 Category's Page
Category's Page

Category: Info | Date: 27th February 2026
A morph attack is a type of biometric identity fraud in which two or more facial images are digitally blended to create a single composite image that resembles each contributing individual. The resulting image can sometimes be successfully verified as both people by facial recognition systems.....

Category: Info | Date: 27th February 2026
Introduction A morph image refers to a digitally altered visual created by smoothly transforming one image into another. The term “morph” comes from the word metamorphosis, meaning transformation. In digital imaging, morphing involves gradually blending the structure, shape, color, and....

Category: Info | Date: 26th February 2026
1. Introduction In today’s digital landscape, privacy, security, and unrestricted access to information are essential. Virtual Private Networks (VPNs) have become a key solution for individuals and businesses seeking to protect their online activities. One prominent provider in this field is....

Category: Info | Date: 26th February 2026
In an era where digital life moves faster than ever, privacy has become one of the most valuable commodities online. Every click, search, download, and stream leaves behind a trail of data that can be tracked, analyzed, sold, or even exploited. Hide.me VPN Download From intrusive advertisers to....

Category: Info | Date: 25th February 2026
In today’s digital world, online privacy is no longer optional — it’s essential. Whether you’re browsing from home, working remotely, streaming content, or using public Wi-Fi, your personal data is constantly at risk. That’s where Hide.me VPN comes in. Get Hide.me....

Category: Info | Date: 18th December 2025
The holiday season is the most wonderful time of the year—and the busiest for cybercriminals. As we head into Christmas 2025, online shopping, holiday travel, and new gadget activations are at an all-time high. Whether you are hunting for last-minute deals or streaming festive classics from....
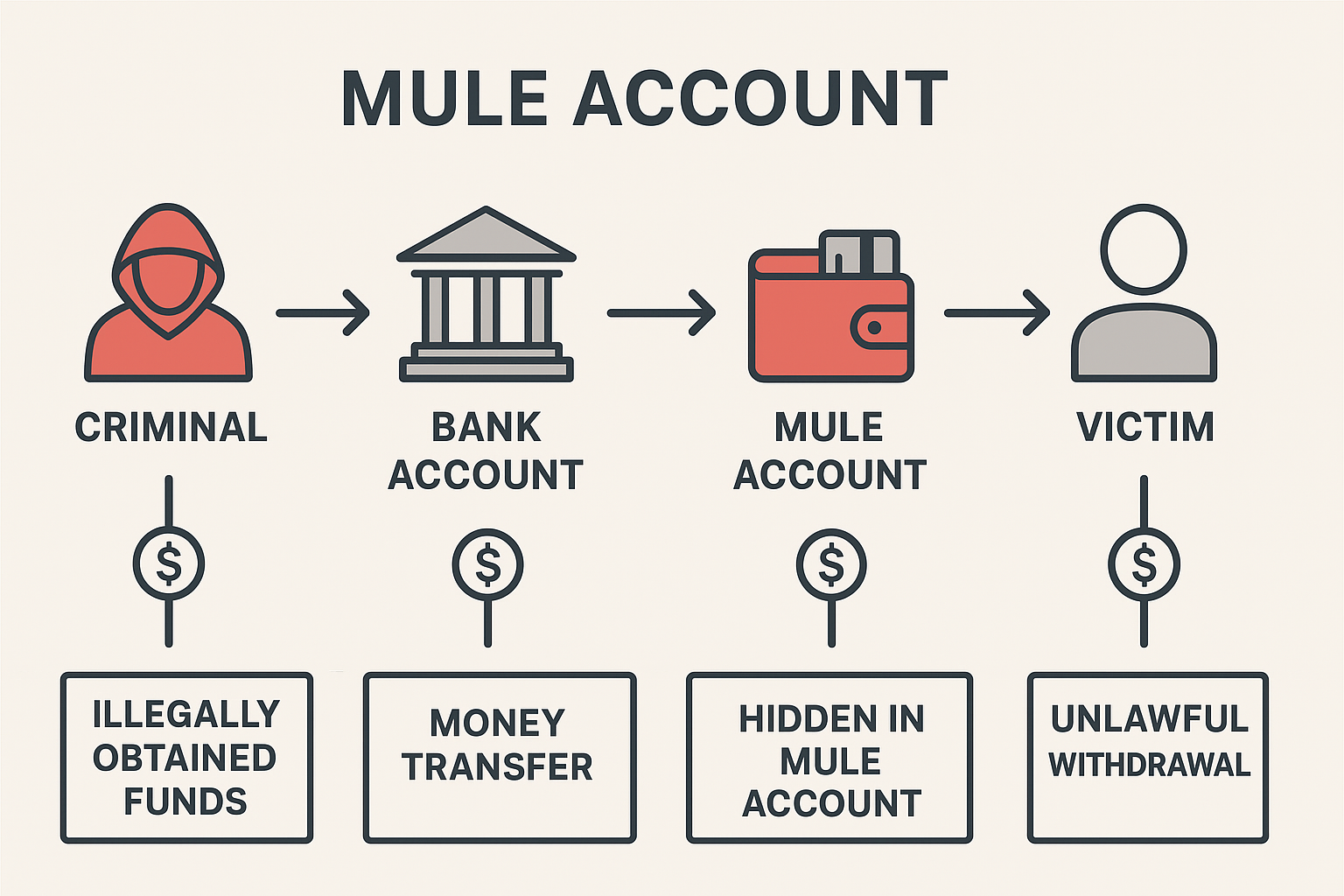
Category: Info | Date: 21st November 2025
1. Introduction A mule account, often called a money mule account, is a bank account used—knowingly or unknowingly—to receive, transfer, or withdraw illegally obtained money on behalf of criminals. In the global financial crime ecosystem, mule accounts are a crucial layer of....
Category: Info | Date: 20th November 2025
In the digital world, every device connected to the internet communicates using an IP (Internet Protocol) address. Whether you browse a website, send an email, use WhatsApp, log into social media, or stream a video—your device interacts through IP addresses. Understanding IP address tracking....

