 Category's Page
Category's Page

Category: Ransomware | Date: 18th February 2026
Introduction Osiris Ransomware is a well-known strain of crypto-ransomware that emerged in late 2016 as a variant of the infamous Locky Ransomware family. It quickly became one of the most widespread and destructive ransomware campaigns of its time, targeting businesses, healthcare institutions,....
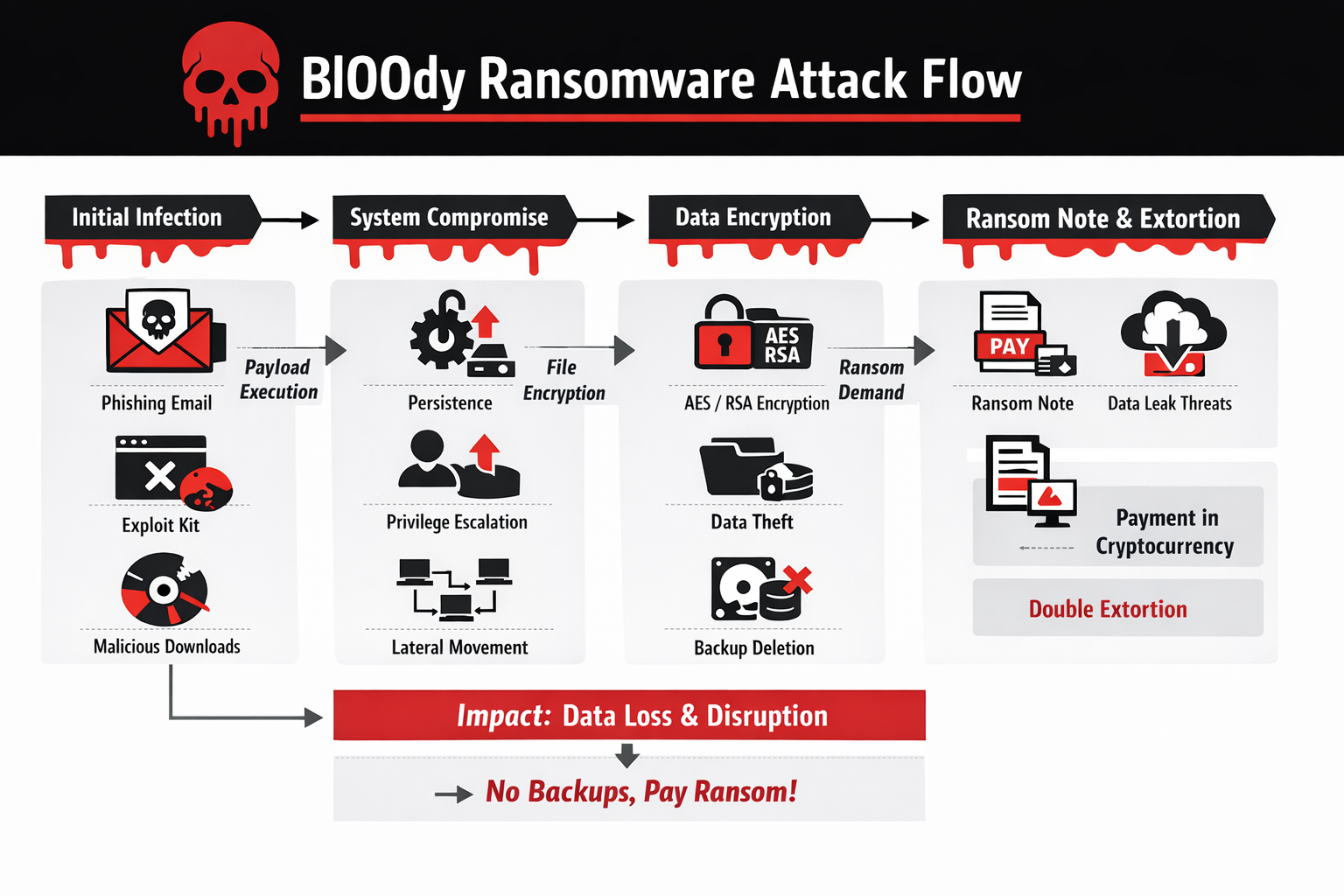
Category: Ransomware | Date: 27th January 2026
Bl00dy ransomware is an emerging strain of crypto-ransomware that has gained attention in the cybersecurity community due to its aggressive encryption techniques, stealthy infiltration methods, and increasing use in targeted cybercrime campaigns. Like other modern ransomware families, Bl00dy is....

Category: Ransomware | Date: 2nd January 2026
Makop Ransomware is a malicious encryption malware that has been actively targeting Windows computers and organizations worldwide since about 2020. A variant of the Phobos ransomware family, it has evolved into a serious cyber threat — especially in regions like India, where recent studies....
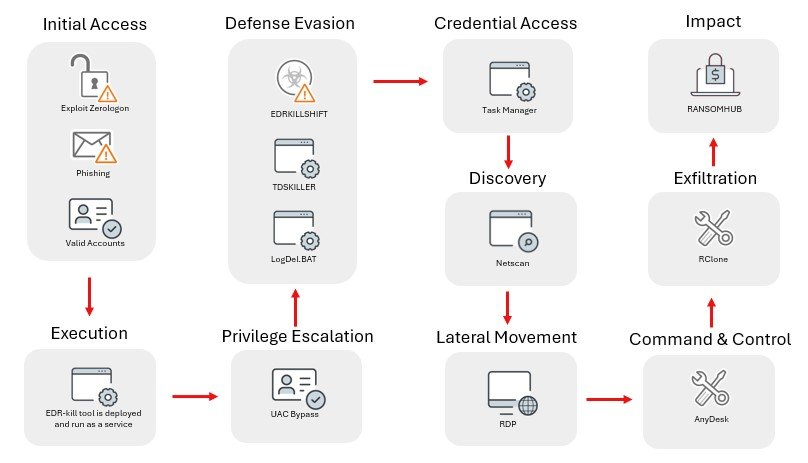
Category: Ransomware | Date: 30th December 2025
RansomHub ransomware including behavior, infection methods, indicators of compromise (IOCs), known malware hashes, and known IP addresses associated with it. This is crucial information for threat analysts, incident responders, and defenders. All information below is drawn from reputable threat....
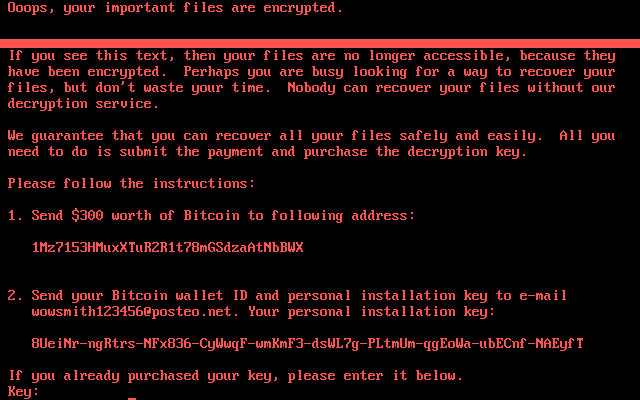
Category: Ransomware | Date: 3rd November 2025
Introduction In the ever-evolving landscape of cyber-threats, ransomware remains one of the most formidable risks to organisations and individuals alike. Among the latest entrants in this arena is the ransomware variant known as Nobody Ransomware (also stylised as NOBODY ransomware). First....
Category: Ransomware | Date: 22nd October 2025
Kyber Ransomware is a dangerous malware strain that encrypts personal and system files, rendering them inaccessible until a ransom is paid. It spreads through phishing emails, cracked software, malicious links, and compromised websites. Once executed, Kyber scans your device for valuable data and....
Category: Ransomware | Date: 22nd October 2025
Trap Ransomware is a malicious program designed to lock your files and demand payment for their release. Once it infiltrates your system—often through phishing emails, malicious downloads, or infected websites—it encrypts personal documents, images, and databases, rendering them....
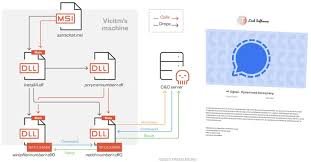
Category: Ransomware | Date: 31st July 2025
RomCom RAT ransomware is a stealthy cyber threat targeting global organizations through fake websites and malicious apps. Learn how it works, its recent campaigns, and how to protect your data. What is RomCom RAT? RomCom RAT (Remote Access Trojan) is a sophisticated malware strain used primarily....
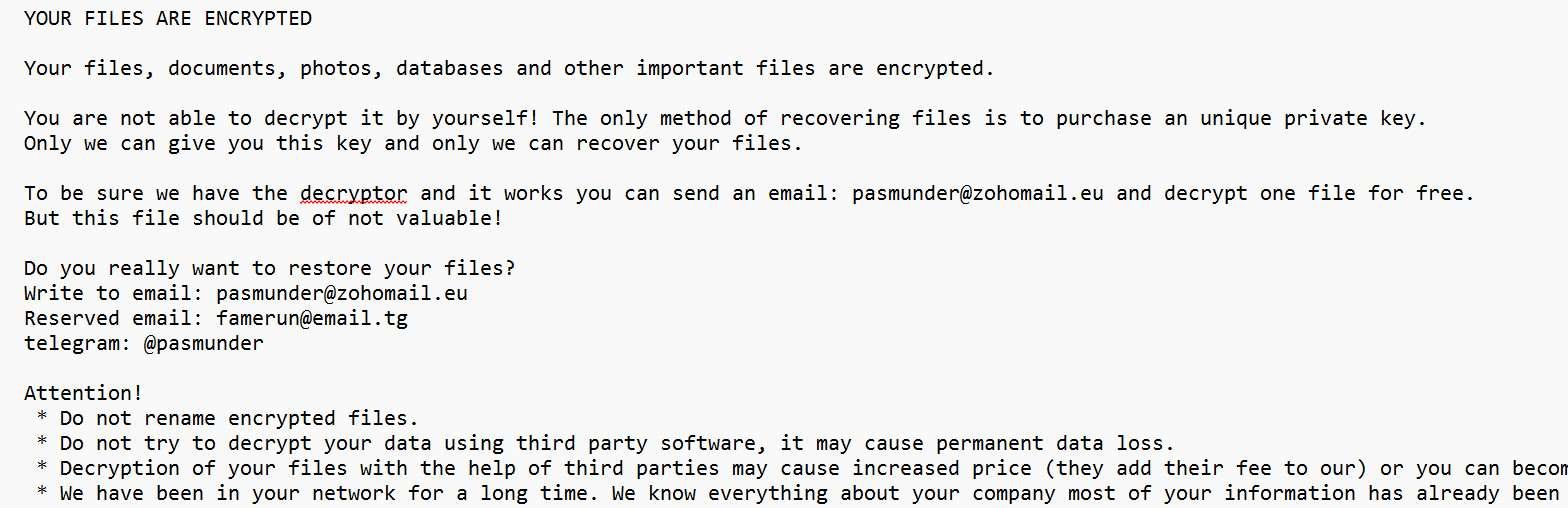
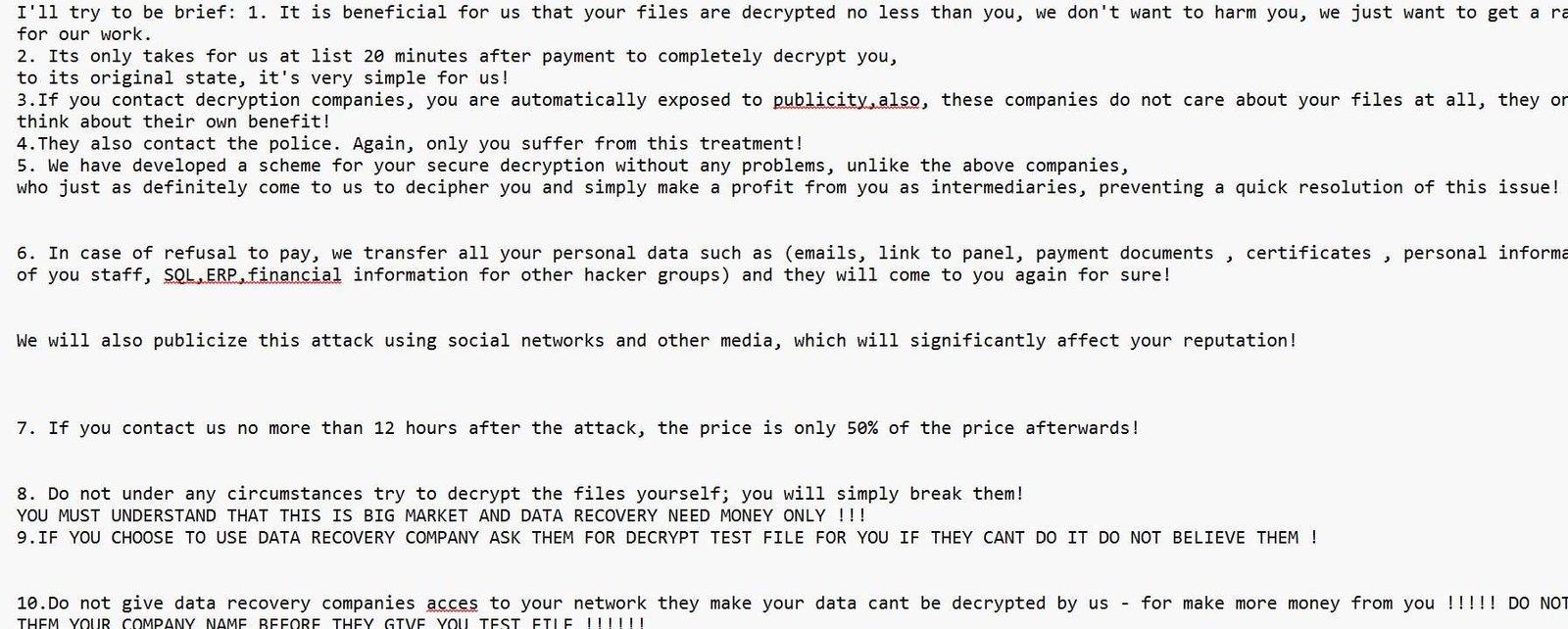
Category: Ransomware | Date: 29th July 2025
Discover how Hush ransomware operates, its stealthy tactics, and how to protect your business or personal data from this dangerous new malware variant. What Is Hush Ransomware? Hush ransomware is a stealthy and rapidly growing ransomware strain that has emerged as a major cybersecurity threat in....
Category: Ransomware | Date: 29th July 2025
Learn everything about Boramae ransomware—how it infects systems, encrypts data, and how to protect your business from this rising cyber threat in 2025. What Is Boramae Ransomware? Boramae ransomware is a new and highly evasive malware variant that has recently emerged in global cybercrime....
Category: Ransomware | Date: 29th July 2025
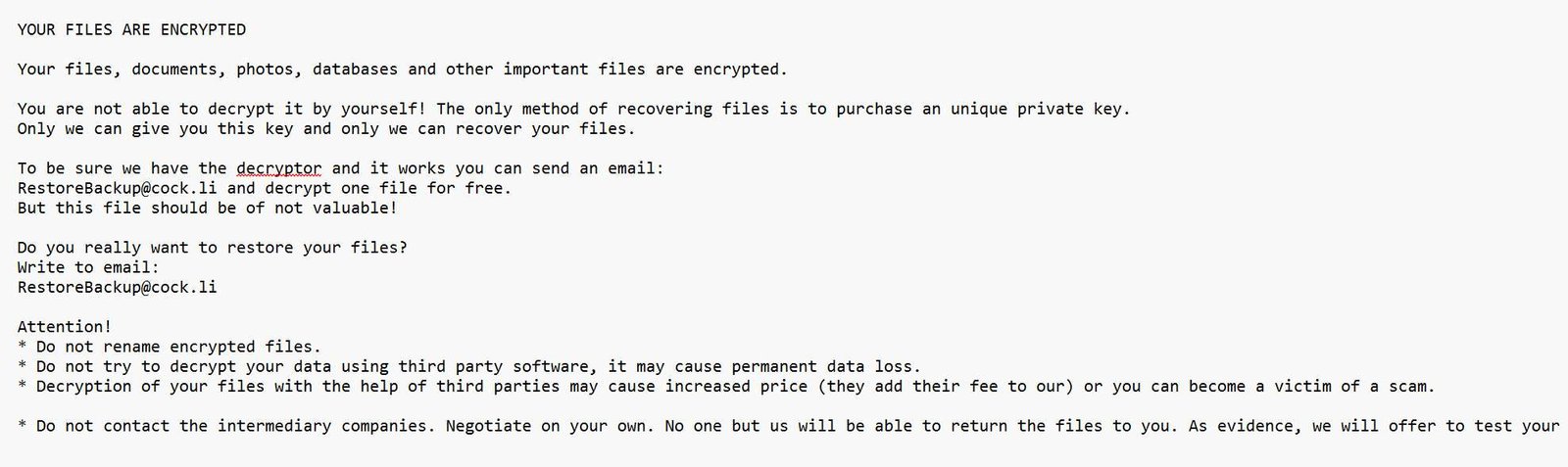
Learn everything about RestoreBackup ransomware—how it spreads, its impact, and actionable tips to prevent and recover from this rising cyberattack threat. What is RestoreBackup Ransomware? RestoreBackup ransomware is a new and dangerous malware strain designed to encrypt valuable files and....
Category: Ransomware | Date: 29th July 2025
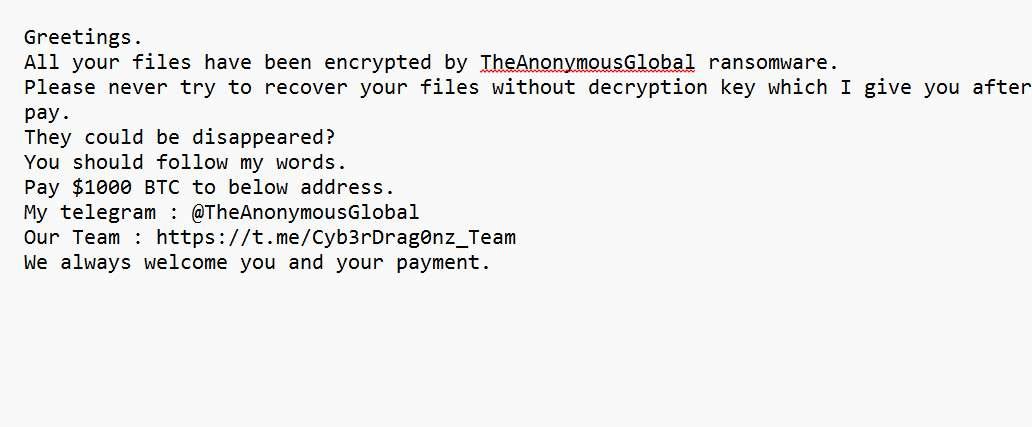
Discover what TheAnonymousGlobal ransomware is, how it works, and essential steps to prevent infection. Learn how this new cyber threat is affecting organizations worldwide. What Is TheAnonymousGlobal Ransomware? TheAnonymousGlobal ransomware is a newly emerging cyber threat making headlines for....
Category: Ransomware | Date: 27th July 2025
In the digital age, hospitals and healthcare institutions rely heavily on computer systems to manage patient care, records, diagnostics, billing, and more. This dependence, while increasing efficiency and accuracy, also exposes them to cyber threats. One such alarming incident took place at the All....
Category: Ransomware | Date: 27th July 2025
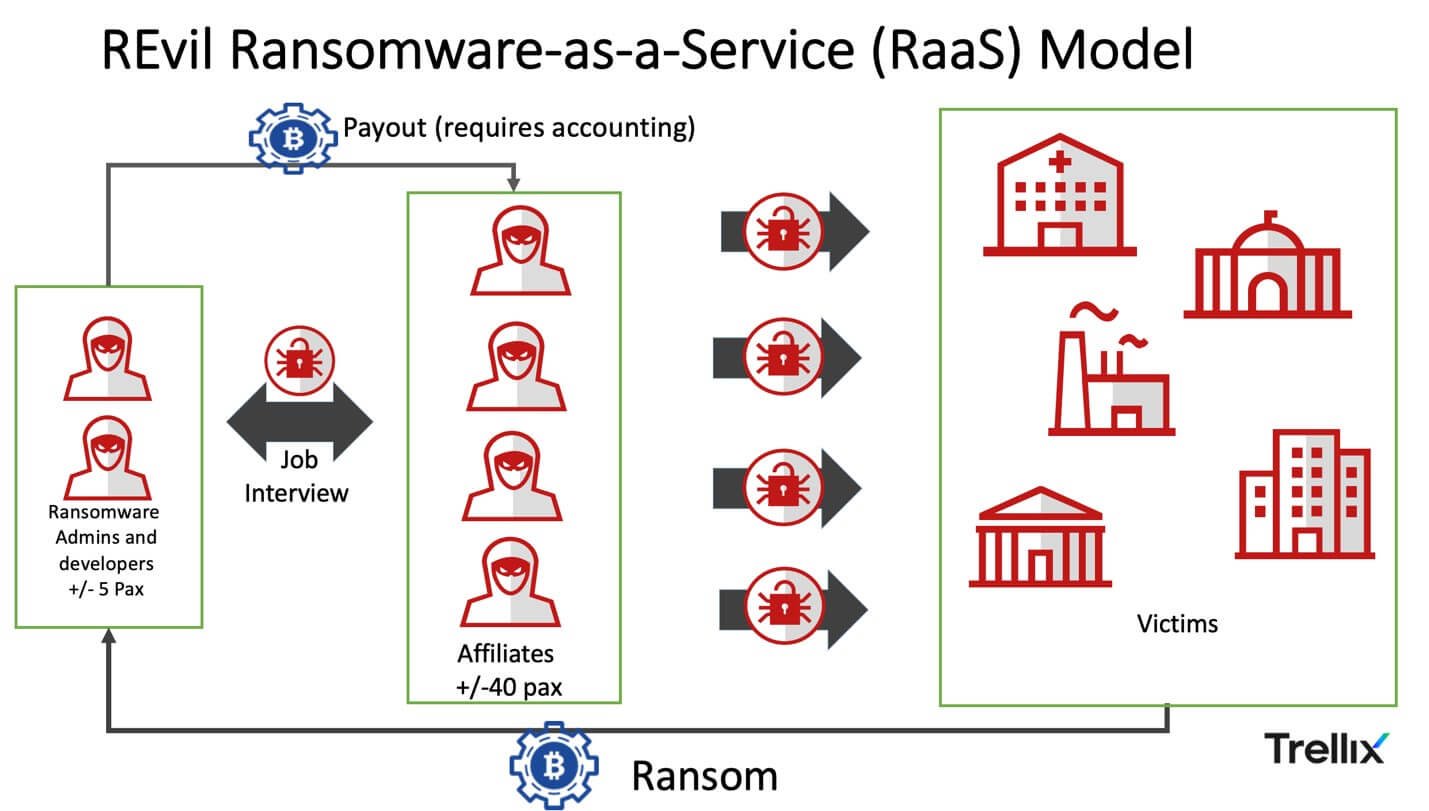
In today’s digital world, ransomware attacks have become one of the most dangerous and disruptive cyber threats targeting individuals, businesses, and critical institutions alike. Among the many ransomware strains, REvil (also known as Sodinokibi) has gained infamy for its sophisticated....

Category: Ransomware | Date: 31st May 2025
What is Dance of the Hillary? Dance of the Hillary is a form of ransomware that infects Windows-based systems. Once installed, it encrypts important user files and demands a ransom in exchange for the decryption key. Named unusually, possibly as a reference or satire, it functions similarly to....

Category: Ransomware | Date: 31st May 2025
What is KillSec? KillSec is a malicious cyber threat group or malware strain known for launching destructive cyberattacks. The term “KillSec” often refers to a group associated with hacktivism and cyber disruption. KillSec malware is designed to compromise systems, exfiltrate data, and....
Category: Ransomware | Date: 31st May 2025
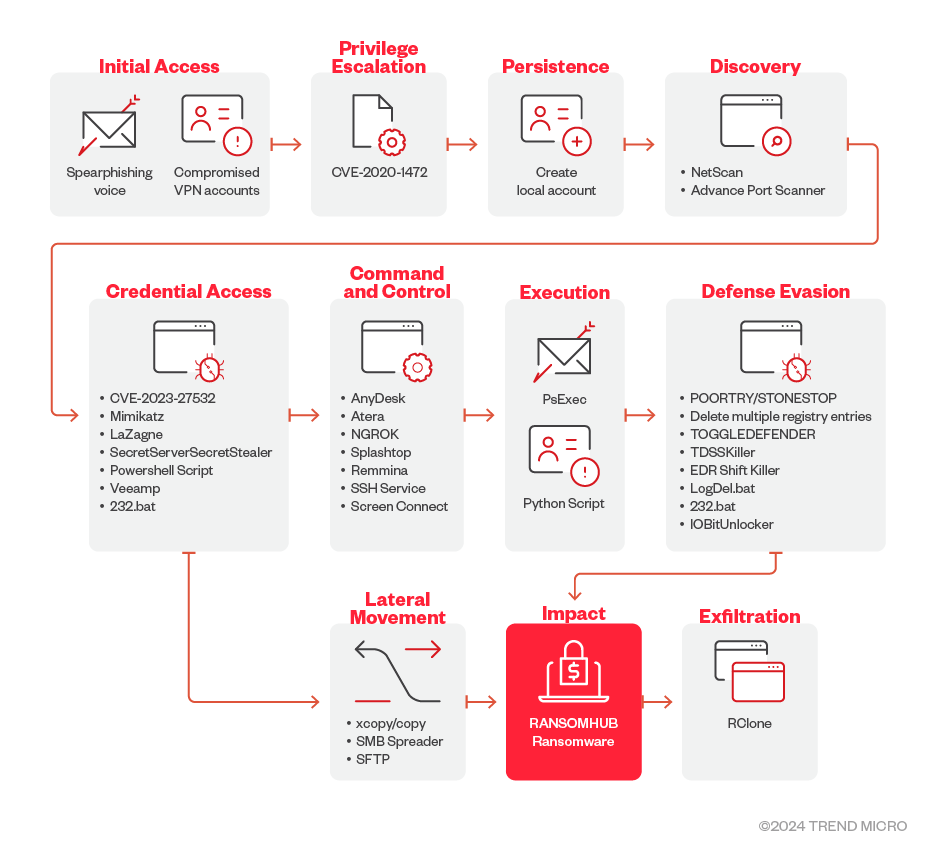
What is RansomHub? RansomHub is a Ransomware-as-a-Service (RaaS) operation that encrypts a victim's files and demands a ransom payment in exchange for a decryption key. It emerged in early 2024 and has quickly become prominent due to its affiliate-based model, allowing other cybercriminals to....

Category: Ransomware | Date: 30th May 2025
? What is LockBit 3.0 Ransomware? LockBit 3.0, also known as "LockBit Black", is the third major variant of the infamous LockBit ransomware family. Released in mid-2022 and still active in 2025, it is a highly sophisticated, modular ransomware used by affiliates under a Ransomware-as-a-Service....

Category: Ransomware | Date: 2nd May 2025
What is FMLN Ransomware? FMLN Ransomware is a type of malicious software designed to encrypt files on a victim’s computer, rendering them inaccessible until a ransom is paid. Named "FMLN" likely as a disguise or to mislead, it typically spreads via phishing emails, malicious downloads, or....
Category: Ransomware | Date: 22nd April 2025
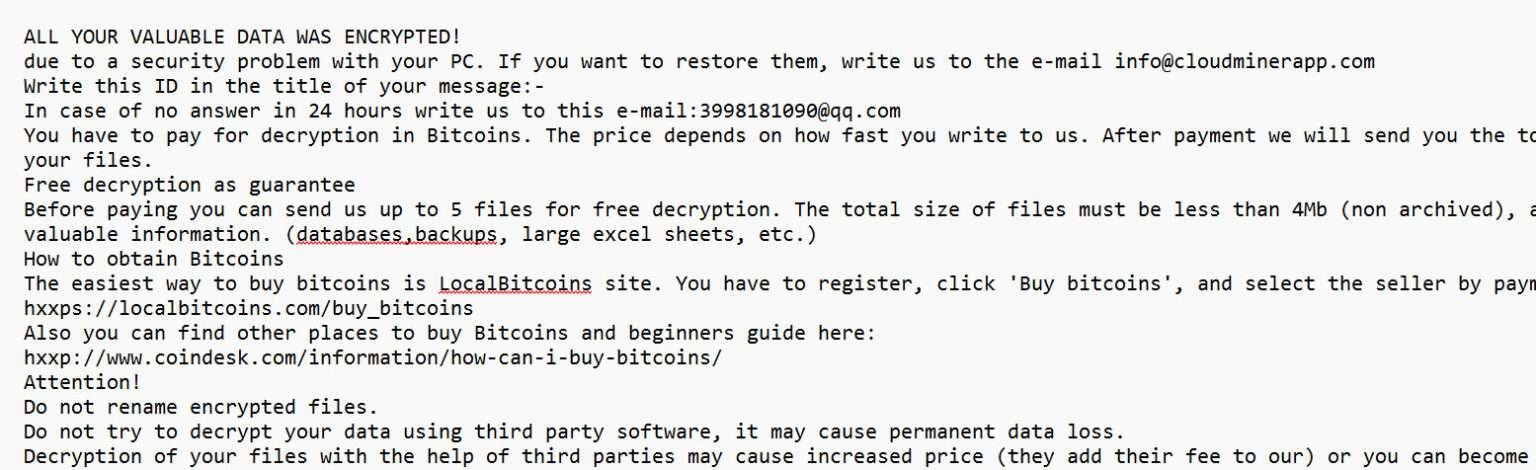
Overview of the JETT Ransomware JETT ransomware is a type of malicious software designed to encrypt files on a victim’s computer and demand a ransom payment in exchange for a decryption key. It typically infiltrates systems through phishing emails, malicious attachments, or vulnerabilities....
Category: Ransomware | Date: 22nd April 2025
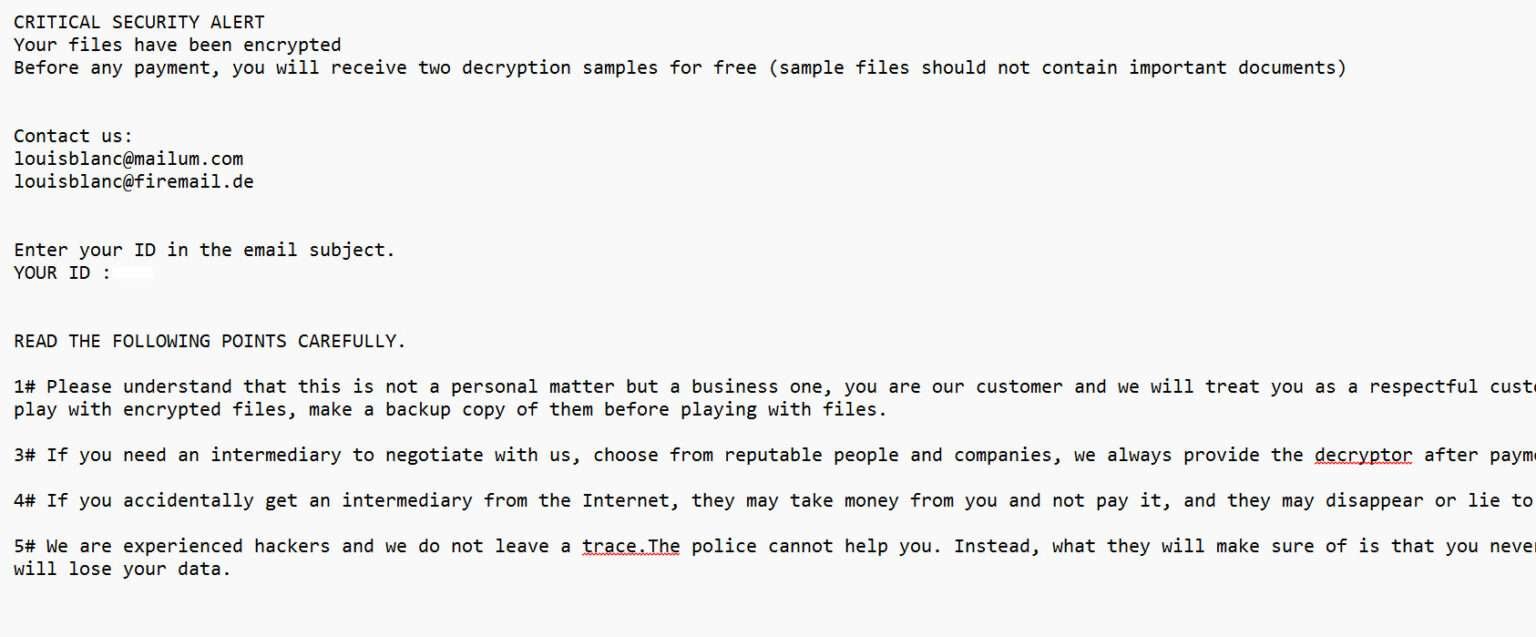
Overview of Louis ransomware Louis ransomware is a malicious software strain designed to encrypt files on infected systems and demand payment for their decryption. First detected in mid-2021, it typically spreads through phishing emails, malicious attachments, or cracked software downloads. Once....
Category: Ransomware | Date: 18th April 2025
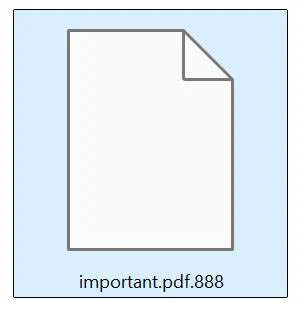
888 Ransomware: What You Need to Know Cybersecurity threats continue to evolve, and one of the latest ransomware strains making headlines is 888 Ransomware. This malicious software encrypts files on infected systems and demands a ransom in exchange for decryption, posing a serious risk to....

Category: Ransomware | Date: 16th April 2025
What is Nullhexxx Ransomware? Nullhexxx ransomware is a type of malicious software that encrypts a victim’s files and demands a ransom for decryption. Typically spread through phishing emails, malicious attachments, or compromised websites, Nullhexxx Ransomware targets personal and business....

Category: Ransomware | Date: 29th February 2024
A comprehensive examination of Lkhy has revealed its malicious intent as a dangerous form of malware meticulously designed to encrypt victims' data. Lkhy Ransomware insidious program falls under the category of ransomware, a type of malware infamous for its extortion tactics. The primary goal of....

Category: Ransomware | Date: 7th February 2024
CDWE Ransomware is a type of malicious software designed to encrypt files on a victim's computer and demand a ransom payment for their decryption. Like other ransomware variants, CDWE encrypts files using strong cryptographic algorithms, making them inaccessible to the victim until a decryption key....

Category: Ransomware | Date: 7th February 2024
CDTT Ransomware is a malicious software program designed to encrypt files on a victim's computer and demand a ransom payment for their release. CDTT Ransomware type of malware is classified as ransomware, a form of cyber attack that has become increasingly prevalent in recent years. CDTT....

Category: Ransomware | Date: 7th February 2024
Your personal files could be in jeopardy as the infamous STOP/DJVU ransomware resurfaces with a fresh variant that encrypts images, documents, and crucial files on compromised systems. This new iteration adds the ".CDPO" extension to encrypted file names, rendering them unreachable. Upon....

Category: Ransomware | Date: 7th February 2024
If you find that you're unable to open files and notice the addition of the ".LPER" extension to them, it's probable that your system has been infected with this malicious ransomware. LPER represents a malicious ransomware infection designed to encrypt files, thereby restricting access to vital....

Category: Ransomware | Date: 6th February 2024
ESSY Ransomware assaults have surged, causing widespread damage and extracting funds from victims worldwide. Among the latest threats is ESSY ransomware, a new variant that encrypts personal files on compromised devices, blocking access until a ransom is remitted. This comprehensive guide offers....

Category: Ransomware | Date: 6th February 2024
The surge of KVIP ransomware attacks continues to escalate, causing widespread harm and demanding payments from victims worldwide. Among the latest threats is the emergence of KVIP ransomware, a particularly pernicious variant. KVIP Ransomware malicious cyber assault encrypts crucial personal files....

Category: Ransomware | Date: 20th January 2024
In the month of December, there were 334 ransomware attacks, and the ongoing ALPHV shutdown saga remained a focal point. In our previous month's recap, we discussed the offline status of ALPHV's infrastructure, sparking widespread speculation about potential law enforcement involvement. However, as....
Category: Ransomware | Date: 4th January 2024
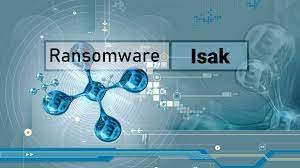
Beware, your private files could be in jeopardy as the infamous STOP/DJVU ransomware has resurfaced with a fresh variant targeting images, documents, and vital data on compromised systems. The updated version appends the ".ISAK" extension to encrypted files, rendering them unattainable. Following....

Category: Ransomware | Date: 19th December 2023
Your personal files might be at risk as the infamous STOP/DJVU ransomware has returned with a new variant. GYCC version encrypts crucial files, including images and documents, on compromised computers and adds the ".GYCC" extension to the filenames, making them unattainable. Upon infection, the....

Category: Ransomware | Date: 19th December 2023
Your personal files could be at risk as the infamous STOP/DJVU ransomware has returned with a new variant. GYZA version encrypts crucial files, including images and documents, on compromised computers and adds the ".GYZA" extension to the filenames, making them unattainable. Upon infection, the....

Category: Ransomware | Date: 19th December 2023
JAZI signifies a file-encrypting ransomware infection that restricts access to various data types, including documents, images, and videos, by encrypting files with the ".JAZI" extension. Subsequently, it endeavors to extort money from victims by demanding a ransom in Bitcoin cryptocurrency in....

