 Category's Page
Category's Page

Category: Malware | Date: 5th March 2026
Introduction to the Dorkbot Worm The Dorkbot Worm is a well-known piece of malware that infected thousands of computers worldwide during the early 2010s. It primarily targeted Windows systems, spreading through removable drives, instant messaging platforms, and compromised websites. Once inside a....
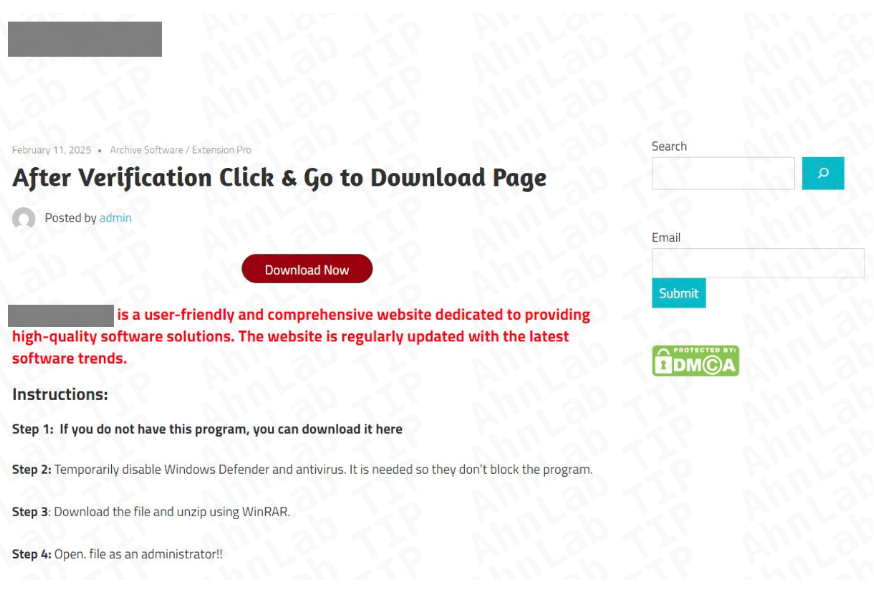
Category: Malware | Date: 23rd February 2026
Introduction In today’s rapidly evolving cybersecurity landscape, attackers continuously refine their techniques to bypass detection and exploit user trust. One particularly deceptive tactic involves disguising malicious software as legitimate, widely used applications. A recent and alarming....