Category: Info | Date: 20th November 2025
In the world of digital communications, every mobile device continuously exchanges signals with nearby cell towers. These towers, also known as Base Transceiver Stations (BTS), form the backbone of mobile networks and are responsible for routing calls, SMS, and mobile data traffic. One of the most....
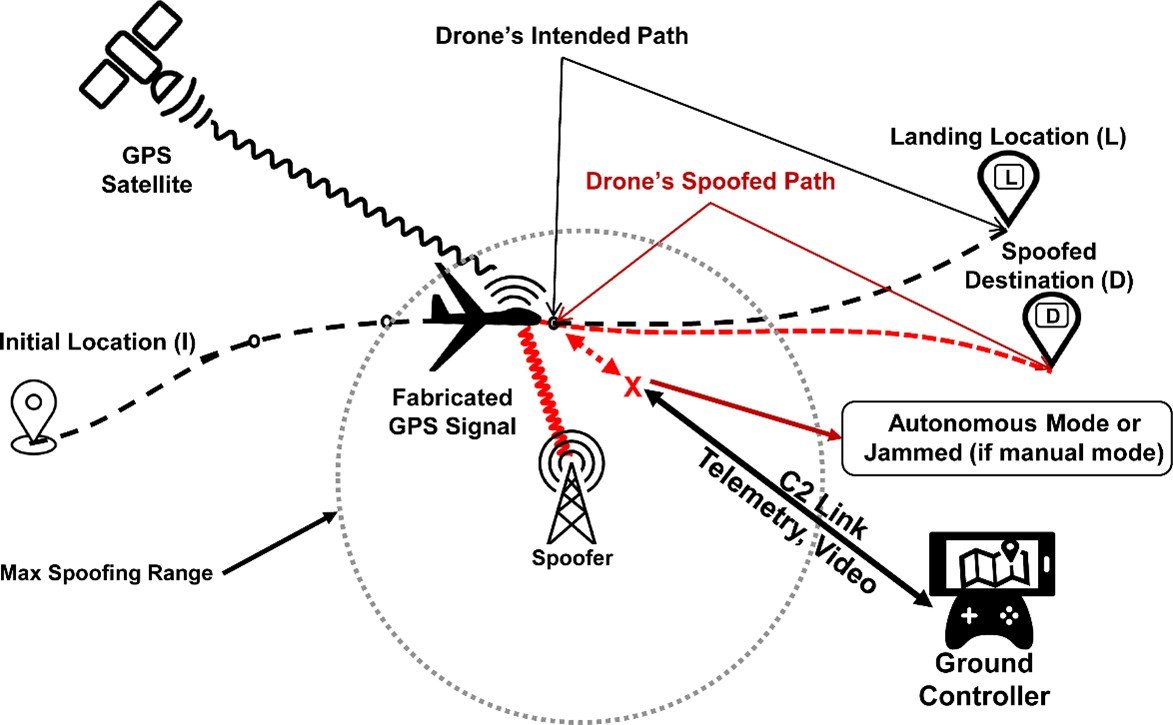
Category: Info | Date: 12th November 2025
Introduction Global Positioning System (GPS) spoofing is the deliberate transmission of counterfeit GNSS (Global Navigation Satellite System) signals to deceive a receiver about its position, velocity, or time. Unlike jamming, which denies service by overwhelming receivers with noise, spoofing....
Category: Info | Date: 3rd November 2025
As the end-of-year shopping frenzy approaches, the term “Black Friday” takes on new meaning for everything from TVs to toasters—and cybersecurity tools are no exception. One deal that savvy internet users should have on their radar is the Black Friday 2025 promotion from NordVPN.....

Category: Info | Date: 1st November 2025
Black Friday 2025 is here, and it’s bringing one of the most exciting cybersecurity offers of the year — 56% off the NordPass Password Manager. Whether you’re a student, a business owner, or simply someone who values online privacy, this is the perfect time to strengthen your....
Category: Info | Date: 1st November 2025
NordVPN Here’s a detailed overview of NordVPN, how it protects your online privacy, what features it offers, and some points to consider — especially relevant since you’re interested in security and privacy topics. Black Friday: Get 56% off a NordPass Personal plan What is....

Category: Info | Date: 31st October 2025
In today’s hyper-connected world, our digital lives are under constant surveillance—by hackers, advertisers, and sometimes even governments. Every time you log in, shop online, or connect to public Wi-Fi, your personal data can be exposed to cyber threats. This is where NordVPN Security....

Category: Info | Date: 31st October 2025
New Data on Payment Card Theft In an age where nearly every purchase we make passes through a digital channel, payment card theft has become one of the most prevalent cybercrimes in the world. Criminals no longer need to steal a wallet from a pocket—they can drain an account with just a few....
Category: Info | Date: 29th October 2025
In today’s digital landscape, cybersecurity has become one of the most critical priorities for businesses of all sizes. With the increasing number of online accounts, tools, and digital services companies rely on, managing passwords securely is no longer a choice—it’s a necessity.....
Category: Info | Date: 24th October 2025
Introduction: The Smartest Black Friday Deal for Password Security Black Friday 2025 has arrived, and with it comes a flood of discounts across every digital platform. But among all these offers, one stands out for its sheer value and long-term importance — the NordPass Black Friday deal.....

Category: Info | Date: 24th October 2025
Black Friday is the year’s best moment to buy a premium VPN: companies slash multi-year plans, throw in extra months, and bundle in extras (antivirus, password managers, cloud storage). Black Friday 74% Discount + 3 Months Extra (30 days money back guarantee) If you want a fast, private,....

Category: Info | Date: 22nd October 2025
The wait is over! Black Friday 2025 is here, and NordPass—the trusted password manager from the cybersecurity experts behind NordVPN—is offering an unbeatable 56% discount on its Personal Plan. If you’ve been struggling to remember dozens of passwords, or if you’ve been....
Category: Info | Date: 22nd October 2025
Black Friday is back, and so is one of the biggest digital privacy deals of the year! NordVPN is offering a massive 73% discount on its premium VPN plans this Black Friday 2025 — making it the perfect opportunity to secure your online life without breaking the bank. Whether you want to....
Category: Info | Date: 18th October 2025
As the most anticipated shopping event of the year approaches, the buzz isn’t just about discounted gadgets and fashion—it’s also a golden moment to lock in your digital security at a bargain. Enter NordVPN’s Black Friday Special 2025, a deal that marries strong online....

Category: Info | Date: 16th October 2025
In today’s era of hybrid communication, where live streaming, online teaching, and virtual meetings dominate daily life, having a reliable and feature-rich webcam software is no longer optional — it’s essential. ManyCam 9 has emerged as one of the most powerful solutions for....

Category: Info | Date: 16th August 2025
Fix for Battlefield 6 Beta: "Secure Boot Not Enabled" Error Battlefield 6 is finally here with its adrenaline-pumping beta, but many PC players are hitting a frustrating wall: the dreaded “Secure Boot is not enabled” error. If you're one of them, don’t worry—this guide will....

Category: Info | Date: 10th August 2025
In the modern world, computers are essential for work, study, and entertainment. However, over time, they tend to slow down due to junk files, outdated settings, and malware infections. This is where Advanced System Repair Pro shines as a powerful PC optimization software. Download Advanced....