Category: Ransomware | Date: 19th December 2023
Your personal files might be in jeopardy as the infamous STOP/DJVU ransomware has returned with a new variant. JAWR version encrypts crucial files, including images and documents, on compromised computers, and adds the ".JAWR" extension to the filenames, making them unattainable. Upon infection,....

Category: Ransomware | Date: 19th December 2023
Your personal files could be in jeopardy as the infamous STOP/DJVU ransomware has resurfaced with a new variant. NBWR Ransomware version encrypts crucial files, including images and documents, on compromised computers, and adds the ".NBWR" extension to the filenames, making them unattainable. Upon....

Category: Ransomware | Date: 19th December 2023
Your personal files might be in jeopardy as the infamous STOP/DJVU ransomware has returned with a new variant. NBZI ransomware version encrypts crucial files, including images and documents, on compromised computers, and adds the ".NBZI" extension to the filenames, making them unattainable. Upon....

Category: Ransomware | Date: 19th December 2023
Your personal files could be at risk as the infamous STOP/DJVU ransomware has resurfaced with a new variant. HHAZ Ransomware version encrypts crucial files, including images and documents, on compromised computers, and adds the ".HHAZ" extension to the filenames, making them unattainable. Upon....

Category: Ransomware | Date: 19th December 2023
Your private files might be at risk as the infamous STOP/DJVU ransomware has resurfaced with an updated variant. HHUY Ransomware version encrypts critical files, including images and documents, on compromised computers, and adds the ".HHUY" extension to the filenames, making them....

Category: Ransomware | Date: 19th December 2023
Your private files could be at risk as the infamous STOP/DJVU ransomware has resurfaced with an updated version. LJAZ Ransomware variant encrypts essential files, including images and documents, on compromised computers. In this recent iteration, it adds the ".LJAZ" extension to the filenames of....
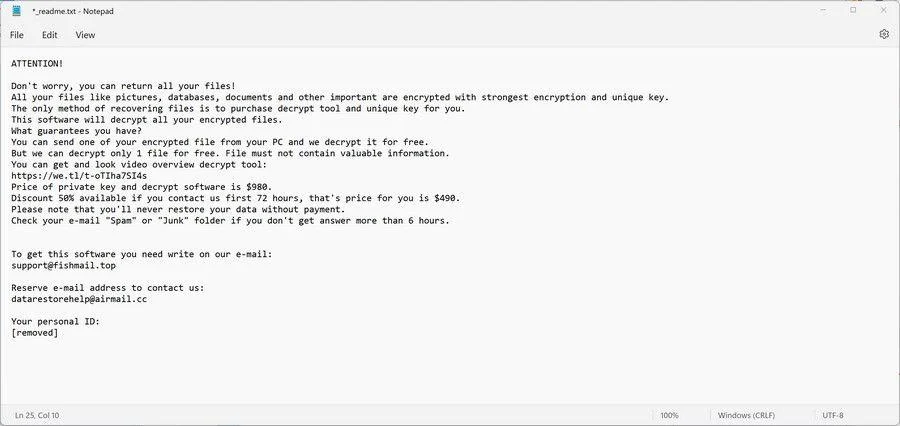
Category: Ransomware | Date: 18th December 2023
Your private files could be in jeopardy as the infamous STOP/DJVU ransomware has resurfaced with a fresh variant that encrypts critical files, including images and documents, on compromised computers. The most recent iteration adds the ".LJUY" extension to the filenames of the encrypted files,....

Category: Ransomware | Date: 14th December 2023
Scientists have discovered a novel form of ransomware called Blackoutware. This malicious threat is designed to encrypt data on compromised devices, forcing individuals to pay a ransom in exchange for the decryption key. After infiltrating a device, Blackoutware secures the files stored on it.....

Category: Ransomware | Date: 29th November 2023
The IMI Ransomware is a newly identified data-locking Trojan, recently discovered by malware researchers. Upon examination, it was revealed to be a variant of the infamous Dharma Ransomware. The Dharma Ransomware family, ranking as the second most active IMI Ransomware family in 2019, has....

Category: Ransomware | Date: 29th November 2023
C3RB3R is classified as a type of ransomware, a malicious software threat designed specifically to encrypt data and demand ransom payments in exchange for decryption. This particular ransomware, C3RB3R, follows the common ransomware practice of altering filenames of encrypted files. It employs one....

Category: Ransomware | Date: 22nd November 2023
Examination of the Yzqe malware threat has verified its classification as ransomware. Similar to other ransomware types, Yzqe is designed to encrypt files on a victim's computer, rendering them inaccessible. In the case of Yzqe, it appends the '.yzqe' extension to the original filenames of....

Category: Ransomware | Date: 21st November 2023
The Barboza Ransomware, a member of the AES-Matrix Ransomware family, is a file-locking Trojan that can permanently prevent the opening of documents and other media. To safeguard their files, Windows users are advised to maintain proper backups. Most anti-malware or PC security suites are equipped....

Category: Ransomware | Date: 21st November 2023
The CALVO Ransomware is a new addition to the notorious Phobos Ransomware family. Despite lacking significant improvements or alterations in comparison to other Phobos Ransomware variants, CALVO Ransomware can effortlessly lock users out of their computers by encrypting stored files with an....
Category: Ransomware | Date: 21st November 2023
The Globe3 Ransomware belongs to the Globe Ransomware family and draws inspiration from the popular movie 'The Purge.' This variant employs a ransom note and desktop picture themed after the movie, appending the extension '.purge' to each affected file during the attack. Functioning as a typical....
Category: Ransomware | Date: 21st November 2023
The 'Better_Call_Saul' Ransomware is a type of ransomware Trojan that encrypts the victim's files, demanding a ransom of $1000 AU for the restoration of access to the encrypted files. A notable concentration of 'Better_Call_Saul' Ransomware infections has been observed in Australia. What....

Category: Ransomware | Date: 21st November 2023
The KimcilWare Ransomware is an encryption ransomware Trojan that has recently been employed to target Magento shops. The administrators of Magento have raised concerns about the KimcilWare Ransomware, identifying it as a variant of the typical encryption ransomware Trojan. Similar to other threats....

Category: Ransomware | Date: 21st November 2023
The Invisible Empire Ransomware is a ransomware Trojan currently circulating on the Dark Web. It represents a recent iteration of the Jigsaw Ransomware, a threat that emerged just a few weeks prior. Remarkably, there are minimal distinctions between the Invisible Empire Ransomware and its....

Category: Ransomware | Date: 21st November 2023
The Dr. Fucker Ransomware represents a recent iteration of the Samas or SamSam Ransomware, a recognized encryption ransomware Trojan. Notably, the Dr. Fucker Ransomware demonstrates enhanced efficacy in evading security software and infiltrating networks. It incorporates superficial modifications,....
Category: Ransomware | Date: 21st November 2023
The Barrax Ransomware is part of the extensive lineage of HiddenTear, an open-source ransomware engine initially released in 2015 for purported 'educational purposes.' Regrettably, since its public release, HiddenTear has served as the foundation for numerous threats, and the Barrax Ransomware is....

Category: Ransomware | Date: 21st November 2023
The AES-Matrix Ransomware was initially detected by PC security researchers on July 7, 2017. It appears to have connections to an earlier ransomware Trojan called the GruxEr Ransomware, which was first identified in May 2017. Throughout 2017, there has been a notable surge in encryption ransomware....
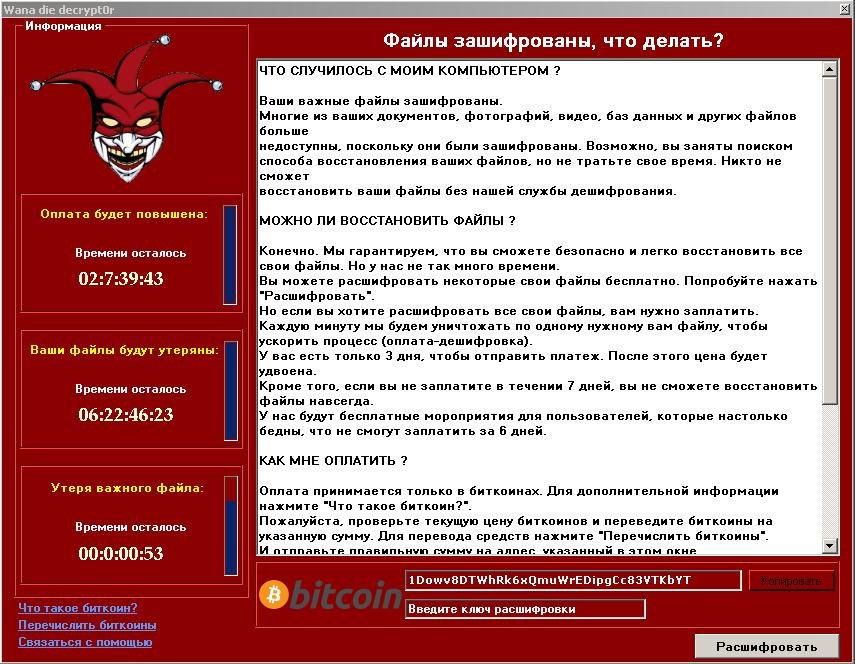
Category: Ransomware | Date: 21st November 2023
The WannaDie Ransomware represents a malicious encryption ransomware Trojan, strategically crafted to hold victims' files hostage by employing a robust encryption algorithm. This insidious malware encrypts the files of its targets and subsequently demands a ransom payment in exchange for the....

Category: Ransomware | Date: 14th November 2023
The Elantra Ransomware has emerged as a perilous new malware detected in the cybersecurity landscape. Despite being identified as a variant within the established Matrix Ransomware family by the information security community, its destructive potential remains significant. Upon infection, Elantra....

Category: Ransomware | Date: 14th November 2023
The 'PacMan' Ransomware poses a significant threat, designed to extort money from its victims. 'PacMan' Ransomware particular ransomware variant has been employed in targeted attacks against Danish chiropractors, utilizing highly specific phishing tactics. Upon infection, the 'PacMan' Ransomware....

Category: Ransomware | Date: 14th November 2023
Emerging in late 2019, the PwndLocker ransomware has swiftly made a substantial impact, notably with unprecedented ransom demands for specific targets. This sophisticated malware has strategically targeted business and local government networks, levying ransom demands surpassing $650,000. The scale....

Category: Ransomware | Date: 14th November 2023
Buhti, a ransomware threat, targets both Windows and Linux systems. On Windows, it utilizes a variant of the leaked LockBit 3.0 Ransomware, with minor modifications. Conversely, when infecting Linux systems, Buhti employs a customized version of the leaked Babuk Ransomware. Buhti Ransomware....

Category: Ransomware | Date: 14th November 2023
The STOP Ransomware family, including the emerging BBOO variant, has gained momentum. The increasing number of STOP Ransomware variants is evident, with numerous new iterations surfacing. The threat continues to evolve, following a pattern observed in 2019, where over 200 versions wreaked havoc,....

Category: Ransomware | Date: 14th November 2023
Security researchers have identified a new malware threat known as the Wuxia Ransomware, linking its underlying code to the VoidCrypt Ransomware family. Once infected, victims of Wuxia Ransomware find themselves unable to access a vast array of files on their compromised devices, as the malware....

Category: Ransomware | Date: 14th November 2023
The Ppvw Ransomware poses a serious threat to software systems, employing a malicious encryption process that renders data inaccessible to its rightful owner on compromised devices. This insidious malware targets a variety of file types, utilizing a sophisticated encryption routine. The malevolent....

Category: Ransomware | Date: 9th November 2023
The Zpww Ransomware is a highly sophisticated malware designed to completely encrypt data on compromised devices. Its main objective is to extort money from victims by holding their files hostage. What sets this ransomware apart is its use of the '.zpww' file extension to identify encrypted....

Category: Ransomware | Date: 8th November 2023
Keylock has emerged as a dangerous ransomware threat. Ransomware is a malicious software that operates by encrypting a victim's files, rendering them inaccessible, and then demanding a ransom payment in exchange for the decryption key. In the case of Keylock, Keylock Ransomware malicious software....

Category: Ransomware | Date: 7th November 2023
Bmo ransomware is a malicious software capable of encrypting a wide array of files including documents, PDFs, archives, databases, images, audio, and video files, among others. Each encrypted file undergoes significant modification, with the addition of a unique victim-specific ID string, an email....
Category: Ransomware | Date: 7th November 2023
Networklock Ransomware, a file-locking Trojan, is believed to be a MedusaLocker Ransomware variant. It encrypts files, holding them hostage until a ransom is paid for restoration. To mitigate risks, users are encouraged to back up their files on separate devices for cost-effective recovery. Most....

Category: Ransomware | Date: 7th November 2023
Information security researchers have recently verified the enduring appeal of the STOP/Djvu Ransomware family within the cybercriminal community. Hackers are consistently introducing new variants within this family, with the emergence of threats like Mmvb Ransomware being a notable example. While....

Category: Ransomware | Date: 7th November 2023
KeRanger Ransomware is a notorious encryption ransomware Trojan, notable for targeting computers running the Mac OS operating system. It gained attention in March 2016 when security researchers discovered it disguised as a fake version of Transmission, a popular BitTorrent client. Once infected,....

Category: Ransomware | Date: 7th November 2023
Thank you for providing additional information about the Yzoo Ransomware. It appears to be a variant belonging to the STOP/Djvu Ransomware family, which is a well-known ransomware strain that encrypts files on infected devices, rendering them inaccessible to the owners. The Yzoo Ransomware....
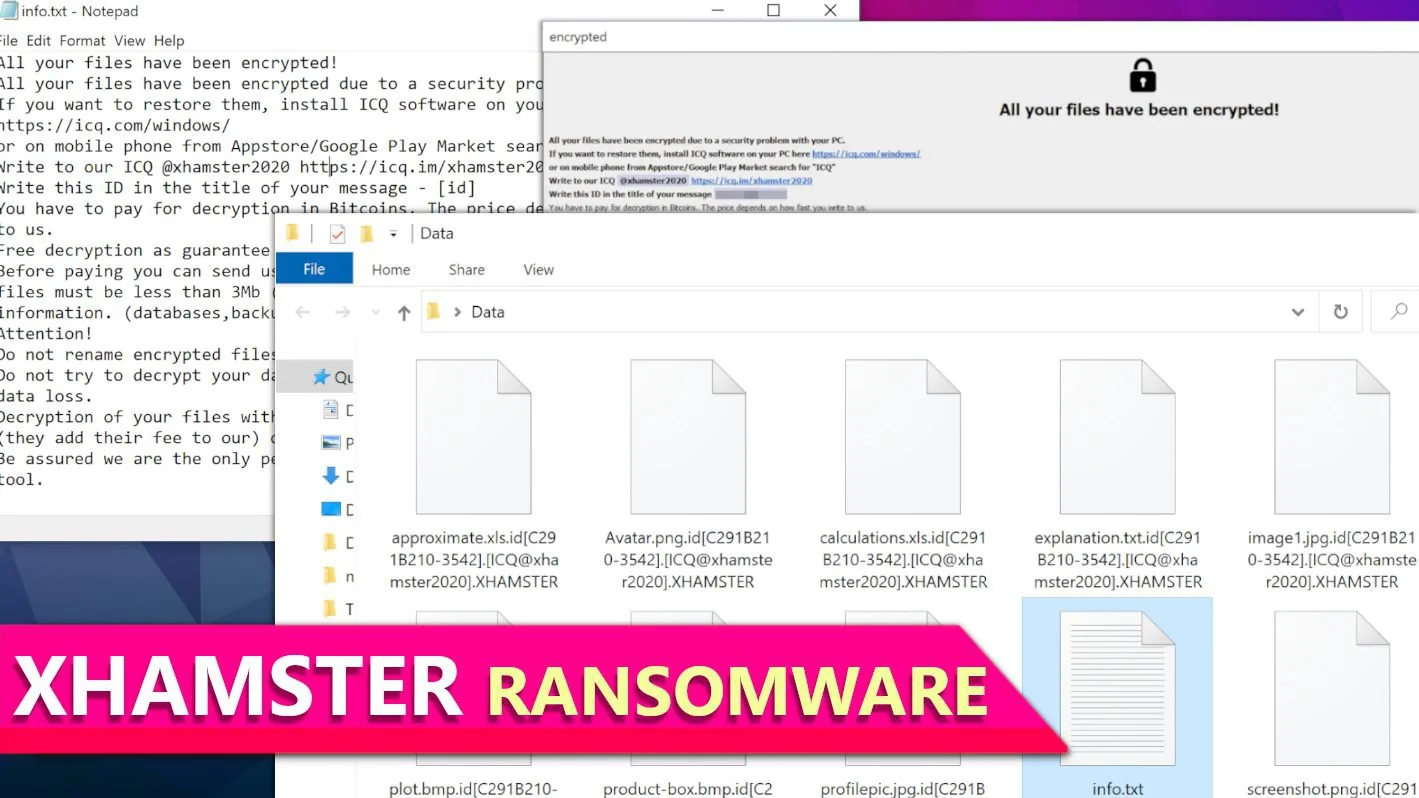
Category: Ransomware | Date: 7th November 2023
Cybercriminals have recently unleashed a new threat known as XHAMSTER Ransomware, a variant of the notorious Phobos Ransomware. This malicious software is designed to lock victims' data, rendering it inaccessible and unusable. XHAMSTER Ransomware employs a powerful encryption algorithm, making it....

Category: Ransomware | Date: 6th November 2023
Nefilim is a type of ransomware that first emerged in early 2020. Similar to other ransomware variants, Nefilim encrypts files on the victim's computer, making them inaccessible, and then demands a ransom payment in exchange for the decryption key. What sets Nefilim apart is its focus on large....

Category: Ransomware | Date: 6th November 2023
Ryuk is a sophisticated and highly targeted ransomware strain that emerged in August 2018. It has gained notoriety for its specifically targeted attacks against large organizations, especially in the healthcare, government, and financial sectors. Ryuk is known for demanding high ransom payments,....

Category: Ransomware | Date: 6th November 2023
Locky is a notorious ransomware strain that emerged in early 2016. It gained widespread attention due to its large-scale and aggressive distribution methods. Like other ransomware, Locky encrypts files on the victim's computer and demands a ransom payment in Bitcoin or other cryptocurrencies to....

Category: Ransomware | Date: 6th November 2023
Bad Rabbit is a ransomware attack that emerged in October 2017. It primarily targeted computer systems in Eastern Europe, especially in Russia and Ukraine. The malware spread rapidly, encrypting files on infected computers and demanding a ransom payment for their release. Bad Rabbit shares....

Category: Ransomware | Date: 6th November 2023
Petya and NotPetya are both types of ransomware that gained notoriety for their destructive and widespread attacks on computer systems. While they share similarities, they are distinct forms of malware. Petya Ransomware: Petya is a ransomware strain that first emerged in 2016. It encrypts the....

Category: Ransomware | Date: 6th November 2023
WannaCry is a notorious ransomware attack that occurred in May 2017. It targeted computers running Microsoft Windows operating systems, encrypting users' files and demanding a ransom payment in Bitcoin cryptocurrency to decrypt them. The WannaCry ransomware spread rapidly across the globe,....

Category: Ransomware | Date: 4th November 2023
Trigona Ransomware, a menacing player in the world of cybercrime, has gained notoriety for Trigona Ransomware disruptive and destructive activities. Named after the aggressive and highly organized Trigona bee, Trigona Ransomware malicious software encrypts files on compromised systems, extorting....

Category: Ransomware | Date: 4th November 2023
ThreeAM Ransomware has emerged as a prominent and insidious threat in the cybersecurity landscape, instilling fear among individuals and organizations alike. Named after the eerie hour, this malicious software operates in the shadows, encrypting files on compromised systems and demanding a ransom....

Category: Ransomware | Date: 4th November 2023
Knight Ransomware, a formidable threat in the digital landscape, has emerged as a perilous adversary, causing distress among individuals and organizations globally. Named after Knight Ransomware stealthy and cunning tactics, Knight Ransomware malicious software encrypts files on targeted systems,....

Category: Ransomware | Date: 4th November 2023
Ragnar Locker Ransomware stands as a menacing force in the realm of cyber threats, instigating fear among individuals and organizations worldwide. Named after the Norse mythological figure, this malicious software encrypts files on targeted systems, rendering them inaccessible to users. The....

Category: Ransomware | Date: 4th November 2023
Medusa Ransomware, named after the mythical creature with snakes for hair, has emerged as a formidable cybersecurity threat, striking fear into the hearts of individuals and organizations worldwide. Medusa Ransomware insidious malware encrypts files on infected systems, holding them hostage until....

Category: Ransomware | Date: 4th November 2023
NoEscape Ransomware has recently emerged as a highly concerning cybersecurity threat, striking fear into individuals and organizations alike. NoEscape Ransomware Named for its elusive nature and the daunting predicament it puts its victims in, NoEscape Ransomware malicious software encrypts files....

Category: Ransomware | Date: 4th November 2023
8Base Ransomware has recently emerged as a highly sophisticated and alarming threat in the realm of cybercrime. Named after its complex encryption algorithms and multi-layered approach, 8Base Ransomware variant is designed to infiltrate computer systems, encrypt valuable files, and demand a ransom....

Category: Ransomware | Date: 4th November 2023
Play Ransomware, a malicious software that derives its name from the high-stakes game it plays with victims, has recently surfaced as a significant cybersecurity threat. Play Ransomware variant operates with a sinister agenda, encrypting files on infected systems and holding them hostage until a....

Category: Ransomware | Date: 4th November 2023
Cactus ransomware has emerged as a potent and sophisticated threat in the realm of cybercrime, leaving a trail of disrupted operations and financial losses for its victims. Cactus Ransomware malicious software, known for its prickly nature, encrypts sensitive files on infected systems, rendering....

Category: Ransomware | Date: 4th November 2023
LostTrust ransomware emerged as a menacing cyber threat, wreaking havoc on individuals and organizations alike. LostTrust Ransomware malicious software, like many other ransomware variants, encrypts valuable data, rendering it inaccessible to users. The group responsible for LostTrust ransomware....

Category: Ransomware | Date: 4th November 2023
Hive ransomware operated as a sophisticated Ransomware-as-a-Service (RaaS) group from June 2021 to January 2023. Their primary targets included public institutions such as healthcare facilities, nonprofits, retailers, and energy providers. Employing a double-extortion tactic, the group first....

Category: Ransomware | Date: 1st November 2023
In the realm of cybersecurity threats, Robbinhood Ransomware continues to be a significant concern for individuals and organizations alike. One notable player in Robbinhood Ransomware malicious game is the Robbinhood Ransomware. Robbinhood Ransomware sophisticated strain has garnered attention for....

Category: Ransomware | Date: 1st November 2023
In the ever-changing landscape of cybersecurity threats, a new player has emerged on the scene: Dual Ransomware. This advanced form of Dual Ransomware represents a significant evolution in the tactics employed by cybercriminals, posing even greater risks to individuals and organizations alike. In....
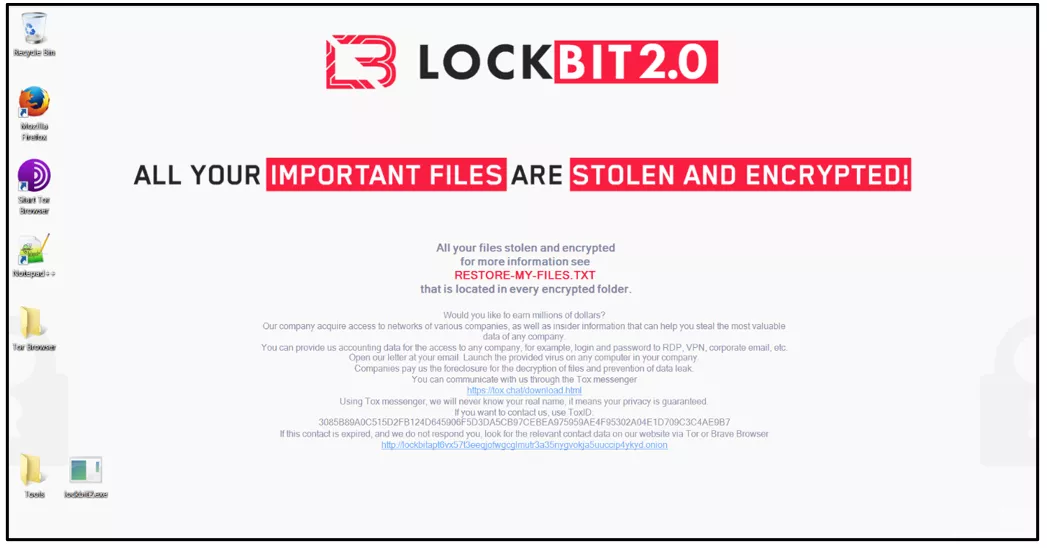
Category: Ransomware | Date: 1st November 2023
In today's digital landscape, where cyber threats loom large, it's crucial to stay informed and vigilant about the latest forms of malware. LockBit ransomware, a notorious strain of malicious software, has gained notoriety for its sophisticated techniques and devastating impact on individuals and....
Category: Ransomware | Date: 31st October 2023
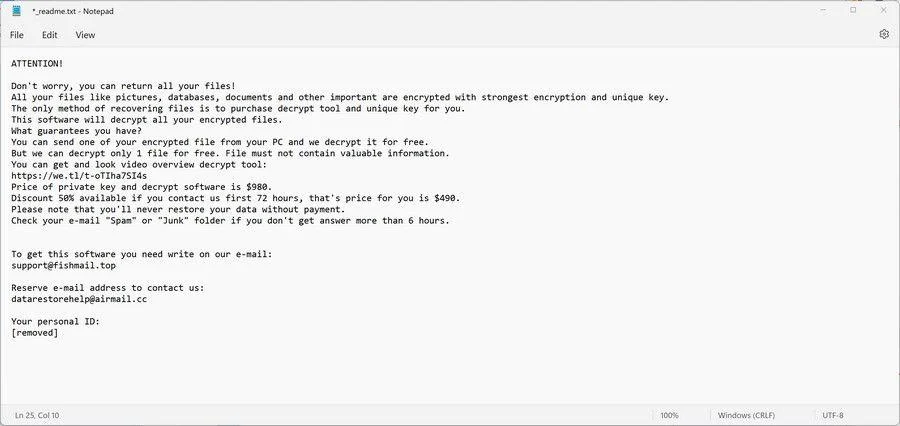
In recent years, the digital landscape has witnessed an alarming rise in cyber threats, with ransomware attacks being one of the most menacing forms of cybercrime. Among the various strains of ITQW ransomware, ITQW ransomware has emerged as a significant threat to individuals, businesses, and even....

Category: Ransomware | Date: 30th October 2023
Your personal files could be in jeopardy. The infamous STOP/DJVU ransomware has resurfaced, introducing a fresh variant that encrypts crucial files like images and documents on compromised computers. This updated version adds the ".PPVS" extension to the filenames of the encrypted files,....
Category: Ransomware | Date: 18th October 2023
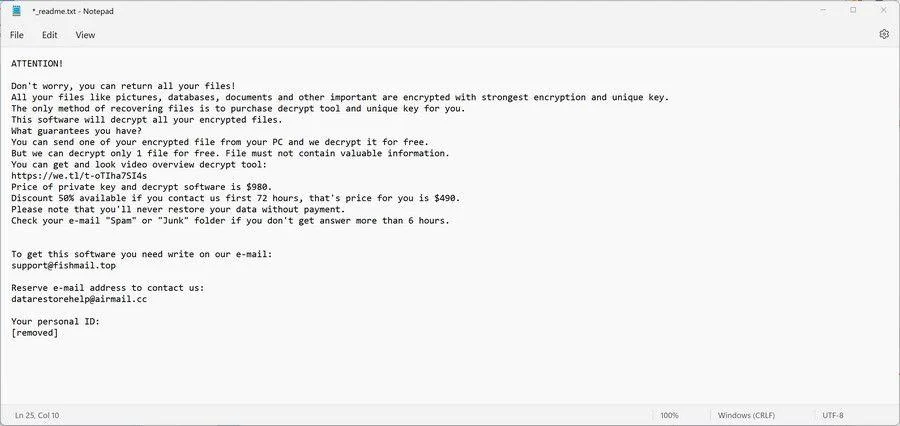
A new iteration of the infamous STOP/DJVU ransomware has emerged, posing a significant threat to your personal files. PTQW Ransomware malicious software encrypts essential documents, images, and various files on infected computers. The defining characteristic of PTQW Ransomware latest version is....

Category: Ransomware | Date: 18th October 2023
A new variant of the infamous STOP/DJVU ransomware has emerged, posing a significant threat to your personal files. This malicious software encrypts crucial documents, images, and various files on infected computers. The distinctive characteristic of this latest version is its tendency to append....

Category: Ransomware | Date: 2nd October 2023
Lost Trust Ransomware stands as a chilling testament to the evolving landscape of cyber threats. This malicious software, like its counterparts, is designed with one sinister purpose: to encrypt a victim’s files and demand a ransom for their release. What sets Lost Trust Ransomware apart is....

Category: Ransomware | Date: 26th September 2023
It's concerning to hear that you've encountered the Azop ransomware, especially given its affiliation with the Djvu ransomware family. Ransomware attacks are a serious threat to both individuals and organizations, as they can lead to data loss and financial consequences. Understanding the behavior....

Category: Ransomware | Date: 26th September 2023
In today's interconnected digital world, ransomware attacks have emerged as one of the most prevalent and destructive forms of cyber threats. These malicious acts not only affect individuals but also have devastating consequences for organizations and even entire economies. In this article, we....
Category: Ransomware | Date: 26th September 2023
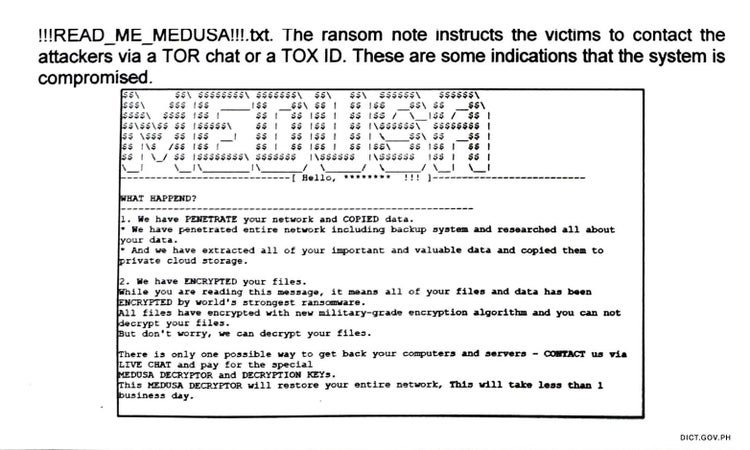
In the ever-evolving landscape of cyber threats, ransomware attacks remain a formidable adversary for individuals and organizations alike. One particularly notorious strain is Medusa ransomware, which has wreaked havoc on victims by encrypting their data and demanding a ransom for its release. To....
Category: Ransomware | Date: 11th September 2023
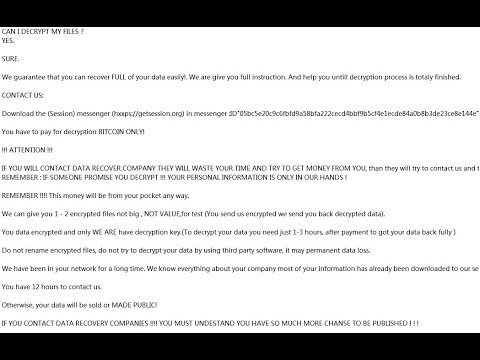
In the ever-evolving landscape of cyber threats, new forms of malware constantly emerge to exploit vulnerabilities in computer systems. One such threat gaining attention in recent times is the Grounding Conductor Ransomware. This insidious malware not only encrypts your data but also poses a....

Category: Ransomware | Date: 23rd August 2023
Ransomware attacks have become increasingly prevalent, and the STOP/DJVU ransomware strain is among the notorious culprits. If your Windows 11 computer has fallen victim to this malware, you're likely dealing with a locked screen and encrypted files. In this article, we'll provide a comprehensive....

Category: Ransomware | Date: 23rd August 2023
In the ever-evolving landscape of cyber threats, one menace has proven to be relentless and highly profitable for cybercriminals: ransomware. Despite ongoing efforts to combat these attacks, ransomware incidents continue to proliferate, posing significant risks to individuals, businesses, and even....

Category: Ransomware | Date: 19th August 2023
The world of cybersecurity is in a constant struggle to stay ahead of malicious actors, and among the many threats that have emerged, Monti Ransomware is a name that sends shivers down the spines of individuals and organizations alike. This article delves into the depths of Monti Ransomware,....

Category: Ransomware | Date: 19th August 2023
The digital world is a battlefield between cybercriminals and cybersecurity experts. Among the numerous weapons in the cybercriminal's arsenal, Nitrogen Ransomware stands out as a particularly menacing adversary. In this article, we will dive into the realm of Nitrogen Ransomware, understanding....

Category: Ransomware | Date: 19th August 2023
In the realm of cybersecurity, the battle against ransomware is relentless. One of the latest adversaries in this ongoing struggle is the SonicWall ransomware. This article delves into the world of SonicWall ransomware, examining what it is, how it operates, and the essential measures individuals....

Category: Ransomware | Date: 17th August 2023
In the ever-evolving landscape of cybersecurity threats, ransomware has emerged as one of the most formidable adversaries. This malicious software can paralyze individuals and organizations by encrypting critical data and demanding hefty ransoms for its release. However, arming oneself with recent....
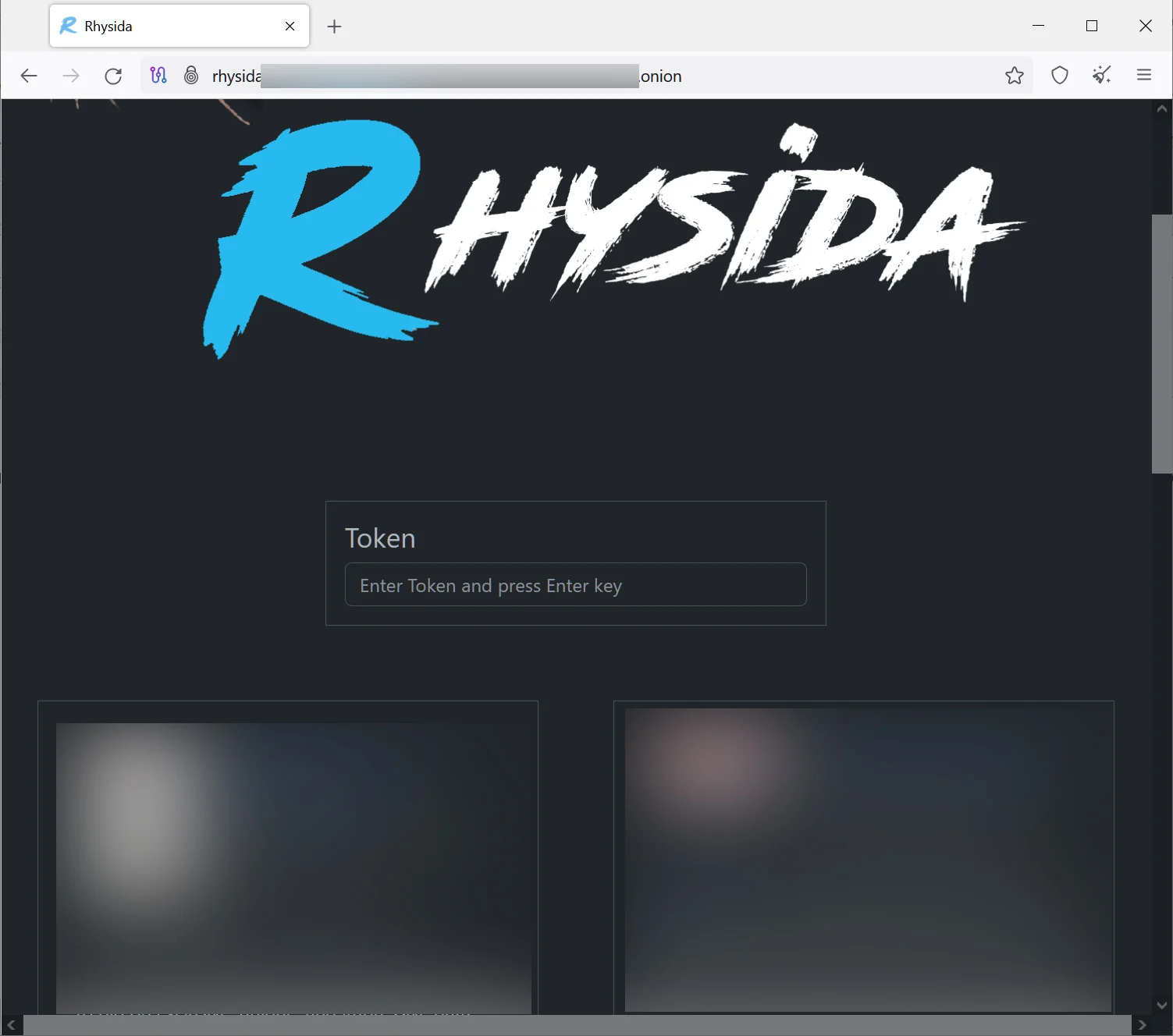
Category: Ransomware | Date: 17th August 2023
In the digital age, where information is paramount, the rise of ransomware attacks has left individuals and organizations vulnerable to devastating cyber threats. One such malevolent software that has gained notoriety is the Rhysida ransomware. With the potential to lock away critical data and....

Category: Ransomware | Date: 16th August 2023
In the digital age, cybersecurity threats have become increasingly sophisticated, and one of the most alarming types of threats is ransomware. Among them, the Knight Ransomware has gained notoriety for its capability to encrypt files, rendering them inaccessible until a ransom is paid. This article....

Category: Ransomware | Date: 12th August 2023
Ransomware remains a persistent and damaging cyber threat that can wreak havoc on individuals and businesses by encrypting critical files and demanding a ransom for their release. Magniber ransomware is one such malicious program that can target your valuable data, locking it away until you meet....