Category: Malware | Date: 8th February 2026
Introduction Ransomware attacks have become one of the most serious cybersecurity threats facing organizations worldwide. Among the many ransomware families that have emerged in recent years, Royal ransomware stands out due to its sophistication, aggressive tactics, and high-profile victims. Since....
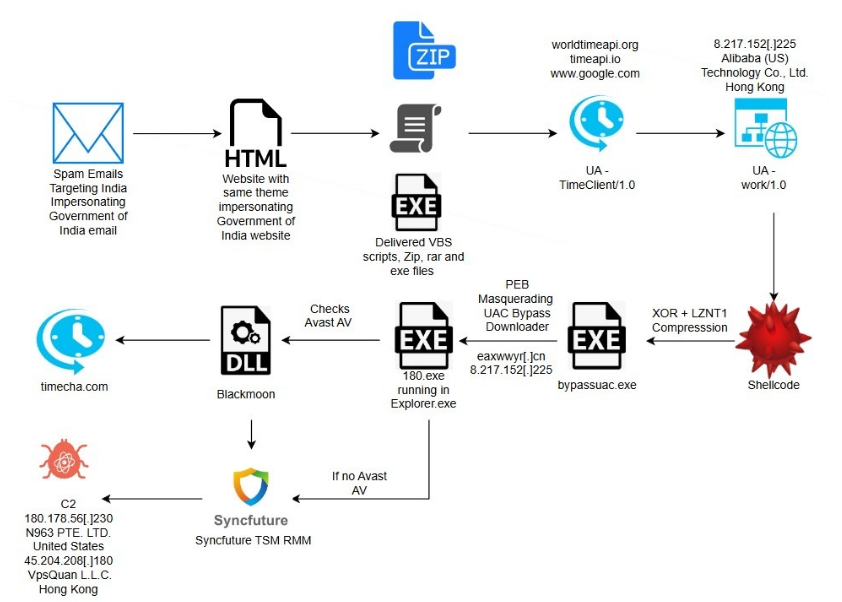
Category: Malware | Date: 8th February 2026
Introduction Malware continues to evolve at a rapid pace, adapting to new technologies, operating systems, and user behaviors. Among the many threats that have surfaced over the years, Blackmoon malware stands out as a sophisticated and stealthy cyber threat that has targeted both individual users....
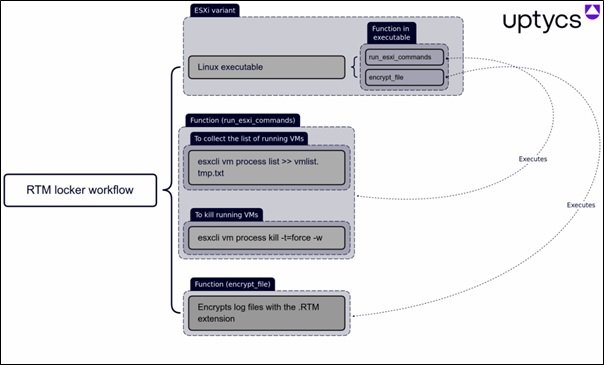
Category: Malware | Date: 5th February 2026
What Is RTM Locker Ransomware? RTM Locker ransomware is a malicious software strain designed to encrypt victim data and demand payment in exchange for decryption. Like many modern ransomware families, RTM Locker targets organizations rather than individuals, focusing on environments where....
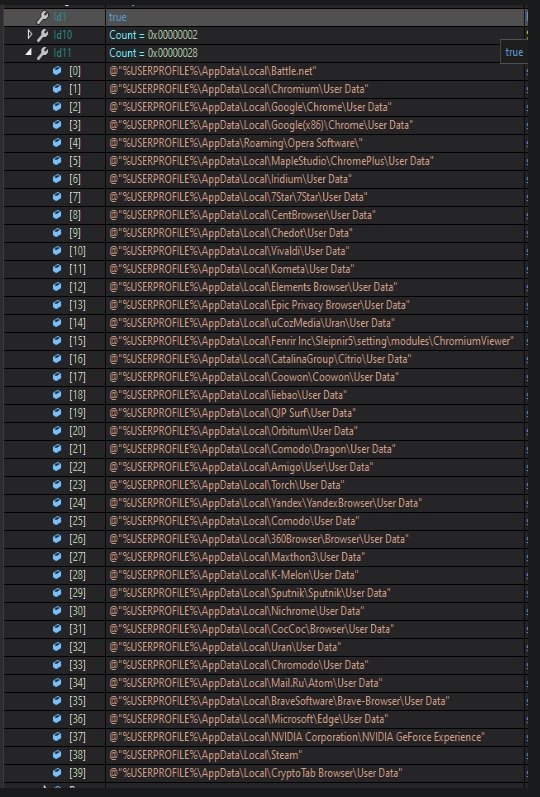
Category: Malware | Date: 3rd February 2026
Cybercrime has evolved rapidly over the past decade, with malware becoming more specialized, stealthy, and profitable for attackers. Among the most notorious threats in recent years is RedLine info-stealer malware, a highly effective malicious program designed to harvest sensitive data from....
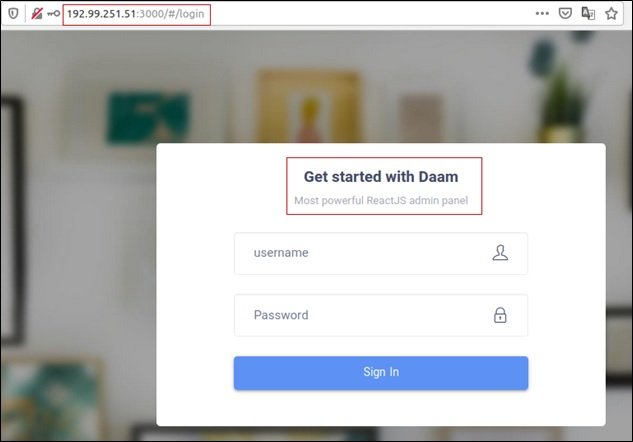
Category: Malware | Date: 2nd February 2026
The rapid growth of Android as the world’s most widely used mobile operating system has made it an attractive target for cybercriminals. Among the many threats that have emerged over the years, the Daam Android botnet stands out as a notable example of how mobile malware has evolved....
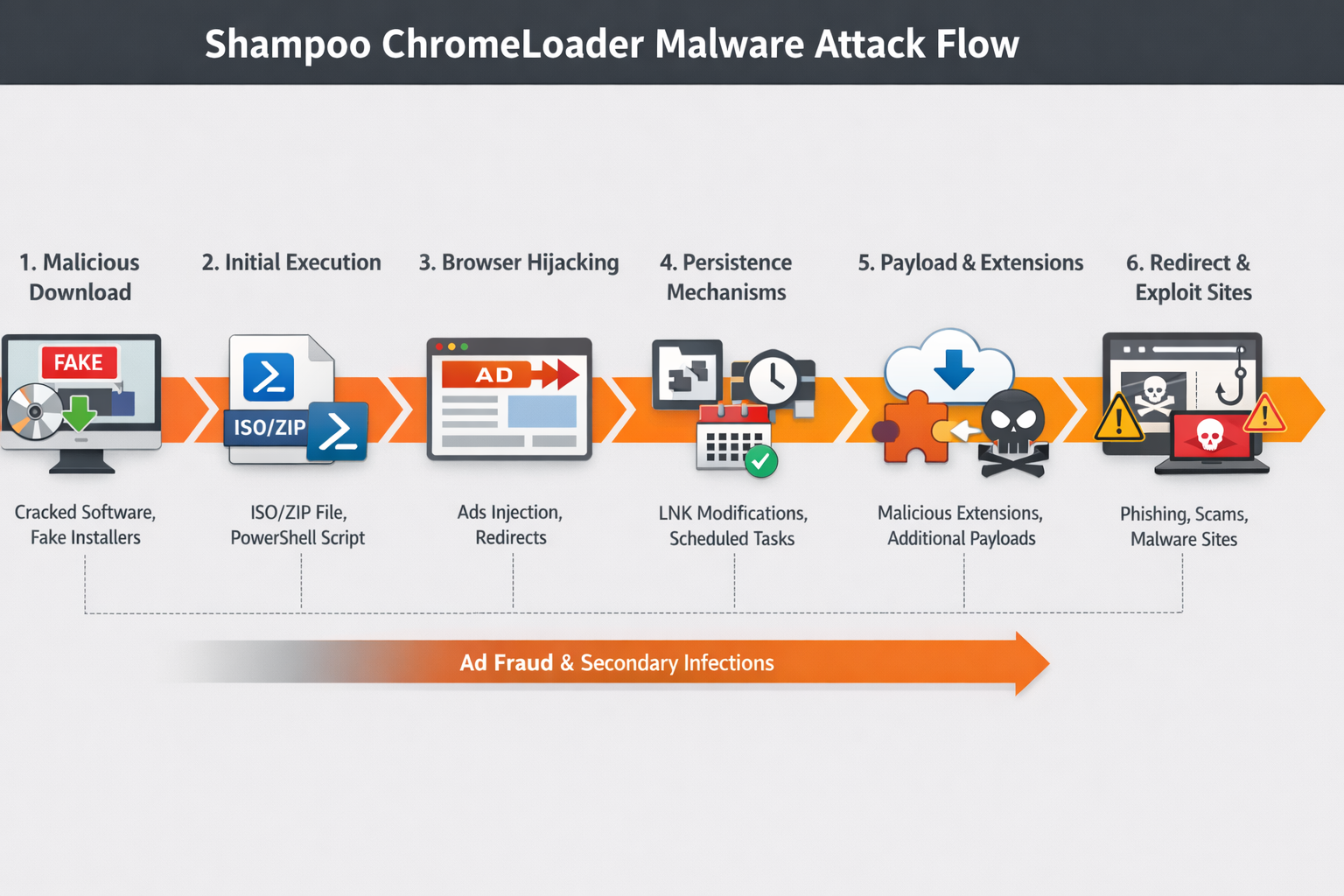
Category: Malware | Date: 21st January 2026