Category: Info | Date: 10th August 2025
In today’s digital age, the internet is both a source of immense convenience and a breeding ground for cyber threats. Every click, download, or website visit carries a potential risk of malware infection, phishing attacks, or ransomware. Buy Now - Malwarebytes This is where....
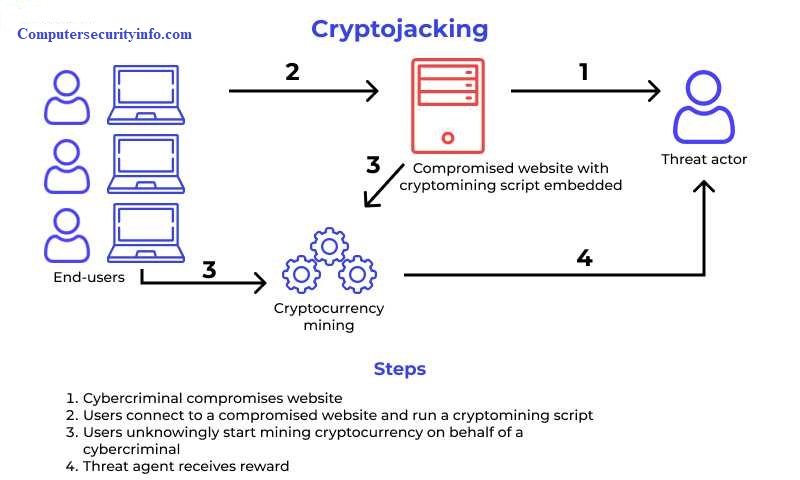
Category: Info | Date: 27th July 2025
Introduction Cryptocurrency has reshaped the digital finance landscape, but it has also opened new doors for cybercriminals. One such growing menace is cryptojacking—a stealthy cyberattack where hackers hijack your computing power to mine digital currencies without your consent. Unlike....

Category: Info | Date: 17th July 2025
FPGA security solutions encompass a range of hardware and software techniques to protect FPGA-based systems from various threats. These include secure boot, hardware isolation, encryption, access control, and monitoring mechanisms. By integrating these features, FPGAs can be used....

Category: Info | Date: 17th July 2025
Unmasking Digital Danger: The Most Common Threats to Information Security In an increasingly connected world, information security isn’t just a concern for tech giants or government agencies—it’s a necessity for everyone. Whether you're a business owner, casual internet user, or....

Category: Info | Date: 17th July 2025
Fortifying Your Digital Fortress: How to Enhance Home Computer Security In a world where our lives are increasingly entangled with technology—from finances and communication to entertainment and work—the need for airtight home computer security has never been more vital. Cybercriminals....

Category: Info | Date: 9th June 2025
A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic based on predefined security rules. Its primary purpose is to establish a barrier between a trusted internal network and untrusted external networks, such as the internet, to prevent....

Category: Info | Date: 1st June 2025
In today’s fast-evolving cyber threat landscape, antivirus software isn’t just a recommendation—it’s a necessity. As malware, ransomware, phishing, and zero-day attacks continue to rise, users need more than just a basic virus scanner. They need advanced, real-time....

Category: Info | Date: 1st June 2025
Advanced System Repair Pro In the digital age, maintaining a healthy and optimized PC system is essential for productivity, security, and overall user experience. Over time, computers tend to slow down due to cluttered registries, junk files, fragmented disks, and unnecessary startup programs. To....

Category: Info | Date: 31st May 2025
In today’s increasingly digital world, computer security—also known as cybersecurity—has become a crucial concern for individuals, businesses, and governments alike. As we rely more heavily on computer systems, networks, and cloud platforms to store, process, and transmit....

Category: Info | Date: 21st May 2025
In an era where online privacy is constantly under threat and cyberattacks are becoming increasingly sophisticated, protecting your digital life has never been more important. One of the most reliable ways to secure your online activity is by using a Virtual Private Network (VPN). Among the top VPN....

Category: Info | Date: 20th May 2025
In a world where digital surveillance, data breaches, and cybercrime are becoming the norm, taking control of your online privacy is no longer optional—it’s essential. One of the most effective tools for securing your internet activity is a Virtual Private Network (VPN). Among the most....

Category: Info | Date: 18th May 2025
NordPass is a powerful password management software developed by the creators of NordVPN, designed to simplify and secure the way users manage their online credentials. With NordPass, users can securely store, generate, and autofill passwords across multiple devices, ensuring that sensitive....

Category: Info | Date: 18th May 2025
NordVPN is a leading virtual private network (VPN) service provider that has gained a reputation for its robust security features, extensive server network, and user-friendly interface. Established in 2012 and based in Panama, NordVPN is well-regarded for its strict no-logs policy and strong....

Category: Info | Date: 17th April 2025
In today’s digital landscape, data breaches and device theft are constant threats. One powerful tool that helps businesses secure sensitive information is Bitdefender Full Disk Encryption. Designed for endpoint protection, Bitdefender Full Disk Encryption helps ensure that your organization's....

Category: Info | Date: 17th April 2025
Bitdefender Patch Management: The Smart Way to Automate Software Updates In the ever-evolving world of cybersecurity, keeping systems up to date is one of the most effective ways to defend against vulnerabilities and attacks. Yet, many organizations still struggle with manual patching, outdated....

Category: Info | Date: 17th April 2025
In today’s rapidly evolving threat landscape, businesses of all sizes need advanced protection against malware, ransomware, phishing, and other cyberattacks. Bitdefender GravityZone Business Security is a trusted solution that offers robust, AI-driven security for endpoints, servers, and....

Category: Info | Date: 17th April 2025
In today’s digital-first world, high-quality video communication is essential—whether you're a content creator, teacher, live streamer, or business professional. ManyCam 9 is here to elevate your video experience with its newest update, packed with cutting-edge features and improved....

Category: Info | Date: 19th July 2024
EaseUS Todo Backup Home is a robust backup software designed to safeguard your data with ease and efficiency. Ideal for both novice and advanced users, it offers a comprehensive suite of features to ensure your files, operating systems, and applications are securely backed up and ready for recovery....

Category: Info | Date: 12th July 2024
Indonesia, the world's fourth most populous nation, has faced a significant cybersecurity challenge: a major ransomware attack. This attack, which has compromised critical data and systems, is a stark reminder of the vulnerabilities in the digital landscape. As Indonesia embarks on the arduous task....

Category: Info | Date: 21st June 2024
In today's digital era, privacy and security have become paramount concerns for internet users. With increasing cyber threats, government surveillance, and data breaches, protecting online activities is more critical than ever. NordVPN, developed by Nord Security, is a leading solution designed to....