Category: Ransomware | Date: 12th August 2023
The digital landscape is not devoid of threats, and ransomware is one of the most notorious forms of malware that can wreak havoc on individuals and organizations alike. Among the ransomware variants, Clop ransomware has gained infamy for its sophisticated tactics and damaging effects. In this....

Category: Ransomware | Date: 12th August 2023
Ransomware continues to be a pressing and evolving cybersecurity threat, wreaking havoc on individuals, businesses, and even critical infrastructure. As we delve into the ransomware landscape in August 2023, it's important to assess the trends, new developments, and challenges that are shaping this....

Category: Ransomware | Date: 2nd August 2023
Ransomware attacks continue to be a serious threat to individuals and businesses, with new variants emerging regularly. One such malicious ransomware strain is POAZ ransomware. POAZ encrypts victims' files, rendering them inaccessible until a ransom is paid to the attackers. However, paying the....

Category: Ransomware | Date: 2nd August 2023
Ransomware attacks have become a major cybersecurity threat, causing significant harm to individuals and organizations worldwide. One such malicious ransomware strain is POUU ransomware. POUU encrypts victims' files, rendering them inaccessible until a ransom is paid to the attackers. However,....

Category: Ransomware | Date: 2nd August 2023
Ransomware attacks have become a pervasive and alarming threat to individuals and businesses worldwide. One such ransomware strain that has gained notoriety is POPN ransomware. POPN encrypts victims' files, making them inaccessible until a ransom is paid to the attackers. However, it is essential....

Category: Ransomware | Date: 2nd August 2023
In recent years, ransomware attacks have emerged as one of the most significant cybersecurity threats, wreaking havoc on individuals, businesses, and even critical infrastructure. These attacks involve malicious actors encrypting victims' data and demanding a ransom in exchange for the decryption....

Category: Ransomware | Date: 1st August 2023
The growing menace of ransomware continues to disrupt individuals and organizations worldwide, causing significant financial losses and data breaches. Among the rising wave of ransomware variants is MOVEit ransomware, a malicious software designed to encrypt files and hold critical data hostage....

Category: Ransomware | Date: 1st August 2023
As the world becomes increasingly digital, the threat of ransomware continues to grow, causing severe disruptions and financial losses for individuals and organizations. Among the numerous variants, Black Basta ransomware has emerged as a significant threat. This article sheds light on Black Basta....

Category: Ransomware | Date: 1st August 2023
In the ever-expanding world of cyber threats, ransomware remains a top concern for individuals and organizations alike. Among the growing number of ransomware variants is PROCOM, a nefarious data encryptor that has been causing havoc across digital landscapes. In this article, we will explore the....
Category: Ransomware | Date: 1st August 2023
Ransomware continues to evolve, and cybercriminals are constantly seeking new ways to exploit vulnerabilities in various operating systems. In recent times, the emergence of the Linux version of Abyss Locker ransomware has posed a serious risk to Linux-based environments. This article delves into....
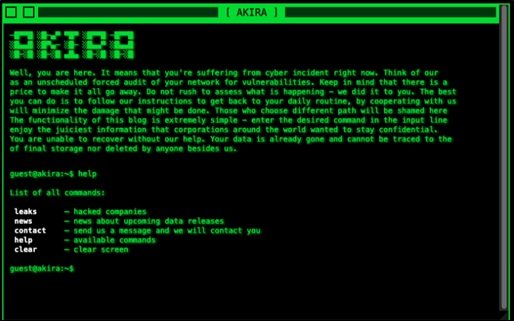
Category: Ransomware | Date: 29th July 2023
In the ever-evolving landscape of cybersecurity threats, ransomware continues to be a dominant menace, wreaking havoc on individuals and organizations worldwide. One such formidable adversary is Akira Ransomware, a cunning variant that employs sophisticated encryption techniques to hold victims'....

Category: Ransomware | Date: 29th July 2023
In the realm of cybersecurity, ransomware continues to be a pervasive and dangerous threat, with evolving variants designed to exploit vulnerabilities in our digital world. One such insidious ransomware is Dallas, a menacing variant that encrypts victims' files and demands a ransom for their....

Category: Ransomware | Date: 29th July 2023
In the world of cybersecurity, new threats are constantly emerging, and one such malevolent entity is the BlackCat Ransomware. Like a stealthy feline lurking in the shadows, BlackCat ransomware variant silently infiltrates systems, encrypts files, and demands a ransom for their release. In this....
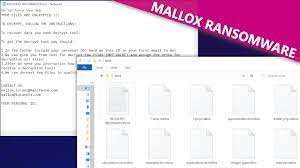
Category: Ransomware | Date: 29th July 2023
Mallox Ransomware, a dangerous variant that can cause severe damage to individuals and organizations alike. In this article, we will explore the nature of Mallox Ransomware, its potential consequences, and most importantly, provide a step-by-step guide on how to remove it from your system and....

Category: Ransomware | Date: 25th July 2023
Ransomware attacks have become increasingly prevalent in the digital landscape, causing significant disruptions and financial losses to individuals and businesses. Big Head Ransomware is one such malicious software that encrypts your files and demands a ransom for their release. If your system has....
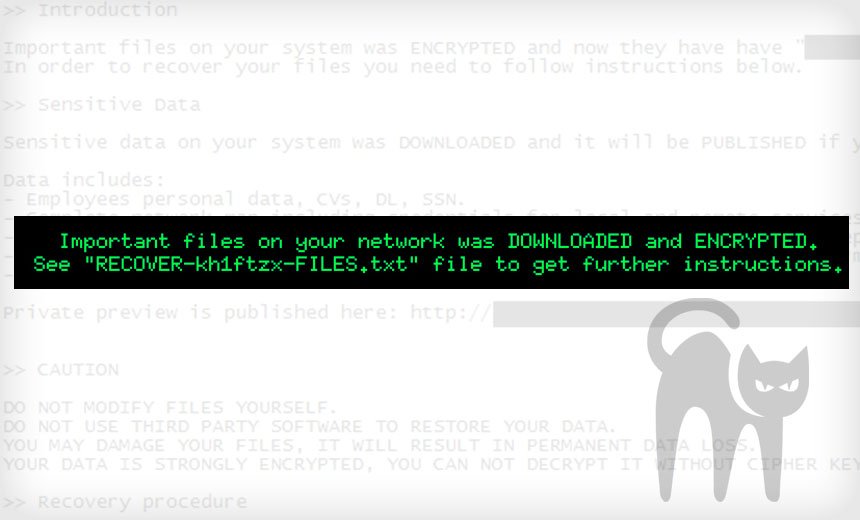
Category: Ransomware | Date: 25th July 2023
Ransomware continues to be one of the most notorious and devastating cyber threats, causing significant disruptions and financial losses to individuals and businesses worldwide. ALPHV ransomware is one such malevolent variant that encrypts valuable data on infected systems, holding it hostage....
Category: Ransomware | Date: 24th July 2023
Ransomware attacks have become an increasingly prevalent threat to individuals and organizations alike. Among the notorious ransomware strains is Clop, a sophisticated and damaging malware that encrypts files and demands a ransom for their release. If you've fallen victim to Clop ransomware, don't....

Category: Ransomware | Date: 16th July 2023
In the ever-evolving landscape of cyber threats, ransomware remains one of the most concerning and damaging forms of malware. Among the numerous variants that have emerged over the years, one notable strain is the Heartbleed ransomware. Named after the infamous Heartbleed vulnerability, this....

Category: Ransomware | Date: 12th July 2023
In the ever-evolving landscape of cybersecurity threats, a new ransomware variant has emerged, known as WAQQ. This malicious software poses a significant risk to individuals and organizations, encrypting files and demanding ransom payments for their release. In this article, we will delve into the....

Category: Ransomware | Date: 12th July 2023
In recent years, ransomware attacks have become an increasingly prevalent threat to individuals and organizations worldwide. One particularly notorious ransomware variant is GAQQ. Known for its sophisticated techniques and devastating consequences, GAQQ poses a significant risk to data security. In....
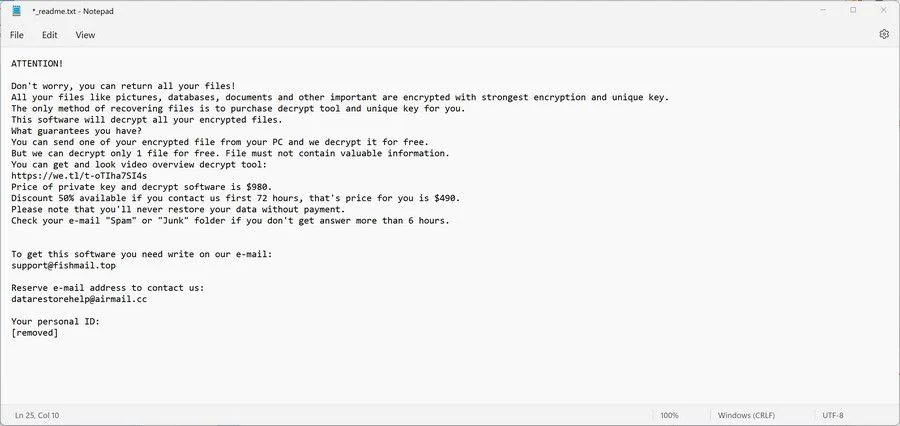
Category: Ransomware | Date: 26th May 2023
GATQ Ransomware is a nasty ransomware program. GATQ Ransomware will encrypt the computer files, and others associated file extension. GATQ Ransomware will attempt to freeze the complete computer function and display the blue screen or black with blue screen color. However, GATQ Ransomware will work....

Category: Ransomware | Date: 23rd May 2023
LockBit 3.0 is a ransomware variant that was first discovered in September 2021. It's important to note that as an AI model, my knowledge is based on information available up until September 2021, so I might not have specific details about recent developments or new variants like LockBit....

Category: Ransomware | Date: 1st March 2023
".darus" Is Very Unique Ransomware And Encryption Code, Which Can Encrypt The Hostile Computer Files. ".darus" Has Been Very Aggressive To Infringe Many Cyber Barrier And Acquire The Feeble Computer Terminal. ".darus" Has Ability To Conceal Itself From The Scanner Or Antivirus....

Category: Ransomware | Date: 27th February 2023
NamPoHyu Has Been Fabricated By The Unknown Computer Criminal. NamPoHyu Will Target Around The Cyber Network. The VPN Network May Annihilate Weirdly By The NamPoHyu Ransomware Malware. NamPoHyu Ransomware Targets Victim’s Computer Files. NamPoHyu Ransomware Is Spreading Through Spam....
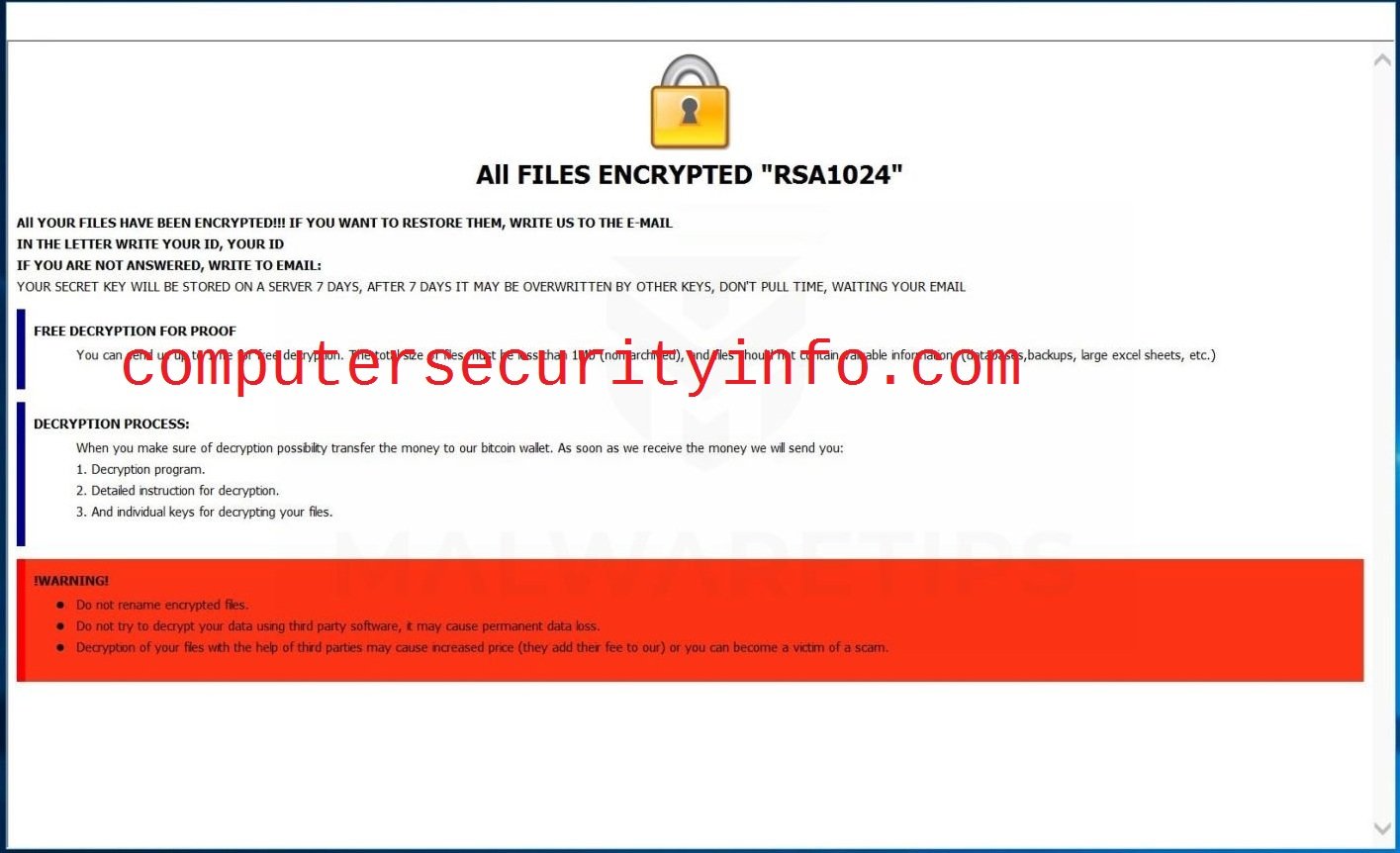
Category: Ransomware | Date: 27th February 2023
[savemydata@qq.com].harma Is Appeared On February 25, 2019. [savemydata@qq.com].harma Is A Ransomware Malware, But [savemydata@qq.com].harma Contains Trojan Virus Characters Or Features. [savemydata@qq.com].harma Will Send Notifications To The Compromise Computer System, While....
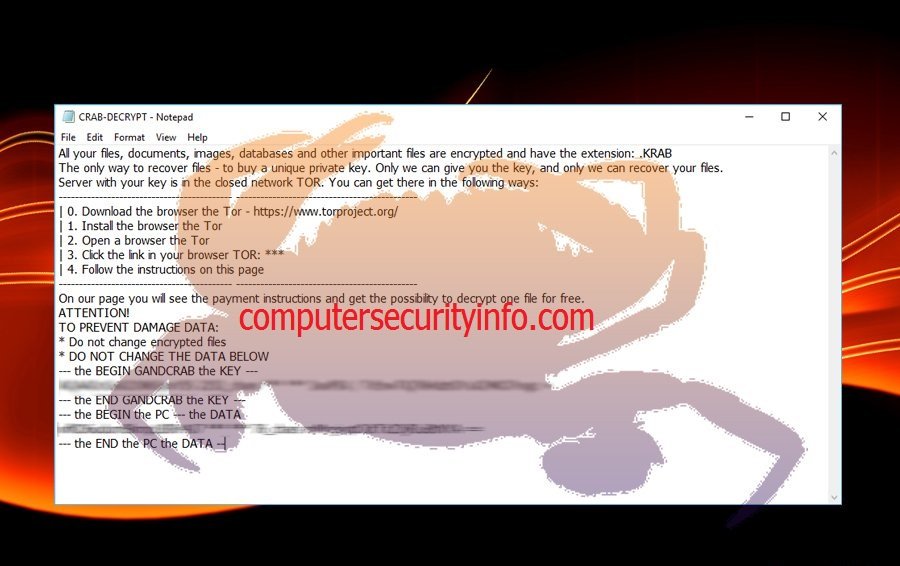
Category: Ransomware | Date: 27th February 2023
GandCrab Is An Obsolete File Encrypting Program And Classified As A Ransomware. GandCrab Has Three Distinguished Versions – GDCB, GandCrab2 And GandCrab3. The Trouble Has Been Occurred Because GandCrab Has Utilized An Advanced Version Of Illegitimate Code. Any The Obsolete Versions Of....
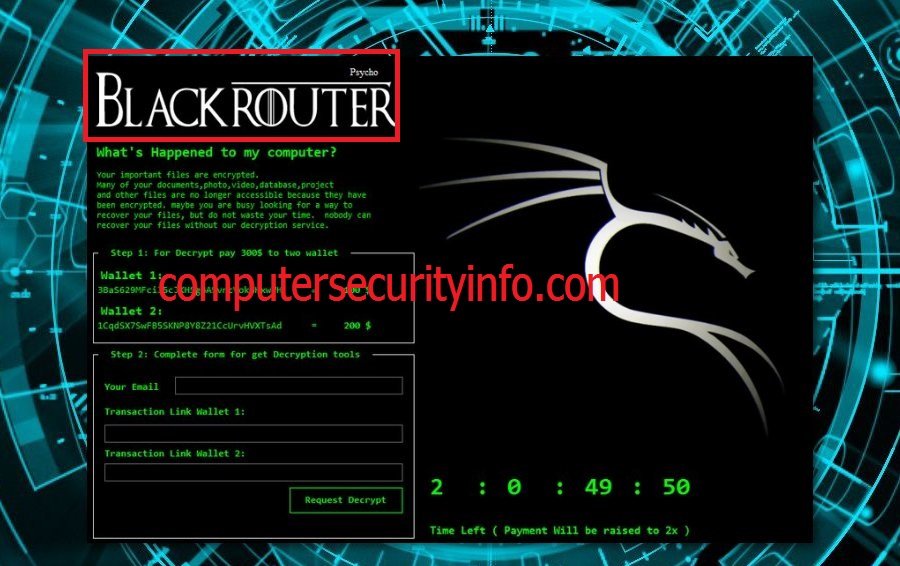
Category: Ransomware | Date: 21st February 2023
BlackRouter Is A Vicious Malware Program To Classified As A Ransomware Code To Hijack The Computer System, Laptop, Tablets And Other Devices. BlackRouter Encrypts The Files, Folders, Images, Database, Video And Audio Files, Installed Software And Tools. BlackRouter Will Strive To Blackmail The....
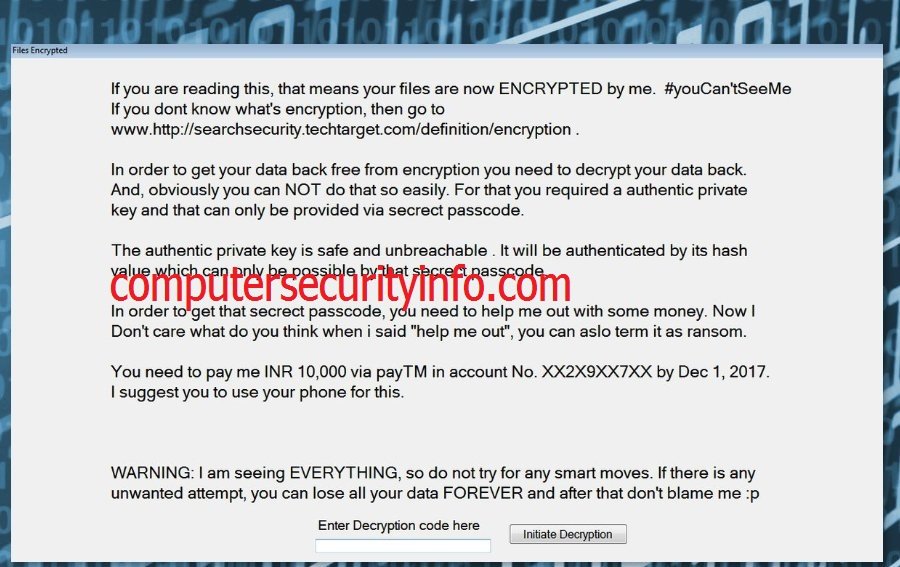
Category: Ransomware | Date: 21st February 2023
IGotYou is Very Obfuscated Program, That Can Elude The User From The Main Goal. Why This Application Can Create Chaos? Unfortunately, IGotYou Is A Vicious As Well As The Dangerous Ransomware Program, Which Has Been Designed By The Cyber Crooks For Their Own Or Individual Interest. IGotYou Has....
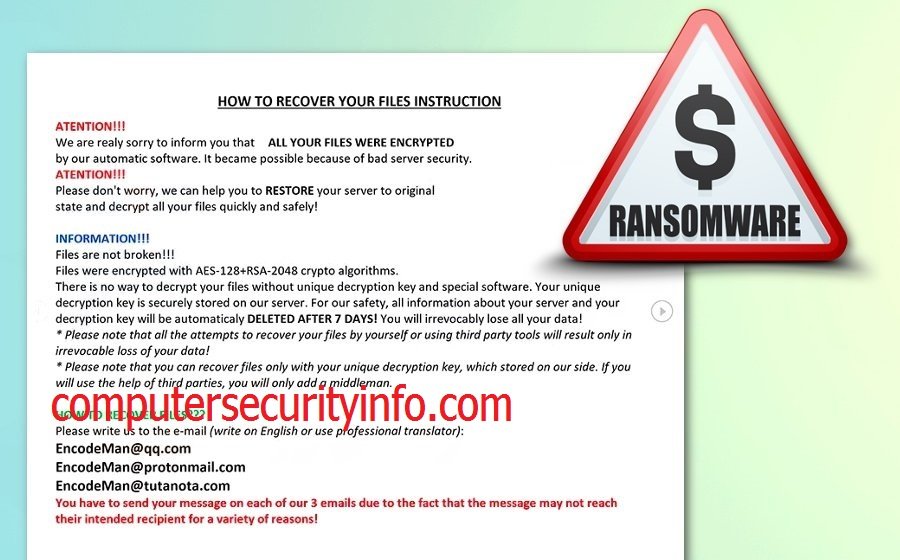
Category: Ransomware | Date: 21st February 2023
Eman Is New Kind Of Ransomware Program, Which Is Related With Crypto-extortionist Called Matrix. Eman Is A New Variant Of Ransomware Application Or Code To Invade The Enfeeble Computer Terminal Suddenly. Eman Ransomware Has Been Crafted By The Several Professional. Eman Ransomware Is Used For....

Category: Ransomware | Date: 17th February 2023
Zlocker Ransomware Has Been Designed By The Perpetrators For Their Own Interest And Generates The Online Revenue From The Illegitimate Source. Zlocker Is A File Encrypting Code To Encrypt The Whole PC Terminal, Including Files, Videos, Audios, Pics, Database And Small App. Zlocker Ransomware....

Category: Ransomware | Date: 17th February 2023
Styx Ransomware Program Is Encrypting The Information, Files, Videos, Images, Database And Tools, While The Process Is Not End. Styx Ransomware Is A Vile Or Treacherous Code To Display Ransom Note In The Text Form, Where To Victimize Users As Well As Victims, For Culprit For Doing....
Category: Ransomware | Date: 17th February 2023
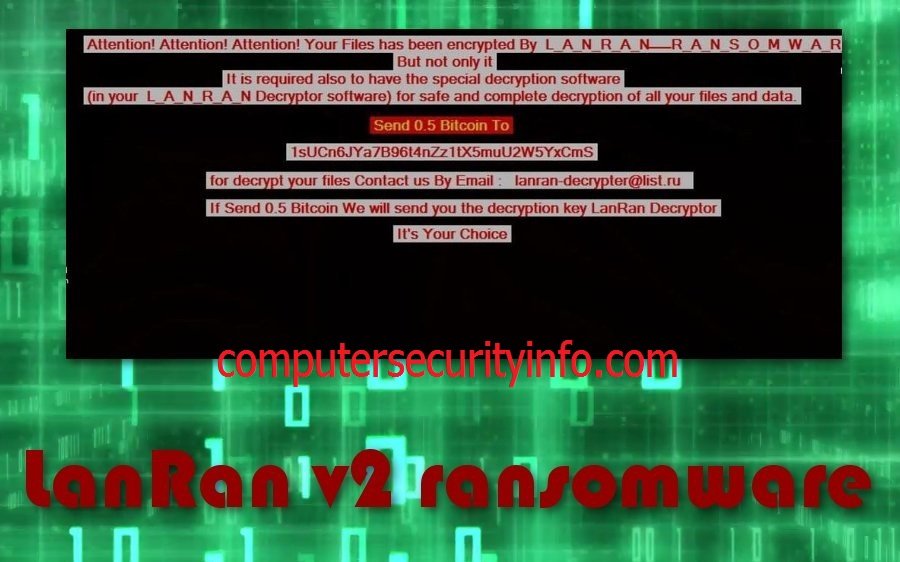
LanRan V2 Ransomware Is A Destructive Internet Bug Created For The Purpose Of Hacking Into A Computer System And Extract Information About Concerned User's Surfing Activities, Session Data And More. The Data Gathered By LanRan V2 Ransomware Is Badly Utilized To Other Third Party Vendors So....
Category: Ransomware | Date: 16th February 2023
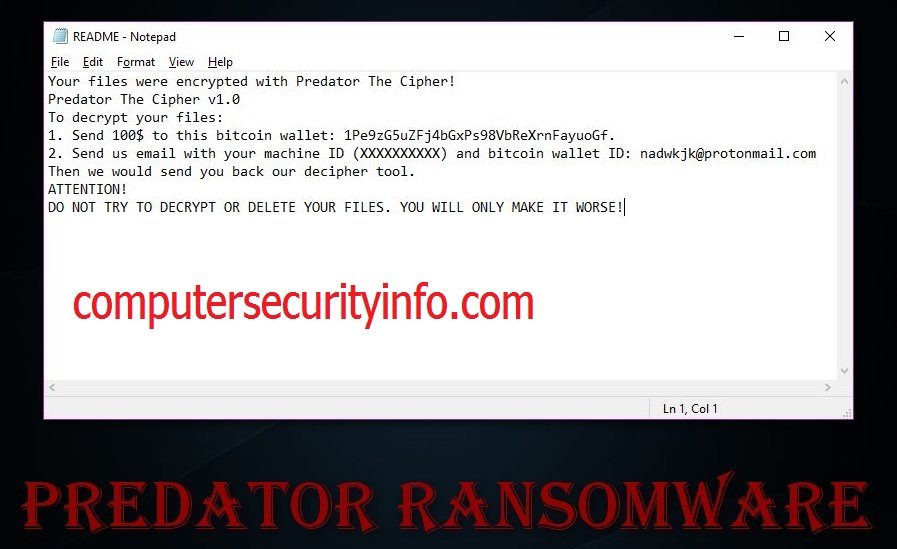
Predator Ransomware Is A File Encrypting Cryptovirus, That Confiscates Numbers Of Files And Appends .predator Extension At The End Of The File Name. However, Predator Ransomware Is Not Manually Remove From The Computer System, Whether You Can Run Windows OS As Well As The Macintosh OS.....
Category: Ransomware | Date: 16th February 2023
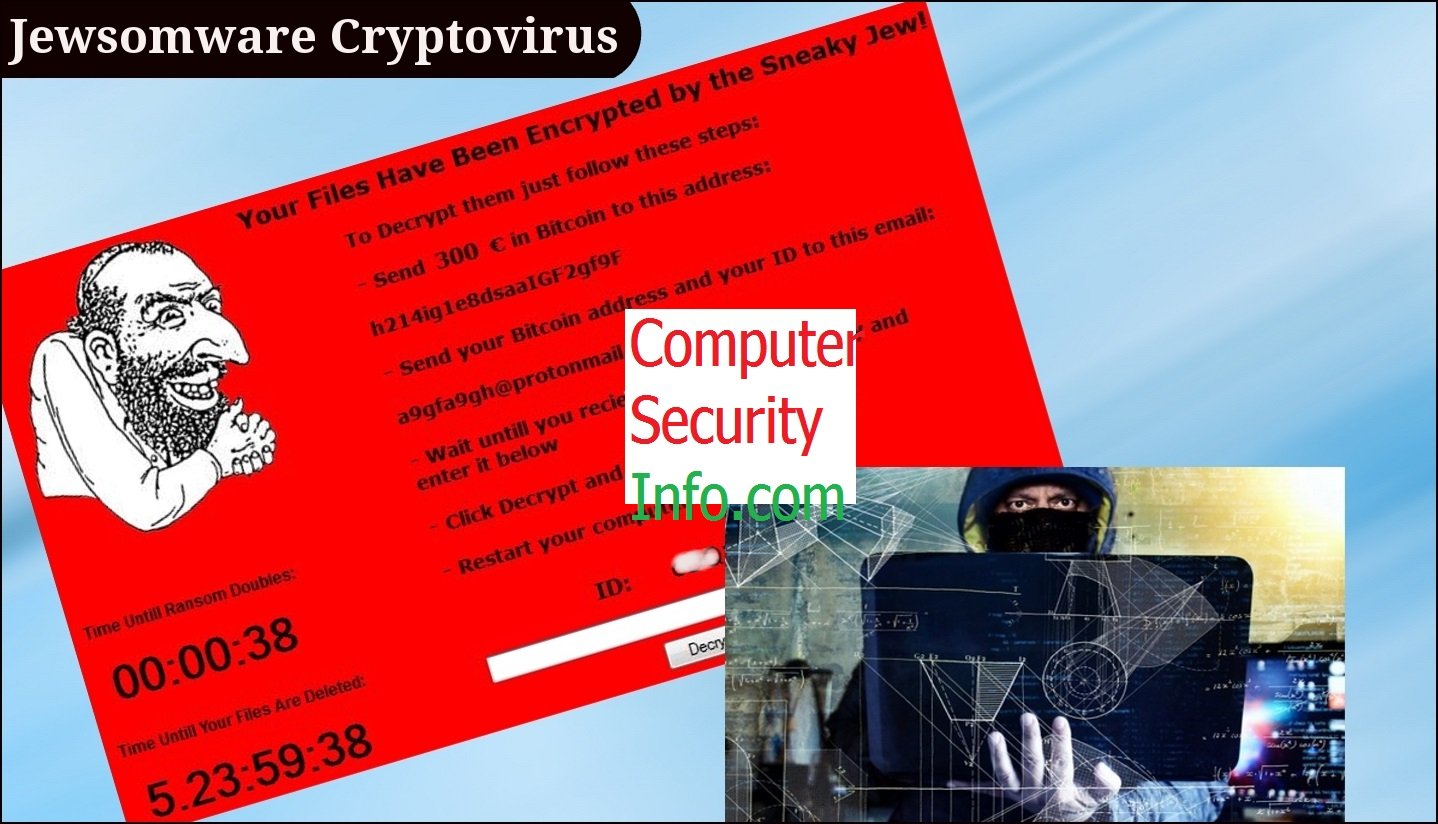
Jewsomware Cryptovirus As Well As Ransomware Code, Which Has Been Very Horrible And Demand The Ransom Money From The Victim. The Amount Of The Ransom Is $300 In Bitcoin. Actually, Jewsomware Is A Cryptovirus, That Can Encrypt Your Text Files, Videos Files, Audios Files, Photos Files, Backup....
Category: Ransomware | Date: 16th February 2023
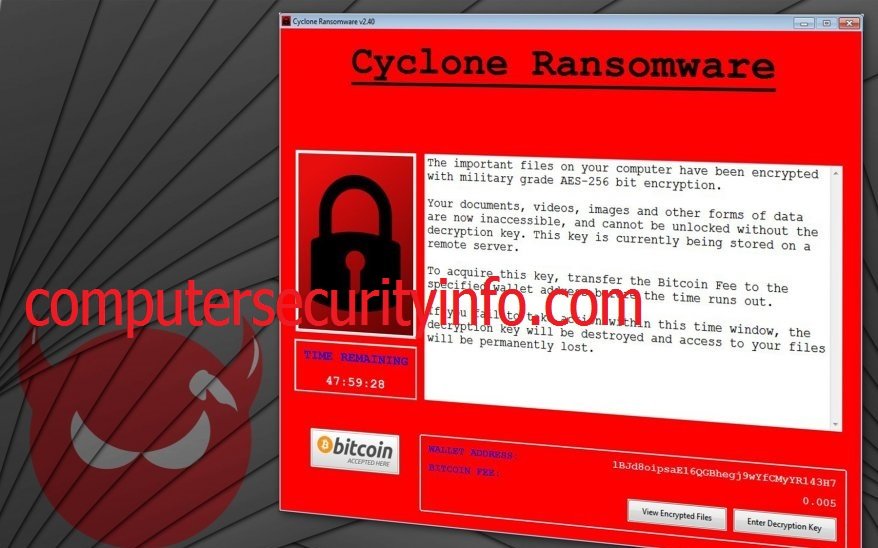
Cyclone Ransomware Program Is An Associated With Noblis Ransomware. Cyclone Ransomware Encrypt Files, Video, Music, Database And Follow Trojan Virus, That Was Commenced On December 12, 2017. Cyclone Ransomware Malware Was Released On December 16. Cyclone Ransomware Is Work As A....

Category: Ransomware | Date: 16th February 2023
Cerber Is A Very Terrible And Dreadful Ransomware Program. Cerber Is A Very Active Program In The Cyber Network. Cerber Ransomware May Annihilate VPN Network, Many Computer System And Peripheral Devices. Cerber Ransomware Encrypts Significant Files, Video, Music, And Database Files. Cerber....

Category: Ransomware | Date: 16th February 2023
CryptoWall Decrypter Is A Dreadful Ransomware Program, That Encrypts The Files, Music Files, Video, Database And Other Small Utility Inside The Computer System. CryptoWall Decrypter Is Coded To Use An Advanced Encryption Algorithm To Make Computer Files Unreachable On The Targeted Terminal....
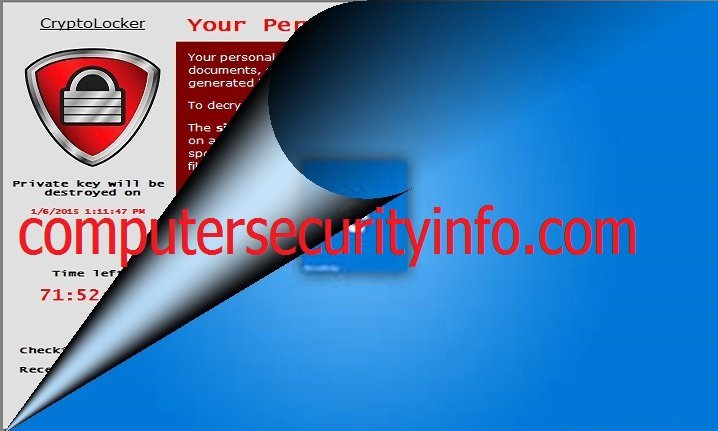
Category: Ransomware | Date: 15th February 2023
EdgeLocker Ransomware Is A Malign Piece Of Code Which Is Concerned With Malware Kin. Its Main Purpose To Hack Computer Terminal And Display Some Message Regrading To Penalty. EdgeLocker Ransomware Claims That Client Violate International Cyber Law, Infringement Of Privacy Policy, Publish Adult....

