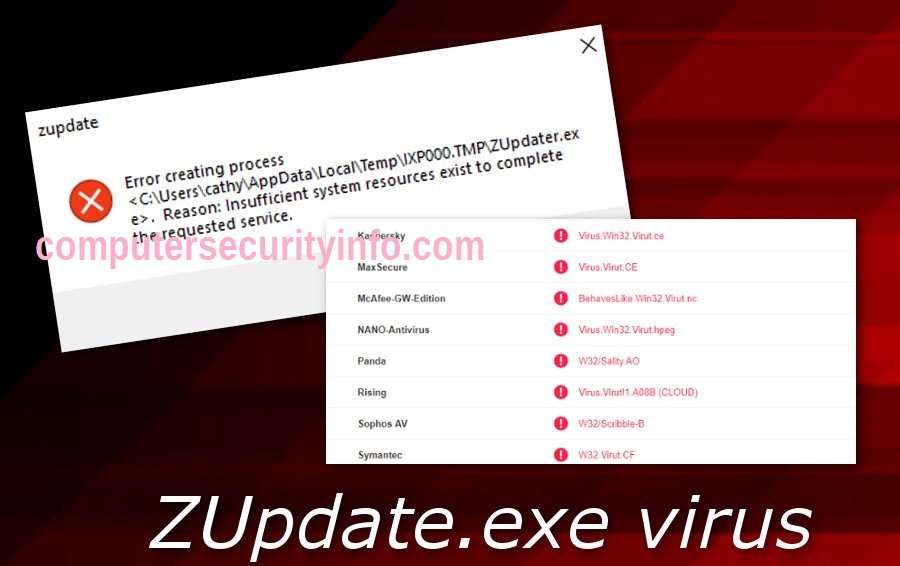
Category: Trojan Virus | Date: 26th November 2022
Zupdater.exe Was Not Coincidently Integrated With Various Malign Program. Zupdater.exe Will Reach The Terminal Through Backdoor, While User Can’t Comprehend. Zupdater.exe Is An Asserted As A Trojan Virus Program. Zupdater.exe Is A Spread Bundled Of Software. Zupdater.exe Will Promote....

Category: Trojan Virus | Date: 26th November 2022
A Malevolent Program Is Scanned By The Heuristics Detection Method, That Is A Trojan:Win32/Zpevdo.A Trojan Virus. Trojan:Win32/Zpevdo.A Is A Great Threat Of The Windows OS Based System. Trojan:Win32/Zpevdo.A May Theft The Crucial Data From The Compromise Computer Terminal.....
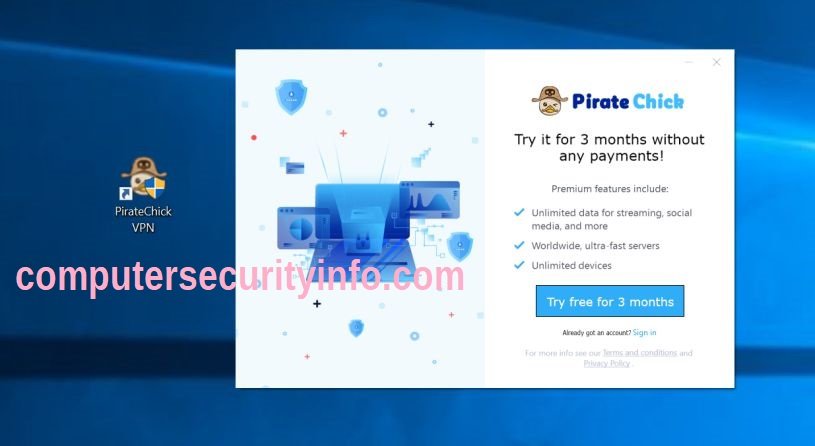
Category: Trojan Virus | Date: 26th November 2022
Pirate Chick VPN Is A Bitter Trojan Virus Code That Professes To Be A Legal VPN Service. Once Pirate Chick VPN Installed In Your Computer System, Then Your Registry Editor Will Show The Malfunction. Regrettably, Freeware And Shareware Downloads Do Not Completely Disclose That Other Suspicious....

Category: Trojan Virus | Date: 26th November 2022
The Vicious trojan virus Is Active In Your Computer System, While User Could Accidentally Enable The Strange Web Links. The Name Of The Trojan Virus Is TR/Crypt.XPACK.GenERIF. TR/Crypt.XPACK.GenERIF Will Target The Weak As Well As Unguarded Computer Terminal. TR/Crypt.XPACK.GenERIF May....

Category: Trojan Virus | Date: 26th November 2022
MatchPop Is A Very Unique Name Of The trojan virus program. MatchPop Will Start Interruption If You Can Help To Enter The Terminal. If Your Firewall As Well As Security Software Does Not Work Well, That Means Your System Has Been Infected By The MatchPop Trojan Virus. MatchPop Is Pertaining With....