Category: Info | Date: 21st June 2024
In the contemporary digital landscape, where the average user has to manage a multitude of online accounts, password security is paramount. Managing these passwords effectively and securely can be a daunting task. NordPass, developed by Nord Security, offers a solution designed to simplify....

Category: Info | Date: 21st June 2024
In an era where cyber threats are constantly evolving, having a robust firewall is essential for protecting personal and professional data. ZoneAlarm Pro Firewall, developed by Check Point Software Technologies, offers advanced security features that make it a crucial tool for anyone serious about....

Category: Info | Date: 21st June 2024
In a world increasingly dependent on digital interactions and online presence, cybersecurity has become a fundamental necessity. Cyber threats such as malware, phishing, and hacking are ever-evolving, posing significant risks to personal and professional data. ZoneAlarm Pro Antivirus + Firewall....

Category: Info | Date: 21st June 2024
In today's digital landscape, cybersecurity is paramount. With increasing threats from malware, phishing, ransomware, and other cyber-attacks, individuals and businesses need robust security solutions to protect their data and privacy. ZoneAlarm Extreme Security NextGen ZoneAlarm Extreme Security....

Category: Info | Date: 8th June 2024
Introduction Malwarebytes is a leading cybersecurity company known for its effective malware detection and removal tools. With a range of products designed for both personal and business use, Malwarebytes offers various pricing plans to suit different needs and budgets. This guide provides an....

Category: Info | Date: 8th June 2024
Introduction Malwarebytes is a widely recognized name in the cybersecurity industry, known for its powerful and user-friendly software designed to protect computers and mobile devices from a variety of cyber threats. Founded in 2008, Malwarebytes has grown to become a trusted tool for millions of....
Category: Info | Date: 13th March 2024
What is Advance System Care? Advanced System Care is a popular optimization software developed by IObit, designed to improve the performance and security of Windows-based computers. Advanced System Care offers a range of features aimed at optimizing system performance, cleaning up junk files,....

Category: Info | Date: 11th March 2024
What is iTop Screen Recorder? "iTop Screen Recorder" appears to be a screen recording software designed for capturing activities on your computer screen. It enables users to record their screens, which is useful for creating tutorials, demonstrating software features, or capturing gameplay. iTop....

Category: Info | Date: 11th March 2024
As of my last update in January 2022, iTop VPN is a virtual private network (VPN) service. VPNs like iTop VPN allow users to establish a secure connection to another network over the internet. They can be used to access region-restricted websites, shield browsing activity from prying eyes on public....

Category: Info | Date: 23rd November 2023
The Comprehensive DIY Data Recovery Tool for Mac is a user-friendly software solution designed to empower users in recovering lost or deleted files from their Mac systems. With an intuitive interface and powerful features, this tool allows users to perform in-depth scans of their storage devices,....

Category: Info | Date: 23rd November 2023
DIY Data Recovery Software for Windows is a user-friendly tool designed to help individuals recover lost or deleted files from their Windows-based systems. This software empowers users to perform data recovery operations independently, without the need for professional assistance. With intuitive....

Category: Info | Date: 11th November 2023
ZoneAlarm is a comprehensive cybersecurity solution offering both antivirus and firewall protection. As an antivirus, ZoneAlarm employs advanced threat detection mechanisms to safeguard your system from a wide range of malicious software, including viruses, malware, and spyware. It continuously....

Category: Info | Date: 11th November 2023
SpyHunter 5 stands as a stalwart defender of your computer, providing robust security against sophisticated malware threats and potential hacker intrusions. Tailored with an intuitive user interface, SpyHunter 5 seamlessly integrates advanced protection to fortify your online security and shield....

Category: Info | Date: 11th November 2023
A Virtual Private Network (VPN) can be a valuable tool for protecting your data by encrypting your internet connection and providing a secure tunnel for your online activities. Why Use a VPN? A VPN encrypts your internet connection, making it more challenging for hackers, ISPs, or government....

Category: Info | Date: 11th November 2023
Resetting your internet browser can help to eliminate unwanted changes, extensions, or settings that may have been caused by malware or other issues. The steps for resetting a browser can vary slightly depending on the browser you're using. Here are instructions for some of the most common....

Category: Info | Date: 11th November 2023
Removing a malicious extension from your internet browser is essential to ensure the security and stability of your browsing experience. Here are general steps you can follow for some of the most commonly used browsers: Google Chrome: Open Chrome and click on the three vertical dots in the....

Category: Info | Date: 6th November 2023
Avira Antivirus is a renowned cybersecurity solution that provides robust protection against malware, viruses, ransomware, and other online threats. Founded in 2006, Avira has gained a global reputation for its advanced security technologies, user-friendly interface, and commitment to keeping users....

Category: Info | Date: 4th November 2023
Malwarebytes Premium Malwarebytes Premium is a powerful cybersecurity solution designed to protect your digital life from a wide range of threats. With Malwarebytes Premium advanced technology and user-friendly interface, Malwarebytes Premium offers comprehensive real-time protection against....

Category: Info | Date: 2nd November 2023
In the modern era, where the world relies heavily on digital technologies, the concept of computer security plays a pivotal role in the broader domain of information security. Computer security, a subset of information security, focuses specifically on safeguarding computer systems, networks, and....

Category: Info | Date: 1st November 2023
In the interconnected world of the internet, cyber threats can transcend borders, affecting nations and organizations worldwide. India, a rapidly advancing digital economy, has not been immune to these threats. One such significant incident was the Mirai botnet malware attack, a global....

Category: Info | Date: 1st November 2023
In the digital age, where connectivity is paramount, telecommunications companies play a crucial role in keeping nations connected. However, they are not immune to cyber threats. One such incident that sent shockwaves through the tech world was the BSNL (Bharat Sanchar Nigam Limited) malware....

Category: Info | Date: 1st November 2023
In recent years, India has become a prime target for cybercriminals launching devastating ransomware attacks. These attacks have not only disrupted critical sectors but also highlighted the pressing need for robust cybersecurity measures nationwide. In this article, we delve into the seven most....

Category: Info | Date: 1st November 2023
In the ever-evolving landscape of cybersecurity, adware remains a persistent threat, disrupting users' online experiences and compromising their privacy. As the digital realm expands, the demand for effective adware removal solutions has surged. This market analysis delves into the Adware Removal....

Category: Info | Date: 1st November 2023
As the holiday season approaches, tech enthusiasts and privacy-conscious individuals eagerly await the biggest shopping event of the year – Black Friday. This year, the excitement is amplified for online security enthusiasts as leading Virtual Private Network (VPN) providers gear up to offer....

Category: Info | Date: 27th October 2023
As the digital landscape continues to expand, ensuring your online privacy and security is paramount. In the vast sea of VPN services, Surfshark stands out as a reliable and feature-rich option. This Black Friday, gear up to unlock exclusive Surfshark VPN deals that promise not only affordability....