Introduction of Shampoo ChromeLoader Malware Shampoo ChromeLoader Malware is a nasty application. It has been developed by the cyber criminal for own goal. However, Shampoo ChromeLoader Malware has been facilitated with ChromeLoader extension called “Shampoo”. It can only target the....
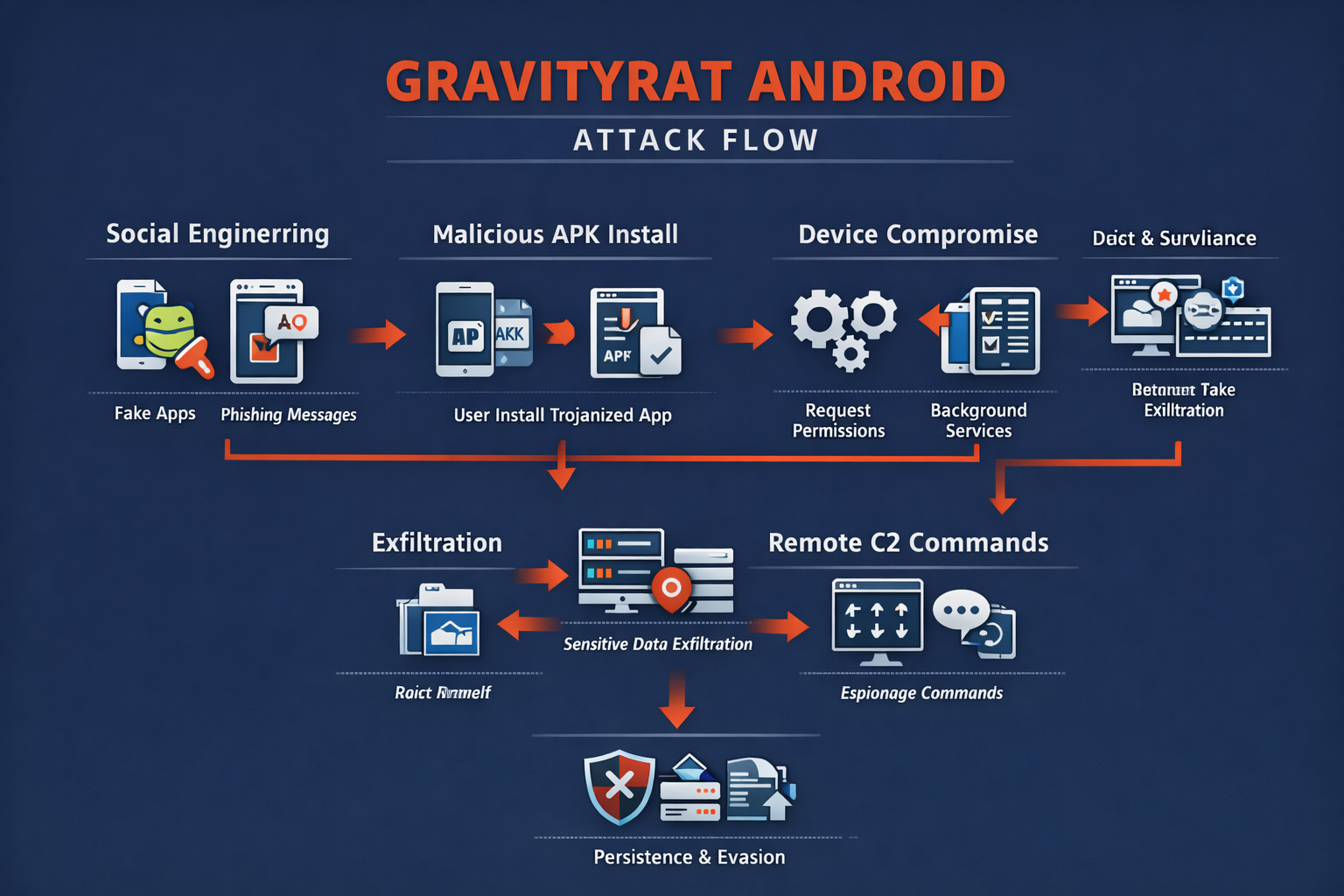
Category: Malware | Date: 20th January 2026
GravityRAT is a highly sophisticated Android malware strain categorized as a Remote Access Trojan (RAT) that is primarily used for cyber-espionage and targeted surveillance operations. Originally identified in Windows-based espionage campaigns, GravityRAT later evolved into mobile....
Category: Malware | Date: 18th January 2026
Introduction to Nitrogen Malware Nitrogen Malware is an emerging and highly evasive malicious software family designed to infiltrate systems silently, maintain persistent access, and facilitate secondary payload delivery such as ransomware, spyware, or banking trojans. Unlike traditional malware....
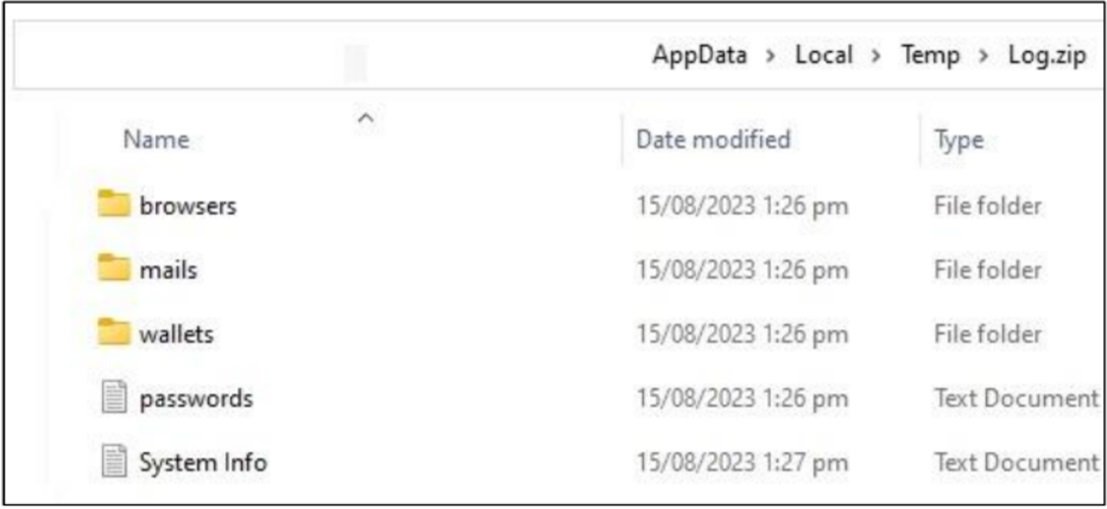
Category: Malware | Date: 11th January 2026
Raccoon Infostealer Malware: A Comprehensive Analysis of a Persistent Cyber Threat Raccoon Infostealer malware is one of the most notorious information-stealing threats observed in the modern cybercrime ecosystem. Designed primarily to harvest sensitive user data such as login credentials,....
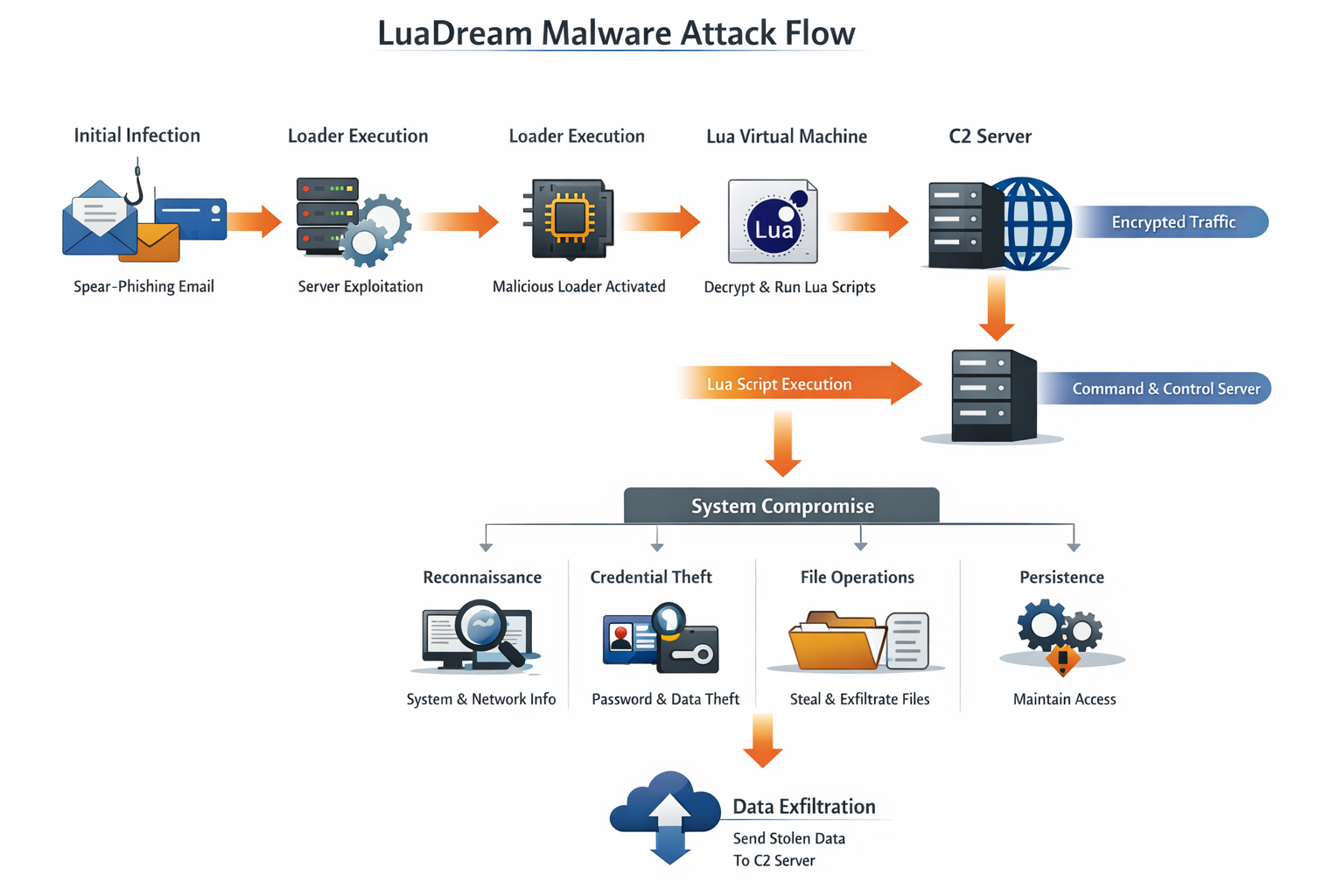
Category: Malware | Date: 9th January 2026
Introduction to LuaDream Malware LuaDream malware is a sophisticated cyber-espionage backdoor that has gained attention in the cybersecurity community due to its stealthy behavior, modular design, and use of the Lua scripting language. Unlike conventional malware written in C, C++, or Python,....
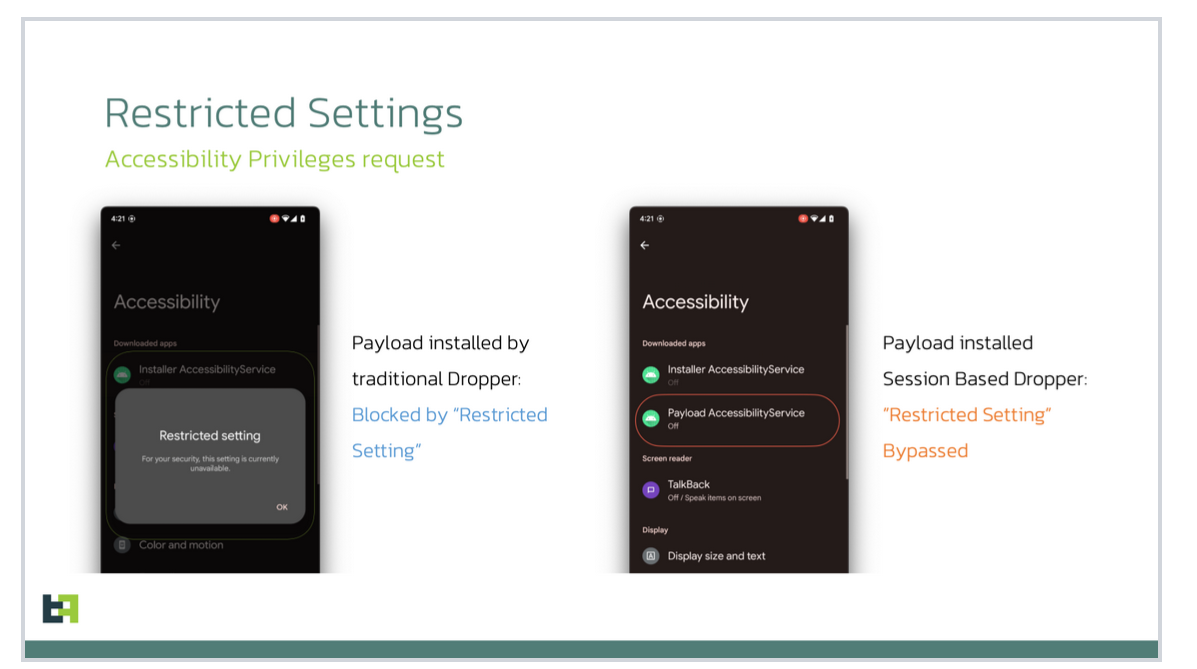
Category: Malware | Date: 6th January 2026
SecuriDropper represents a new and dangerous evolution in the cybercrime ecosystem, operating under the model of Dropper-as-a-Service (DaaS). As cyberattacks become increasingly automated and commercialized, services like SecuriDropper allow threat actors with minimal technical skills to deploy....