Category: Ransomware | Date: 15th February 2023
CryptoSweetTooth Is A Code That Belongs To A Ransomware, Which Can Targets Specific Region Especially Spanish Speaking Countries. CryptoSweetTooth Encrypts User's Files As Well As Folders And Avoid From Accessing Their Critical And Other Classified Information, Which Is Stored In The Zip....
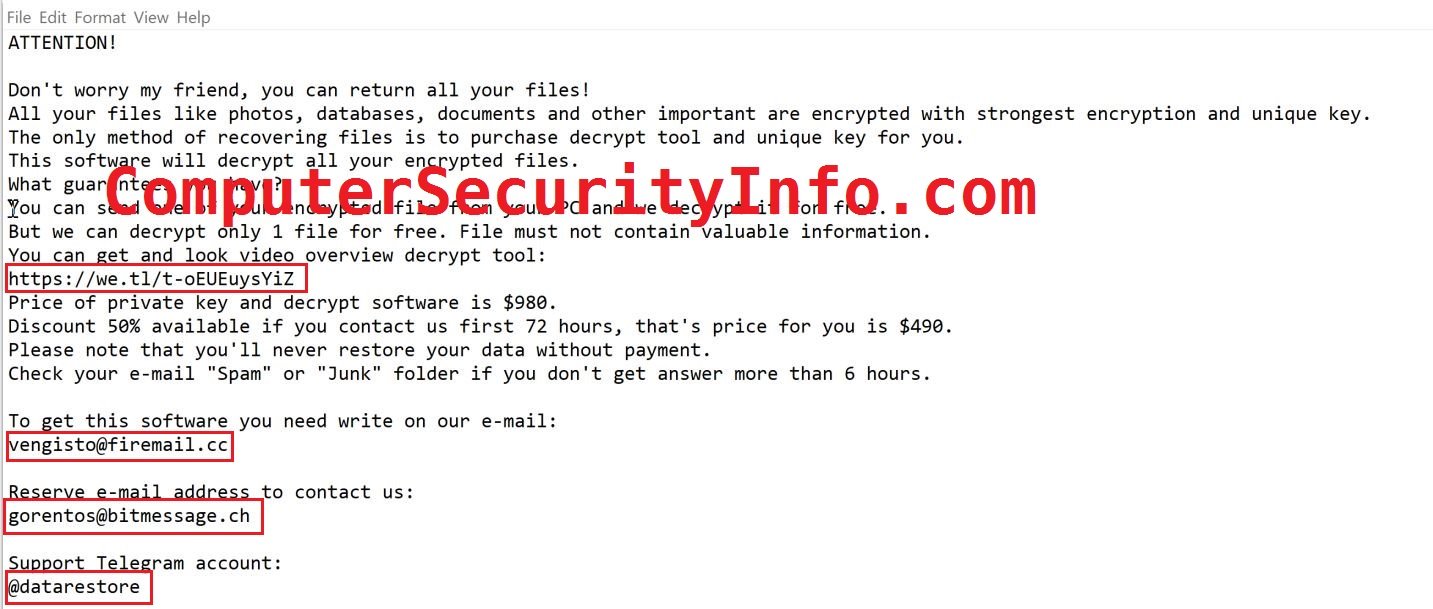
Category: Ransomware | Date: 14th February 2023
Dutan Ransomware Is An Extension Of The STOP (DJVU) Ransomware Program. You Can Say That, Dutan Ransomware Will Hide Behind STOP (DJVU) Ransomware Program. Dutan Ransomware Stops Access To File And Data To Used By The Victim. Dutan Ransomware Encrypts All Data As Well As The Files And Folders.....
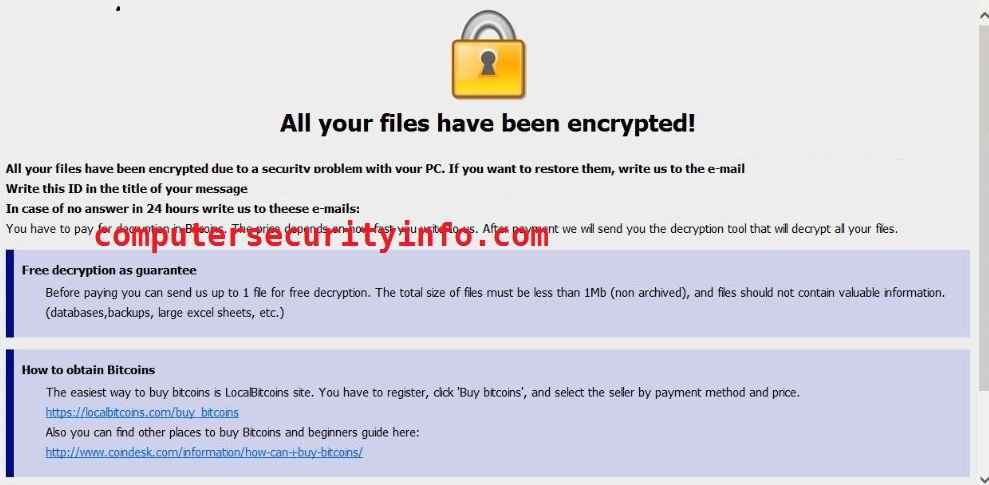
Category: Ransomware | Date: 14th February 2023
[Bitcharity@protonmail.com].com Is An Aghast Ransomware Program, That Can Delude The User From The Main Goal. [Bitcharity@protonmail.com].com May Cripple The Entire Computer System. The Computer Security Is Highly Affected By [Bitcharity@protonmail.com].com Ransomware. However,....

Category: Ransomware | Date: 7th February 2023
.AUF Files Is A File And Incorporate With ASAUpdater2 By ASA Datensystem GmbH. .AUF Files To Modify The LTBO Database, Which Is Used By The LTBOffice, An Aircraft Maintenance Program. AUF Means Audacity Block File. While Your Computer System Does Not Open The .AUF Files Format, That Means Your....
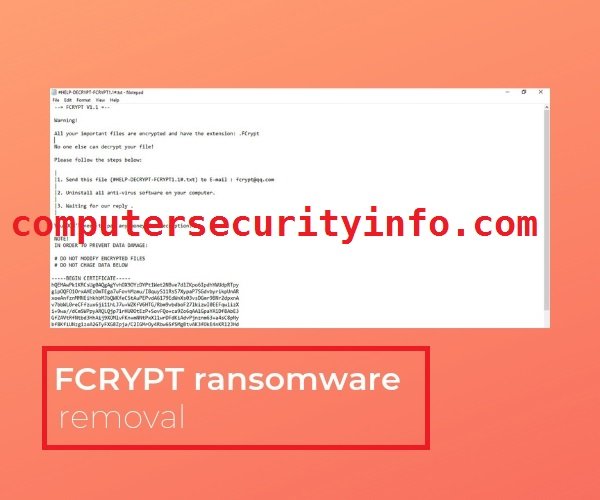
Category: Ransomware | Date: 7th February 2023
Fcrypt Ransomware Is A Big Potential Threat, Because Fcrypt Ransomware Has Been Freezed The Entire Computer System As Well As Function. The User Can’t Access Anything. Fcrypt Ransomware Encrypts The Files, Musics Files, Video Files, And Databases Files. After Encryption Process. Fcrypt....

Category: Ransomware | Date: 7th February 2023
Nemesis Ransomware Encrypts Your Files, Databases And File Extension. Petropasevich@aol.com Email Is Used By The Nemesis Ransomware, Which Might Be Attached As A New File Extension Into Encrypted Files. Actually, Nemesis Is A Diagnose In The Month Of May 2018. Nemesis Ransomware Should....

Category: Ransomware | Date: 7th February 2023
B0r0nt0K (Rontok) Is A Hazardous As Well As Insecure Ransomware Program. February 25, 2019 Is A Bad Day For Those Client, Who Has Been Affected By B0r0nt0K (Rontok) Ransomware. B0r0nt0K (Rontok) Was Noticed For The First Time While B0r0nt0K (Rontok) Encrypts The Files, Folders, Musics Files,....

Category: Ransomware | Date: 7th February 2023
.good File Extension Is A Suspicious Ransomware Program. The .good File Extension Is A Generic Ransomware Code Exist With Versions Of The HiddenTear Open-source Ransomware. The .good File Extension Is Detected Or Scanned In September 2018. The .good File Extension Is A Recent Ransomware....
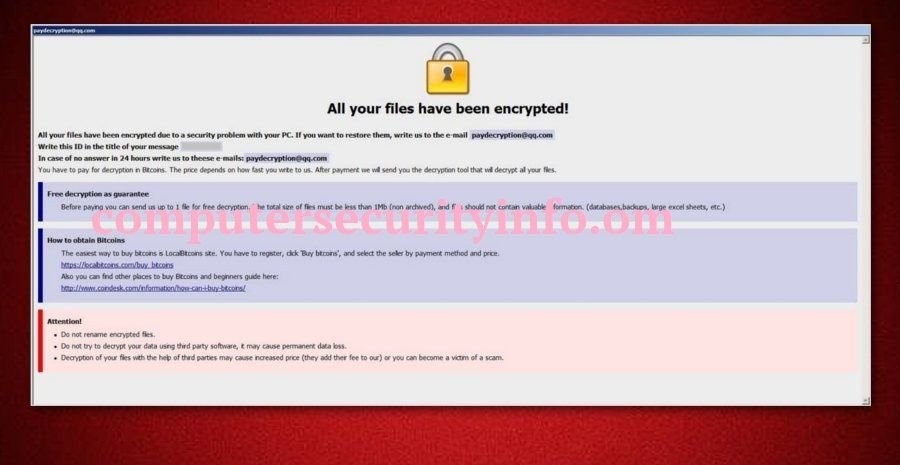
Category: Ransomware | Date: 7th February 2023
paydecryption@qq.com Is An Email Address Used By The Ransomware Developers To Get The Money From The Victim. Paydecryption@qq.com Is An Analogous With Dharma Virus And Crysis Ransomware Application. Paydecryption@qq.com Is A Blend Of A Dharma Ransomware As Well As The Crysis Ransomware.....
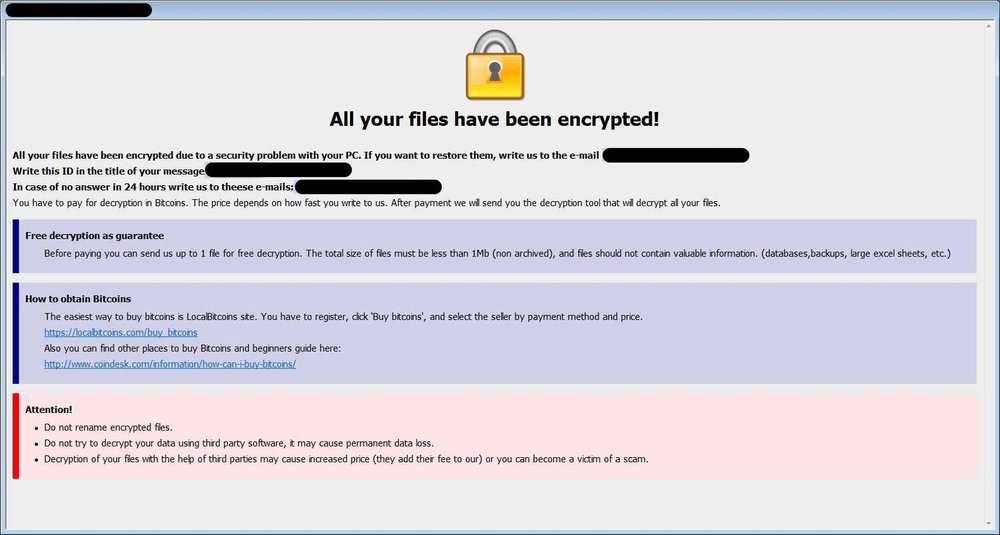
Category: Ransomware | Date: 6th February 2023
Dharma is a type of ransomware that encrypts the files on a target device or network, making them inaccessible to the user. The attackers then demand a ransom payment in exchange for the decryption key, which is necessary to restore access to the encrypted files. Dharma is a highly sophisticated....
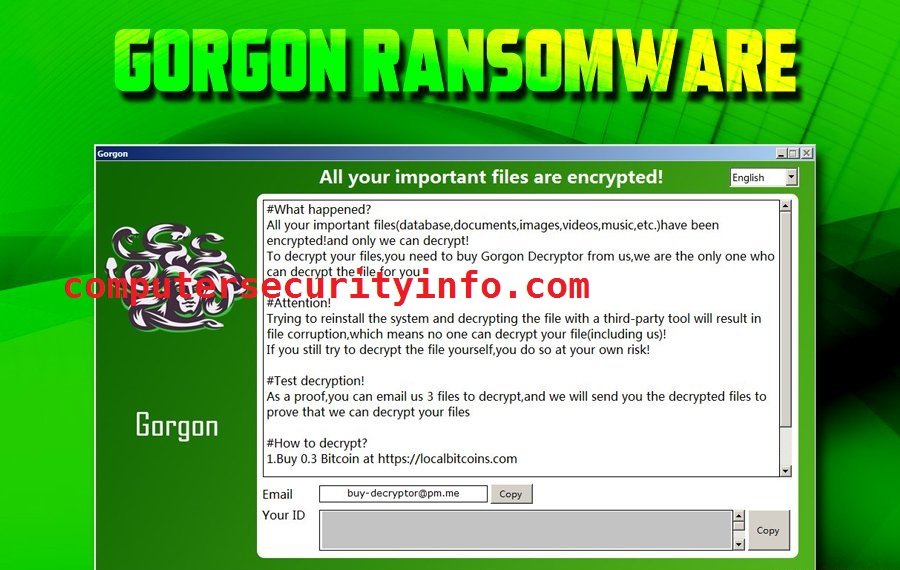
Category: Ransomware | Date: 4th February 2023
buy-decryptor@pm.me Gorgon Is A Small Piece Of Malware Program, That Encrypts All Indispensable Files And Folders. Buy-decryptor@pm.me Gorgon Ransomware Has Been Created By The Perpetrators For Their Financial Benefits. The User Of The Internet Buy-decryptor@pm.me Gorgon Ransomware Virus....
Category: Ransomware | Date: 4th February 2023
GEFEST Looks Alike A Ransomware Code With Different Extension Like GEFEST 3.0 Ransomware Code. GEFEST Encrypts The Computer System Has Been Influenced By The Victim System. GEFEST 3.0 Ransomware Code Has Also Been Sorted By The Many Files. GEFEST 3.0 Also Encrypts Video Files, Music Files,....
Category: Ransomware | Date: 4th February 2023
helpfilerestore@india.com.ETH Is A New Sort Of Ransomware Code. Helpfilerestore@india.com.ETH Has Been Coded By The Computer Offender To Earn The Revenue From The Institution As Well As The Stealing The Data From The Other Organization. Helpfilerestore@india.com.ETH Has Been Integrated With....
Category: Ransomware | Date: 4th February 2023
korvin0amber@cock.li.amber Is A Browser Extension Program. Korvin0amber@cock.li.amber Is A Travel Through The Email And Infects Your Computer System With The Help Of Dharma Ransomware Program. However, Korvin0amber@cock.li.amber Is A Part Of The Dharma Ransomware Code. Dharma Ransomware Is A....
Category: Ransomware | Date: 4th February 2023
polmacpol@cock.li.heets Ransomware Is A Malign Piece Of Code Which Is Concerned With Malware Kin. Its Main Purpose To Hack Computer Terminal And Display Some Message Regrading To Penalty. Polmacpol@cock.li.heets Ransomware Claims That Client Violate International Cyber Law, Infringement Of....

Category: Ransomware | Date: 4th February 2023
GandCrab V5.2 Ransomware Is A Nasty Malicious Program That Can Restricts Access To The Infected Computer Machine. GandCrab V5.2 Demands From The Client To Pay A Fine Or Ransom To The Malware Operators To Uninstall The Restriction. GandCrab V5.2 Ransomware Is Perilous Malware For Data....
Category: Ransomware | Date: 4th February 2023
crypted_files@qq.com.aqva Ransomware Is A Very Crucial Computer Code, Which Is Invading The All Check And Balance For The Computer System. Crypted_files@qq.com.aqva Ransomware Has Been Created By The Some Significant IT Professional To Gain The Financial Advantage. There Are Number Of Computer....
Category: Ransomware | Date: 4th February 2023
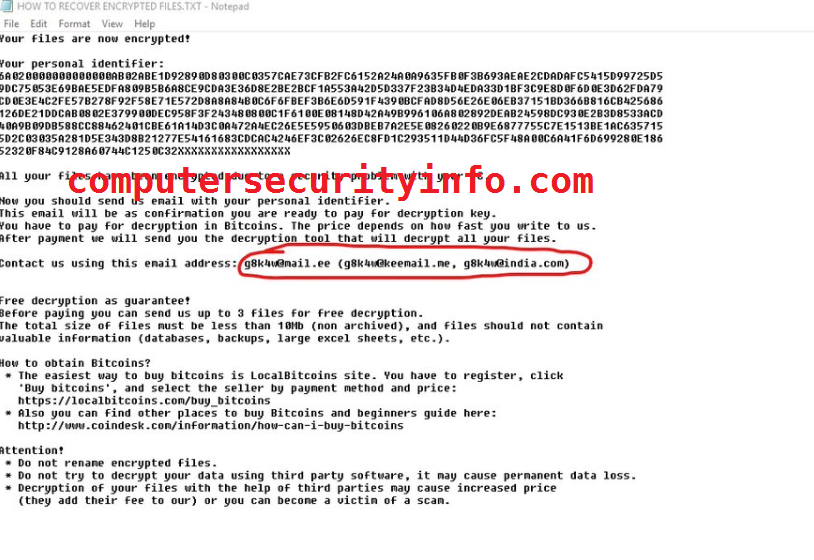
Dy8wud Ransomware Is A Very Crucial Computer Code, Which Is Invading The All Check And Balance For The Computer System. Dy8wud Ransomware Has Been Created By The Some Significant IT Professional To Gain The Financial Advantage. There Are Number Of Computer Tools Or Peripheral Device, Which Is....
Category: Ransomware | Date: 4th February 2023
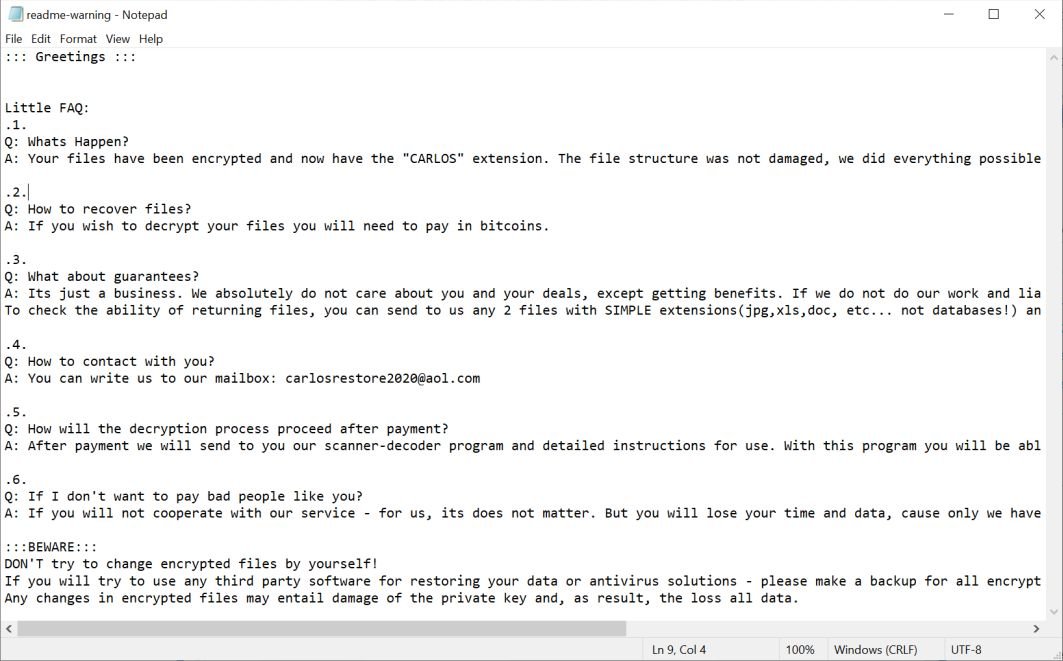
[carlosrestore2020@aol.com].CARLOS Is A Deceptive Ransomware Code, Which Has Been Designed By The Perpetrators To Leak Information From The Client's Terminal. However, [carlosrestore2020@aol.com].CARLOS May Also Violate Many Cyber Law And Infringes Data As Well As Create Number Of Issues.....

Category: Ransomware | Date: 4th February 2023
[crown_desh@aol.com].crown Is A Very Nasty Application That Can Encrypts The Files, Folders, Musics Files, Video Files, Databases And Other Significant Information. [crown_desh@aol.com].crown Ransomware May Stop To Access The Data From The System. It Is Completely Create A Freeze The Computer....

Category: Ransomware | Date: 4th February 2023
[SmartDen@protonmail.com] MDEN Is An Email Address With Some Strange Extension, That May Create A Chaos Inside The Users. However, [SmartDen@protonmail.com] MDEN Has Been Created By The Some Perpetrators To Contravene Your Privacy Policy And Many Things. [SmartDen@protonmail.com] MDEN Has Been....

Category: Ransomware | Date: 4th February 2023
[atomickule@cock.li].[ID].ATKL Is A Notorious Ransomware Program. [atomickule@cock.li].[ID].ATKL Will Strive To Cash All Amount From The Bank Accounts, Which Is Related With Users, Specially Online Users. [atomickule@cock.li].[ID].ATKL Is An Extension To Encrypt The Files, Folders, Database....
Category: Ransomware | Date: 4th February 2023
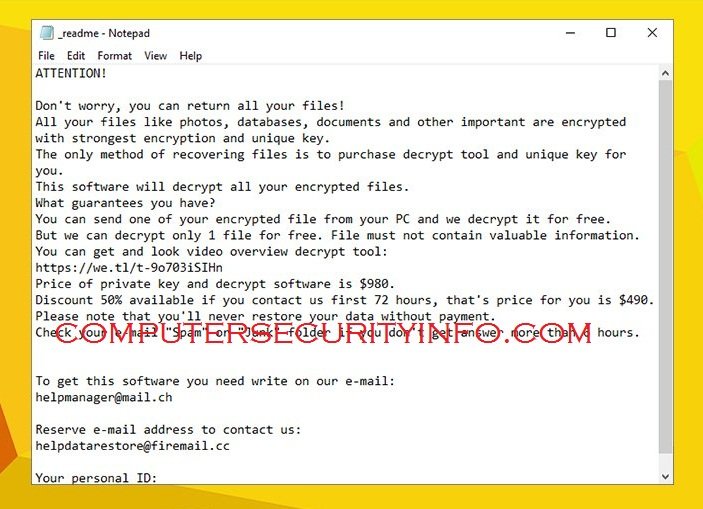
MPAJ Ransomware May Start The Encrypting Process While MPAJ Ransomware Reaches Your Computer Terminal. MPAJ Is A Dangerous Ransomware Application, Because MPAJ Has Been Created By The Cyber Criminal For Financial Advantages. However, MPAJ Will Encrypt Various Significant Documents. MPAJ May Demand....
Category: Ransomware | Date: 4th February 2023
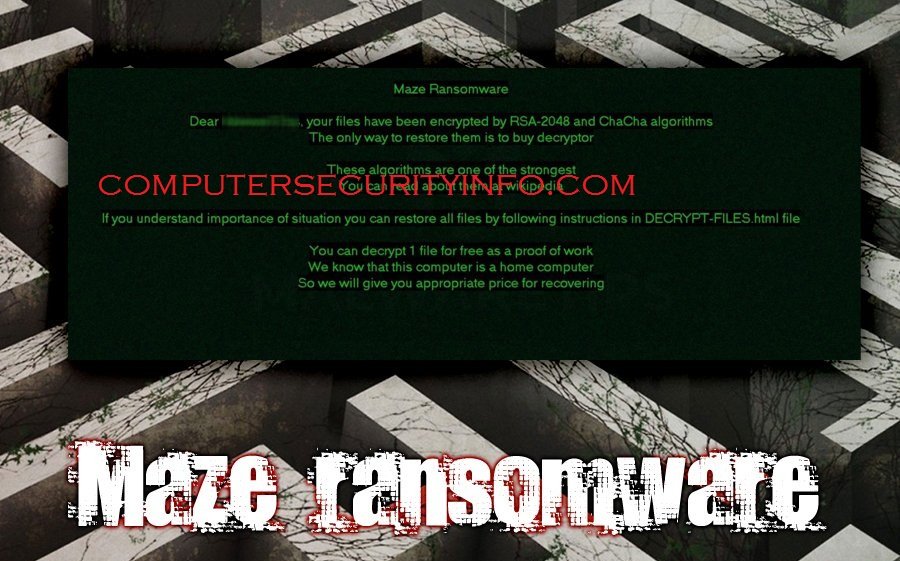
Maze Ransomware Is A Very Perfidious Code, That Has Been Created By The Cyber Perpetrators. Maze Ransomware Is A Combination Of Theft As Well As Encryption Technique, And Target The US Farms And Companies. Maze Ransomware Will Apply Various Method To Target The Terminal, Whether You May....
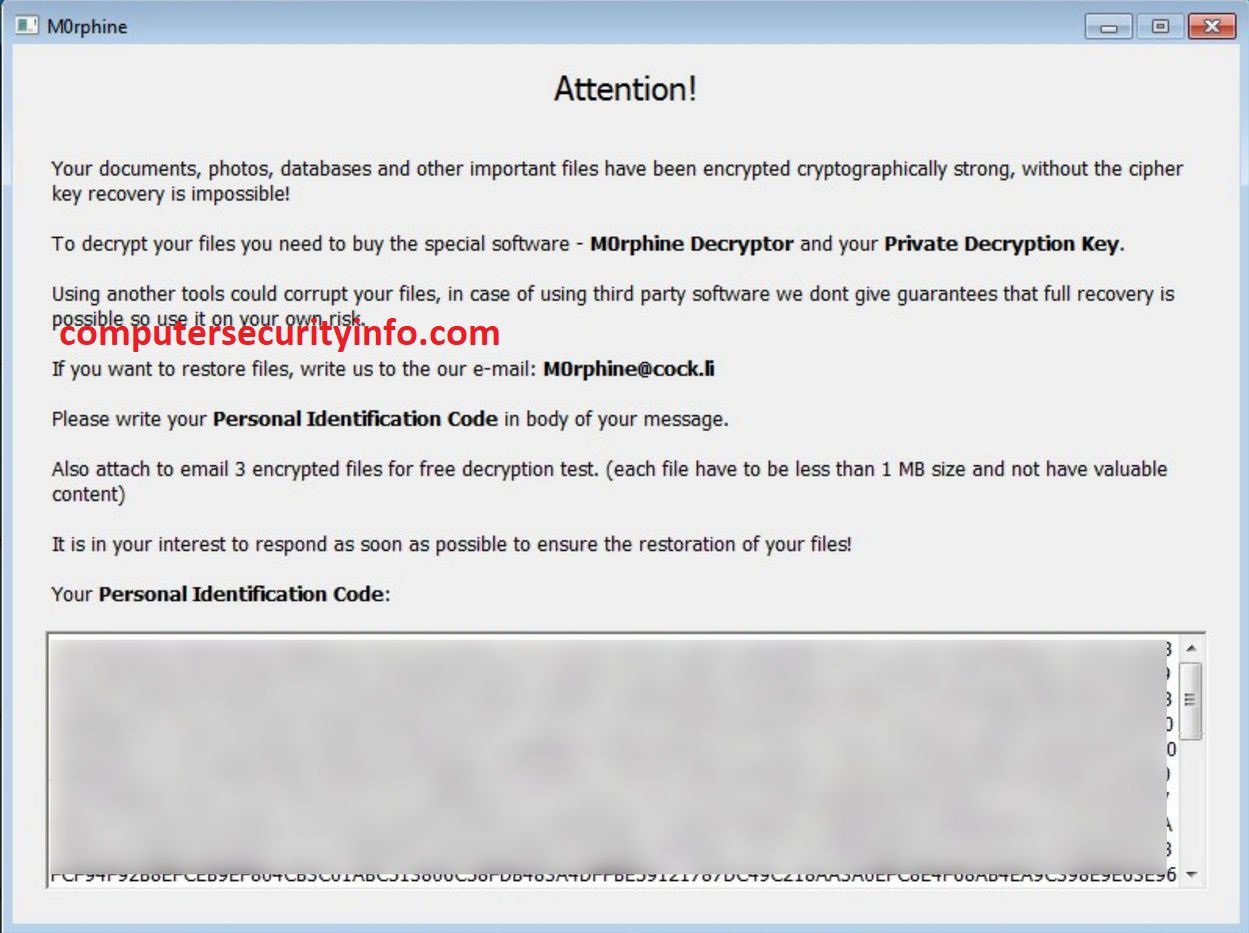
Category: Ransomware | Date: 4th February 2023
M0rphine Ransomware Is A Very Deadly Code To Encrypt Your Significant File Such As Images Files, Video Files, Document Files, Music Files, Database Files And More. M0rphine Ransomware Has Been Designed To Engage The Your Computer Function Gradually. There Are Number Of Issues Occurred....

Category: Ransomware | Date: 4th February 2023
MZLQ Ransomware Encryption Code To Encrypts Various Files As Well As Folders. MZLQ Ransomware Has Been Created By The Cyber Goons For Their Financial Advantage. There Are Number Of Issues Raised Occurred Randomly. MZLQ Ransomware Is Most Favourable Threats Program, Which May Use Trojan Program....
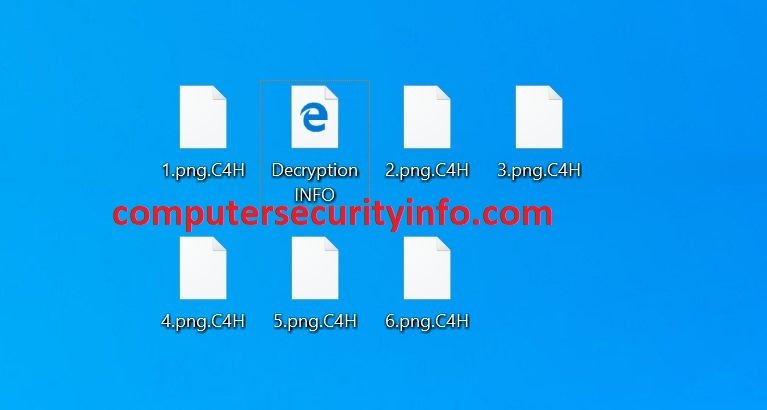
Category: Ransomware | Date: 4th February 2023
C4H Ransomware Encrypts The Data File And Database Files. C4H Ransomware Has Been Created By The Cyber Goons. The Cyber Criminal Uses CH4 Ransomware Code To Explore The Data From The Victim’s Computer System. CH4 Is Files Extension And Use This Extension After Encryption. C4H....
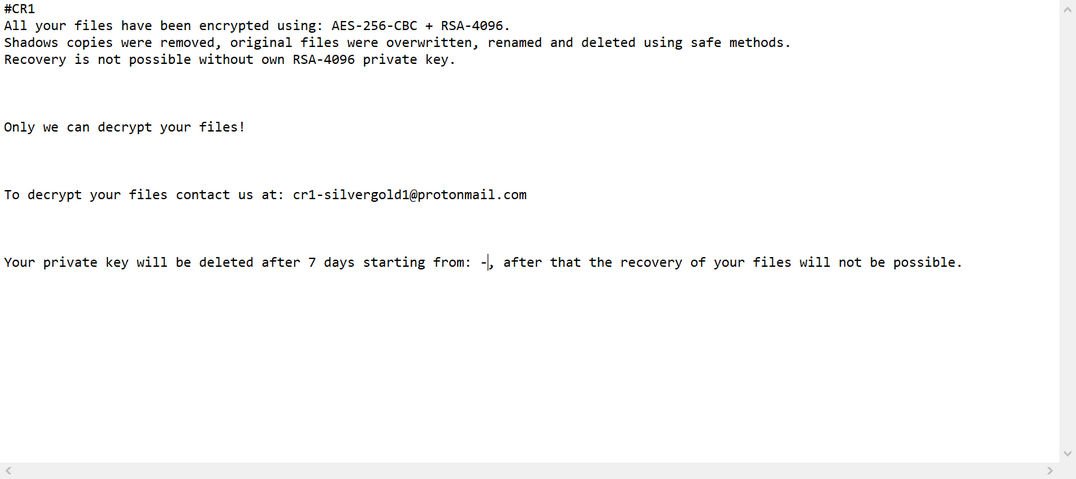
Category: Ransomware | Date: 4th February 2023
CR1 Ransomware Has Been Crafted By The Delinquent For Getting Money From The Victim’s System. The Hacker Will Strive For Accumulating The Information Regarding Money, Financial Transaction, Bank Account, User Name, Password And Other Significant Data. CR1 Ransomware Will Affect The Computer....
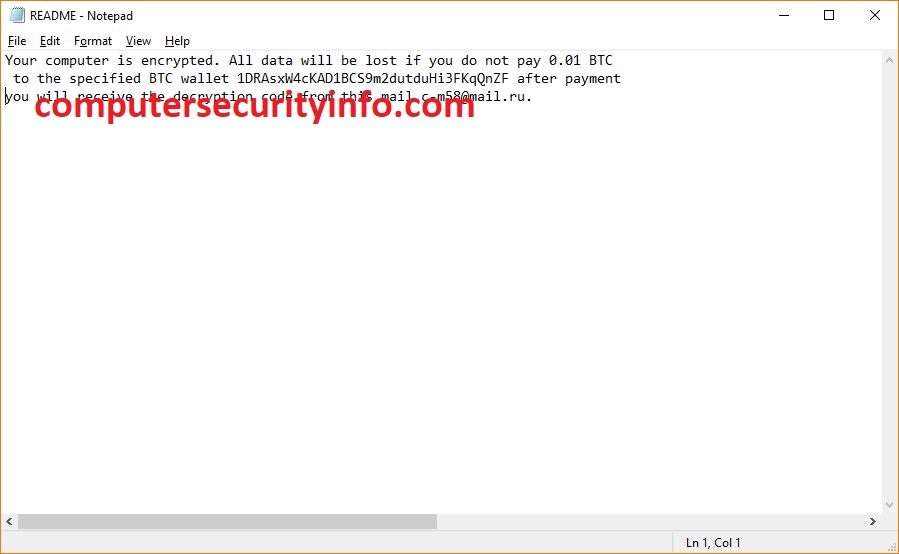
Category: Ransomware | Date: 4th February 2023
Thanatos Is A Jeopardy Ransomware Code, Which Can Fabricate Your System Program And Hack The Whole Function Along With Application, Which Was Pre-installed Into The Computer System. Thanatos Is A Crypto Computer Virus, That May Turn Into The Ransomware Program Which Belongs To Crypto Kin. First,....
Category: Ransomware | Date: 3rd February 2023
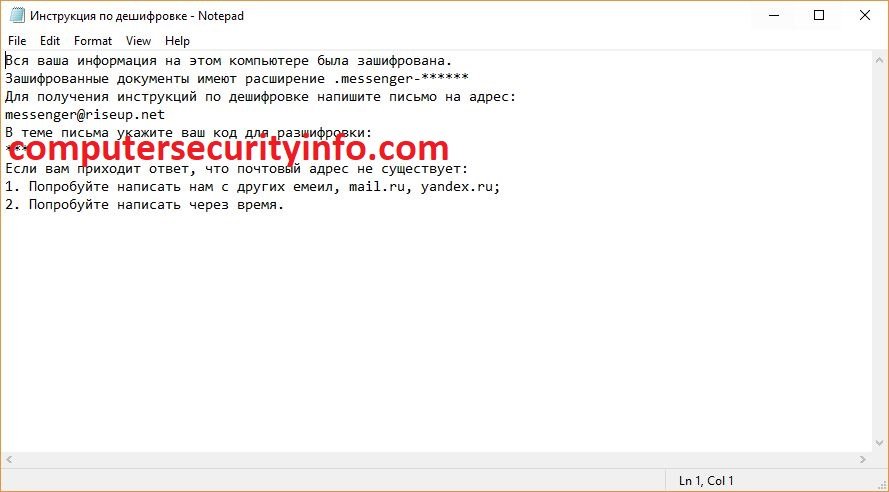
Russenger Is A Jeopardy Ransomware Program For The Computer System That Can Encrypt Ransomware Trojan, Which Was Perceived On 19 February 2018. The Phishing E-mail Or Mail Messages Is The Main Accountable To Spread Every Where In The Cyber Network. The Phishing E-mail Has Contained Perverted File....
Category: Ransomware | Date: 3rd February 2023
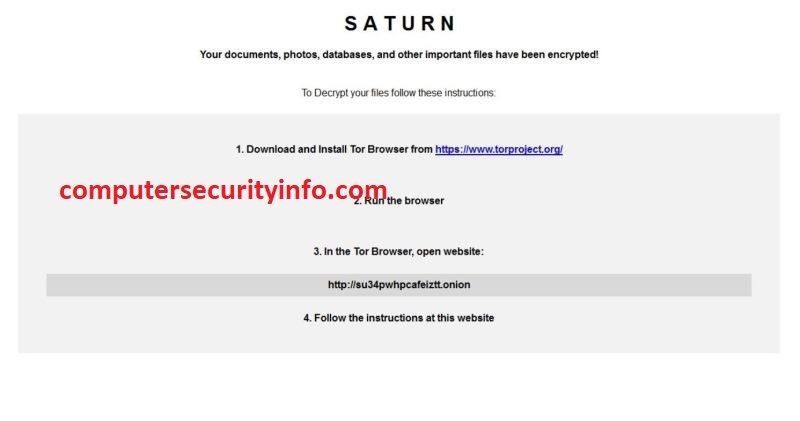
Saturn Virus Is The New Name Of Ransomware, Which Is Pertaining With The Planet, But The Cyber Network, Saturn Is A Jeopardy Ransomware Code, To Cripple Many Computer Security Software As Well As The Firewall Application. Saturn Ransomware Malware Can Ruin Security Hedge. Saturn Ransomware Virus....
Category: Ransomware | Date: 3rd February 2023
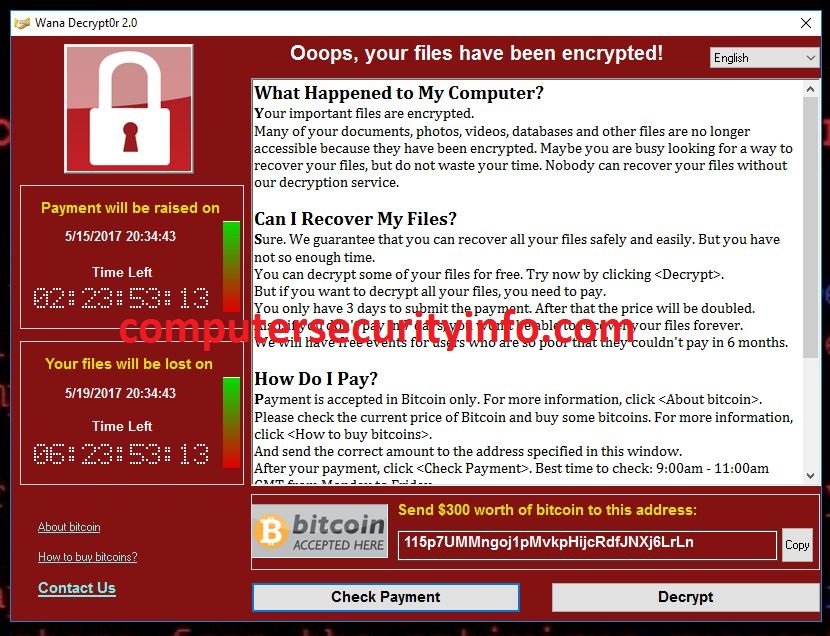
Wana Decrypt0r Is A File Encryption Ransomware Program To Encrypt The File, Folder, Database, Images, Video, And Installed Software Or Tools. Wana Decrypt0r Has Been Crafted By The Group Of Miscreant Professional To Earn As Well As The Steal Information From The Compromise Computer System. Wana....