Category: Info | Date: 27th October 2023
Black Friday, the much-anticipated shopping extravaganza, is just around the corner, and shoppers are gearing up for unbeatable discounts and jaw-dropping deals. As we approach the year 2023, retailers are gearing up to offer some of the most enticing offers ever seen. From cutting-edge....

Category: Info | Date: 28th September 2023
In an increasingly digital world, Mac users are not immune to cybersecurity threats. While macOS is known for its robust security features, it's still essential to have a reliable antivirus software installed to safeguard your Mac from potential threats. With the ever-evolving landscape of....

Category: Info | Date: 28th September 2023
In today's interconnected world, online privacy and security have become paramount. A Virtual Private Network (VPN) is a powerful tool that ensures your data remains secure and your online activities private. For Windows users, finding the right VPN can make a significant difference in....

Category: Info | Date: 26th September 2023
Losing important files on your Windows 10 computer can be a frustrating and distressing experience. Whether it's due to accidental deletion, a corrupted storage device, or an unexpected system crash, the fear of losing valuable data can haunt anyone. Fortunately, Windows 10 offers several methods....

Category: Info | Date: 25th September 2023
The Windows Subsystem for Linux (WSL) is a powerful tool that allows users to run a Linux distribution alongside their Windows operating system. It provides developers and enthusiasts with a seamless way to use Linux utilities and tools without the need for a separate virtual machine. However,....

Category: Info | Date: 21st September 2023
In today's interconnected world, where we rely on the internet for almost every aspect of our lives, ensuring the security of our digital devices has become paramount. Malware, viruses, and cyber threats are ever-evolving, making it crucial to have reliable antivirus software installed on your....
Category: Info | Date: 14th September 2023
In the age of technology, our computers accumulate various unwanted files, software, and bloatware over time. This digital clutter not only occupies precious storage space but can also slow down your system's performance. To combat this issue, we rely on junkware removal tools – specialized....

Category: Info | Date: 14th September 2023
In today's interconnected world, where we spend a significant portion of our lives online, we are constantly bombarded by advertisements. While ads are an essential part of the digital ecosystem, some advertisements cross the line into the realm of annoyance and invasiveness. This is where....

Category: Info | Date: 11th September 2023
In the world of computer viruses and malware, one particularly insidious type of threat is the file-infecting virus. These viruses are designed to infiltrate and manipulate executable files on a computer, compromising its integrity and potentially causing significant harm. In this article, we will....
Category: Info | Date: 11th September 2023
Oculus VR has revolutionized the world of virtual reality, offering immersive experiences that transport users to different worlds. However, as with any software, Oculus users occasionally encounter installation issues that can be frustrating. One such problem is the "We Encountered an Error"....

Category: Info | Date: 11th September 2023
In today's digital age, our lives are increasingly intertwined with the online world. From emails and social media to online banking and shopping, we rely on numerous accounts, each requiring a password for access. With the growing importance of cybersecurity, it's crucial to keep your passwords....

Category: Info | Date: 9th September 2023
As smartphones become an integral part of our daily lives, protecting our Android devices from malware and cyber threats is of paramount importance. In 2023, the threat landscape is continuously evolving, and it's crucial to have a robust antivirus solution in place to safeguard your Android....

Category: Info | Date: 9th September 2023
In today's digital landscape, the threat of ransomware attacks looms larger than ever before. Ransomware can encrypt your valuable data and demand a ransom for its release, causing severe damage to individuals and organizations alike. To safeguard your data and systems against such threats, it's....

Category: Info | Date: 23rd August 2023
In today's interconnected digital world, the ability to run a wide array of Windows applications seamlessly on non-Windows systems has become a necessity for many. Enter Parallels Desktop, a versatile virtualization solution that empowers users to effortlessly run thousands of Windows applications....

Category: Info | Date: 23rd August 2023
In the ever-evolving world of internet security, Google Chrome remains at the forefront of ensuring user safety while browsing the web. Recently, the Chrome development team has been working on a new feature that promises to provide enhanced protection by automatically detecting and removing....

Category: Info | Date: 23rd August 2023
Cryptocurrency, a digital or virtual form of currency, has revolutionized the way we think about money and finance. Since the inception of Bitcoin in 2009, cryptocurrencies have grown in popularity and have diversified into a vast ecosystem. In this article, we'll explore what....

Category: Info | Date: 23rd August 2023
In an age where our digital lives play an increasingly central role, the significance of securing our online presence cannot be overstated. Cyber threats are evolving rapidly, making robust antivirus software a necessity. As we step into 2023, it is crucial to equip ourselves with the best tools....

Category: Info | Date: 23rd August 2023
In an age where online privacy and security are of paramount importance, virtual private networks (VPNs) have become indispensable tools for safeguarding your internet connection. Among the many VPN protocols available, WireGuard has gained popularity for its simplicity, speed, and security. In....

Category: Info | Date: 17th August 2023
In a significant technological move, the Indian Defence Ministry has set its sights on replacing the widely used Windows operating system with a homegrown alternative known as Maya OS. This bold step is part of India's larger strategy to enhance its cybersecurity, data sovereignty, and reduce....

Category: Info | Date: 17th August 2023
Installing software or updates on your Windows 11/10 system can occasionally lead to frustrating roadblocks, such as the "The Installer Has Insufficient Privileges" error. This error message indicates that the current user account doesn't possess the necessary permissions to carry out the....

Category: Info | Date: 17th August 2023
In an era where smartphones have become an extension of our lives, concerns about privacy, security, and data protection have taken center stage. Choosing the safest mobile operating system (OS) is a critical decision that impacts our digital lives. But which OS can genuinely claim the title of....

Category: Info | Date: 17th August 2023
Gaming enthusiasts often encounter technical challenges while immersing themselves in their favorite titles. One such issue that has plagued players is the "Remnant 2 Low-Level Fatal Error." This vexing error can disrupt gameplay and dampen the gaming experience. However, fear not, as this article....

Category: Info | Date: 12th August 2023
In an era where streaming has become a dominant form of entertainment, many users rely on Virtual Private Networks (VPNs) to access a wider range of content on platforms like Netflix. However, not all VPNs are created equal, and finding the right one that successfully bypasses Netflix's....

Category: Info | Date: 12th August 2023
As streaming services like Netflix offer a vast library of content, users often find themselves limited by geographical restrictions that prevent access to certain shows and movies. This is where a Virtual Private Network (VPN) comes into play. By employing a VPN, users can transcend these....