Category: Malware | Date: 5th January 2026
Complete Guide to Info-Stealer Malware: Threats, Indicators, and Mitigations Info-stealer malware has emerged as one of the most dangerous and rapidly growing cyber threats in recent years. Unlike ransomware, which announces its presence loudly, info-stealers operate silently in the background,....
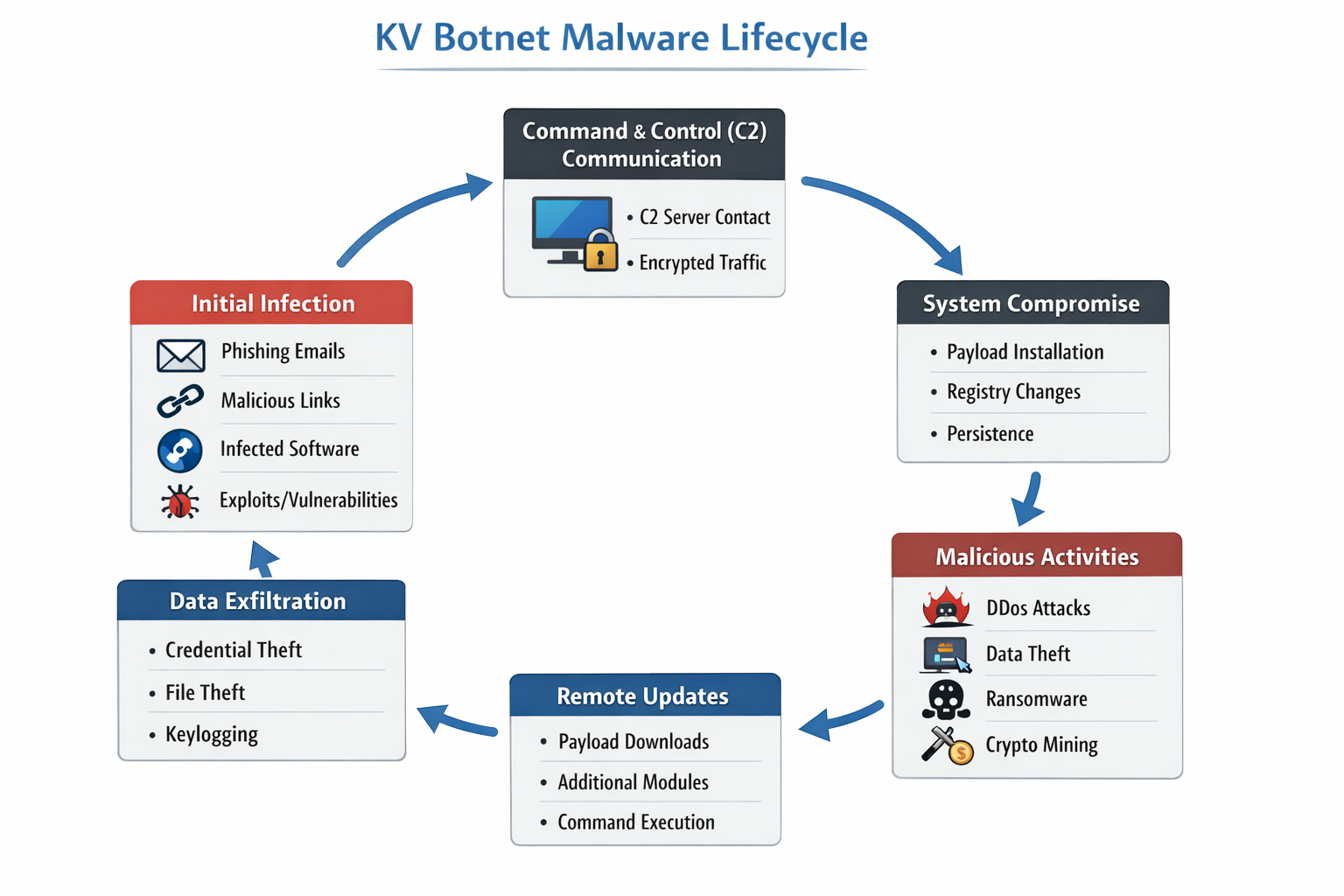
Category: Malware | Date: 3rd January 2026
The KV Botnet is an emerging and dangerous form of malware that has gained attention in the cybersecurity landscape due to its stealthy infection methods, command-and-control (C2) architecture, and ability to compromise large numbers of devices simultaneously. Botnets like KV Botnet are....
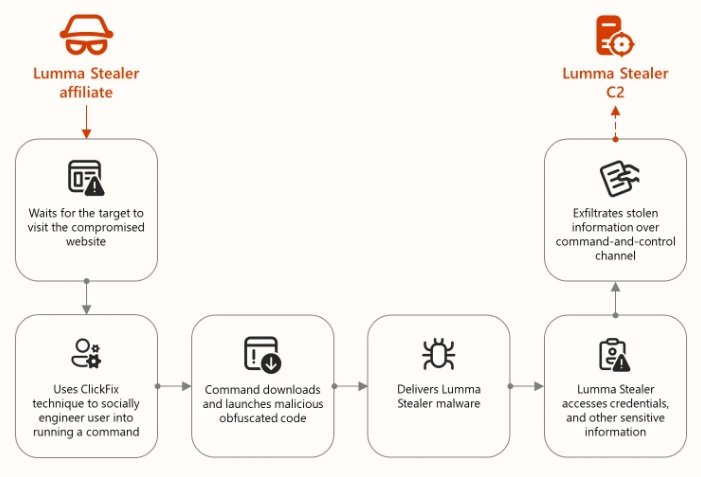
Category: Malware | Date: 22nd December 2025
Lumma Infostealer (also known as LummaC2) is a high-performance malware-as-a-service (MaaS) written in C and assembly language, active since August 2022. It is primarily used to harvest sensitive data from compromised Windows devices and is currently one of the most prevalent infostealers....
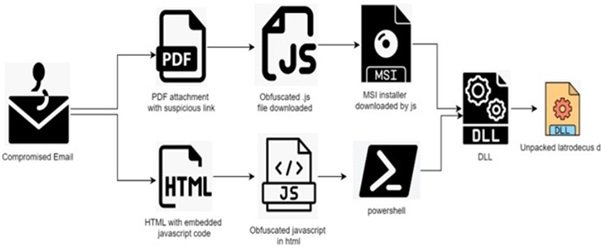
Category: Malware | Date: 18th December 2025
In the ever-evolving world of cybercrime, new threats often emerge to fill the voids left by dismantled botnets. Following the 2024 disruption of the infamous IcedID and Qakbot, a new apex predator has claimed the spotlight: Latrodectus. Named after the genus of the black widow spider,....
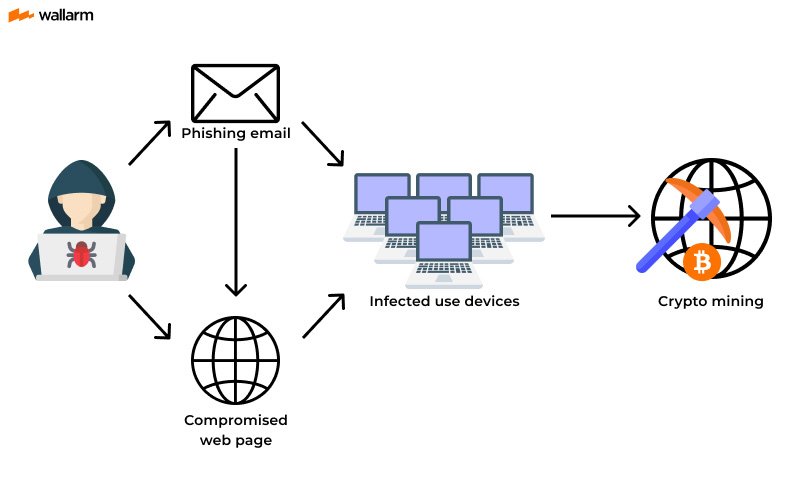
Category: Malware | Date: 20th November 2025
Malicious cryptomining—also known as cryptojacking—has rapidly become one of the most widespread and profitable cyber threats in the digital ecosystem. As cryptocurrencies continue to evolve, cybercriminals have shifted significantly from ransomware and data theft to stealthy....
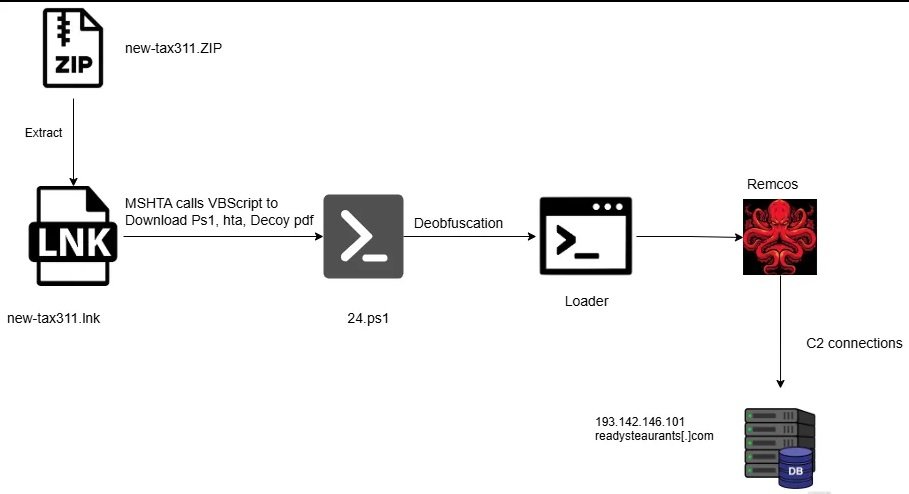
Category: Malware | Date: 10th November 2025
Remcos is a nasty one when delivered filelessly. Below I’ll turn your description into a compact, actionable threat brief you can use for detection, hunting, containment, and remediation (includes ready-to-run commands and detection rules you can drop into EDR/SIEM). I avoid inventing....