Category: Trojan Virus | Date: 25th November 2022
Winlog.exe Is An Executable File, That Is Pertaining With Windows Control. The Cyber Criminal May Create A Same File Name, And Try To Run Winlog.exe Executable File Through Backchannel And Corrupt The Real File. Winlog.exe Is A Very Sensitive File That Can Work While User May Visit The Windows....
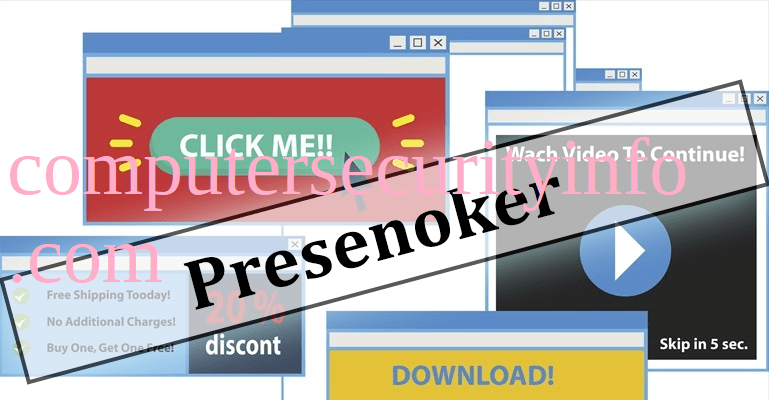
Category: Trojan Virus | Date: 14th July 2022
PUA:Win32/Presenoker Is A New Kind Of Trojan Virus, Which Is Pertaining With Malware Family. PUA:Win32/Presenoker Is Working As A Heuristic Detection Coded To Generically Scanned A Potentially Intrusive Application. PUA:Win32/Presenoker Is A Very Treacherous Code That Contains Adware, Browser....
Category: Trojan Virus | Date: 7th July 2022
Trojan:Win32/CryptInject!ml Is A Trojan Virus Program, That Pertaining With Malware Family. Trojan:Win32/CryptInject!ml Is A Nasty As Well As Dreadful Program To Annihilate The computer System File. Trojan:Win32/CryptInject!ml Has Been Created By The Cyber Criminal To Target The Innocent....

Category: Trojan Virus | Date: 15th June 2022
Win32:FunWeb-K [PUP] Is A Stubborn Trojan Virus. Win32:FunWeb-K [PUP] Will Be Access The System Without Presence In The Public Domain. There Are Lot Of Hoax Advertisements Associated With That Malicious Code. Win32:FunWeb-K [PUP] Has Been Created By The Criminal For Their Own Intend.....
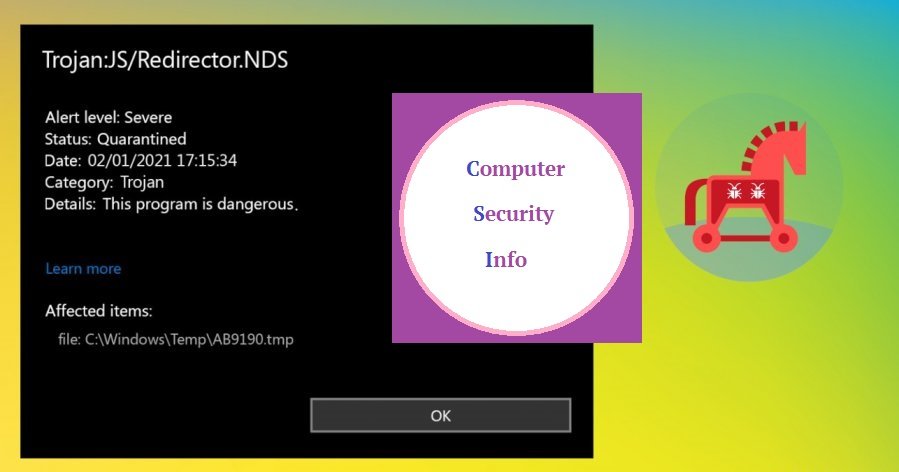
Category: Trojan Virus | Date: 31st May 2022
JS/Redirector.NDS Is A Dreadful Detection As Well As The Fabricated To Normally Find A Potentially Unwanted Trojan Virus Application. JS/Redirector.NDS Is A Treacherous Trojan Virus Code To Manipulate The Computer Boot Files And Function. JS/Redirector.NDS May Change The register Editor....
Category: Trojan Virus | Date: 9th May 2022
Backdoor.Win32.Miancha Is A Nasty Backdoor Trojan Virus, That Is Distributing Code As Part Of The Counterfeit Modifying For The GOM Player Program. Backdoor.Win32.Miancha Is Installed In A Japanese Nuclear Power Plant Due To Employee’s Recklessness Or Laxity. Backdoor.Win32.Miancha Is A Big....

Category: Trojan Virus | Date: 9th May 2022
Mekotio Banking Trojan Is A Very Unique Trojan Virus Program To Infiltrate The Banking System. Mekotio Banking Trojan Will Spread Various Types Of Reckless Code And Web Links To Annihilate The Unwanted Program. The Trojan Virus Will Apply Dubious Kind Of Method To Delude The User And Infected....

Category: Trojan Virus | Date: 9th May 2022
win32/floxif.h Is A Very Malign Trojan Based Virus Program That Can Influence The Windows Operating System. How To Remove Win32/floxif.h trojan Virus From The Windows Operating System Base Terminal? Win32/floxif.h Seems To Be Perilous Virus Program That Often Fix Itself To Distinguish....

Category: Trojan Virus | Date: 26th February 2022
A Trojan Virus Is An Unauthorized Program That Perform Functions Strange By The User. A Trojan Virus Typically Gets Installed Automatically Along With A Contaminated Legitimate Application Or Code, That Is, A Legal Program That Has Been Updated By The Placement Of Unauthorized Code Within It. Once....