Category: Info | Date: 12th August 2023
In an increasingly digital world, online security remains a top priority for individuals and businesses alike. The evolving landscape of cyber threats necessitates proactive measures to safeguard sensitive information and ensure a secure browsing experience. Addressing this need, Fortect, a....

Category: Info | Date: 12th August 2023
In a world where digital privacy and security are of utmost importance, setting up a Virtual Private Network (VPN) on your devices has become a vital step to protect your online presence. Whether you're using a computer, smartphone, tablet, or even a smart TV, the process of configuring a VPN....

Category: Info | Date: 4th August 2023
Setting up your own Virtual Private Network (VPN) server can be a valuable solution for enhancing security and privacy while accessing the internet. By creating your VPN server, you gain full control over your data and browsing activities. This article will guide you through the steps required to....

Category: Info | Date: 4th August 2023
Windows 11, the latest operating system from Microsoft, brings numerous improvements and features to enhance user experience. As more users transition to this updated platform, it becomes crucial to prioritize security and privacy while using the internet. A Virtual Private Network (VPN) serves as....

Category: Info | Date: 2nd August 2023
In today's interconnected world, where data privacy and cybersecurity are paramount, Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding online activities. VPNs provide users with secure and private internet connections by encrypting their data and routing it through....

Category: Info | Date: 2nd August 2023
In today's digital age, smartphones have become an essential part of our lives, handling a wide range of personal and sensitive information. Unfortunately, these devices are also susceptible to hacking attempts, potentially compromising our privacy, security, and even financial well-being. It is....

Category: Info | Date: 2nd August 2023
In today's fast-paced digital world, a sluggish computer can be frustrating and impact productivity significantly. One of the core components responsible for a computer's speed is the Central Processing Unit (CPU). The CPU acts as the brain of your computer, executing instructions and processing....

Category: Info | Date: 2nd August 2023
In the realm of technology and internet connectivity, errors and issues are inevitable. The BT_Datachannel error is one such occurrence that has puzzled users and raised concerns about the stability of their network connections. This error message, encountered mainly by BitTorrent users, can....

Category: Info | Date: 2nd August 2023
In the ever-expanding digital landscape, where cyber threats lurk at every corner, having a robust antivirus solution is a critical aspect of safeguarding our devices and sensitive data. The search for the "best" antivirus software is a common quest among users seeking optimal cyber....

Category: Info | Date: 27th July 2023
In today's digital age, computer security is of utmost importance. Malware, short for malicious software, poses a constant threat to individuals and organizations alike. It can lead to data breaches, financial loss, and identity theft. Protecting your computer from malware is essential to....

Category: Info | Date: 25th July 2023
Losing important files can be a distressing experience for anyone. Whether it's due to accidental deletion, a system crash, formatting the wrong drive, or any other reason, the loss of valuable data can lead to frustration and panic. However, if you're using Windows 10, there is hope. The....

Category: Info | Date: 25th July 2023
MainSearchSignal is a browser extension that has gained popularity in the online community due to its promising features and supposed ability to enhance the browsing experience. However, like many browser extensions, users often have questions about its legitimacy, functionality, and potential....

Category: Info | Date: 16th July 2023
With the increasing reliance on smartphones and the sensitive data they contain, protecting your Android device from malware and other cyber threats has become essential. Android antivirus software plays a crucial role in safeguarding your personal information and ensuring the security of your....
Category: Info | Date: 16th July 2023
In today's digital landscape, protecting your devices and personal information from malicious threats is more important than ever. Antivirus software plays a critical role in defending against viruses, malware, and other online threats. While premium antivirus solutions offer comprehensive....

Category: Info | Date: 16th July 2023
In today's interconnected world, the threat of malware is an ever-present concern for individuals and businesses alike. Malware, short for malicious software, can wreak havoc on your digital environment, compromising sensitive data, disrupting operations, and causing financial losses. To combat....

Category: Info | Date: 16th July 2023
In today's fast-paced business landscape, having the right tools is crucial for success. However, acquiring top-notch business software can often come with a hefty price tag. Fortunately, the realm of free software has significantly evolved over the years, offering powerful solutions to help....
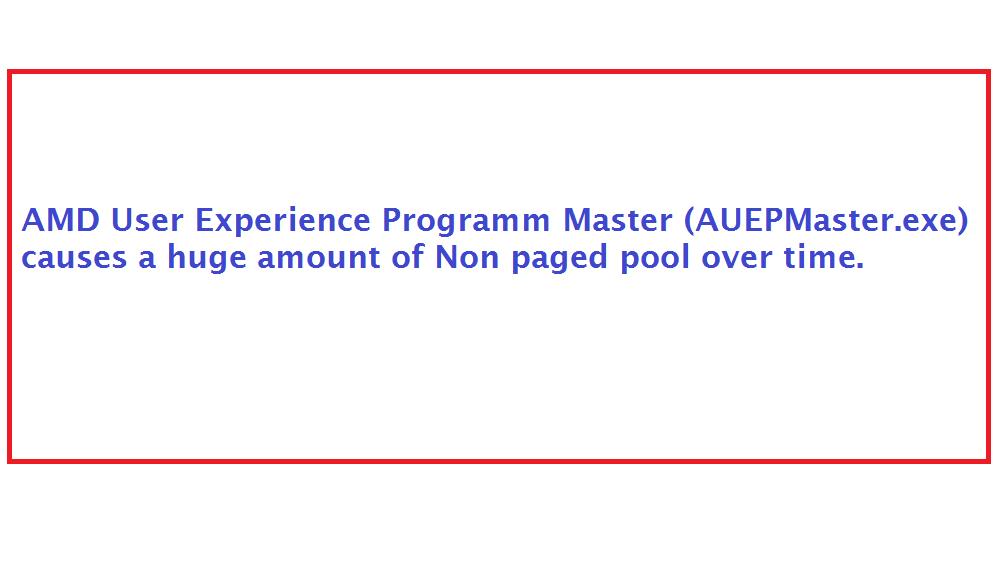
Category: Info | Date: 6th July 2023
If you're experiencing a high consumption of non-paged pool memory over time specifically related to AUEPMaster.exe, it could indicate a potential issue with the AMD User Experience Program Master software or a compatibility issue with your system. Here are some steps you can take to address the....

Category: Info | Date: 30th May 2023
UNIX is a popular and influential operating system that was developed in the 1960s and 1970s. It was originally designed by a group of researchers at Bell Labs, including Ken Thompson, Dennis Ritchie, and others. UNIX is known for its simplicity, elegance, and power, and it has had a significant....