Category: Ransomware | Date: 3rd February 2023
NLAH Ransomware Program Is Encrypting The Information, Files, Videos, Images, Database And Tools, While The Process Is Not End. NLAH Ransomware Is A Vile Or Treacherous Code To Display Ransom Note In The Text Form, Where To Victimize Users As Well As Victims, For Culprit For Doing Infringements,....
Category: Ransomware | Date: 3rd February 2023
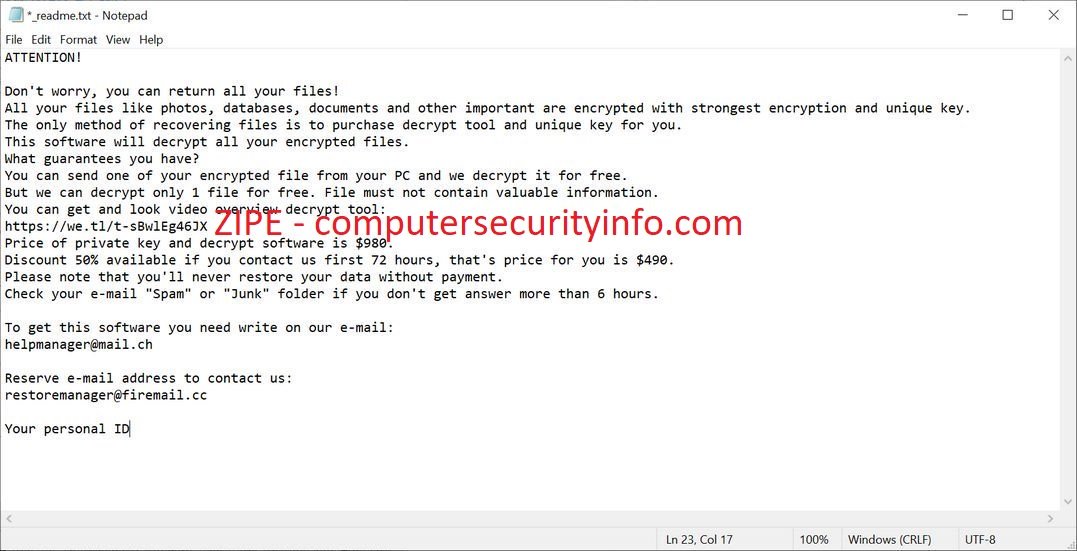
ZIPE Ransomware Has Been Designed By The Perpetrators For Their Own Interest And Generates The Online Revenue From The Illegitimate Source. ZIPE Is A File Encrypting Code To Encrypt The Whole PC Terminal, Including Files, Videos, Audios, Pics, Database And Small App. ZIPE Ransomware Is Written In....

Category: Ransomware | Date: 3rd February 2023
Banks1 Is A PC Virus And Treacherous Code For The Terminal. Banks1 Ransomware Encrypt The Computer Files, Images, Videos, Audios And Database. Banks1 Ransomware Is A Crypto-malware Code Written In The Python Programming Language, And It Encodes Information Using The AES (Advanced Encryption....
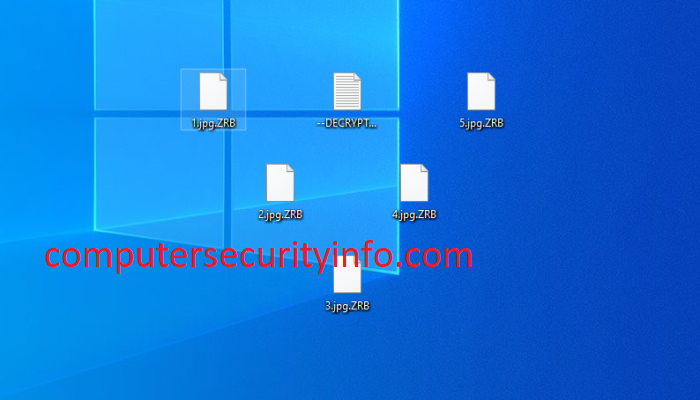
Category: Ransomware | Date: 3rd February 2023
ZORAB Ransomware Is An Encryption Ransomware Code, That Was First Perceived By The PC System Security Researchers On 15 December, 2017. ZORAB Ransomware Is Crippled Internal Function To The Owner Of The Computer System Or PC Workstation To Access The PC’ Files And Software. ZORAB Ransomware....

Category: Ransomware | Date: 3rd February 2023
Space Is Very Obfuscated Program, That Can Elude The User From The Main Goal. Why This Application Can Create Chaos? Unfortunately, Space Is A Vicious As Well As The Dangerous Ransomware Program, Which Has Been Designed By The Cyber Crooks For Their Own Or Individual Interest. Space Has Possible To....
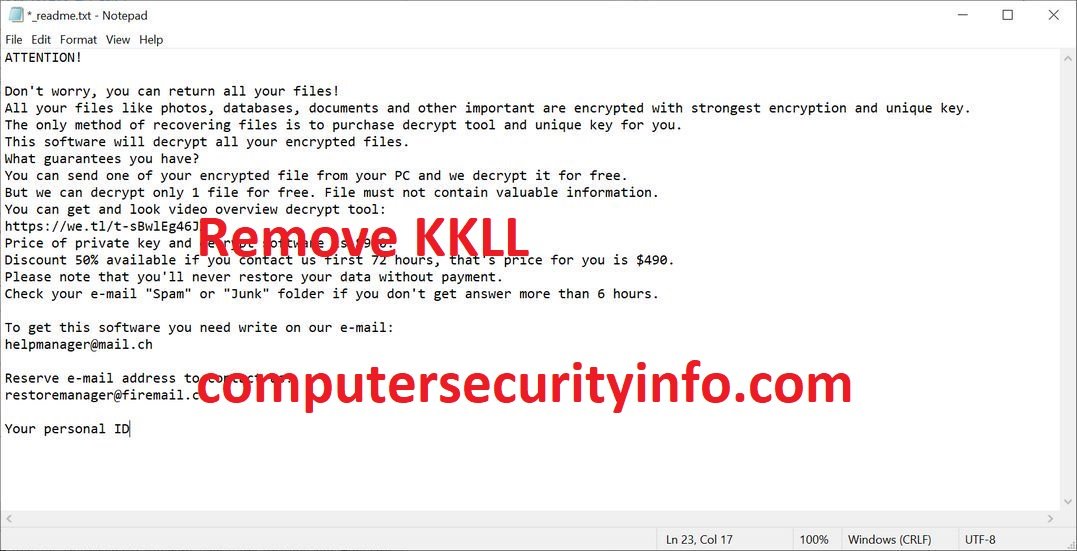
Category: Ransomware | Date: 3rd February 2023
F-Secure ID Protection - Avoid online identity theft with 24/7 data breach monitoring and a password vault that makes signing in to your accounts easier and safer. ID PROTECTION comes with these benefits ALERTS AND GUIDANCE If a data breach occurs and your information is exposed, we will....
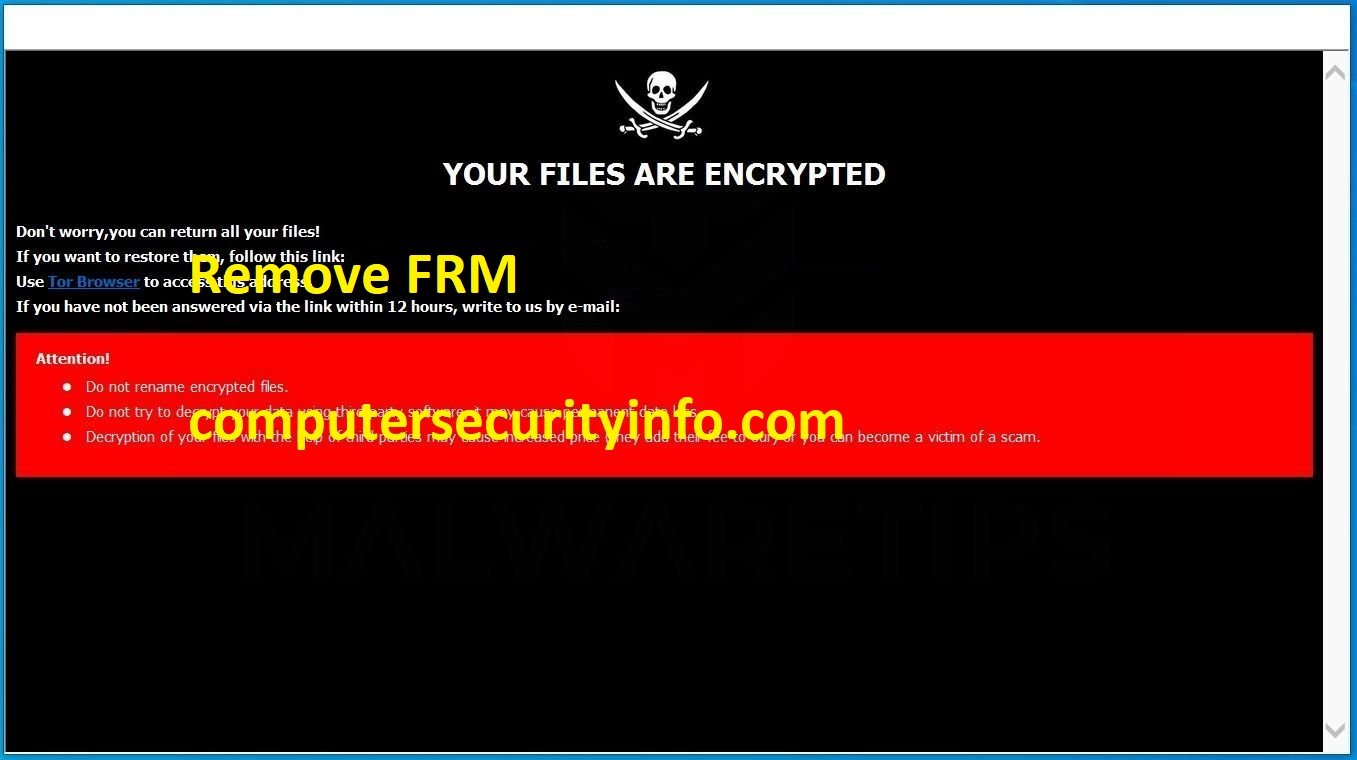
Category: Ransomware | Date: 3rd February 2023
F-Secure ID Protection - Avoid online identity theft with 24/7 data breach monitoring and a password vault that makes signing in to your accounts easier and safer. ID PROTECTION comes with these benefits ALERTS AND GUIDANCE If a data breach occurs and your information is exposed, we will....
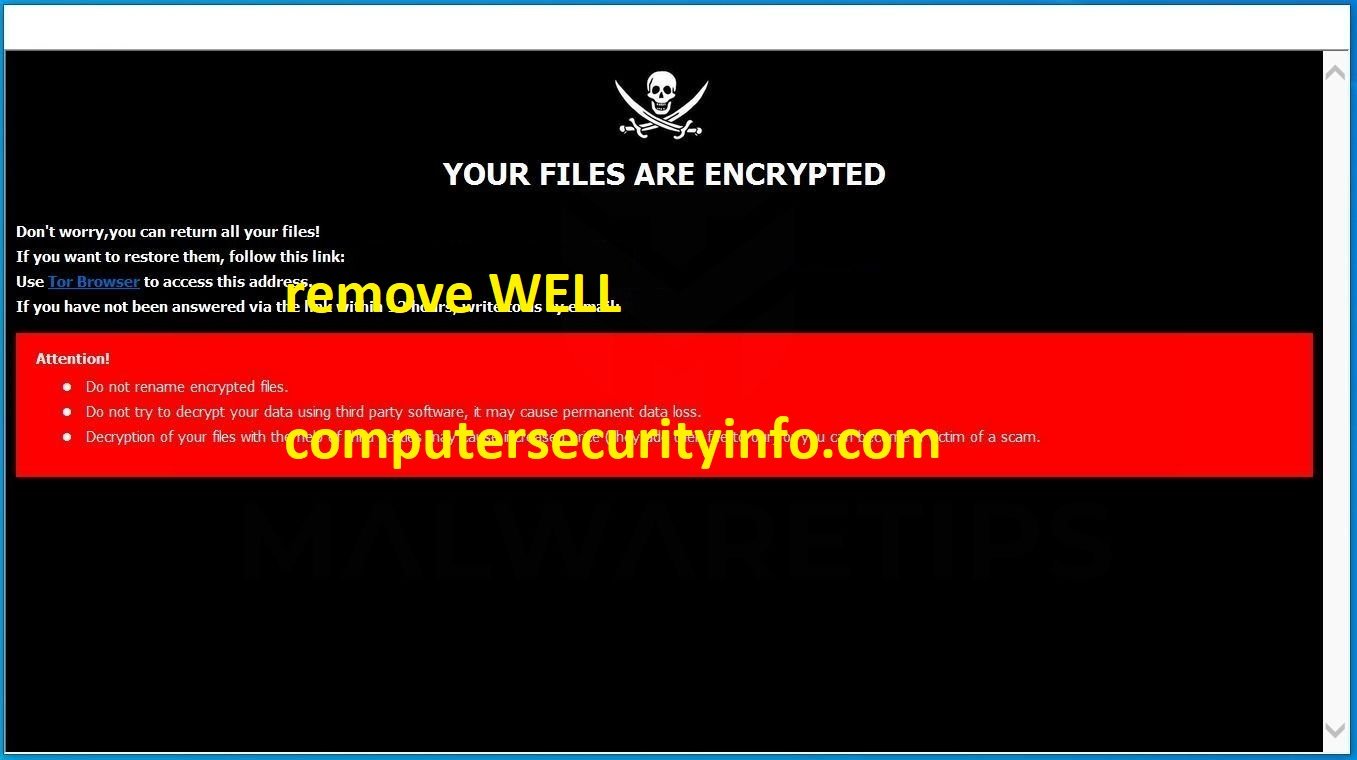
Category: Ransomware | Date: 3rd February 2023
WELL Ransomware Is Involves Various Illegal Activities And Cripples Several Significant Files, Musics, Videos, And Databases. The Cyber Security Researchers Detected Specimen Of A Normal File Cryptor Titled, Which Is Name As ‘Ransomware Cryptolocker.pdb’, That Was Acknowledged To A....

Category: Ransomware | Date: 2nd February 2023
BOMBO Is A Jeopardy Ransomware Application Or Code, That Is Disable The Entire Action, While Download As Well As Install Into The Victim’s Computer System. How Can You Comprehend That, Your System Has Been Pretentious By The BOMBO Ransomware. If Your Files And Folders Has Been Pretentious....
Category: Ransomware | Date: 2nd February 2023
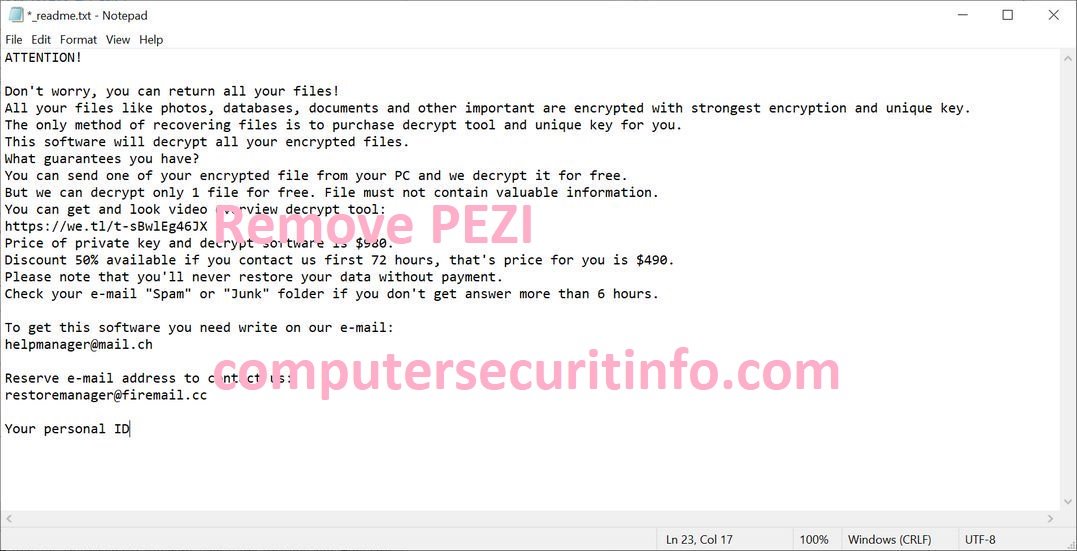
PEZI Is A Vicious As Well As Treacherous Ransomware Code. The PEZI Is Encrypting The Files And Folders Randomly. The PEZI Can Staggeringly Block The Significant Action Or Process Inside The Computer System. PEZI Ransomware Is A Worst Terminal Threat, Which Is Active Astonishingly On The Computer....
Category: Ransomware | Date: 2nd February 2023
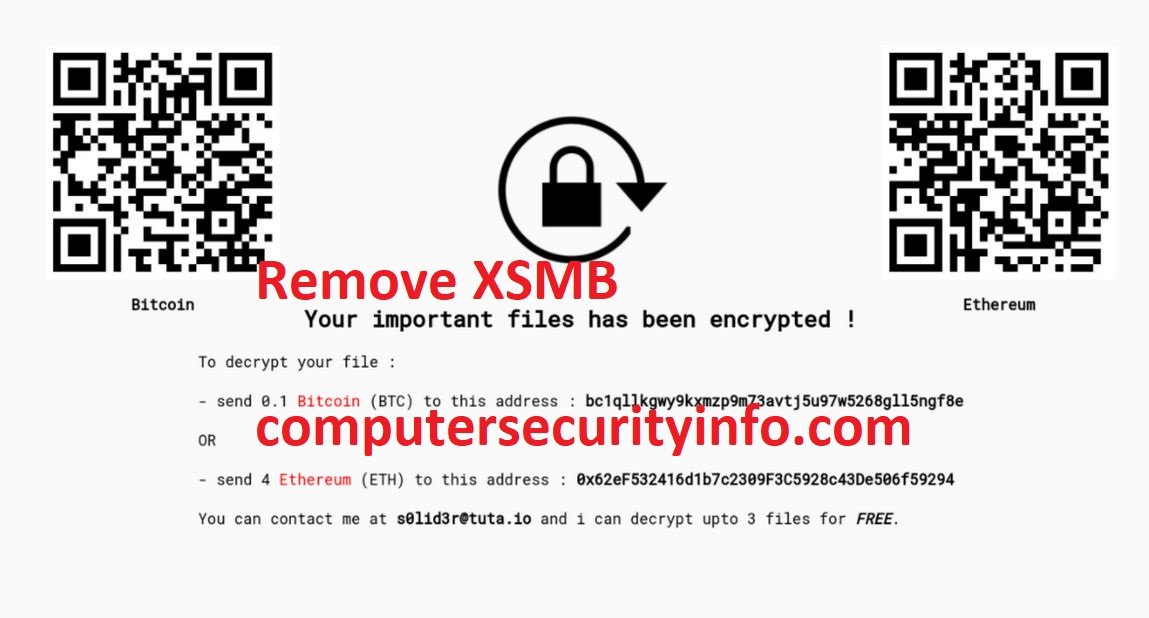
XSMB Is A Browser Extension Program, Which Is A Spreading The Ransomware Program, That Is Called As A Dharma Ransomware. XSMB Is An Infiltrate Your Computer System Through Spam Mail, Fake Junk Email And Others Sources. However, Dharma Ransomware Is A New Type Of File Encrypting Code To Encrypt The....
Category: Ransomware | Date: 2nd February 2023
CORONA-LOCK Is A Treacherous Browser Extension Program, Which Is A Spreading The Ransomware Program, That Is Called As A Dharma Ransomware. CORONA-LOCK Is An Infiltrate Your Computer System Through Spam Mail, Fake Junk Email And Others Sources. However, Dharma Ransomware Is A New Type Of File....

Category: Ransomware | Date: 2nd February 2023
BANG Is A Deceitful Browser Extension Program, Which Is A Spreading The Ransomware Program, That Is Called As A Dharma Ransomware. BANG Is An Infiltrate Your Computer System Through Spam Mail, Fake Junk Email And Others Sources. However, Dharma Ransomware Is A New Type Of File Encrypting Code To....
Category: Ransomware | Date: 2nd February 2023
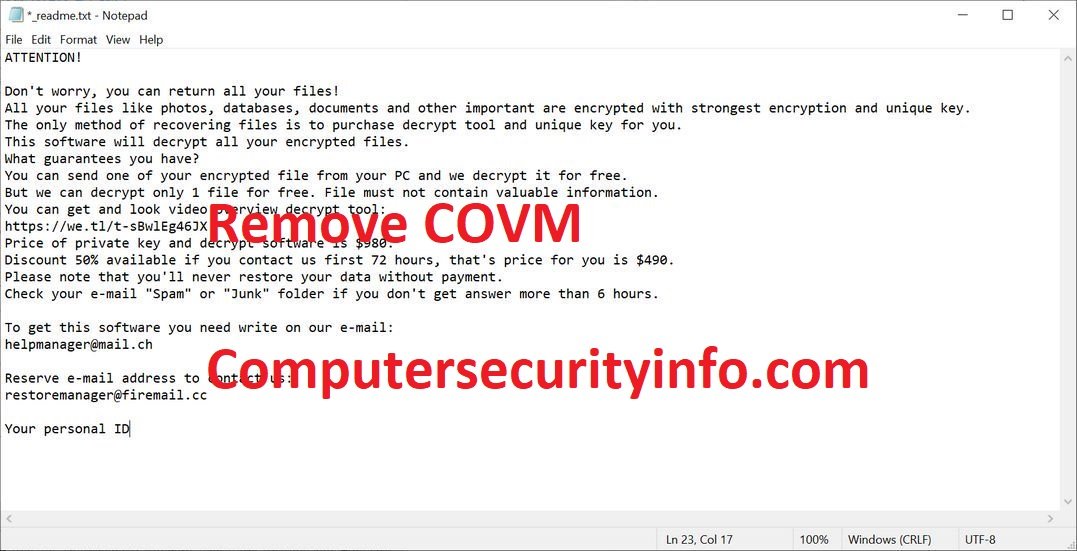
COVM Is A Deceitful Browser Extension Program, Which Is A Spreading The Ransomware Program, That Is Called As A Dharma Ransomware. COVM Is An Infiltrate Your Computer System Through Spam Mail, Fake Junk Email And Others Sources. However, Dharma Ransomware Is A New Type Of File Encrypting Code To....
Category: Ransomware | Date: 2nd February 2023
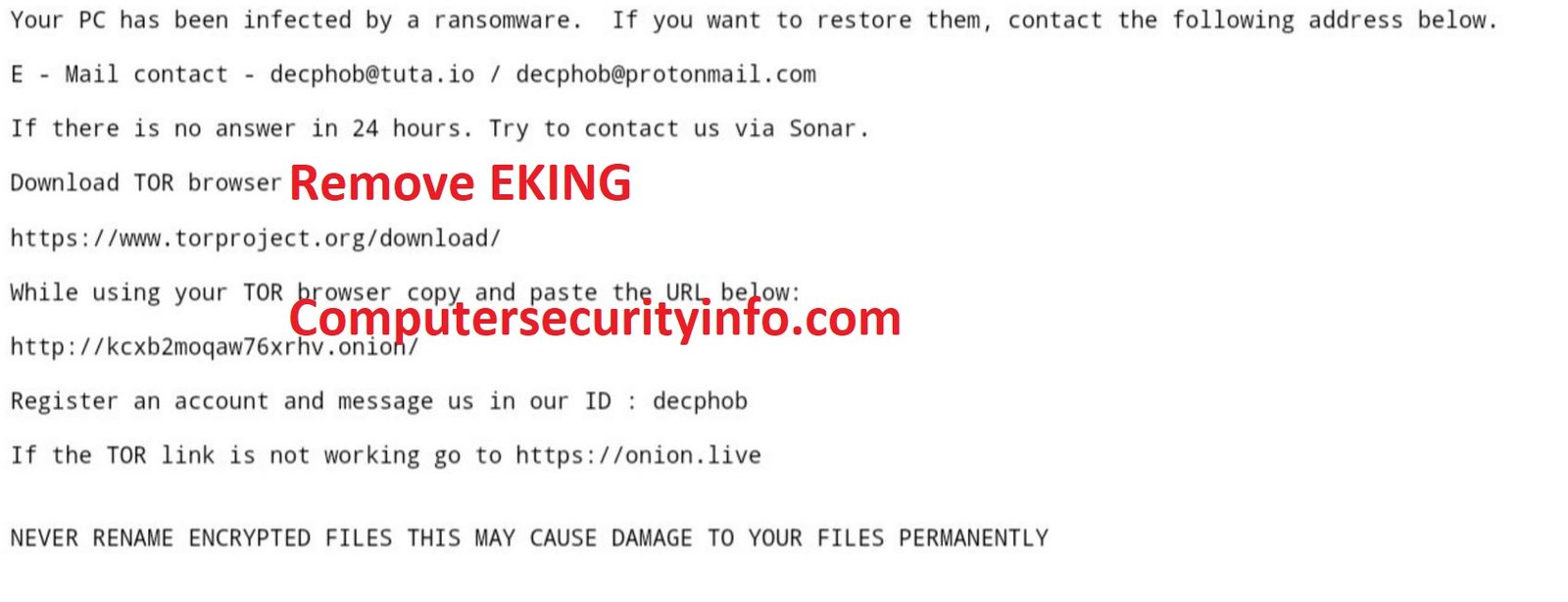
EKING Is A Deceitful Browser Extension Program, Which Is A Spreading The Ransomware Program, That Is Called As A Dharma Ransomware. EKING Is An Infiltrate Your Computer System Through Spam Mail, Fake Junk Email And Others Sources. However, Dharma Ransomware Is A New Type Of File Encrypting Code To....
Category: Ransomware | Date: 2nd February 2023
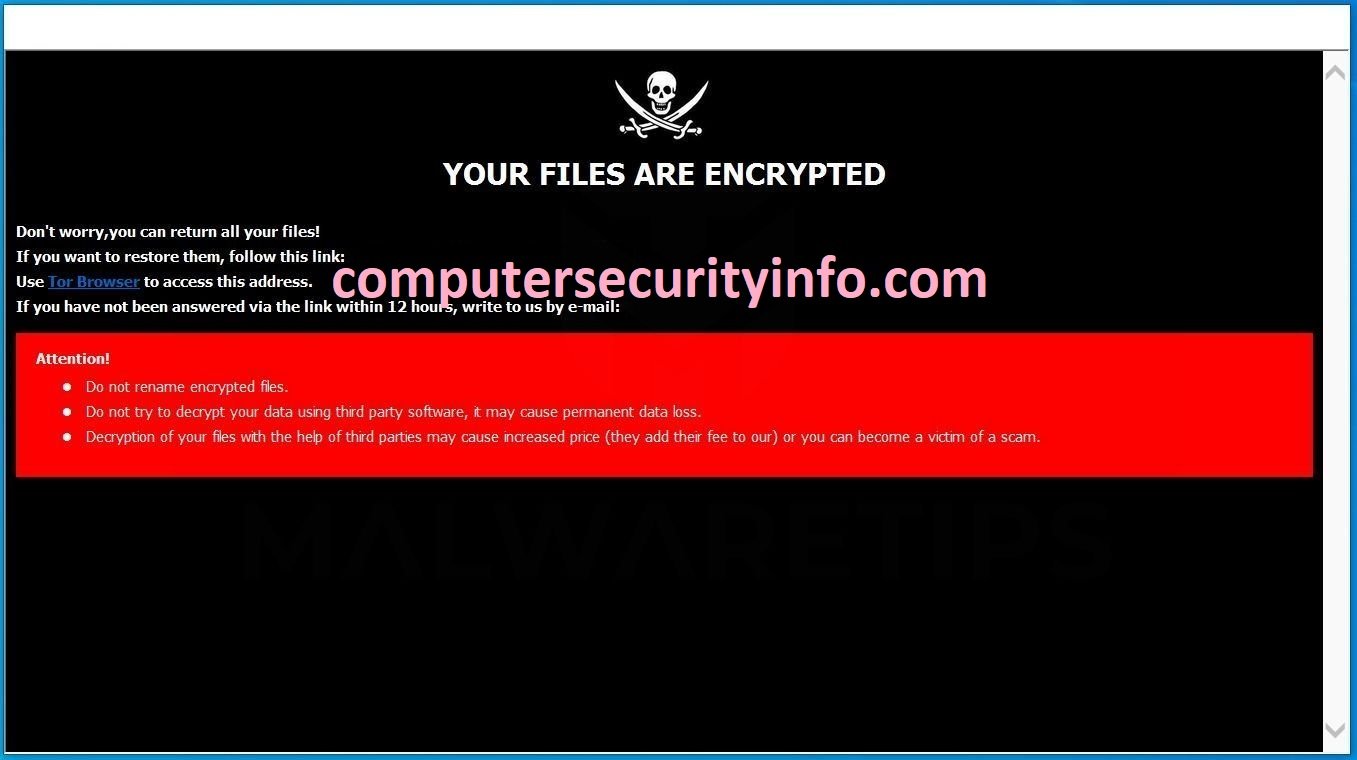
WCH Is Another Types Of Ransomware Program, That Can Contain The Character Of The Trojan Virus Based On The This Treacherous Or Horrible Ransomware Code. November 2017, Was A Month To Perceived In WCH Ransomware. In Midst Of May 2018 And July 2018, Cyber Security Experts Have Noted Various Types Of....
.jpg)
Category: Ransomware | Date: 2nd February 2023
PGP Is A Very Common Ransomware Code, Which May Flourish By The Spam Mail, And Freeware Executable File Like (.exe) And Dynamic Link Library (.dll). PGP Is A Part Of The PGP Ransomware Program, That Can Contain The Characteristic Of The Trojan Virus. PGP May Possible To Counter Various Security....

Category: Ransomware | Date: 2nd February 2023
Frogo Is A Mail Extension That Can Use For Sending Email. Its A Normal Perception Develop By The User. Unfortunately, Frogo Is A Part Of The Crypto-virus Ransomware Program, That Can Foray The Innocent Users And Capture The Terminal. Crypto-virus Ransomware Is A File Encrypting Code To Encrypt The....

Category: Ransomware | Date: 2nd February 2023
ZWER Ransomware Encrypts The Personal Documents, Music Files, Video Files, Databases, And Private Networks Files. ZWER Ransomware Has Been Crafted By The Cyber Perpetrators, That Would Utilize ZWER Ransomware As A Revenue Generating Tools From The Internet. ZWER Ransomware Was Placed A Message On....
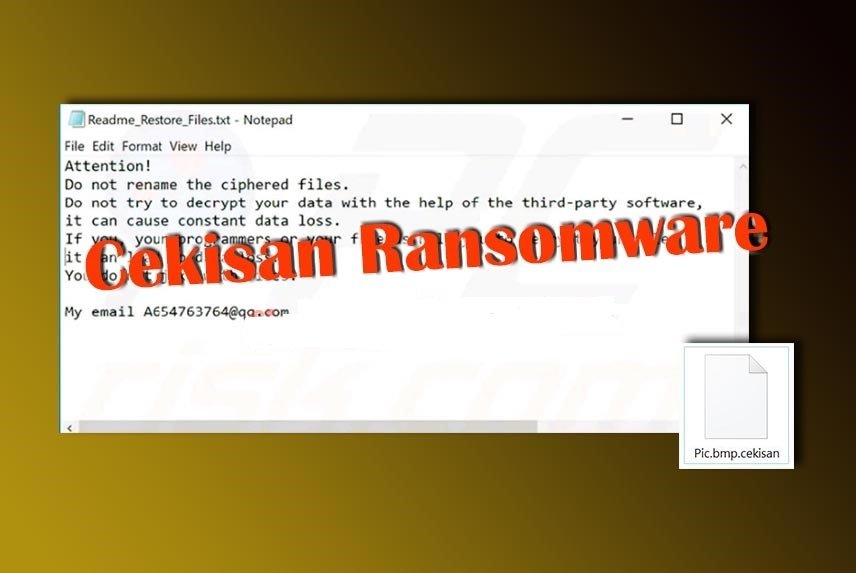
Category: Ransomware | Date: 2nd February 2023
cekisan Is An Appeared With ‘.cekisan File Extension’ Ransomware Virus. The Cekisan Ransomware Foray Were The First Reported On February 20, 2019. The ‘.cekisan File Extension’ Ransomware Looks A Like A Distinguish Malware Program, That Can Create Threats Perception And....