Category: Malware | Date: 16th August 2025
From ransomware that paralyzed hospitals to worms that defaced government websites, these malware attacks have left a permanent mark on digital history. Here's a breakdown of the 10 most devastating malware strains ever unleashed—each summarized in 100 words for quick insight and....

Category: Malware | Date: 2nd August 2025
Here’s a comprehensive list of the Top 10 Malware Families to Watch in 2025, based on recent trends, evolving attack vectors, and the increasing sophistication of cyber threats: ? Top 10 Malware Families to Watch in 2025 1. PhantomLayer Type: Modular Loader Targets: Windows....

Category: Malware | Date: 2nd August 2025
Introduction In recent years, messaging platforms have become prime targets for cybercriminals looking to exploit trust and popularity. One such target is Telegram, a widely-used messaging app known for its encrypted communications and broad user base. Cyber attackers are now weaponizing fake....
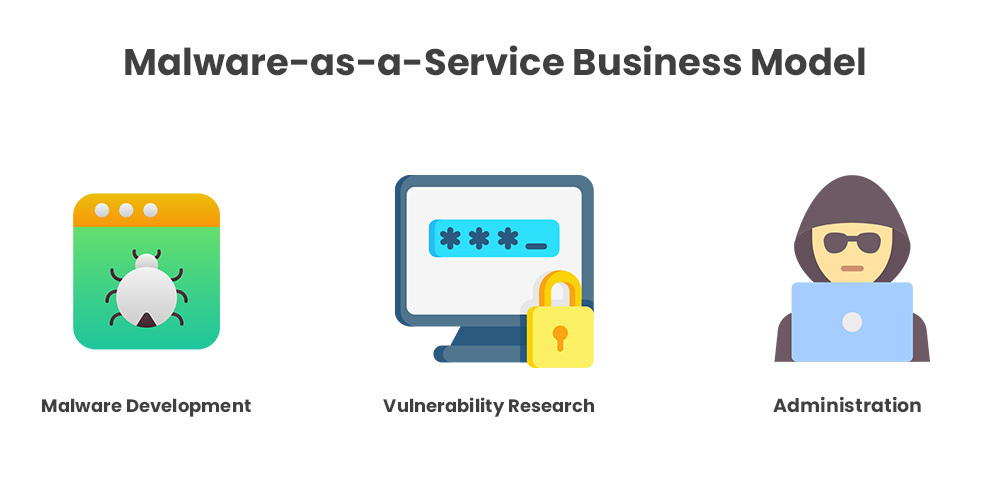
Category: Malware | Date: 1st August 2025
In the evolving world of cyber threats, traditional malware is no longer just a product of skilled hackers writing code in dark rooms. Today, cybercrime has become a full-fledged business, and Malware-as-a-Service (MaaS) is one of its most dangerous and fast-growing branches. MaaS platforms provide....

Category: Malware | Date: 27th July 2025
In recent years, India has witnessed a significant surge in cyberattacks targeting its critical infrastructure, including government websites, educational institutions, healthcare facilities, and private enterprises. Among the various types of cyber threats, malware and ransomware attacks have....

Category: Malware | Date: 1st June 2025
What is Lumma Stealer? Lumma Stealer (also known as LummaC2 or Lumma malware) is a Windows-based information-stealing trojan sold on underground forums as Malware-as-a-Service (MaaS). It is popular among cybercriminals because it's easy to deploy and provides real-time logs via Telegram, FTP, or a....