Category: Info | Date: 27th May 2023
Linux and Windows are two different operating systems commonly used on personal computers and servers. Linux: Linux is an open-source operating system kernel that serves as the foundation for various Linux distributions (distros). Linux is known for its stability, security, and flexibility. It is....
Category: Info | Date: 26th May 2023
There are several types of operating systems, each designed for specific purposes and platforms. Here are some commonly used types of operating systems: Windows: Developed by Microsoft, Windows is one of the most popular operating systems for personal computers. Different versions of Windows,....

Category: Info | Date: 22nd May 2023
A mainframe computer is a powerful and high-performance computer system that is designed for large-scale computing tasks and data processing. It is known for its reliability, scalability, and ability to handle a vast amount of simultaneous transactions and users. Mainframes have been in use since....

Category: Info | Date: 22nd May 2023
An operating system (OS) is a software that manages computer hardware and software resources and provides essential services for computer programs. It acts as an intermediary between the computer hardware and the applications running on it. The primary purpose of an operating system is to provide....

Category: Info | Date: 17th May 2023
In the context of computer systems, the term "OS bootstrap" refers to the process of initializing and loading an operating system (OS) into memory when a computer is powered on or restarted. It is the first step in the startup sequence of a computer system. The OS bootstrap process typically....

Category: Info | Date: 17th May 2023
Bootstrap is a popular open-source front-end framework for building responsive and mobile-first websites and web applications. It was originally developed by Twitter and is now maintained by the Bootstrap community. The main goal of Bootstrap is to provide developers with a set of tools and....
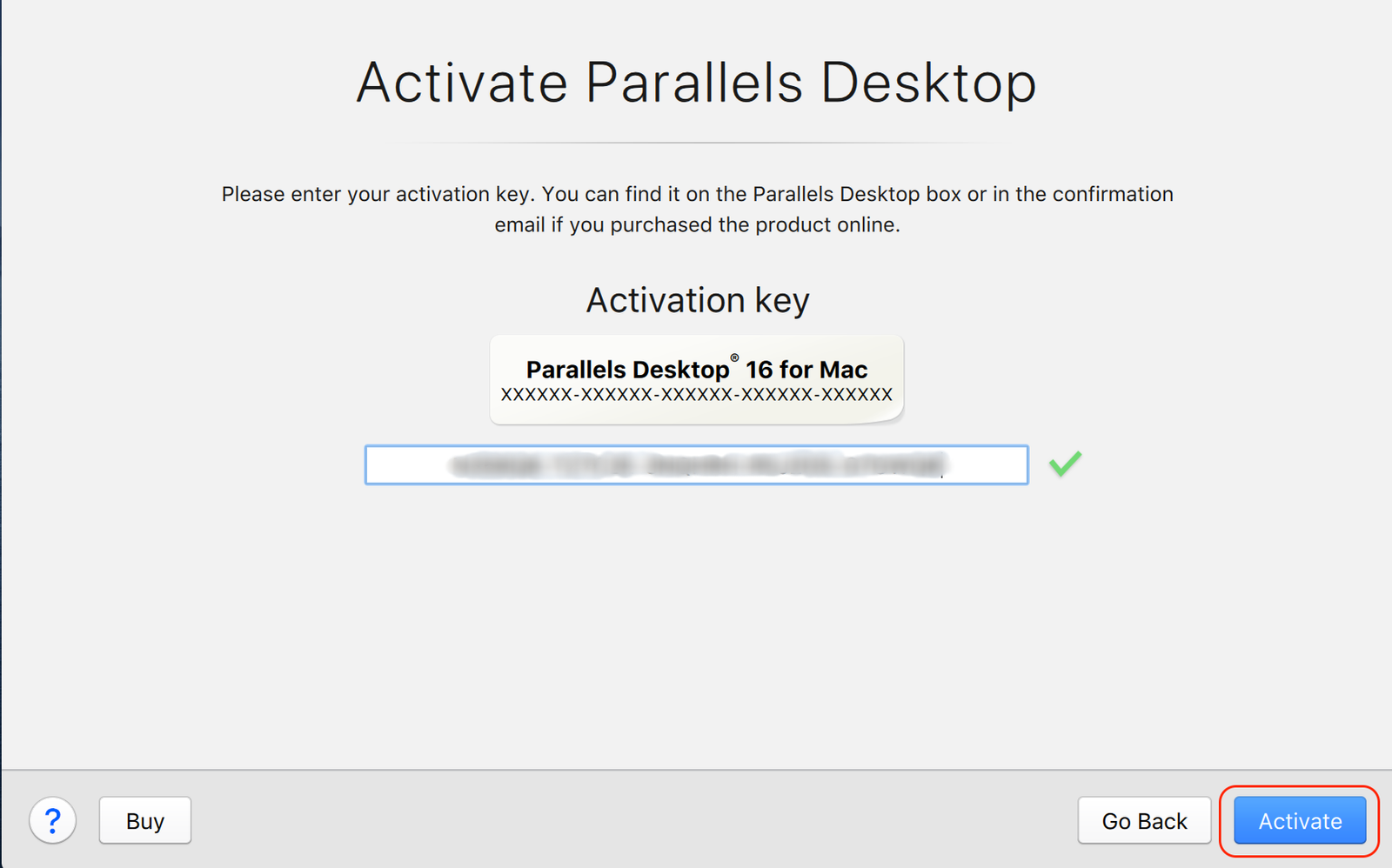
Category: Info | Date: 20th April 2023
Parallels is a best software publisher and provide the Free Products Keys for the Mac Software as well as the Windows Software too. However, Free Products Keys is an important trigger to switch to start the software while download and install on the computer system. There is number software to....

Category: Info | Date: 19th April 2023
Computer security services refer to a broad range of measures and technologies that are designed to protect computer systems and networks from unauthorized access, theft, damage, or disruption. These services aim to maintain the confidentiality, integrity, and availability of digital information by....