Category: Ransomware | Date: 2nd February 2023
Snatch Is An Appeared With ‘.snatch File Extension’ Ransomware Virus. The Snatch Ransomware Foray Were The First Reported On December 26, 2018. The ‘.snatch File Extension’ Ransomware Looks A Like A Distinguish Malware Program, That Can Create Threats Perception And....
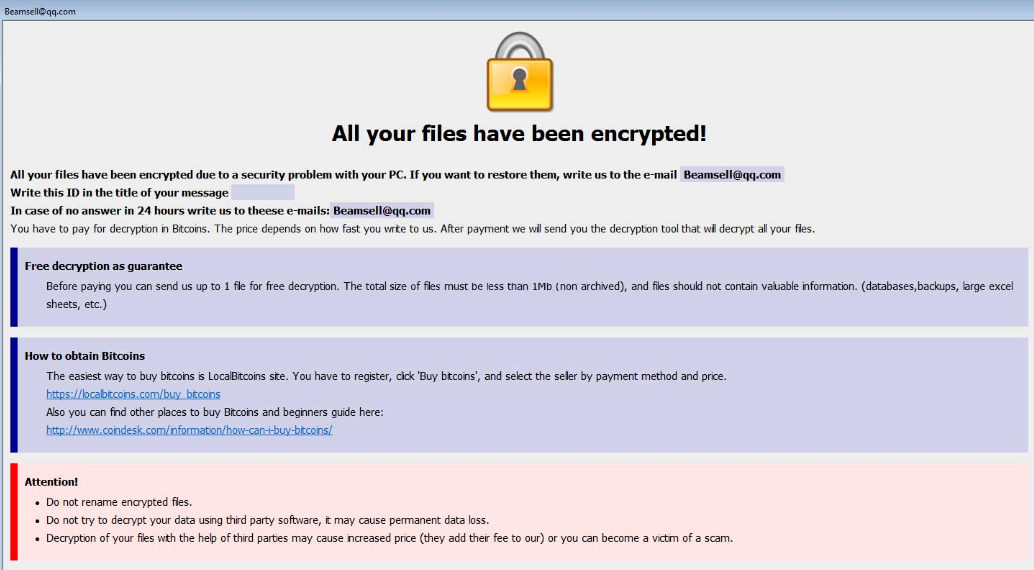
Category: Ransomware | Date: 2nd February 2023
Jupstb Is An Appeared With ‘.jupstb File Extension’ Ransomware Virus. The Jupstb Ransomware Foray Were The First Reported On February 14, 2019. The ‘.jupstb File Extension’ Ransomware Looks A Like A Distinguish Malware Program, That Can Create Threats Perception And....
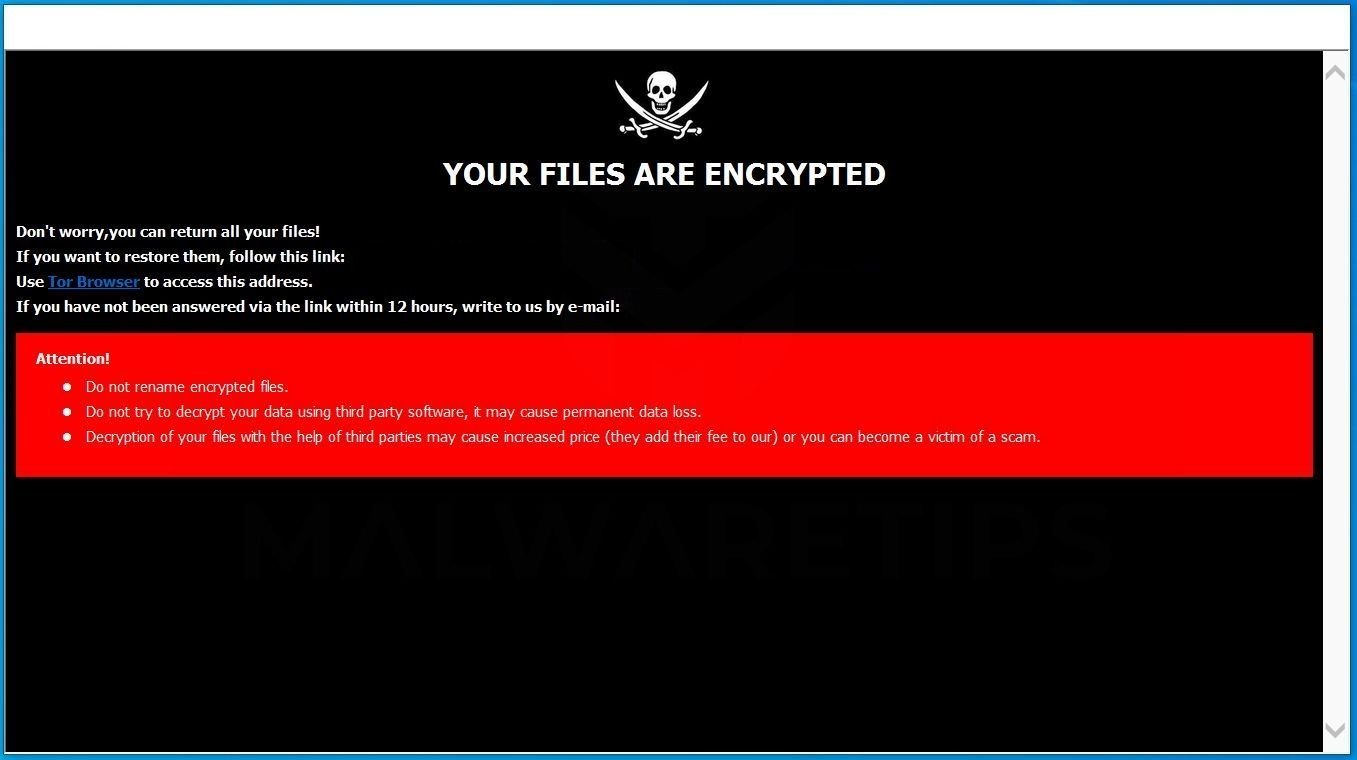
Category: Ransomware | Date: 2nd February 2023
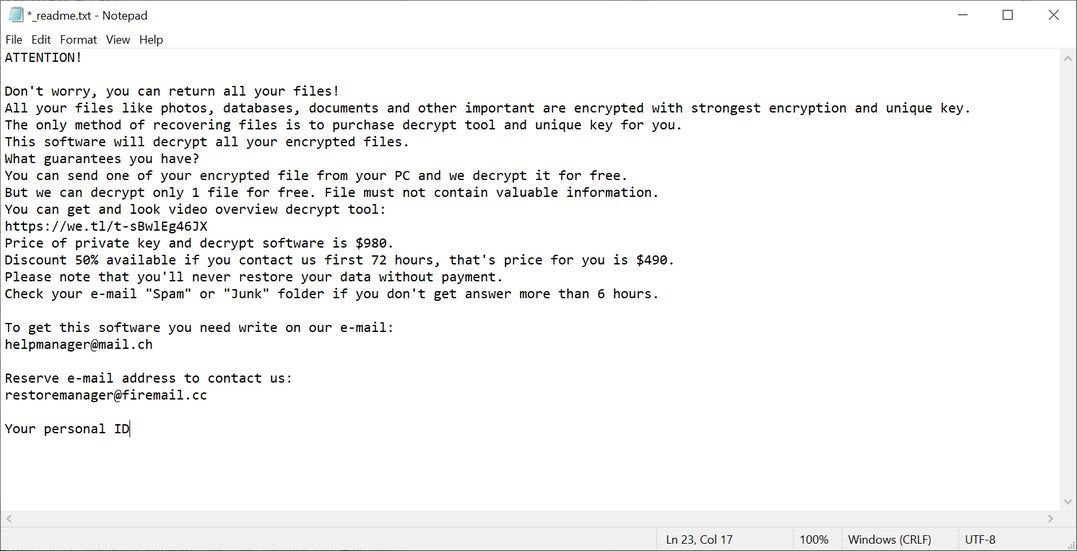
[dr.decrypt@aol.com].dr ransomware Is A Destructive Computer Program, That Must Invade The Terminal Without Any Warning As Well As Genuine Message. [dr.decrypt@aol.com].dr Ransomware Is A Treacherous Internet Bug, Which Has Been Developed By The Perpetrator For The Purpose Of Generating....
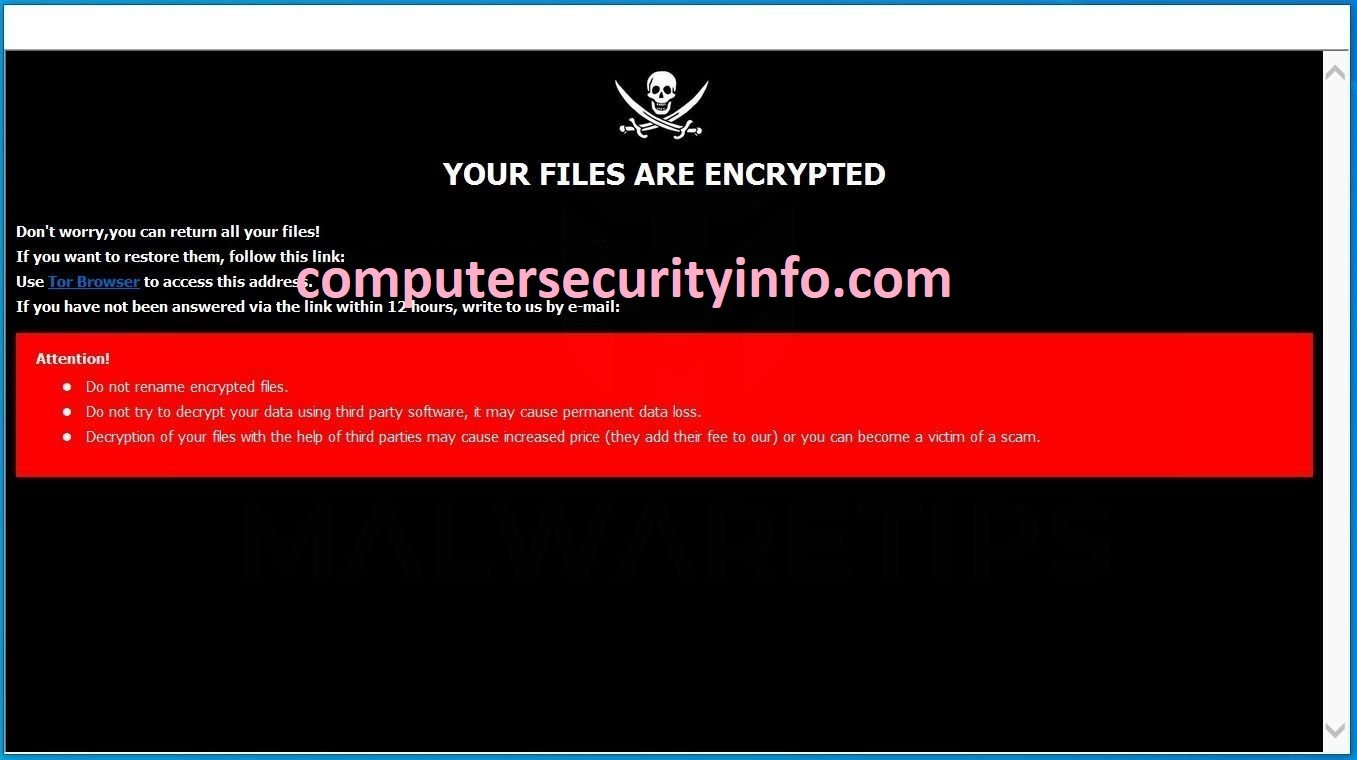
Category: Ransomware | Date: 2nd February 2023
NYPD Is A Precarious ransomware Internet Virus, That Has Been Created By The Cyber Criminal For The Purpose Of Hacking The Computer System. NYPD May Extract Information From The Victim’s Computer System, As Well As The Activities, Session Data And More. NYPD Has Capacity To Disrupt....
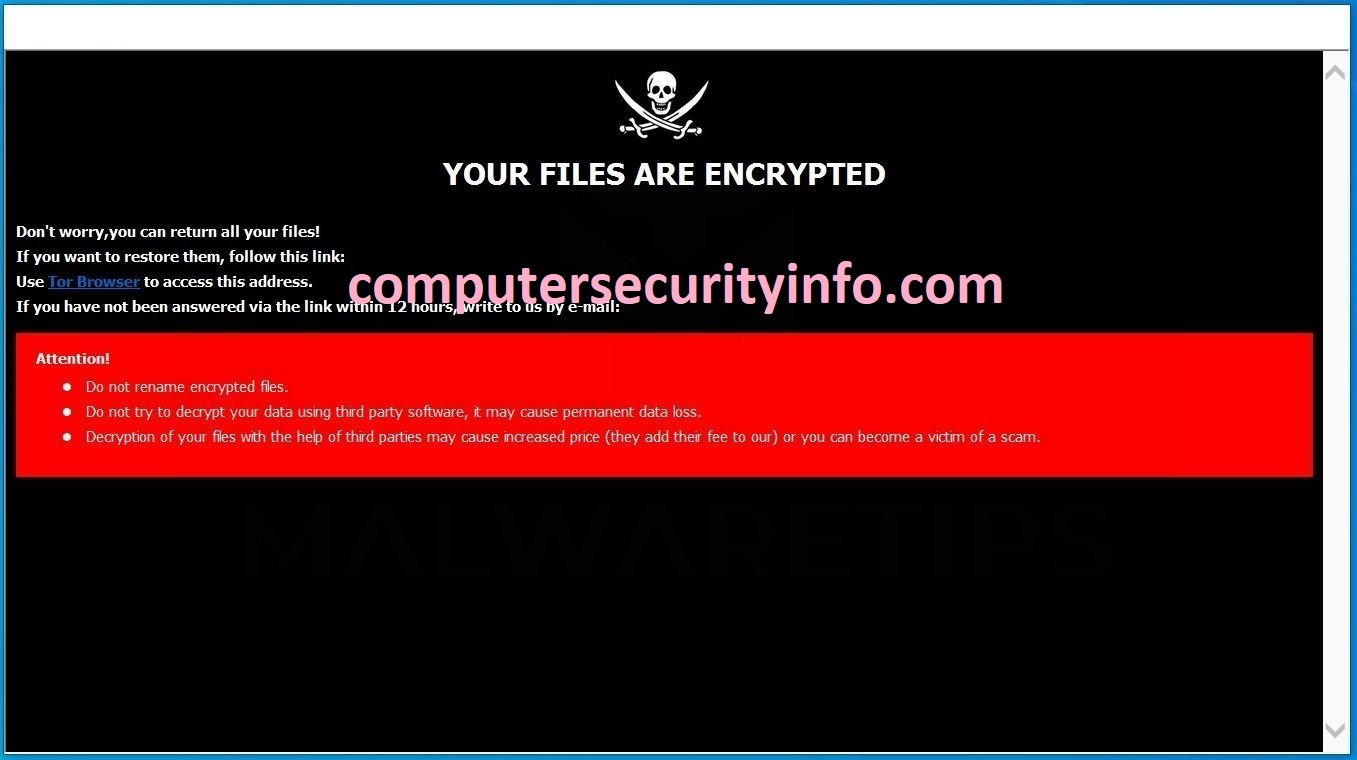
Category: Ransomware | Date: 1st February 2023
HLLP Is A Dangerous Ransomware Program, Which Can Encrypt Your Significant Files, Folders, Musics, Images, Databases And Other Pertaining Tools. HLLP Will Access Your PC Terminal By The Help Of Freeware Software. The Shareware Programs Are Responsible To Carry Irrelevant Program And Spam Links. You....
Category: Ransomware | Date: 1st February 2023
BASE Is A Menacing Ransomware Program That Is A Kin Of malware. BASE Is A Encryptor Virus, Which Can Encrypt Hundreds Of PC Files. BASE May Need To Send Money Behalf Of Decrypter Key, Which Can Help To Normalize The PC And Run All Program Smoothly. BASE Ransomware Program May Reach Your PC Any....
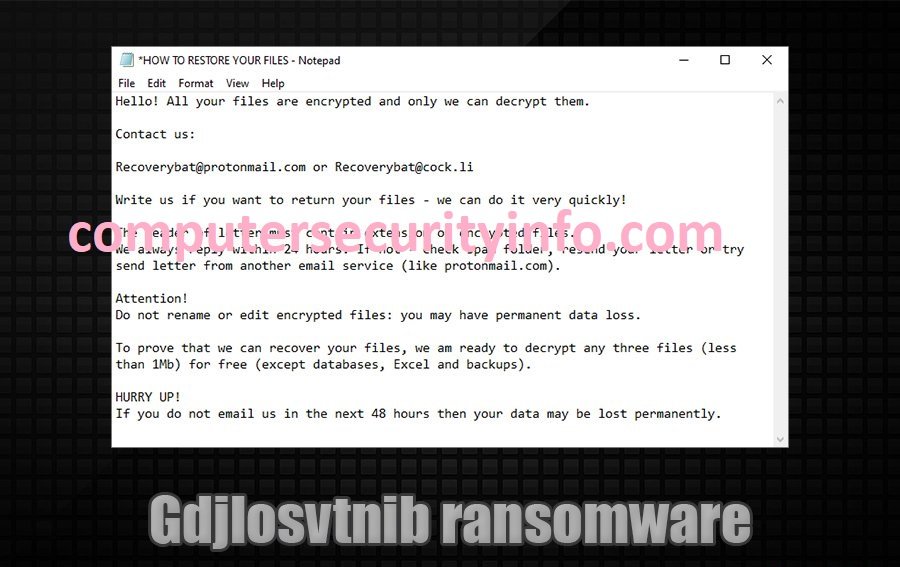
Category: Ransomware | Date: 1st February 2023
Gdjlosvtnib Is A Very Strange Name In The Cyber Network. Gdjlosvtnib Has Been Declared As A Ransomware Program. Gdjlosvtnib Is Pertaining With Snatch Ransomware Kin. Gdjlosvtnib Is A Data-locker Code As Well As trojan virus program. The Phishing Email Is Used To Spread Gdjlosvtnib Ransomware.....
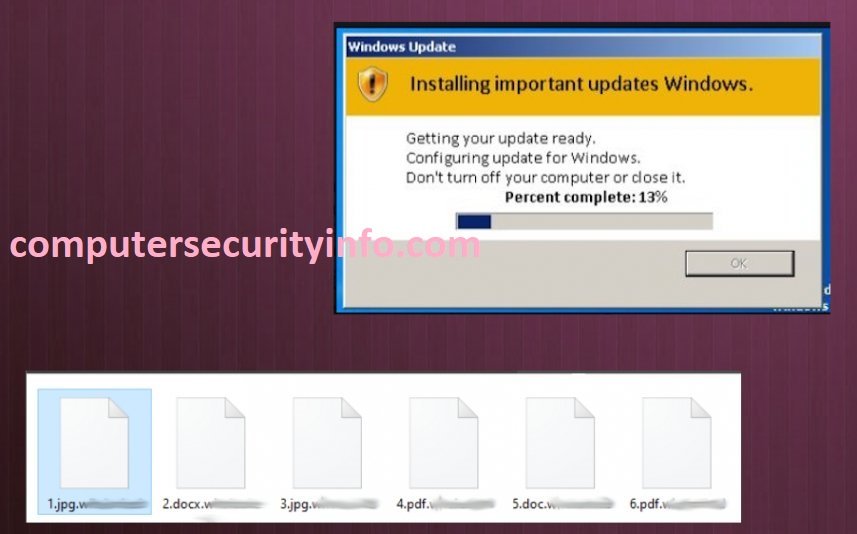
Category: Ransomware | Date: 1st February 2023
If Your System Has Not Been Boot While You Can Try More Than 2 Times, Then You May Comprehend That Your Computer System Has Been Hacked By The REPL Ransomware Program. REPL Ransomware Malware Has Ability To Counter Any Obsolete Security Based Computer System. You May Use Advanced Security Software....
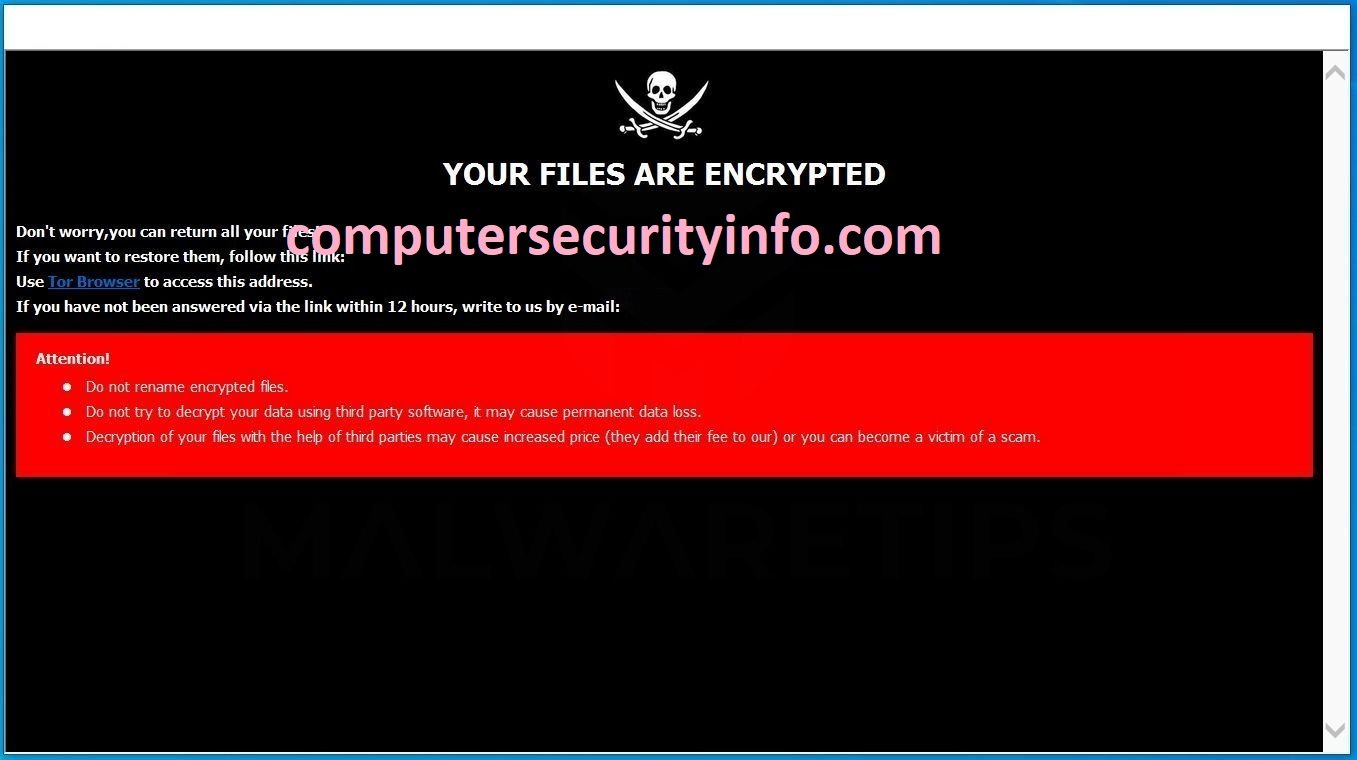
Category: Ransomware | Date: 1st February 2023
NULL Is New Genre Of ransomware program, Which Has Contain The Character Of trojan virus. NULL Will Not Directly Engage With Victim. NULL Ransomware Has Been Used Trojan Virus Program To Infiltrate The Computer System And Steal Significant Data As Well. NULL Ransomware Encrypts The Files,....

Category: Ransomware | Date: 1st February 2023
KUUS Ransomware Has Been Fabricated By The Professional For Their Own Goals. KUUS Ransomware Has Ability To Engage Various Website As Well As Security System. However, KUUS Ransomware Is A Pertaining With DJVU Kin. KUUS Ransomware Encrypts Many Important Files And Document Such As Videos, Images,....
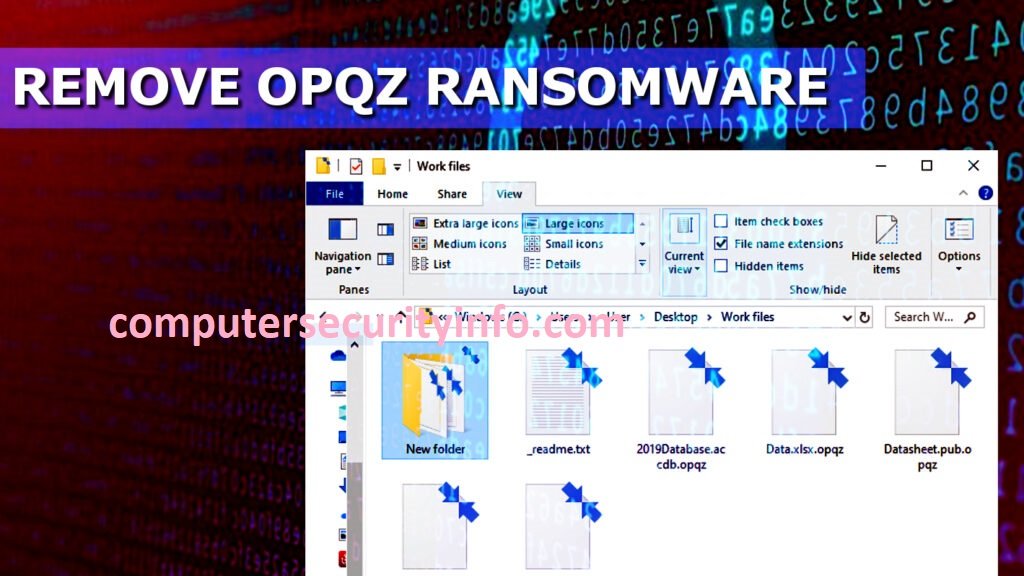
Category: Ransomware | Date: 16th January 2023
OPQZ Ransomware Is A Malevolent Application, That Has Been Pertaining With DJVU Ransomware Family. OPQZ Ransomware Is Designed To Encrypts The Significant Files, Creates Unwanted Files, Updates The File Name And Generates The Ransom Message. OPQZ Ransomware Is A File....

Category: Ransomware | Date: 16th January 2023
HOMER Ransomware Is A Pertaining With Dharma Ransomware Kin. HOMER Malware Scanned Is Credited To The Marcelo Rivero. HOMER Ransomware Encrypts Many Files And Application, Such As Database Files, Images Files, Video Files And More. HOMER Ransomware Always Asking Ransom Money Behalf Of Decryption....
Category: Ransomware | Date: 12th January 2023
GNS Is A Pertaining With Dharma Family Ransomware Program. GNS Will Encrypts The Data, Files, Folders. GNS Ransomware Designer Are Demanding The Ransom Money To Normalize The Computer System. When GNS Ransomware Reside In The Compromised Computer System, While User Never Access Any File And....
Category: Ransomware | Date: 12th January 2023
Felix Ransomware Has Been Scanned By The Jakub Kroustek. Felix Is The New Name Of The Ransomware, Which Is Pertaining With Dharma Ransomware Family. Thus, Felix Ransomware Has Been Contaminated Computer System And Peripheral Devices. Felix Ransomware Encrypts The Files, Videos, Images, Databases....

Category: Ransomware | Date: 10th January 2023
BMTF Is The Name Of Ransomware Code, Which Is Pertaining With Dharma Ransomware Family. BMTF Inceptions Of Encrypting The Windows Operating System Files, Videos, Images, Databases And Other Significant Items. BMTF Ransomware Behaves Very Bitter Against The Computer System. BMTF Ransomware Send The....
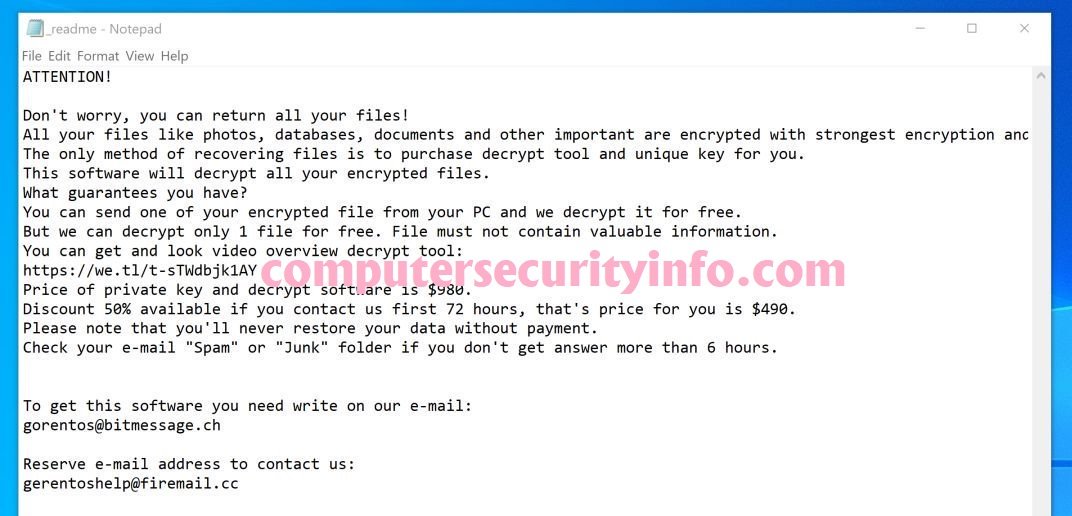
Category: Ransomware | Date: 10th January 2023
MEDS Seems A Treacherous Ransomware Code And Pertaining With Djvu Ransomware Family. Unfortunately, MEDS Ransomware Malware Code Are Used To Encrypt Significant Files And Folders. MEDS Forces Them To Buy The Decryption Tools As Well As The Indispensable Keys. MEDS Ransomware Appends The....
Category: Ransomware | Date: 10th January 2023
Credo Ransomware Has Been Encrypted Code To Manipulate The Files Of The Windows OS, Linux, Mac OS And Other Operating System. Credo Ransomware Is Capable To Counter Number Of Security Program As Well As Firewall Software. Credo Ransomware Has Been Fabricated By The Cyber Criminal To Target The....

Category: Ransomware | Date: 10th January 2023
Gyga Is Well Known Cryptovirus Program. Gyga Is Also Pertaining With A Ransomware Kin. However, Gyga Has Been Capable To Tackle Obsolete Security System As Well As Firewall Fence. Gyga Ransomware Is An Associated With Dharma Ransomware Family. Gyga Ransomware Code Is Specially Designed To Demand....

Category: Ransomware | Date: 6th January 2023
Lxhlp Is A Vicious Ransomware Program. Lxhlp Is Also A Pertaining With Dharma Ransomware Family. Your Personal Documents, Files, Videos, Images, Musics, And Databases Files Are Encrypting By The Lxhlp Ransomware. After Encrypting The Files, Victim Can Observer That File Name Extension Is Also....
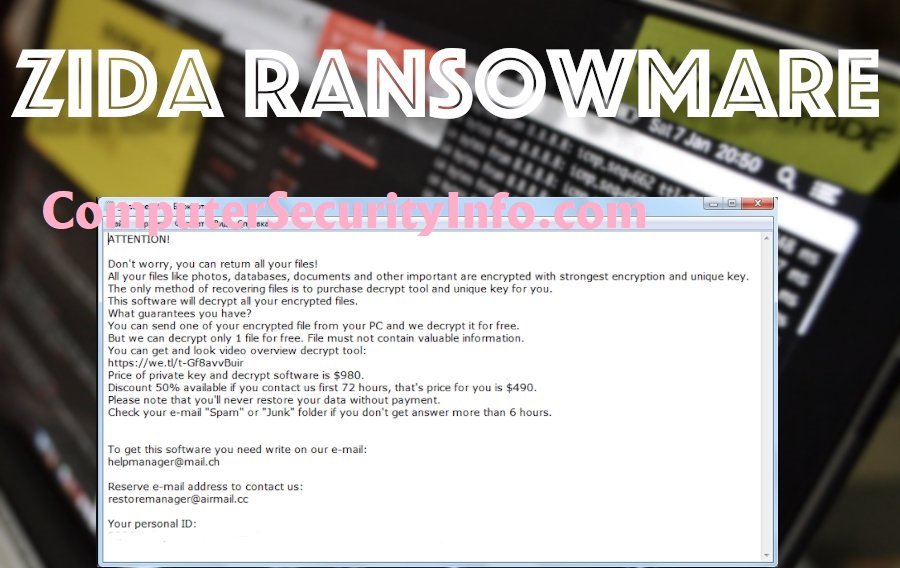
Category: Ransomware | Date: 6th January 2023
ZIDA Is A Small Code That Can Encrypt The Computer System Files, If ZIDA Code Will Run In The Terminal. However, ZIDA Has Been Declared As A Vicious Ransomware Program. Djvu Ransomware Family Is Associated With ZIDA Ransomware Code. The Computer System Has Been Compromised Along With Peripheral....
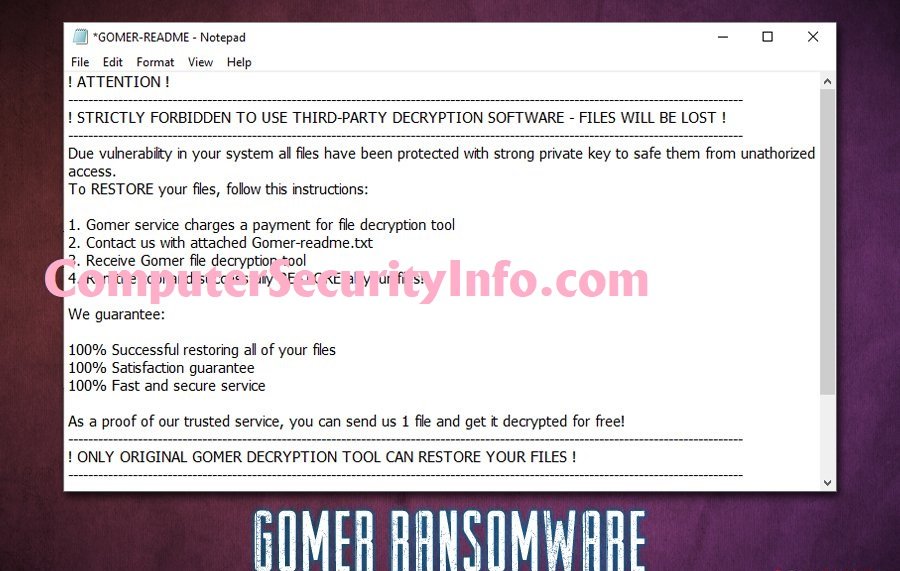
Category: Ransomware | Date: 6th January 2023
Gomer Seems A New Type Of Outsider Ransomware Code. Gomer Ransomware Was Discovered By Dnwls0719. It’s Renames Encrypted Files Through Appending The “.gomer” Ransomware Extension. For Instance, Gomer May Change A File Name Extension. Gomer Ransomware Program Encrypts Various Files....
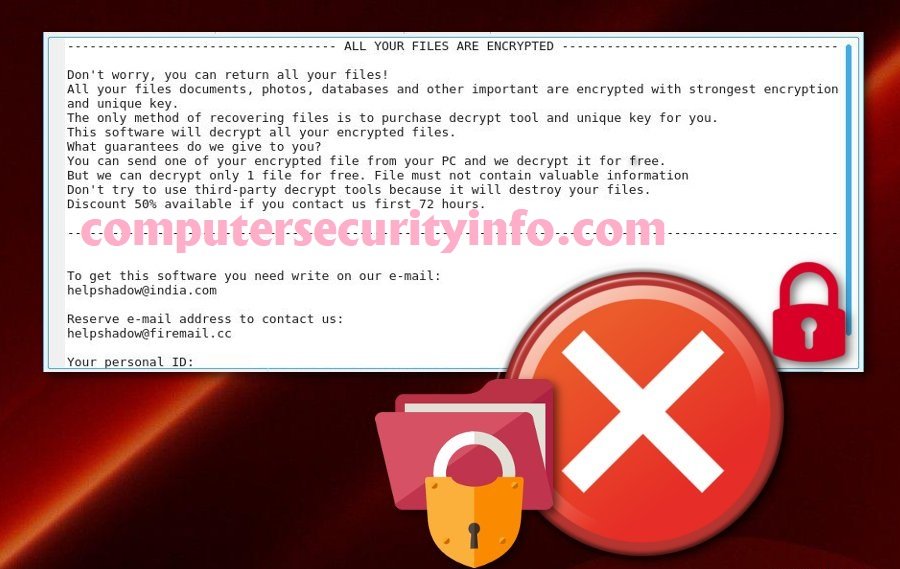
Category: Ransomware | Date: 6th January 2023
Djvu Ransomware Is A Pertaining With File-locking Computer Virus Program That Runs An Online Robot Encryption Code Which Is Associated With Algorithm To Block The Classified Personal Information. Djvu Ransomware Is Also Used An Extension To Control The File Function. The Goal Of Malware And....

Category: Ransomware | Date: 5th January 2023
PYKW Is A Name Of The Ransomware Program, Which Has Been Associated With Djvu Ransomware Family. PYKW Ransomware Encrypts The Crucial Files, Video, Images, Picture, Databases And Others. PYKW Ransomware May Demand The Ransom Money To Release The Decryption Key. PYKW Ransomware May Inception Of An....
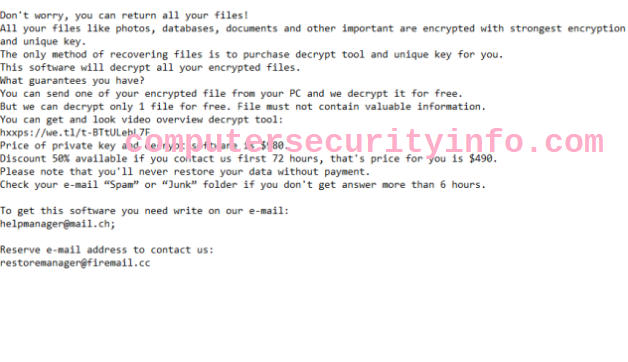
Category: Ransomware | Date: 4th January 2023
1dec Ransomware Encrypts The Files, Documents, Video, Images, As Well As Other Significant Application. 1dec Ransomware Also Encrypts The Personal Documents Like Pan Card, Aadhar Card, And Other Crucial Documents. 1dec Ransomware Could Not Work Automatically. 1dec Ransomware May Track Your Online....
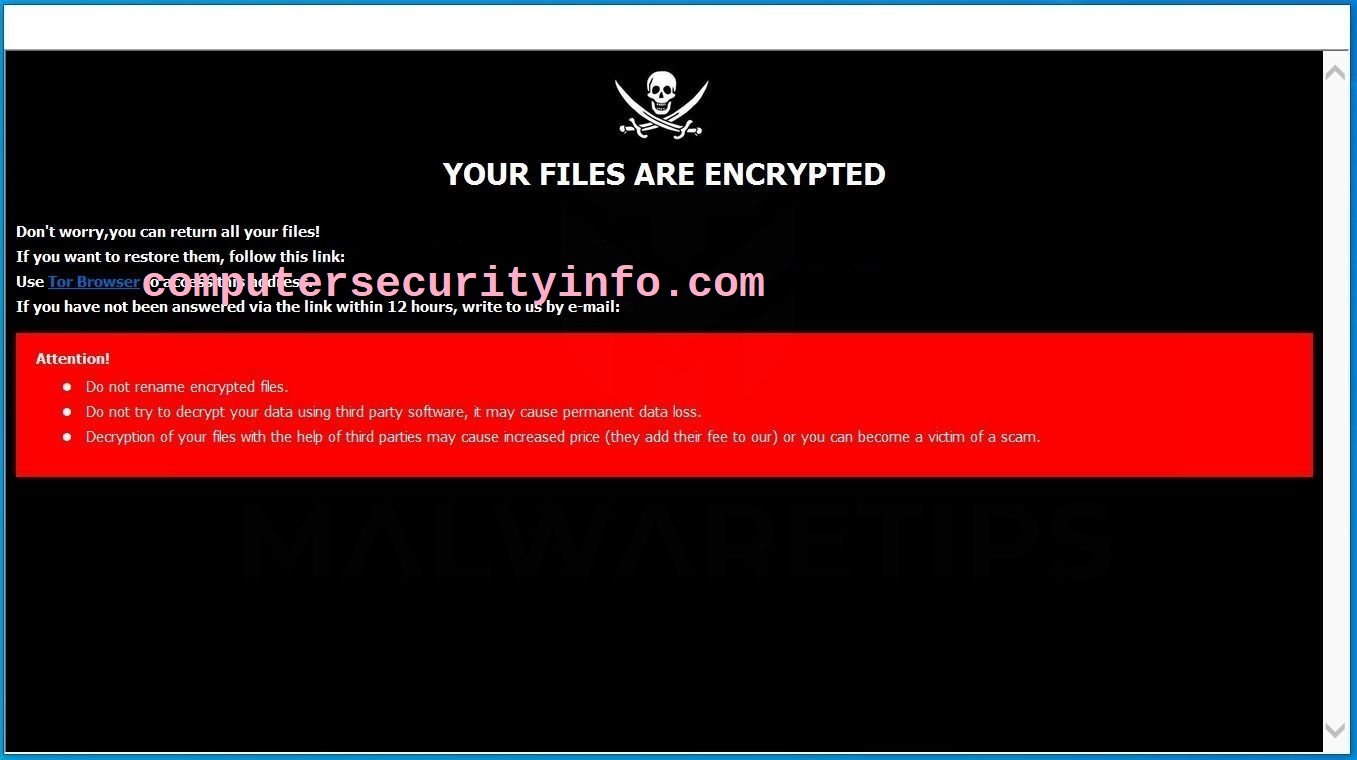
Category: Ransomware | Date: 26th December 2022
An Encryption Is The Characteristics Of The R3F5S ransomware. R3F5S Ransomware Is Corrupt The System Network, Task Manager, Database, Registry Editor And More. R3F5S Ransomware Has Been Coded By The Cyber Criminal To Target The Big Firm, Institutions, Bank And etc. However, R3F5S Ransomware....