Category: Malware | Date: 24th April 2025
What is a Zero-Day Exploit? A Zero-Day Exploit is a type of cyberattack that targets a previously unknown vulnerability in software, hardware, or firmware. The term “zero-day” refers to the fact that developers have zero days to fix the issue because it has already been exploited by....
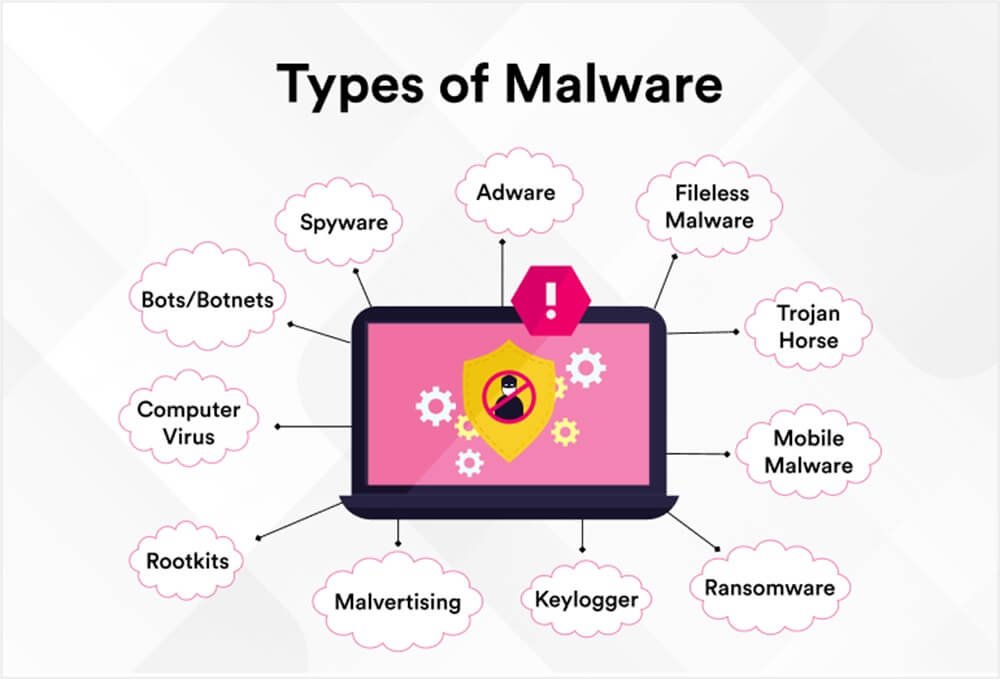
Category: Malware | Date: 20th April 2025
Types of Malware That Commonly Attack Systems in India (2025 Guide) In 2025, cyber threats are more aggressive than ever, especially in rapidly digitizing economies like India. From small businesses to government organizations, everyone is at risk. One of the biggest cybersecurity concerns in....

Category: Malware | Date: 14th June 2024
Introduction In the digital age, cybersecurity threats have evolved, becoming more sophisticated and harder to detect. Among these threats, SocGholish stands out as a notable example of a socially engineered malware campaign. This essay explores the origins, mechanisms, impact, and mitigation....

Category: Malware | Date: Friday, 22nd December 2023
A rootkit is a type of malicious software designed to gain unauthorized access to a computer or computing system while hiding its presence from the user and often from security software. Rootkits are particularly stealthy and can provide attackers with persistent access and control over a....

Category: Malware | Date: 22nd November 2023
AboutExtended emerges as another questionable application specifically aimed at Mac users. Its primary function revolves around executing activities commonly linked to adware and browser hijackers. Moreover, the application employs tactics to conceal its installation, utilizing dubious distribution....

Category: Malware | Date: 14th November 2023
Campo Loader (or NLoader) is a malware threat that is being leveraged in attack campaigns against Japanese entities. Campo Loader acts as an early-stage threat designed to deliver the real malware payloads on the already compromised computers. Campo Loader has been observed to drop several....

Category: Malware | Date: 11th November 2023
W32/Virut.gen is a destructive worm known for infecting and causing harm to various types of files. It primarily targets executable files but can also compromise HTML, PHP, and ASP files. Employing typical worm-like behavior, W32/Virut.gen spreads across connected drives, posing a risk to a range....

Category: Malware | Date: 11th November 2023
W32.Stuxnet!lnk is a precarious worm infection specifically targeting the Windows platform. Files affected by the W32.Stuxnet worm are commonly identified as W32.Stuxnet!lnk. W32.Stuxnet!lnk malware leverages the Microsoft Windows Shortcut 'LNK' Files Automatic File Execution Vulnerability to....

Category: Malware | Date: 11th November 2023
Lily Jade emerges as a worm infection capable of exploiting vulnerabilities across various web browsers, making it browser-independent. Operating on Java, Lily Jade often manifests as extensions for major browsers like Google Chrome, Mozilla Firefox, and Internet Explorer. Its primary objective is....

Category: Malware | Date: 11th November 2023
W32/Flame-A, commonly referred to as 'Flame,' has its roots traced back to Iran and subsequently spread across the Middle East and Northern Africa. The dissemination of information about W32/Flame-A was initially hindered by a media embargo, contributing to a delayed global awareness of its....

Category: Malware | Date: 11th November 2023
SecurityRisk.NetCat is a notorious spyware that poses a significant security threat to users' privacy and sensitive information. Known for its stealthy behavior, SecurityRisk.NetCat operates as a backdoor Trojan, enabling unauthorized access and control over infected systems. Once infiltrated,....

Category: Malware | Date: 11th November 2023
"Spyware.WebHancer.A" refers to a type of spyware known as WebHancer. WebHancer is a piece of software that was developed by eAcceleration Corporation. It was initially designed to collect information about users' internet browsing habits and provide feedback to website owners for the purpose of....

Category: Malware | Date: 27th October 2023
Malware, short for malicious software, is a persistent threat in today's digital age. It can compromise your personal information, damage your files, and even harm your computer's performance. Recognizing and removing malware promptly is crucial to safeguarding your digital life. In this guide, we....

Category: Malware | Date: 17th October 2023
Removing the DarkGate malware from your computer requires a systematic approach and the use of reputable security tools. Here’s a step-by-step guide to help you remove DarkGate malware from your system: 1. Isolate the Infected Computer: Disconnect your computer from the internet and any....

Category: Malware | Date: 28th September 2023
ZenRAT is a dangerous Remote Access Trojan (RAT) that can infiltrate your computer, steal sensitive information, and give cybercriminals remote access to your system. Removing ZenRAT from your computer is crucial to safeguard your privacy and security. This guide outlines the steps to effectively....
Category: Malware | Date: 28th September 2023
The internet has become an integral part of our daily lives, providing us with access to a wealth of information, entertainment, and services. However, this digital landscape is not without its dangers, and one of the most insidious threats that lurk in the online world is spyware. Spyware is....
Category: Malware | Date: 25th September 2023
Predator spyware is not a widely recognized or established term in the field of cybersecurity or information technology. It is possible that you may be referring to a specific piece of malicious software, but without more context or information, it is difficult to provide a detailed....

Category: Malware | Date: 8th September 2023
In recent years, the world has witnessed an alarming rise in digital espionage, with governments and organizations employing advanced technologies to surveil individuals and target adversaries. One such tool that has gained notoriety is the Pegasus spyware program, developed by the Israeli....

Category: Malware | Date: 19th August 2023
In the world of cybersecurity, new threats are constantly emerging, and one such threat that has gained notoriety is the LaplasClipper malware. LaplasClipper is a type of malicious software that poses a significant risk to cryptocurrency users and traders. In this article, we will explore what....

Category: Malware | Date: 18th August 2023
The cyber threat landscape is a dynamic and ever-evolving arena, with new malware strains constantly emerging to challenge the defenses of individuals and organizations alike. Gootloader malware, a relatively recent addition to the digital arsenal of cybercriminals, has garnered attention due to....

Category: Malware | Date: 18th August 2023
In the realm of cybersecurity, new and intricate threats emerge constantly, challenging defenders to stay ahead of the curve. The Whirlpool malware is a prime example of this evolving landscape. This article delves into the depths of the Whirlpool malware, its stealthy tactics, potential....

Category: Malware | Date: 18th August 2023
In the ever-evolving realm of cybersecurity threats, botnets have emerged as a powerful tool for cybercriminals to orchestrate large-scale attacks. The Gafgyt botnet, also known as BASHLITE, is one such notorious example that has wreaked havoc on the digital landscape. This article delves into the....

Category: Malware | Date: 18th August 2023
In the constantly evolving landscape of cybersecurity threats, malware remains a persistent adversary that wreaks havoc on both individuals and organizations. One such recent menace is the SystemBC malware. Known for its ability to compromise systems and facilitate other malicious activities,....
Category: Malware | Date: 4th August 2023
The digital landscape has witnessed a rapid evolution of malware over the past few decades. From simple viruses designed to cause nuisance to highly sophisticated and targeted attacks, malware has become a significant cybersecurity concern worldwide. As technology advances, cybercriminals....

Category: Malware | Date: 4th August 2023
In the ever-evolving landscape of cyber threats, new malware strains continue to emerge, challenging cybersecurity professionals and users alike. One such threat is DarkBERT, a sophisticated malware that poses serious risks to your computer's security and your sensitive data. DarkBERT belongs to....

Category: Malware | Date: 1st August 2023
In the ever-evolving world of cyber threats, new malicious software emerges regularly, targeting individuals, businesses, and governments alike. One such nefarious entity is the CherryBlos malware, a sophisticated cyber weapon designed to infiltrate and compromise computer systems covertly. In....

Category: Malware | Date: 29th July 2023
CVE-2023-37450 spyware, a dangerous and intrusive program designed to covertly collect sensitive information from unsuspecting victims. We will explore the nature of CVE-2023-37450 spyware, its potential implications, and most importantly, guide you through the steps to effectively remove it from....

Category: Malware | Date: 29th July 2023
The rapid advancement of technology has brought about remarkable innovations, but it has also given rise to the dark underbelly of the digital world: malware. One such threat is the notorious Atomic Stealer, a stealthy and malicious software that infiltrates systems to steal sensitive....

Category: Malware | Date: 29th July 2023
In today's digital landscape, the rise of sophisticated spyware poses a significant threat to our privacy and security. Among these threats, DragonEgg has emerged as a notorious spyware capable of infiltrating and compromising various devices. In this article, we will delve into the....

Category: Malware | Date: 29th July 2023
In an increasingly interconnected world, where technology governs every aspect of our lives, digital privacy and security have become paramount concerns. Unfortunately, with the rapid advancements in technology, cybercriminals have found new and sophisticated ways to exploit vulnerabilities and....

Category: Malware | Date: 27th July 2023
In the fast-paced digital world, cyber threats loom large, and one of the most insidious among them is info-stealing malware. This type of malicious software, designed to surreptitiously infiltrate systems, targets valuable personal and sensitive information, posing severe risks to individuals,....

Category: Malware | Date: 25th July 2023
The ever-evolving landscape of cybersecurity continues to witness new and sophisticated malware threats, and BundleBot is no exception. BundleBot is a malicious software that can wreak havoc on your system by infecting it with harmful components and potentially compromising your data and....

Category: Malware | Date: 25th July 2023
In the ever-evolving landscape of cybersecurity threats, new and sophisticated forms of malware continue to emerge, posing significant risks to individuals and organizations alike. One such malware that has garnered attention in recent times is WispRider, a self-propagating and....

Category: Malware | Date: 25th July 2023
SOGU Malware is a type of malicious software that poses a significant threat to your computer's security and can compromise your sensitive information. It is essential to detect and remove SOGU Malware promptly to prevent potential damage and safeguard your privacy. In this article, we will explore....

Category: Malware | Date: 24th July 2023
In the vast world of cybersecurity, new and complex threats constantly emerge, seeking to exploit vulnerabilities and compromise digital security. One such insidious menace is PicassoLoader malware, a sophisticated and deceptive cyberweapon that specializes in infiltrating systems and conducting....

Category: Malware | Date: 24th July 2023
In the ever-expanding realm of cybersecurity threats, new and sophisticated malware strains continue to emerge, posing significant risks to businesses and individuals worldwide. One such insidious threat is the ShadowPad malware, a highly sophisticated and elusive cyberweapon designed to infiltrate....

Category: Malware | Date: 24th July 2023
The relentless advancement of technology has brought about both incredible innovations and new avenues for cybercriminals to exploit. One such emerging threat is the BlackLotus UEFI bootkit malware, a sophisticated and dangerous cyberweapon that targets the Unified Extensible Firmware Interface....

Category: Malware | Date: 24th July 2023
As the prevalence of Linux systems grows across industries, cybercriminals are increasingly targeting this platform with advanced and evasive malware strains. One such notorious threat is AVrecon, a stealthy Linux-based malware that poses a significant risk to both individuals and organizations.....

Category: Malware | Date: 17th July 2023
In the realm of cybersecurity, the emergence of advanced surveillance tools has raised concerns about the erosion of privacy and the potential for abuse. Pegasus Spyware, developed by the Israeli company NSO Group, has gained significant attention for its powerful capabilities and alleged....
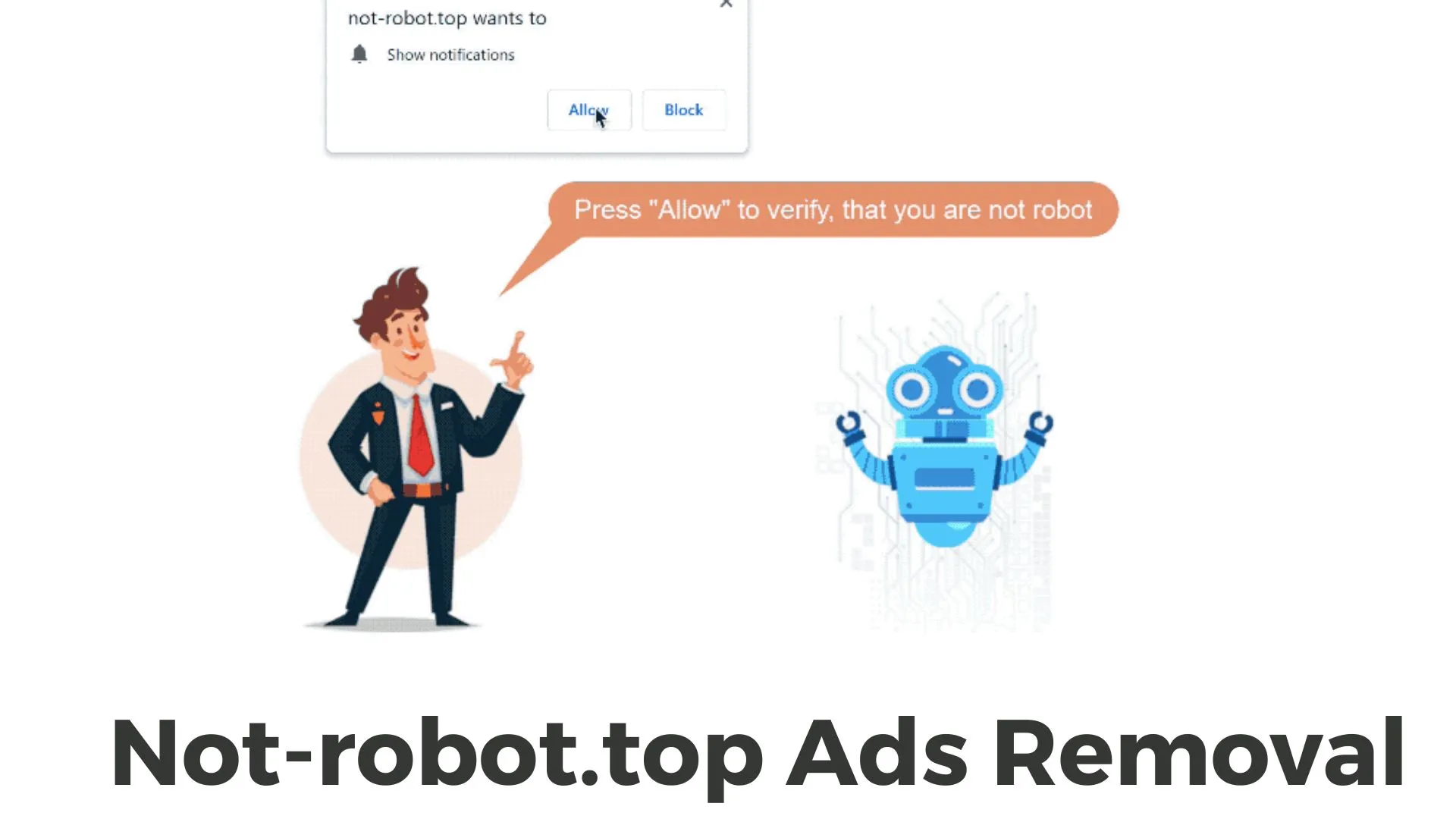
Category: Malware | Date: 17th July 2023
In the digital age, online advertisements have become an integral part of our daily browsing experiences. However, not all ads are created equal, and some can prove to be intrusive, disruptive, or potentially harmful. One such example is the emergence of Not-robot.top ads, which have garnered....