Category: Ransomware | Date: 23rd December 2022
Kook Ransomware Is A Pertaining With DJVU Ransomware Family. Kook Ransomware Is Also Encrypting The Documents, Files, Videos, Musics Files, Images, Databases And More. Kook Ransomware May Also Involve To Send The Warning Message To Victim Regarding The Ransom Amount. Kook Ransomware Could Create A....
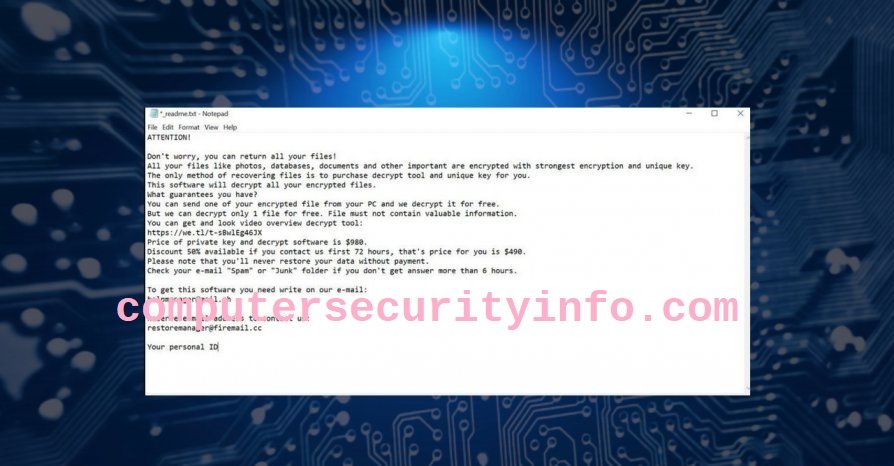
Category: Ransomware | Date: 23rd December 2022
If You Can Start The Computer Machine And Display The Blue Screen In Your Desktop Screen, Then You Should Understand That ERIF Ransomware Program Hack Your Computer Terminal. ERIF Ransomware May Inception Of The Encryption Process And Acquire The All Documents, Files, Videos, Images, Databases And....
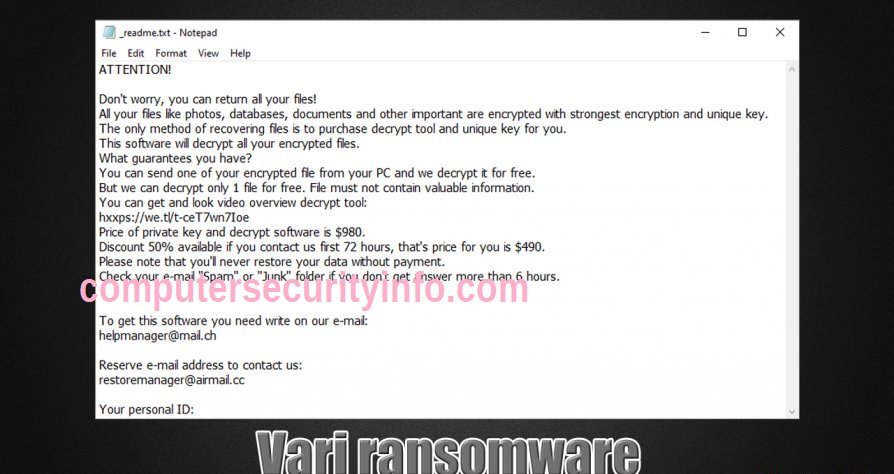
Category: Ransomware | Date: 21st December 2022
When You Are Open The Computer System, Then Your Computer Terminal Has Been Exhibited Blue Screen And Text Message. That Means, Your Computer System Has Been Captured By The Ransomware Code. VARI Ransomware Is A Name. However, VARI Ransomware Could Categorized As A Malware Program. VARI Ransomware....

Category: Ransomware | Date: 28th November 2022
GET Ransomware Is A Nasty Stuff For The Computer System And Big Institutions As Well As Financial Firms. GET Ransomware Has Been Coded For Generating The Money Through Hacking The Big Institution Website. GET Ransomware Is A Notorious Stuff, That GET Can’t Remove Immediate From The Infected....
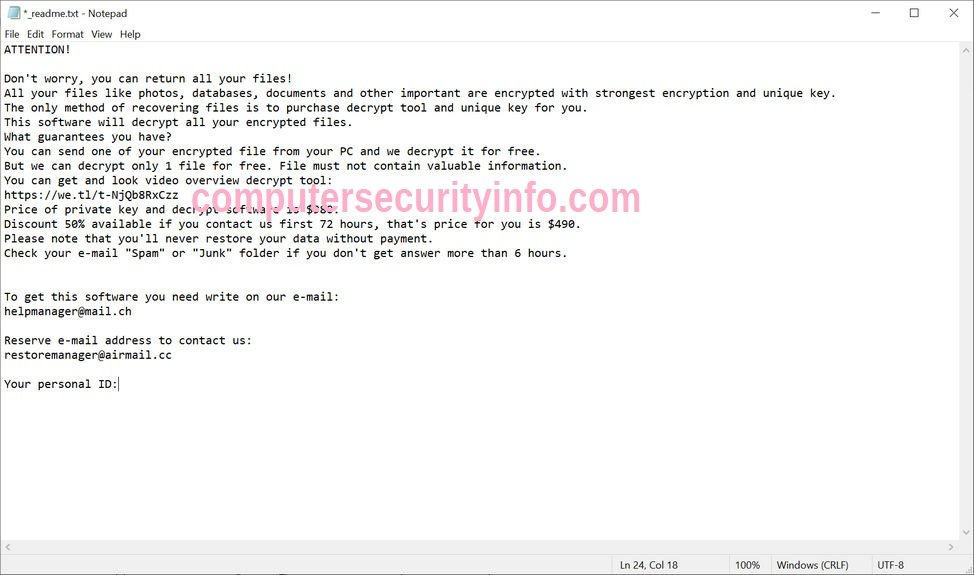
Category: Ransomware | Date: 27th November 2022
XATI ransomware Is A Pertaining With Dharma Ransomware Family. XATI Ransomware Inception An Encryption Process While System May Has Been Compromised. XATI Ransomware Will Work Behind The System And Display The Blue Screen In The Desktop. XATI Ransomware May Also Exhibit The Alert Warning....
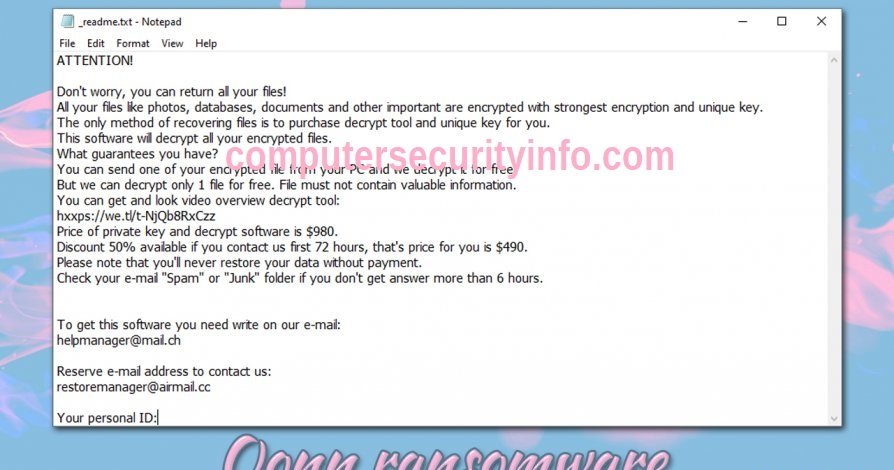
Category: Ransomware | Date: 27th November 2022
OONN Ransomware Program Is Related With DJVU/STOP Ransomware Family. OONN Ransomware Start An Encryption Process When OONN Ransomware Is Reach The Feeble Computer System Through Backdoor. The Photos, Documents, Videos And Databases Files Are Influenced By The OONN Ransomware Program. OONN....
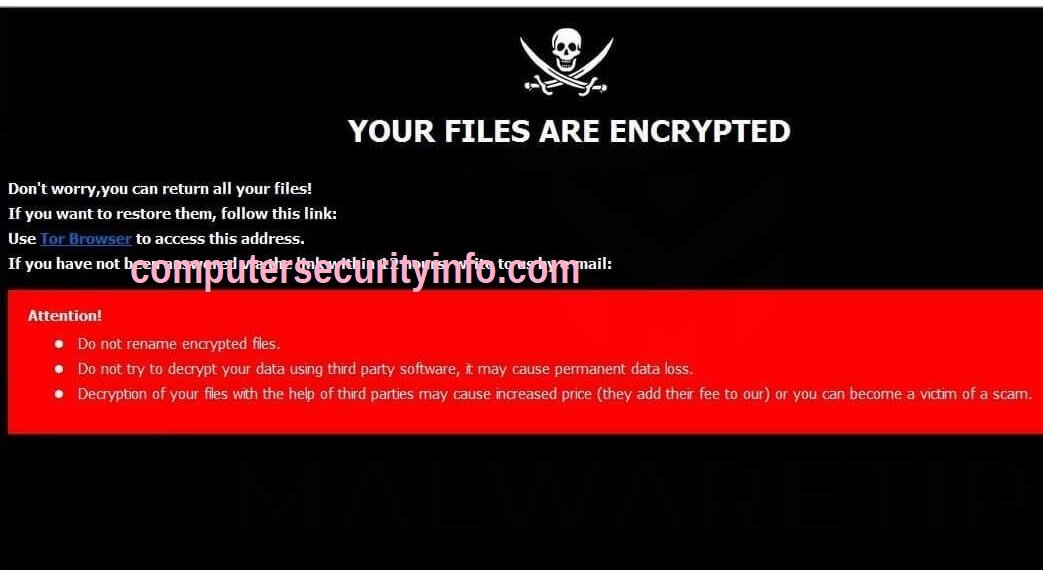
Category: Ransomware | Date: 27th November 2022
PPHL Is Also A Ransomware Code, That Can Start The Encryption Process And Encrypted The Complete Computer Files. After Encryption, You Never Access The Files As Well As Configuration Files. The Bootable Files Could Be Corrupted Abysmally. However, PPHL Ransomware Programmer May Ask The Money To....
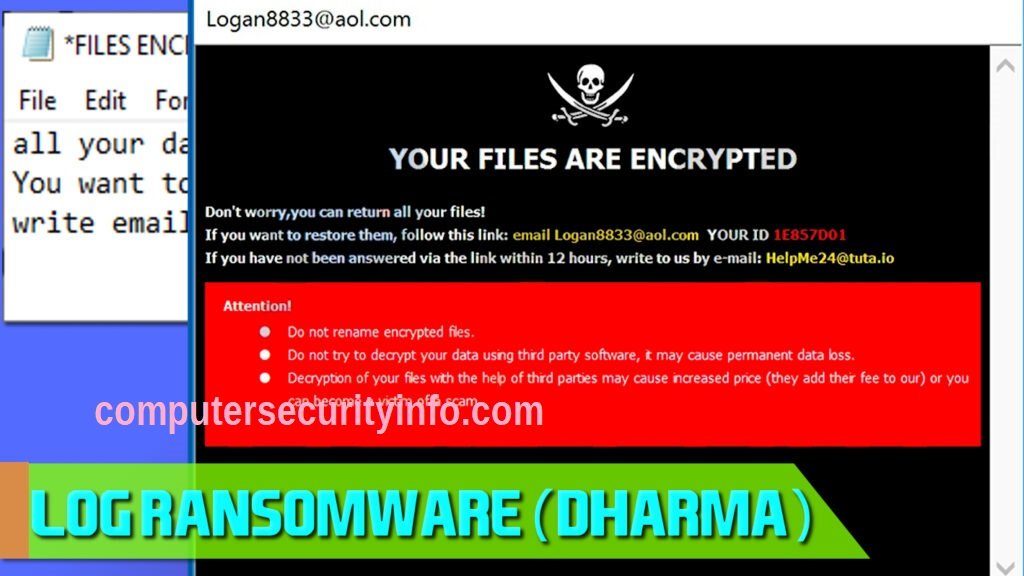
Category: Ransomware | Date: 27th November 2022
LOG Ransomware malware Code Is Pertaining With Dharma Ransomware Family. LOG Ransomware May Target The Financial Institutions, And Bank. You Get Loss Millions Of Information And Others. LOG Ransomware Has Been Specifically Designed To Target For Money Generating Tools. However, LOG....

Category: Ransomware | Date: 27th November 2022
NILE Ransomware Will Not Promote Itself But Bundled Of Software To Aid The NILE Ransomware Program. NILE Ransomware Has Been Created By The Cyber Perpetrators To Disable The Feeble Computer Terminal. NILE Ransomware May Demand The Ransom Amount After Encrypted All Significant Computer Files. These....

Category: Ransomware | Date: 26th November 2022
TCPRX Ransomware Was Pertaining With Dharma Ransomware Code That Could Steal Data Into Compromise And Begin Encrypting All System Files. TCPRX Ransomware Cybercriminal Who Spreads Threats Such As TCPRX Ransomware Goal At Spam Mail, Phishing Email And Starts Black Mailing The Users Into Send The....
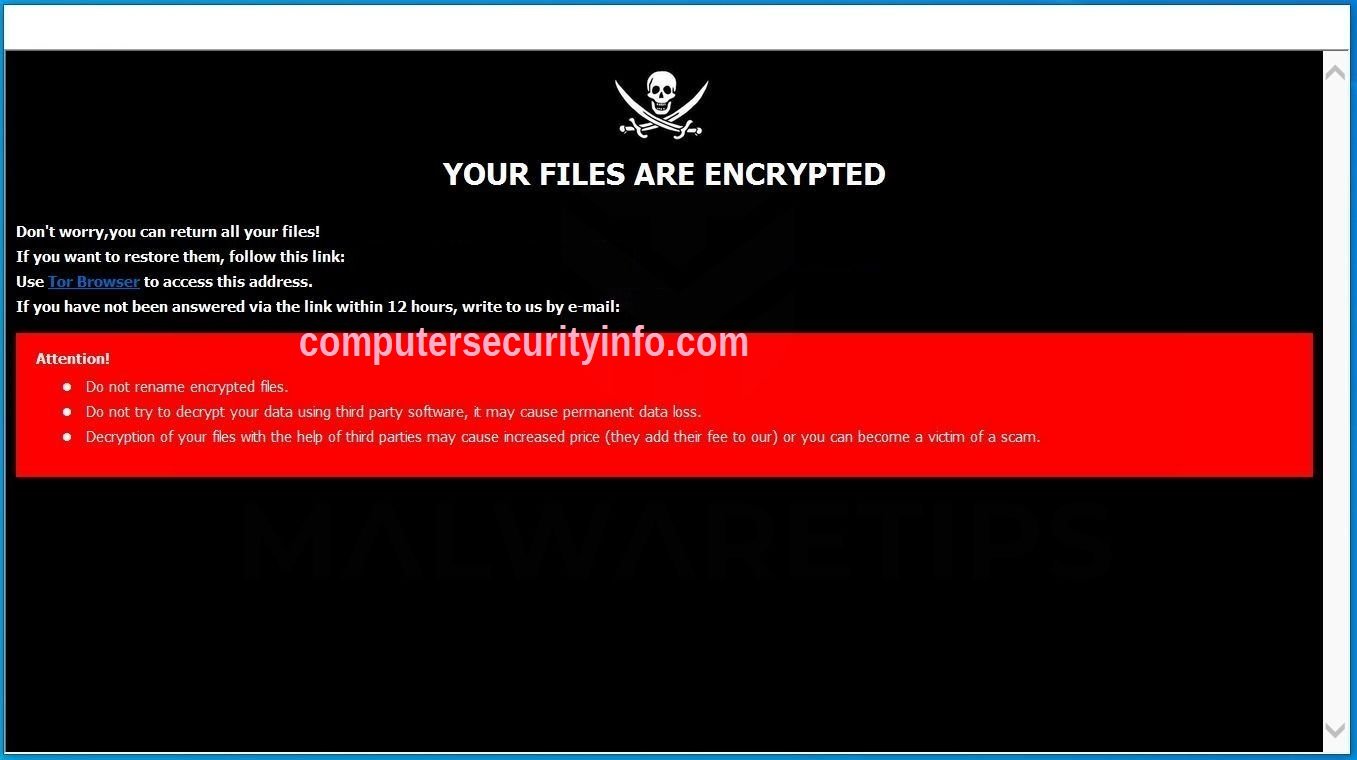
Category: Ransomware | Date: 26th November 2022
You Known, What Is A HAT? HAT Is A Ransomware Application To Encrypts The System Files, Images, Videos, Databases And Documents. HAT Ransomware Can Incept The Encryption Process Automatically. Thus, HAT Ransomware Will Terrible Program For The Computer System. Cryptovirus Is An Other Name Of HAT....
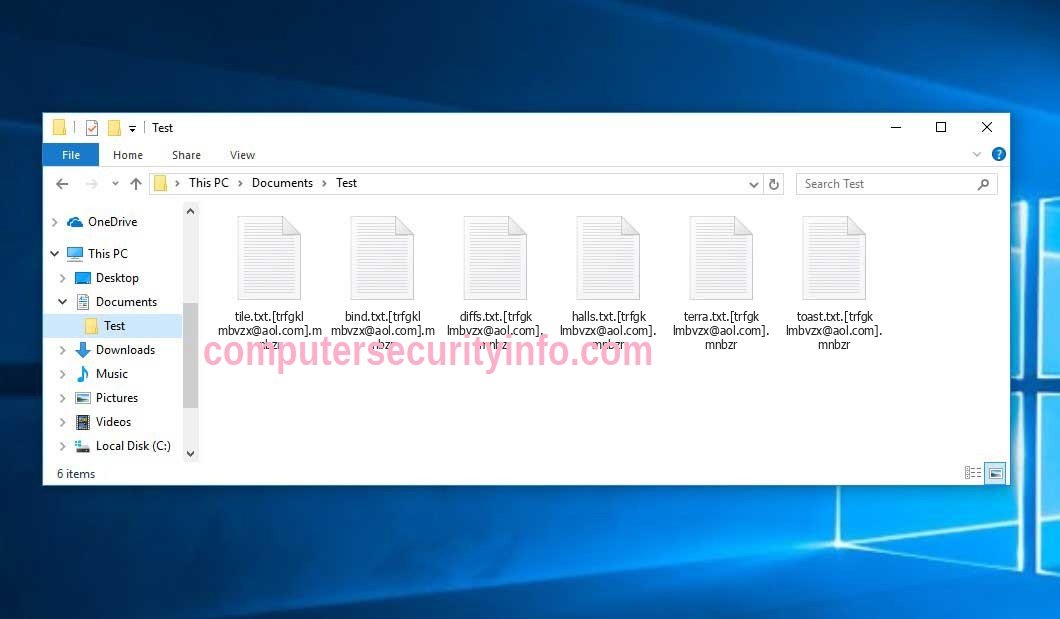
Category: Ransomware | Date: 26th November 2022
The Dharma Ransomware Family Is A Kin Of MNBZR Ransomware Code. According To The Computer Security Experts, MNBZR Ransomware Has Been Very Terribled computer malware code. MNBZR Ransomware May Encrypt Number Of Distinguish Files, Including Documents, Images, Pics, Videos, .doc, .docx, .jpg,....

Category: Ransomware | Date: 19th October 2022
[Tchukopchu@tutanota.com].chuk Is A Risky Ransomware Application, That Would Spread The Other Malicious Code And Web Links To Grab The Innocent User’s Terminal. The [Tchukopchu@tutanota.com].chuk Ransomware Program Was Deadly Weapons, Which Is Used By The Developers. Once An Install, In Your....

Category: Ransomware | Date: 19th October 2022
[Linajamser@aol.com].lina Is An Extension Of The LINA Ransomware Program. LINA Ransomware Program Is A Malevolent Code That Encrypt The Computer Related Files And Personal Documents. You Can Not Access By The User Of The File, Because LINA Ransomware Can Block Them. LINA Ransomware Program Is....

Category: Ransomware | Date: 19th October 2022
npph Is A Treacherous And Menace Ransomware Code, And Pertaining With DJVU/STOP Ransomware Family. However, Npph Ransomware May Start The Encryption Process While Feeble System Was Compromised. Thus, Npph Ransomware Will Demand The Ransom Money Through Bitcoins. The Ransomware Program Is....
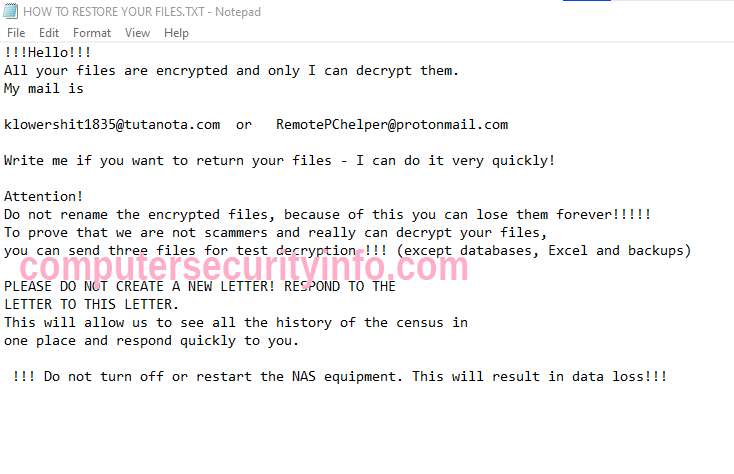
Category: Ransomware | Date: 17th September 2022
Computer System Has Been Infected With Hbdalna Ransomware. Hbdalna Ransomware Will Encrypt The Essential Files And Documents, Including Videos, Images, Pics, And Databases. Hbdalna Ransomware Program Has Been Fabricated By The Cyber Crooks. Hbdalna Ransomware Can Use As A Tools To Get The Revenue....
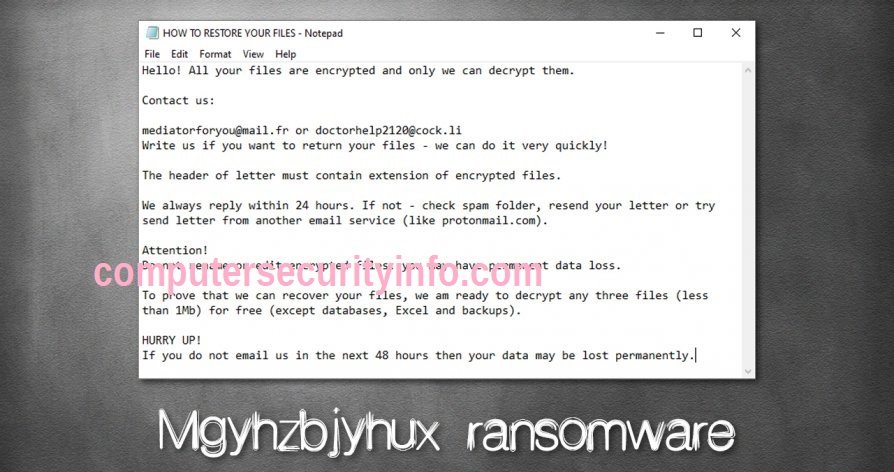
Category: Ransomware | Date: 17th September 2022
Mgyhzbjyhux Ransomware Program Is Contaminated The Computer Terminal And Encrypt The Files. You Can Not Access The Files As Well As The Computer System, Because Mgyhzbjyhux Ransomware Can Block To Access The File And Other Useful Things. Mgyhzbjyhux ransomware Is Also File Encrypting....

Category: Ransomware | Date: 17th September 2022
If Your Desktop Screen Has Been Appeared With Blue Screen, Then You Should Understand That Your System Has Been Compromised By The Jarkvgtiiq Ransomware Program. Jarkvgtiiq Ransomware May Reach Your Terminal By The Infiltration Via External Assistance. Jarkvgtiiq Ransomware May Have A File Like HOW....

Category: Ransomware | Date: 17th September 2022
You Can Not Open The Document, Files, Videos, Images, Pics And Databases, Because .qdfvbbiqtth Extension Has Been Associated With Them. The .qdfvbbiqtth Extension Is Pertaining With Qdfvbbiqtth Ransomware Program. Qdfvbbiqtth Infects Your Computer Terminal And Freeze Entire Function Of The Windows....

Category: Ransomware | Date: 15th September 2022
Cposysrzk is A Treacherous ransomware program To Infringe Many Cyber Law And Take The Feeble Terminal Into Under Control. Cposysrzk Ransomware Has Been Designed By The Perpetrators. Cposysrzk May Utilise The Social Website, Pornographic Website And Other Valuable Links To Reach The....
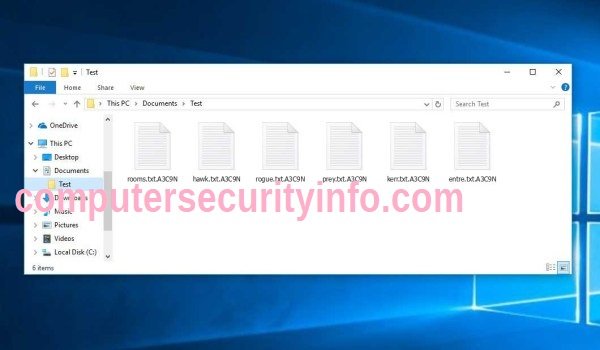
Category: Ransomware | Date: 15th September 2022
If You Can Not Open The Terminal While Your Desktop Screen Shows The Warning Message Regarding The Ransom, Then You Should Comprehend That Your System Has Been Contaminated By The A3C9N Ransomware Program. A3C9N ransomware program Uses The .A3C9N Extension To Capture The Encrypted Files.....
Category: Ransomware | Date: 15th September 2022
Eur seems To Be A ransomware Code, That Can Work As A Nasty Application. Eur ransomware Encrypts The Files, Images, Videos, And Databases. The Indispensable Documents And Personal Data. Eur ransomware Was Kills The Function Of The Bootable Files. Your....

Category: Ransomware | Date: 15th September 2022
OGDO Has Been Created By The Cyber Criminal To Track The Banking As Well As The Personal Activity On The Website. OGDO Is A Ransomware Application To Hack The Complete Computer Terminal. OGDO Ransomware Will Strive To Leak The Significant Data Including Username, Password, File Details, And More.....

Category: Ransomware | Date: 12th September 2022
Cndqmi Is A Very Nasty Ransomware Application, Which Can Start With Encryption Process. Cndqmi Ransomware Is Associated With Snatch Ransomware Family. Cndqmi Ransomware Encrypts The Files, Documents, Images, Videos, And Other Essential Items. Cndqmi Has Been Created To Generate The Money From The....
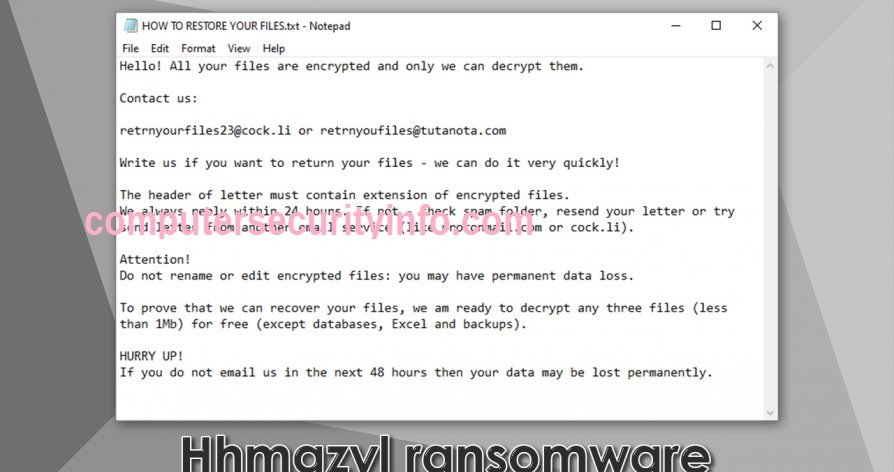
Category: Ransomware | Date: 12th September 2022
Hhmgzyl Ransomware Could Target The Feeble Computer System As Well As The Notorious Program To Wipe Out Significant Information. Hhmgzyl Ransomware Will Notion To Encrypts The Files Including Video, Images, Documents As Well As Databases. Hhmgzyl Has Been Created By The Profession Cyber Criminal.....

Category: Ransomware | Date: 12th September 2022
Zphs Ransomware Will Pop Up In Your Weak Computer Terminal By Spam Mail, And Phishing Email. Zphs Ransomware May Access Your Terminal In Others Process, Which Is Called As A Social Engineering. Zphs Ransomware May Use The Social Website To Proliferate Itself. The Bundled Of Software Like PDF....

Category: Ransomware | Date: 12th September 2022
[ICQ@cavallograndecapo].horse Is A Terrible Ransomware To Infiltrate The System, Which May Be Not Feasible To Protect The Terminal Against Malware Or Ransomware Invasion. [ICQ@cavallograndecapo].horse Has Been Fabricated By The Cyber Perpetrators To Infringes Many Cyber Law.....

Category: Ransomware | Date: 12th September 2022
[Cl_crypt@aol.com].cl is A Terrible Ransomware Application, That Has Been Created By The Crooks To Mine The money From The Internet. [Cl_crypt@aol.com].cl Has Capable To encrypt The Computer Files, Documents, Videos Files, Images Files, And Other Files Extension.....

Category: Ransomware | Date: 12th September 2022
[Backmydata@protonmail.com].bmd is A Horrible Ransomware Program. [Backmydata@protonmail.com].bmd Has Been Coded By The cyber Professional To Target The Feeble Computer System. [Backmydata@protonmail.com].bmd Can Strike The Terminal To Engage The Many Peripheral Devices.....

Category: Ransomware | Date: 31st August 2022
It’s A Reckless Question Occur Every Minute In The Mind Of The Human, That KASP Is A Ransomware Code Or Aid. KASP Is A Pertaining With DJVU Ransomware Family. KASP Was Not Inadvertently Reach The Computer System Instantly. KASP Ransomware Works Superstitiously In The Feeble Computer System.....

Category: Ransomware | Date: 31st August 2022
Tkoinprz Ransomware Is An Associated With Snatch Ransomware Family. Tkoinprz Ransomware Will Try To Encrypt The Files, Folders, Documents, And Other Pertinent Tools. Tkoinprz Ransomware May Strive To Persuade The User To Send The Ransom Money And Gets The Decryption Keys To Normalize The System.....

Category: Ransomware | Date: 31st August 2022
GOLD Ransomware Is A Part Of The Dharma Ransomware Family. GOLD Ransomware Encrypts The Data And File Of The Vulnerable Computer System. GOLD Ransomware Demands The Payment Through Bitcoins. Bitcoins Is Used By The Most Of The Ransomware Developers And GOLD Ransomware Is One Of The Them. GOLD....

Category: Ransomware | Date: 31st August 2022
Dmmcpsshl Is A Pernicious Ransomware Program. Dmmcpsshl Ransomware Will Active While User Can Create A Links Or Path To Reach The System. Once, Dmmcpsshl Ransomware Enter Your System, Then Dmmcpsshl Ransomware Starts The Encryption Process And Freeze The Entire Files And Documents, Including Video,....
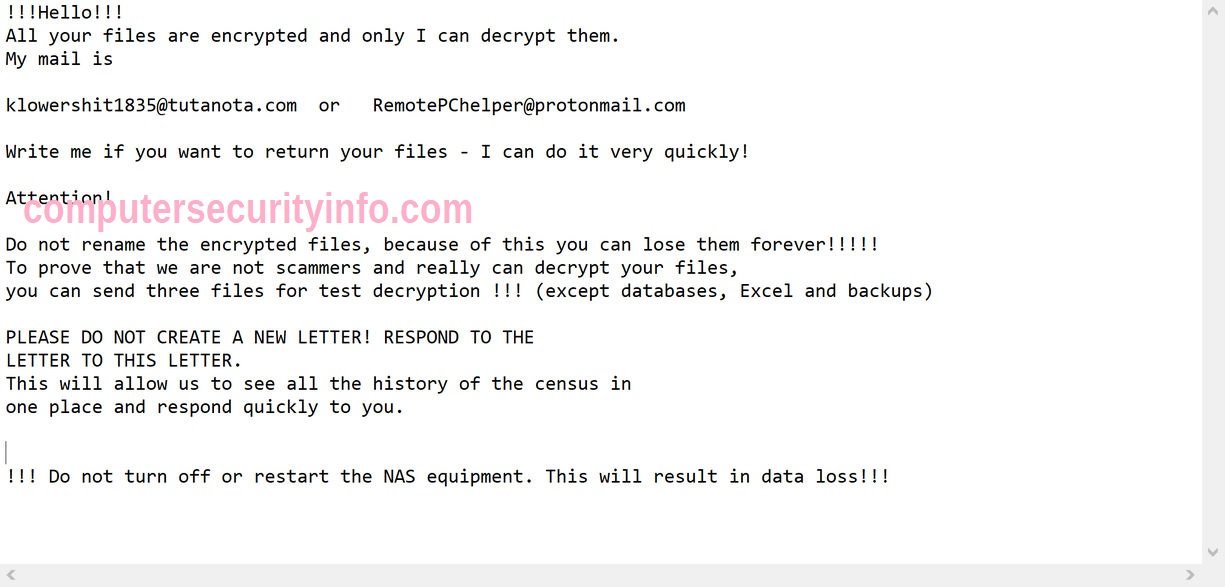
Category: Ransomware | Date: 31st August 2022
Mcauwpjib Was Not Appeared In Your Computer Terminal Automatically. Mcauwpjib Ransomware Works While Developers Can Aid The Path And Send The Command. Mcauwpjib Ransomware Is An Encrypted Files And Virus Code. Mcauwpjib Ransomware Will Change The Name Of The Files And Other Extension. You Will Try....

Category: Ransomware | Date: 31st August 2022
Fxmwtv Is A Name Of The Ransomware Program, Which Can Encrypt Files, Including Music, Video, Pics, Images, Personal Files, Documents And Databases. Fxmwtv Ransomware Has Potential To Breach The Security Fence And Other Security Features. The Firewall Has Not Been Detected Fxmwtv Ransomware....

Category: Ransomware | Date: 31st August 2022
Eknkfwovyzb Is A Malevolent Code To Run In The Windows System. Eknkfwovyzb Is Classified As A Ransomware Code And Snatch Ransomware Is Pertaining With Them. Eknkfwovyzb Ransomware Has Used The .Eknkfwovyzb Extension For Encrypted File. You Would Observe That Your System Has Been Corrupted By The....

Category: Ransomware | Date: 31st August 2022
WSHLP Ransomware Will Proliferate By The Freeware Software, Bundled Of Software And Other Strange Tools. The Phishing Email, Spam Mail May Aid To Promote WSHLP Ransomware In The Cyber World. The Innocent User Does Not Comprehend The Action Or Behavior Of The WSHLP Ransomware Program. WSHLP Is A....

Category: Ransomware | Date: 18th August 2022
GENO Is A New Name For The Computer Security Experts, Because GENO Is An Associated With Ransomware Program. STOP/DJVU Ransomware Is A Pertaining With GENO Ransomware Program. GENO Is Used The .geno Extension For The Encryption Files. While Encryption Process Has Been Completed, Then You Could Not....

Category: Ransomware | Date: 18th August 2022
AIM Ransomware Will Proliferate By The Freeware Software, Bundled Of Software And Other Strange Tools. The Phishing Email, Spam Mail May Aid To Promote AIM Ransomware In The Cyber World. The Innocent User Does Not Comprehend The Action Or Behavior Of The AIM Ransomware Program. WSHLP Is A Malware....
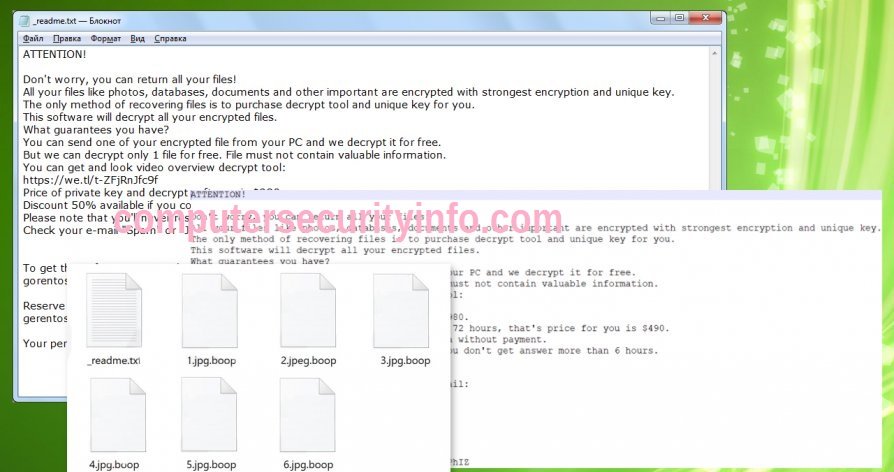
Category: Ransomware | Date: 18th August 2022
BOOP Is A New Name For The Computer Security Experts, Because BOOP Is An Associated With Ransomware Program. STOP/DJVU Ransomware Is A Pertaining With BOOP Ransomware Program. BOOP Is Used The .geno Extension For The Encryption Files. While Encryption Process Has Been Completed, Then You Could Not....

Category: Ransomware | Date: 18th August 2022
[Decphob@tuta.io].eking Has Been Coded By The Cyber Criminal To Target The Machine And Windows Terminal. [Decphob@tuta.io].eking Has Been Used As A Tools To Manipulate The Bootable Files. [Decphob@tuta.io].eking Has Capable To Corrupt The Firewall As Well As The Obsolete Security Software.....

Category: Ransomware | Date: 15th July 2022
IGDM Ransomware Is A Dreadful Program, And Append With .igdm Extension. However, IGDM Ransomware Will Try To Encrypt The Data As Well As The Files Or Documents. IGDM May Cripple The Complete Computer System. You Can Not Access The Files, Documents And Other Installed Application. In The Spite Of,....

Category: Ransomware | Date: 14th July 2022
Fireee Ransomware Is A Serious Program To Encrypt The Valuable Information To The Victim’s Computer System. Fireee Ransomware Has Ability To Counter The Firewall As Well As The Security Program, Which Might Be Obsolete. However, Fireee Ransomware Can Get The Advantage And Trap The User....

Category: Ransomware | Date: 14th July 2022
[Fairexchange@qq.com].fair Ransomware Is A Deceptive Malware Program To Encrypts The Information Along With Files And Documents. The Video, Audio, Images, And Other Significant Files Is Encrypted By The [Fairexchange@qq.com].fair Ransomware Code. [Fairexchange@qq.com].fair Will Persuade....
Category: Ransomware | Date: 14th July 2022
Fybtwagknr Ransomware is A Nasty Malware Application, That May Run In The Character Interface And Annihilate The Graphic Interface Program. However, Fybtwagknr Ransomware Is Belong To Snatch Ransomware Family. The computer System Contaminated With Fybtwagknr Ransomware malware,....

Category: Ransomware | Date: 7th July 2022
Leitkcad Ransomware Program Will Reach Your Computer System While User May Enable The Unwanted Web Link, Torrent Installers, And Other Terrible Program. Leitkcad Ransomware Has Been Fabricated By The Cyber Criminal, Which Can Expert To Infiltrate The Normal computer terminal. The .leitkcad Is An....
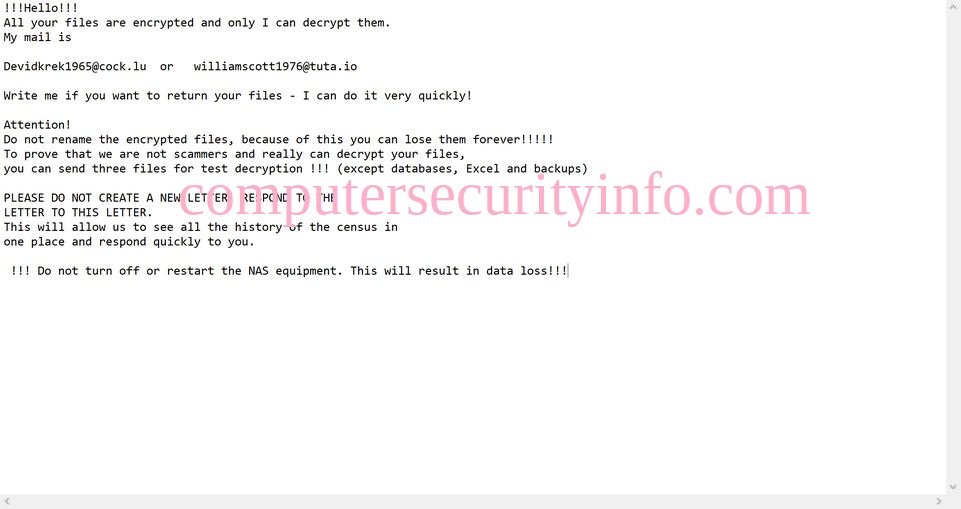
Category: Ransomware | Date: 7th July 2022
Jfwztiwpmqq ransomware Is Used A .jfwztiwpmqq Extension For Append The Encrypted Files Like Images, Videos, Documents And Other Files. Jfwztiwpmqq Ransomware Is A Treacherous Code To Violate The Cyber Law As Well As The Infringement For Privacy Policy. However, Jfwztiwpmqq Ransomware....
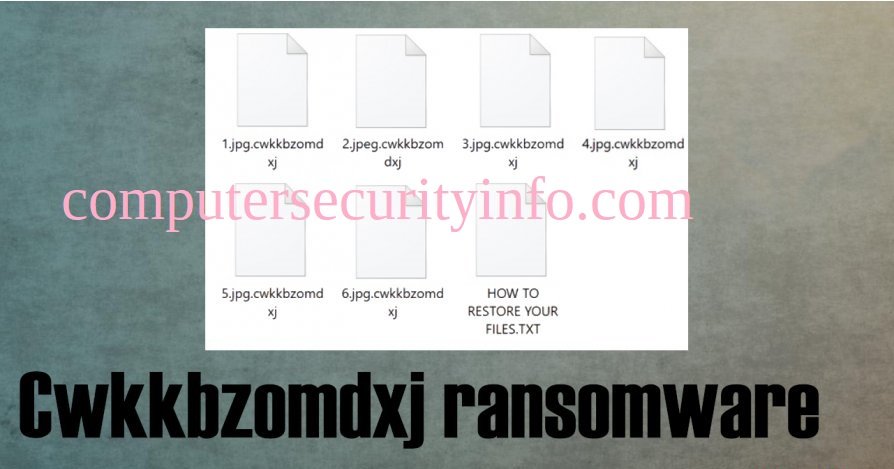
Category: Ransomware | Date: 25th June 2022
Cwkkbzomdxj Is A Very Terrible Ransomware Program, That Can Encrypt The Documents, Images, Videos, And Databases. Cwkkbzomdxj Ransomware Program Will Violate The Firewall And security Software. Cwkkbzomdxj Ransomware May Also Use The .Cwkkbzomdxj Extension, Then Your Terminal Has Been Infected....

Category: Ransomware | Date: 25th June 2022
Yes, TSAR Ransomware Will Reach Your computer Terminal With Assistance The Light Weight Malicious Adware As Well As The Hijacker Application. TSAR Ransomware Is An Awful Code For Infringe The Documents And Encryption. The TSAR Ransomware May Initiate The Encryption Process While TSAR....

Category: Ransomware | Date: 25th June 2022
MIFR Ransomware Will Start The Encryption And Encrypt The Videos, Images, Audios And Databases Files Steps By Steps. MIFR Ransomware Will Steal The Data Simultaneously. After Accumulating The Data Then MIFR Ransomware May Prepare For Transfer Them To Remote Server. You Could Not Find The Remote....

Category: Ransomware | Date: 25th June 2022
SWEAT Ransomware Will Hide Itself From The Download Software Program. Generally, non-techy people Or User Can’t See This. However, SWEAT Ransomware Will Active Inadvertently In Your Computer System, Then Your Machine Has Been Faced Various Rogue Problem, Annihilate The Configuration....

Category: Ransomware | Date: 25th June 2022
SWAT Is A very unique code To encrypt The Computer’s Files. According To The Behaviour, SWAT Is Deemed As A Ransomware Program. SWAT Ransomware Has Been Coded By The Cyber Perpetrators To Generate The Revenue From The Compromise Computer Terminal. SWAT Ransomware May Annihilate The Computer....
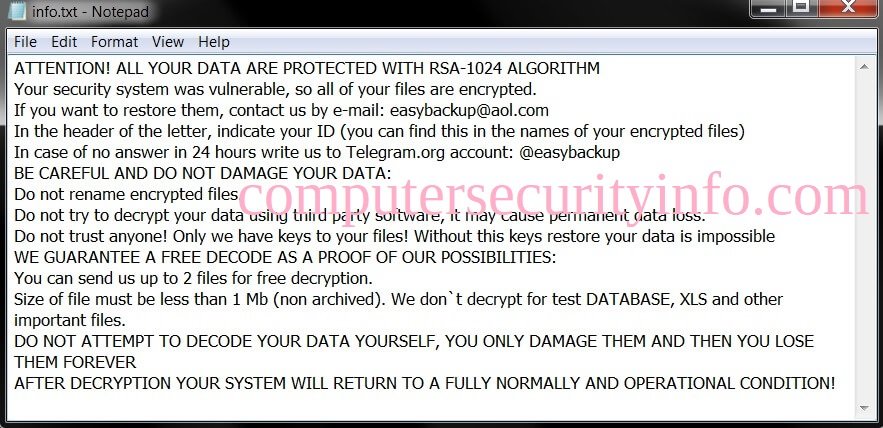
Category: Ransomware | Date: 15th June 2022
[Easybackup@aol.com].easy Is A Virus File, That Can Incorporated With Email ID. [Easybackup@aol.com].easy Is Classified As A Ransomware Code. [Easybackup@aol.com].easy Ransomware Program Inception The Encryption Process While System Compromise. [Easybackup@aol.com].easy May Corrupt The Various....

Category: Ransomware | Date: 15th June 2022
Crazy Name Is Associated With The Ransomware Malware Program. Crazy Ransomware Is A Pertaining With Malware Family. Crazy Ransomware Encrypts The Data, Files, Documents, And Databases. The File Extension Like .doc, .docx, .jpg, ,png, .gif, .wmv And Others Extension Has Been Compromised By The Crazy....

Category: Ransomware | Date: 14th June 2022
ZaToN Was A File Locking Trojan Virus That From The Xorist Ransomware Kin. ZaToN Ransomware Freeze The Files, Databases Actions, Media Files Advantage On The Computer Files Including The Documents Through Encrypting Them. ZaToN Ransomware Program Has Been Created By The Money Making Purpose. The....

Category: Ransomware | Date: 14th June 2022
LyDark Ransomware Was Very Treacherous Malware Program. LyDark Ransomware Freezes Your Computer Terminal. You Can Not Work Properly Because LyDark Ransomware Encrypts The System As Well As The Files. LyDark Ransomware Has Been Created By The Cyber Goons. LyDark Is Used For Money Making Program.....

Category: Ransomware | Date: 14th June 2022
EnCryp13d Ransomware Has Been Rigorous Program, That Can Declare By The Computer Security Experts. EnCryp13d Ransomware Is Related With Xorist Ransomware Family. EnCryp13d Was Intricated Specifically To Start Encryption Process And Encrypt The All Significant Files And Folders. While People Are Try....

Category: Ransomware | Date: 14th June 2022
[Leeza@keemail.me].LTC is A Ransomware Program That Encrypts The Documents, Files And Personal Folders. [Leeza@keemail.me].LTC Detected On The Victim’s Computer System Along With .[Leeza@keemail.me].LTC Extension. [Leeza@keemail.me].LTC Exhibits The Message Which Shows Offers To Decrypts....
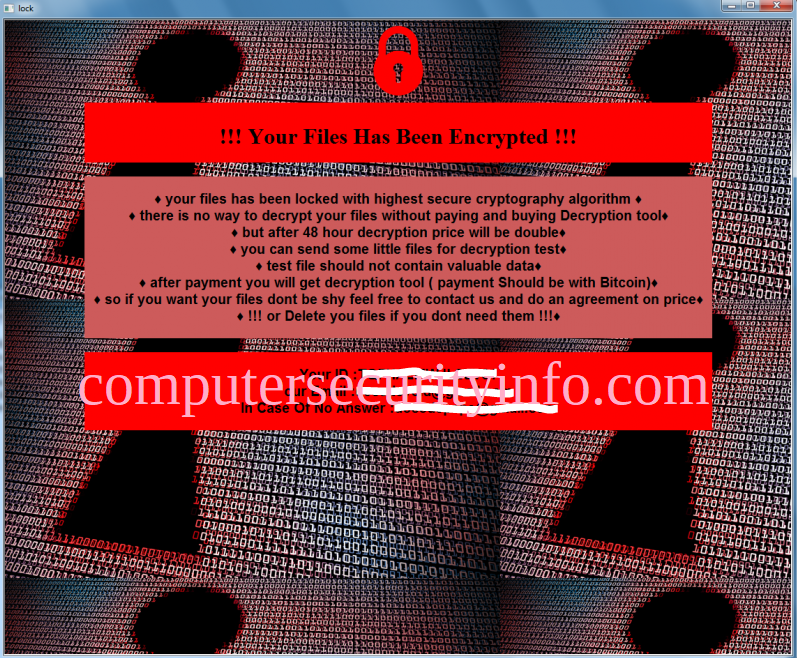
Category: Ransomware | Date: 14th June 2022
[god85Ar@yandex.com] GOD Is A Horrible Ransomware Code. [god85Ar@yandex.com] GOD May Incorporate With Yandex.com. It Is A Search Engine, Which Is Belong To Russia. I Hope [god85Ar@yandex.com] GOD Developer Diminish The Name Of The Yandex Search Engine. [god85Ar@yandex.com] GOD Encrypts....

Category: Ransomware | Date: 14th June 2022
Esexz Ransomware Encrypts Your Files As Well As Appends The .esexz extension To Encrypts Filenames. Esexz Ransomware Creates A Ransom Note And Display On The Windows Screen. Esexz Ransomware Can Encrypts The Database Files, And Accumulate The Personal Information. Esexz Ransomware Is Used....

Category: Ransomware | Date: 13th June 2022
Aulmhwpbpzi Ransomware Is Core Based Program To Deeply Annihilate The Computer System. Snatch Ransomware Family Is Pertaining To Aulmhwpbpzi Ransomware Program. Aulmhwpbpzi Ransomware Initiates An Encryption Process And Encrypts All Classified As Well As Significant Data, Files, Documents, Folder,....
Category: Ransomware | Date: 13th June 2022
Qsayebk is The New Name Of The Ransomware Program. Qsayebk Ransomware Initiates The First Process In The Compromise System Is Encryption. All Indispensable File Has Been Encrypted By The Qsayebk Ransomware Program. Snatch Ransomware Program Kin Is coupled With Qsayebk Ransomware....

Category: Ransomware | Date: 13th June 2022
Snatch Ransomware Family Is Pertaining With HRDHS Ransomware Program. HRDHS Ransomware Is A Potentially Unwanted Program. HRDHS Ransomware Is Fabricated To Encrypt Data As Well As The Information. HRDHS Ransomware May Demand The Payment Or Ransom Money For The Decryption Process. While Encryption....
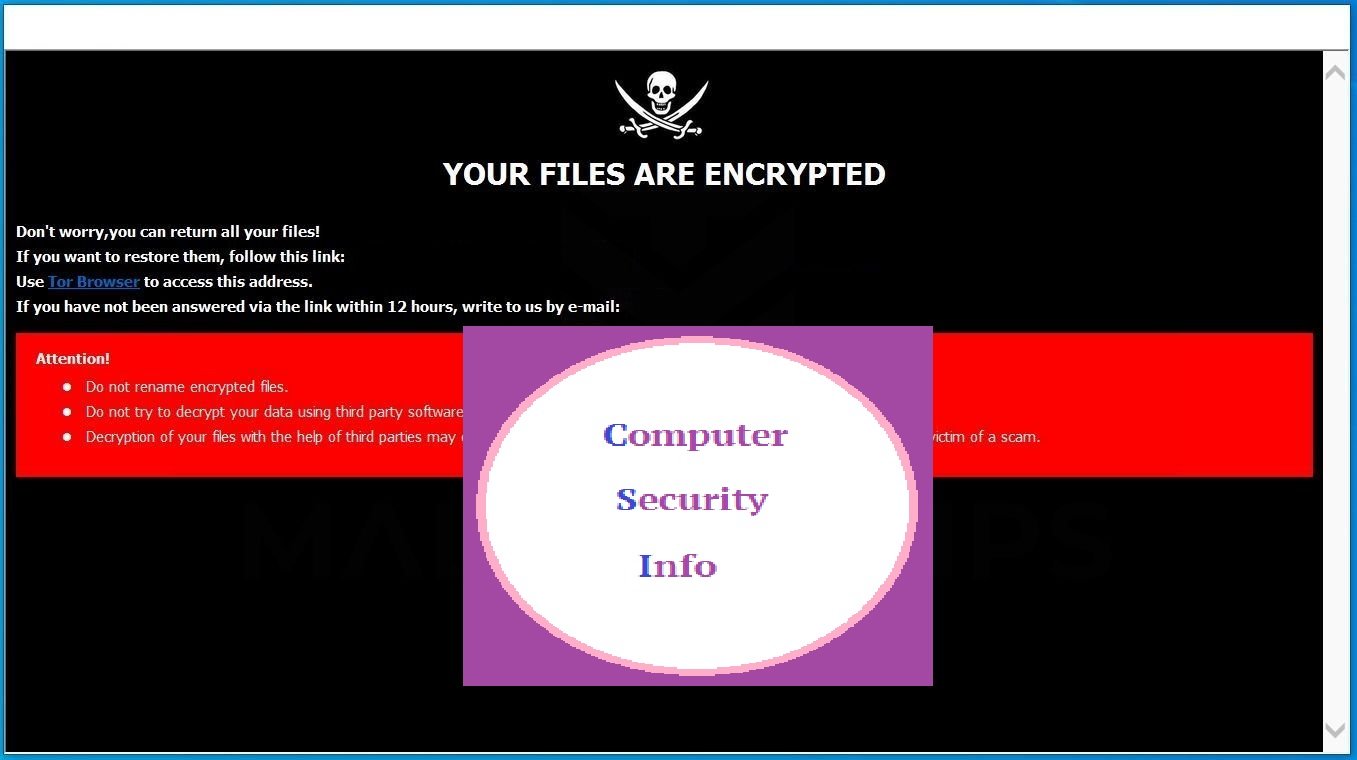
Category: Ransomware | Date: 13th June 2022
[Decrypt@disroot.org].DIS is A Spurious Ransomware Application That Encrypts The Data, Files, Documents And Software. Your All Imperative Data Has Been Accumulated By The [Decrypt@disroot.org].DIS Developers. Your Computer System Has Been Freezed Due To [Decrypt@disroot.org].DIS Ransomware....
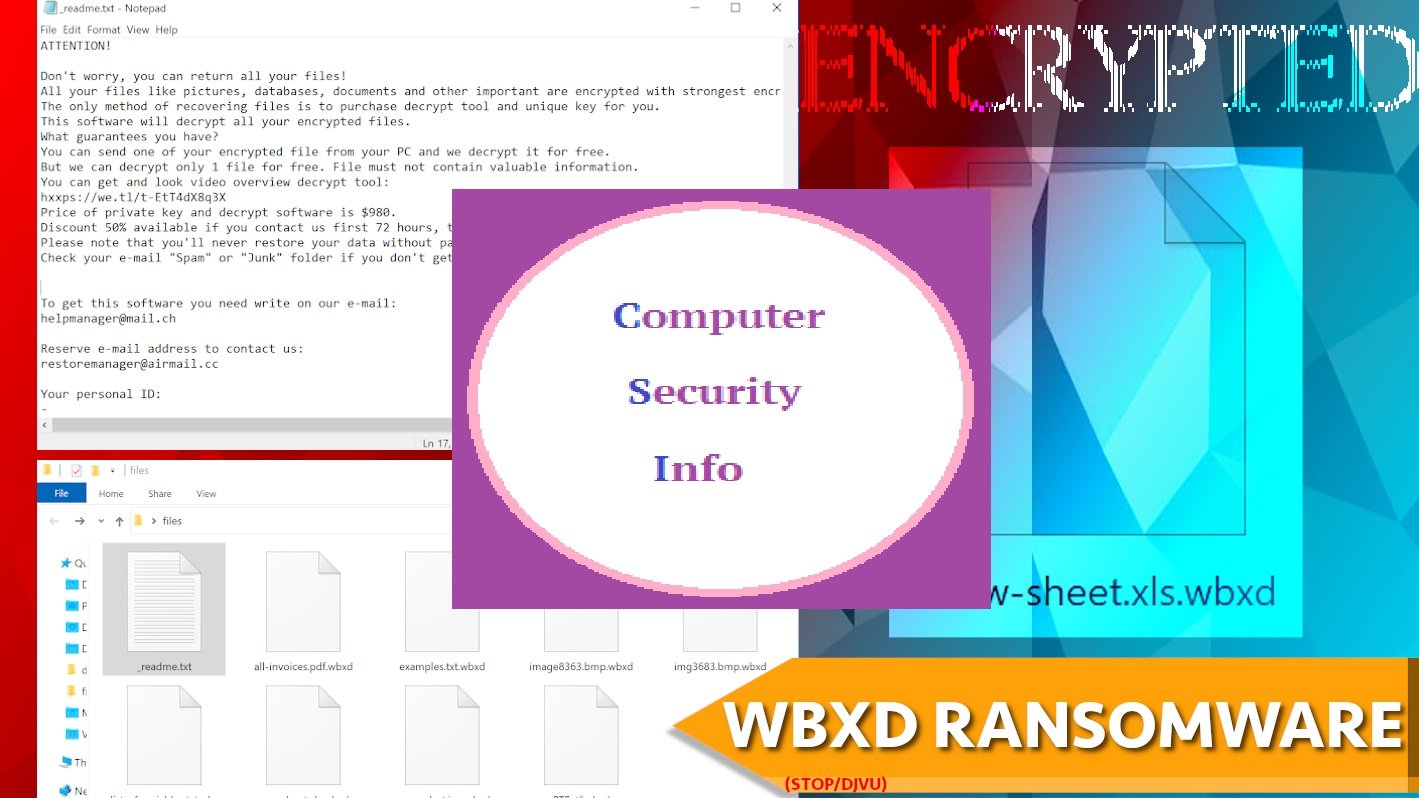
Category: Ransomware | Date: 13th June 2022
WBXD Ransomware Program Is A Very Cunning Application To Create A Huge Trouble For The Computer System. WBXD Will Initiate The Encryption Process To Control The Files, Application, And Other Significant Data. Djvu Ransomware Family Is Pertaining With WBXD Ransomware Program. WBXD Has Been Created....
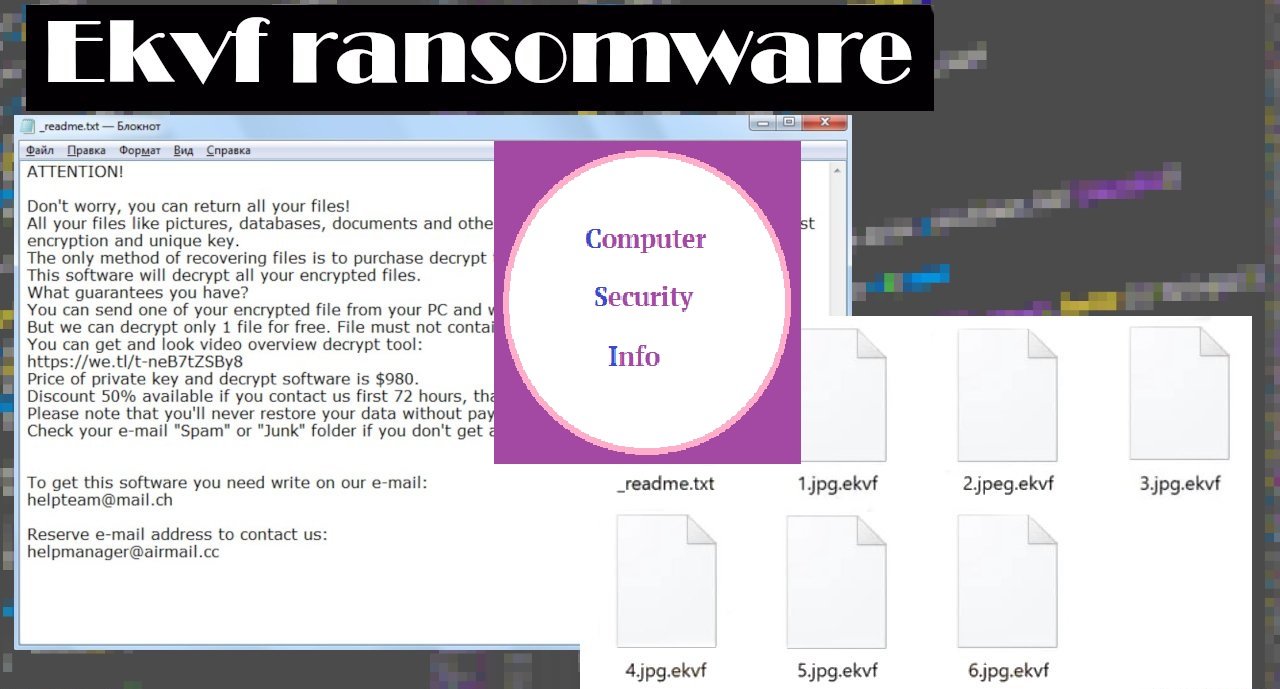
Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....
Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....

Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....
Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....
Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....
Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....

Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....

Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....
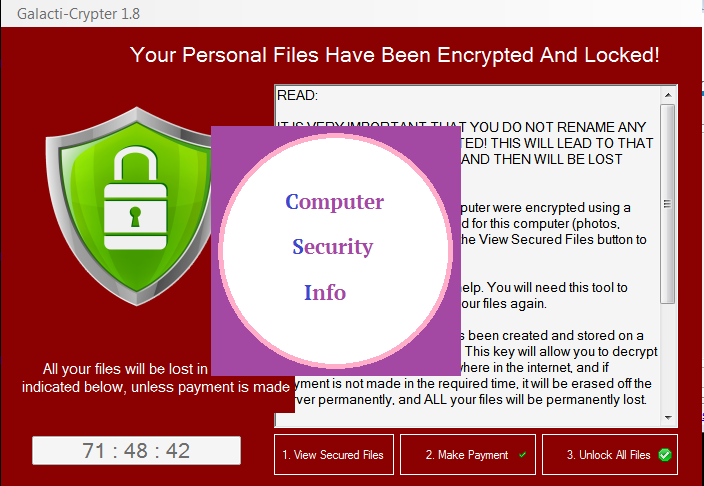
Category: Ransomware | Date: 12th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....

Category: Ransomware | Date: 11th June 2022
Detecting Malware On A System Can Be Tough For The Normal Computer User, And Manually Removing All Traces Of Threats Even More So. Detect As Well As Remove Computer Virus And Malware With Advance AntiVirus Removal App. Advance Removal App Offers Powerful, Anti-virus Protection. You....
Category: Ransomware | Date: 11th June 2022
Dev0 Ransomware Is A Very Treacherous Malware Program. Dev0 Ransomware Was Not Reached Your Computer System Automatically. However, Dev0 Ransomware Has Been Terrible Code To Cope The Computer System And CPU Function Very Well. Dev0 Ransomware Has Been Created By The Cyber Criminal To....

Category: Ransomware | Date: 23rd May 2022
HOOP Ransomware Is A Very Perilous Ransomware Program That Can Start The Encryption Process To Confiscate The Files Including Videos, Images, Pitcures, Documents And Others Significant Files. HOOP Ransomware May Also Influence The Browser Extnesion, Browser Helper Object (BHO), Domain Name....
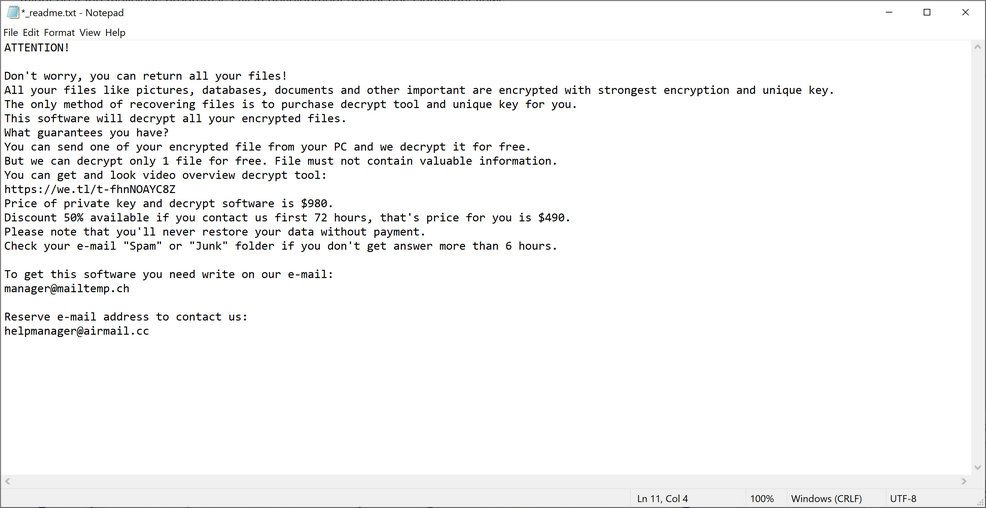
Category: Ransomware | Date: 9th May 2022
IRJG Is A File-encrypting Ransomware Infection That Restricts Access To Data (documents, Images, Videos) By Encrypting Files With The “.irjg” Extension. This Guide Teaches You How To Remove IRJG Ransomware For Free By Following Easy Step-by-step Instructions. IRJG Ransomware Is Not....

Category: Ransomware | Date: 25th April 2022
The File Encrypting Process Has Been Used By The Ransomware Program And RIGJ Is One Of Them. RIGJ Ransomware Will Initiate The Encryption Process When Computer Has Been Contagious. RIGJ Ransomware Can Encrypt Documents, Images, Videos And Other Significant Files Along With “.rigj” File....
Category: Ransomware | Date: 25th April 2022
YQAL Is A Program To Encrypts The File And Documents In The Hostile Computer System. YQAL Ransomware Program Is A Ruthless Infection That Can Freeze All Files, Folders, Documents, Images And Videos To Access By The Users. However, YQAL Ransomware Is A Potentially Unwanted Program That Can Create A....

Category: Ransomware | Date: 25th April 2022
MOIA Ransomware Is A Unique Code To Mislead The Computer System Along With Security Software Like Firewall And Antivirus Program. MOIA Ransomware May Infringe Cyber Law And Send Ransom Note To Pay Ransom Money Via Bitcoin Or Cryptocurrency. However, MOIA Ransomware Has Been Created By The Cyber....
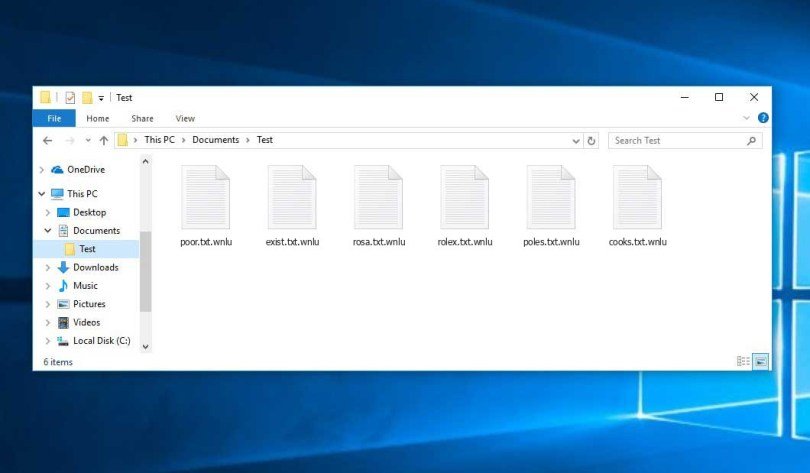
Category: Ransomware | Date: 25th April 2022
WNLU Ransomware Is A Pervert Malware Code That Can Encrypts The Essential Data File Such As .doc, .docx, .xls, .png, .jpeg, .jpg, .pdf, .txt And Even More. WNLU Ransomware Program Has Been Fabricated By The Computer Professional That May Involve In Cyber Hacking And Other Illegitimate Work In The....
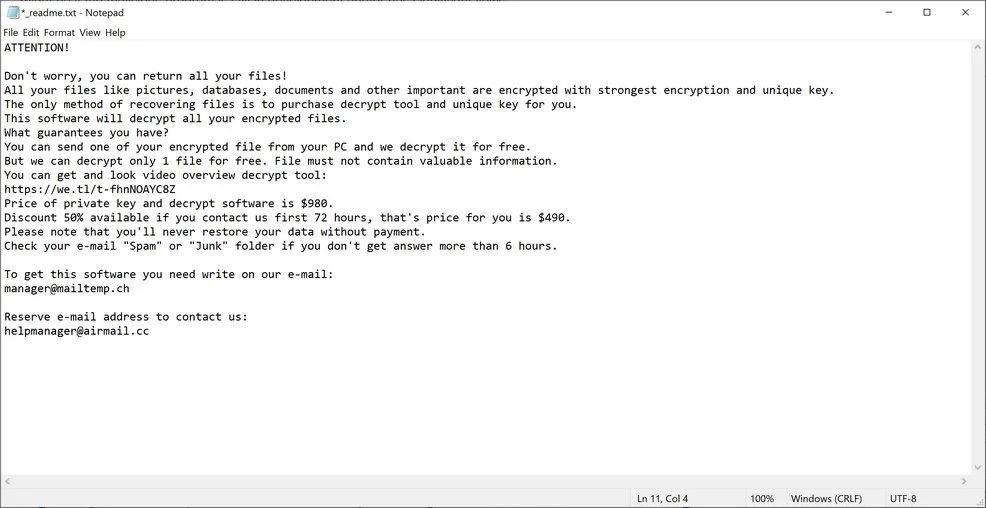
Category: Ransomware | Date: 11th March 2022
HGSH Ransomware Encrypts The Files, Documents, Images, Videos, And Other Significant File Extension. While Reaching Your Computer System, HGSH Ransomware May Initiate The Process Of Encryption And Cripple The All Function Of The Terminal. It Is Very Sad Moment For The Computer Users And Machine....
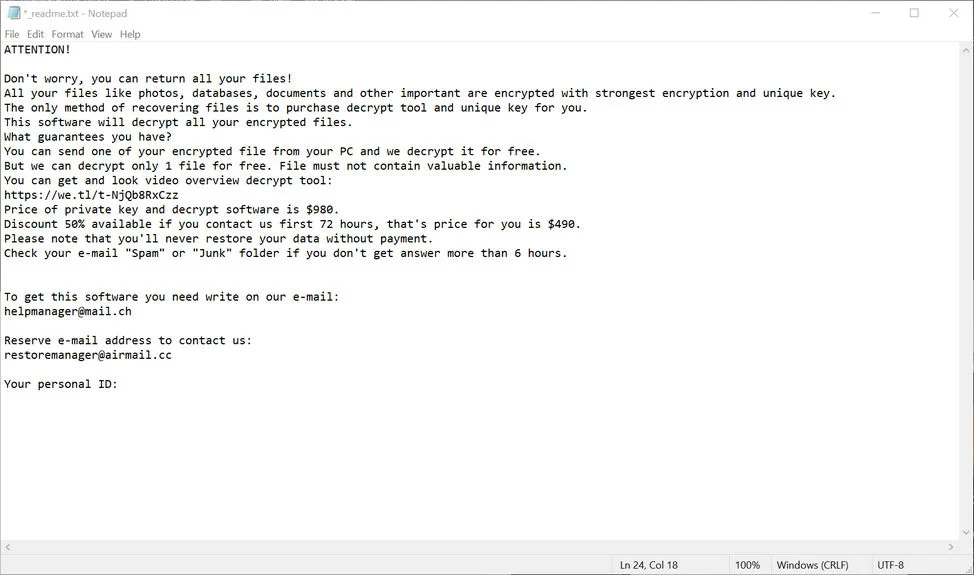
Category: Ransomware | Date: 7th March 2022
HUDF Ransomware is a dreadful and deceptive malware program that maligns the computer system inadequately. HUDF Ransomware is a related with STOP/DJVU ransomware family. Upon arrival on the target the computer system, HUDF Ransomware starts encrypting all files stored on it as well as the appending....
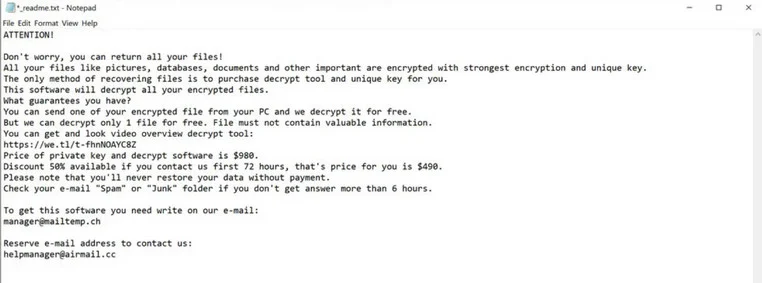
Category: Ransomware | Date: 7th March 2022
ZAQI is a deadly ransomware code to encrypt the files, folders and documents. ZAQI Ransomware is used .zaqi file extension to lock the files, where users cannot open the file, folders and documents. ZAQI Ransomware creates a ransom text note and attach with file like __readme.txt file. Djvu....
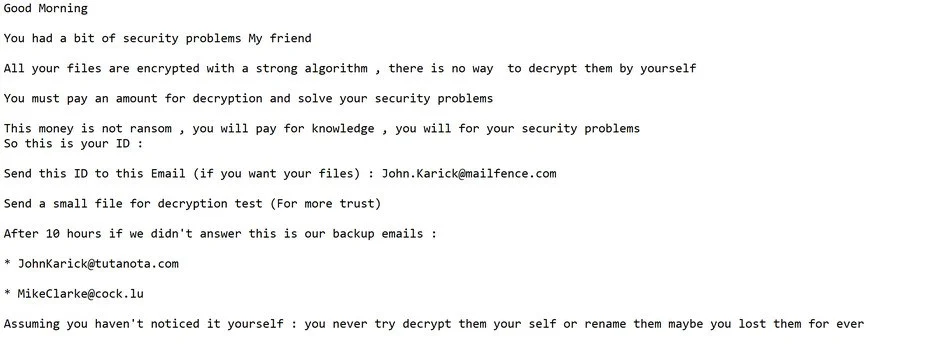
Category: Ransomware | Date: 2nd March 2022
RSFDD Ransomware Is A File Encrypting Infection That Freeze Access To The File As Well As The Data Like Documents, Images, Videos And More. RSFDD Ransomware Starts The File Encryption Process While RSFDD May Enter The System Simultaneously. RSFDD Ransomware Is Apply The File Extension As Well As....
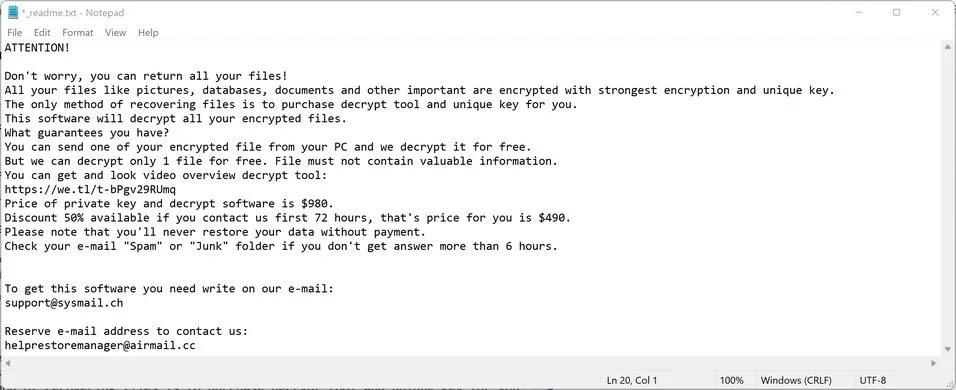
Category: Ransomware | Date: 28th February 2022
Ooii ransomware is a nasty application, because it is a ransomware program. However, OOII Ransomware know about the behaviour and action inside the computer system. OOII Ransomware may start encryption process to encrypt all files and folders. If Microsoft OS and Macintosh OS has been affected....

Category: Ransomware | Date: 26th February 2022
Ransomware Is A Type Of Computer Code, That Can Annihilate The Complete Computer's Function And Hardware Like CPU, Hard Disk, And Peripheral Devices Such As Printer, Camera And More. In The Other Words, Ransomware Is A Malign Software Program To Infiltrate The System Without Permission. Ransomware....