Category: Malware | Date: 13th July 2023
In the realm of cybersecurity, threats come in various forms, each seeking to exploit vulnerabilities and compromise sensitive information. One such class of malware that has gained notoriety is Infostealer malware. As the name suggests, Infostealers are malicious programs specifically designed to....

Category: Malware | Date: 13th July 2023
The ever-evolving landscape of cybersecurity threats continues to witness the emergence of new and potent malware strains. In recent developments, security researchers have uncovered a new attack vector that drops the LokiBot malware, posing a significant risk to individuals and organizations....

Category: Malware | Date: 13th July 2023
The ever-evolving landscape of cyber threats continues to surprise us with new malware strains and attack vectors. In recent developments, security researchers have identified a novel Linux malware called PyLoose that poses a significant risk to cryptocurrency owners and miners. Unlike traditional....

Category: Malware | Date: 10th March 2023
There are number of issues while malware can invade your computer system. Malware will incorporate your computer system with number of paths, where you cannot decide as well. However, malware will adopt social website to spread itself with discounts offers, best deals, strange web links and other....

Category: Malware | Date: 21st February 2023
Worm:VBS/Jenxcus.CB Is A Computer Worm, That Replicates Itself In Order To Disperse To Other System. Often Worm:VBS/Jenxcus.CB Uses A Computer Network To Reach Own Destination. Worm:VBS/Jenxcus.CB Is A Malware Program, That Can Hurt Various Significant Files, Folders, Standalone Application....

Category: Malware | Date: 16th February 2023
Webbelse Is A Destructive Internet Bug Created For The Purpose Of Hacking Into A Computer System And Extract Information About Concerned User's Surfing Activities, Session Data And More. The Data Gathered By Webbelse Is Badly Utilized To Other Third Party Vendors So That They Can Gain Profit....

Category: Malware | Date: 16th February 2023
Web Monitor Is A Destructive Internet Bug Created For The Purpose Of Hacking Into A Computer System And Extract Information About Concerned User's Surfing Activities, Session Data And More. The Data Gathered By Web Monitor Is Badly Utilized To Other Third Party Vendors So That They Can Gain....

Category: Malware | Date: 15th February 2023
I-worm.dumaru.c Is A Perilous Computer Worm, Which Is Categorized As A Malware Code, That Can Replicate Itself From One Computer To Computer. I-worm.dumaru.c Is Appeared With Various Version. In The Recent Version Of I-worm.dumaru.c Is C.3 From Client’s PC. I-worm.dumaru.c Is Reside In....
Category: Malware | Date: 14th February 2023
A rootkit is a type of malware designed to gain unauthorized access to a computer system or network and hide its presence from users and security systems. Rootkits are often used by attackers to gain administrative or "root" privileges on a system, allowing them to control the system and carry out....

Category: Malware | Date: 14th February 2023
Worm.WORM/LNK.Usbitna.Gen Is Dispense Automatically To Other Computer System. Worm.WORM/LNK.Usbitna.Gen Can Replicate Itself And Without Any Assistance. Thus, Worm.WORM/LNK.Usbitna.Gen Is A Potentially Treacherous Computer Worm. The Removal Devices, Private Network, Computer Network, Is....

Category: Malware | Date: 14th February 2023
A worm or computer worm is a type of malware that is able to self-replicate and spread throughout a computer network or the internet. It typically exploits vulnerabilities in software to infect systems and can cause damage to computer systems and networks by consuming system resources, deleting....
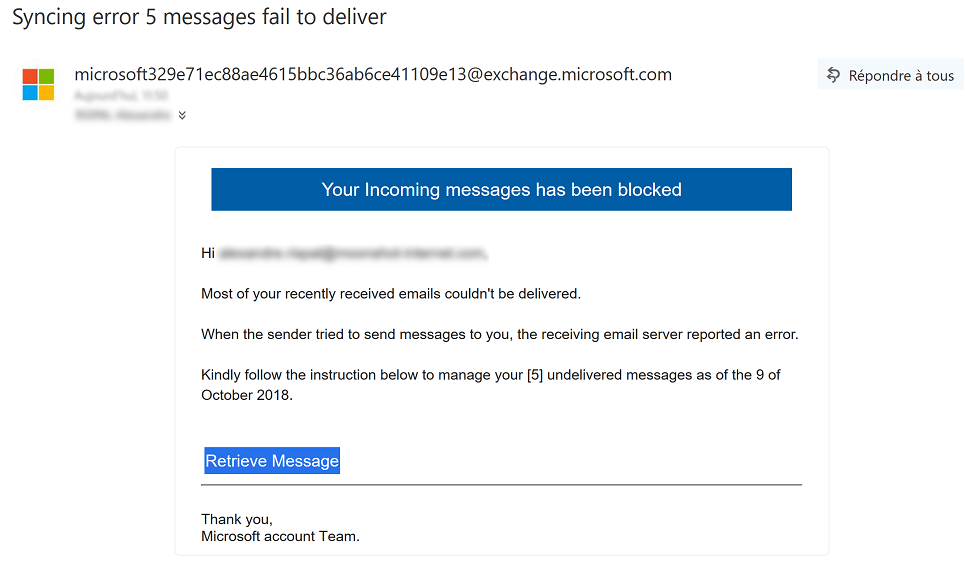
Category: Malware | Date: 14th February 2023
Phishing.PHISH/Fraud.CN Is A New Kind Of Method For Stealing The Data From The PC And Usable Terminal. Phishing.PHISH/Fraud.CN Is A Very Dangerous And Jeopardy Program Code, Because Phishing.PHISH/Fraud.CN Does Not Scan By The Firewall As Well As An Obsoleted Computer Security Software.....

Category: Malware | Date: 3rd February 2023
Apple Mac OS X Operating System Is A Contaminated In These Day By Adware, Virus, Worm, Browser Hijacker, Spyware And Other Malicious Program. Main Goals Of This Program To Mislead Online And Generate Revenue From The Internet. It Develops Web Traffic, Amass Sales Information, Browser History,....

Category: Malware | Date: 2nd February 2023
AUEPMaster.exe Is An Executable File, Which Is Incorporated With AMD (Advanced Micro Device). The Full Name Of AUEPMaster.exe Executable File Is AMD User Experience Program Master, Which Is Belong To Application Support.amd.com Or AUEPMaster Through AMD(Advanced Micro Devices) Www.amd.com.....

Category: Malware | Date: 2nd February 2023
“Something Threaten Online With Sensitive Information” Is A Very Deceitful Information, Which May Hurt Your Sentiment. “Something Threaten Online With Sensitive Information” Will Show That Your Account Has Been Affected By The Some “Spambot Attack” Program.....

Category: Malware | Date: 11th March 2022
Spyware is a very intrusive computer system application to spying the users activity. Spyware is a closely related with adware program and attach with browser hijacker trojan virus and ransomware. Spyware can violate number of cyber law and internet privacy policy. History of the Spyware? Types....

Category: Malware | Date: 3rd February 2022
Malware is a malicious program and malware is a file or code, typically delivered over a computer network, that affects, explores thefts or conducts virtually any behaviour an attack wants. Malware is malign software to target the client’s computer system for gaining others resources for....