Category: Info | Date: 17th April 2023
The internet browser is an important web application that is compulsory component in the daily life. While you can search any things, then you go to Google Chrome web browser whether it is download as well as an install in the smartphone, laptop and computer system. Reset Chrome Browser For....
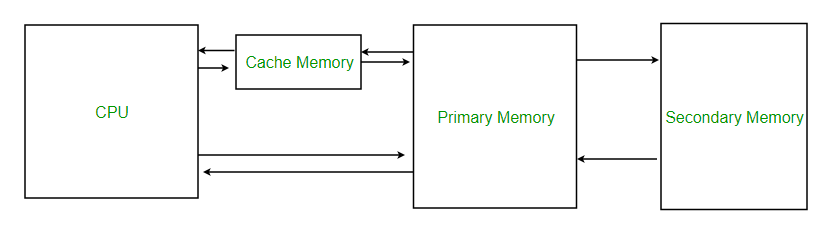
Category: Info | Date: 27th February 2023
Cache or cache memory refers to a type of high-speed memory used by computers and other electronic devices to temporarily store frequently accessed data or instructions. When a computer performs a task, it typically accesses data and instructions from its main memory (RAM). However, accessing data....
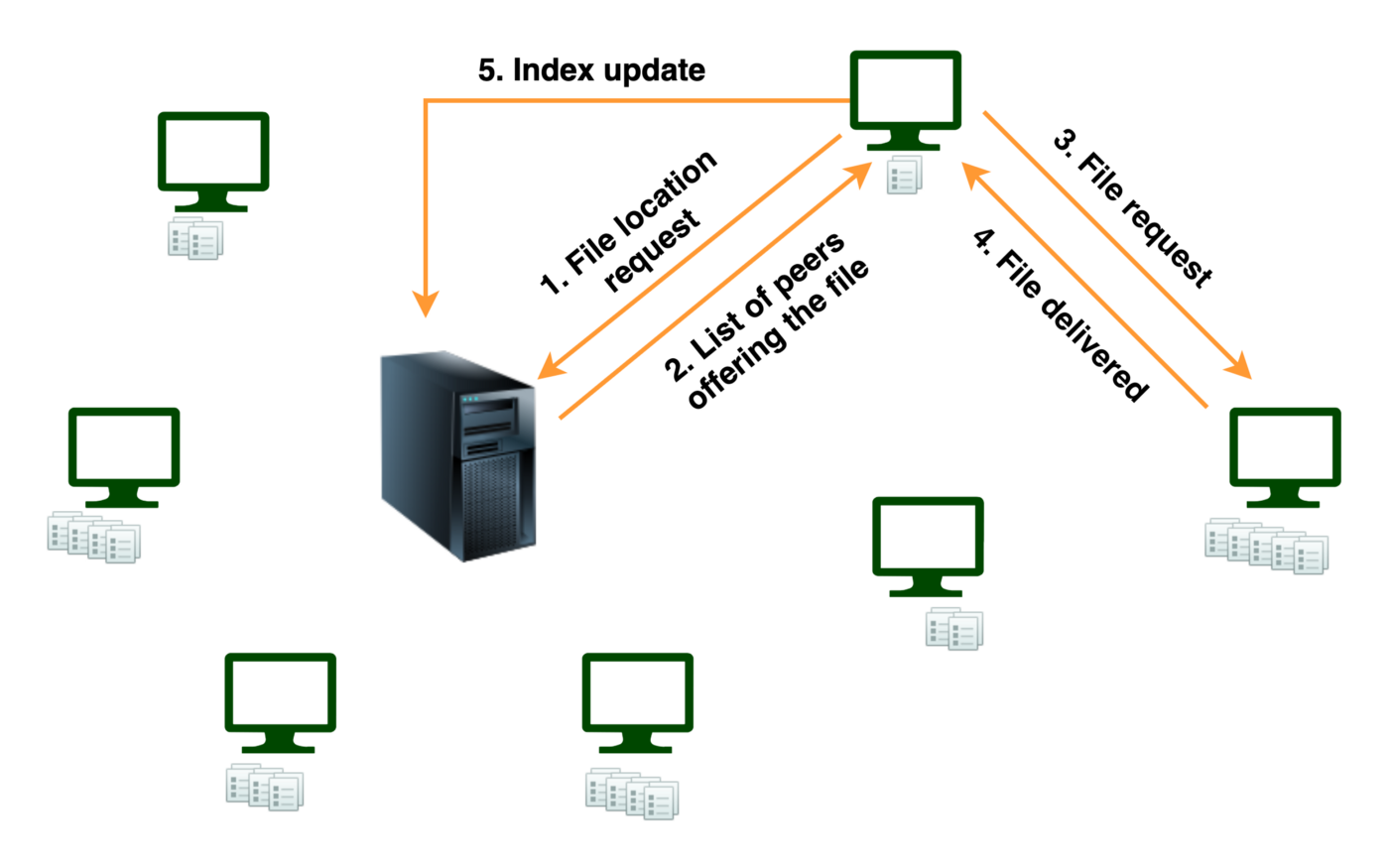
Category: Info | Date: 15th February 2023
Peer-to-peer (P2P) file sharing is a method of distributing digital media and other files over the Internet. In a P2P network, each user's computer acts as both a client and a server, allowing users to share files directly with each other without the need for a central server. In a P2P network,....

Category: Info | Date: 15th February 2023
BHO stands for "Browser Helper Object". It is a type of plug-in or extension that can be installed in web browsers, such as Internet Explorer, to add additional functionality or modify the behavior of the browser. BHOs were first introduced with Internet Explorer 4, and they are implemented as....
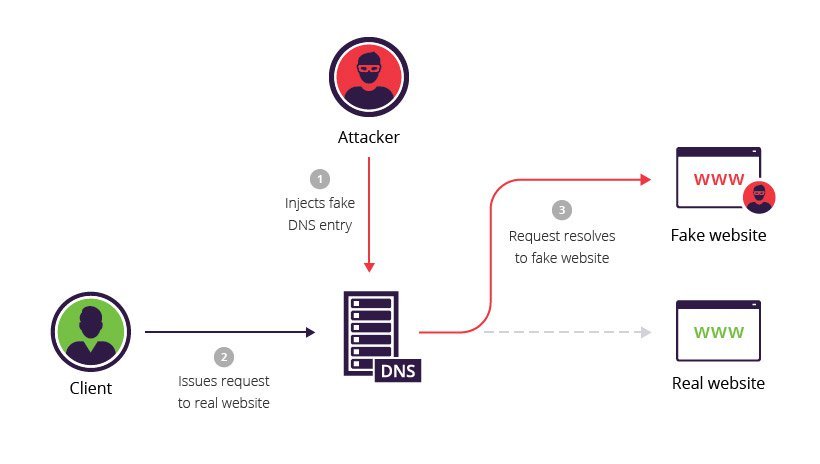
Category: Info | Date: 15th February 2023
DNS security refers to the measures and techniques used to protect the Domain Name System (DNS) from attacks and vulnerabilities. The DNS is a critical component of the Internet infrastructure, and any compromise to its security can have far-reaching consequences. There are several types of DNS....

Category: Info | Date: 15th February 2023
DNS stands for Domain Name System. It is a system used to translate human-readable domain names, such as "google.com" or "facebook.com", into IP addresses that can be understood by computers. When you enter a domain name into a web browser, the browser sends a request to a DNS server, which looks....

Category: Info | Date: 7th February 2023
Decryption is the process of transforming encrypted data back into its original, unencrypted form. The decryption process is the reverse of the encryption process and requires access to the secret key used to encrypt the data. In a symmetric encryption system, the same key is used for both....
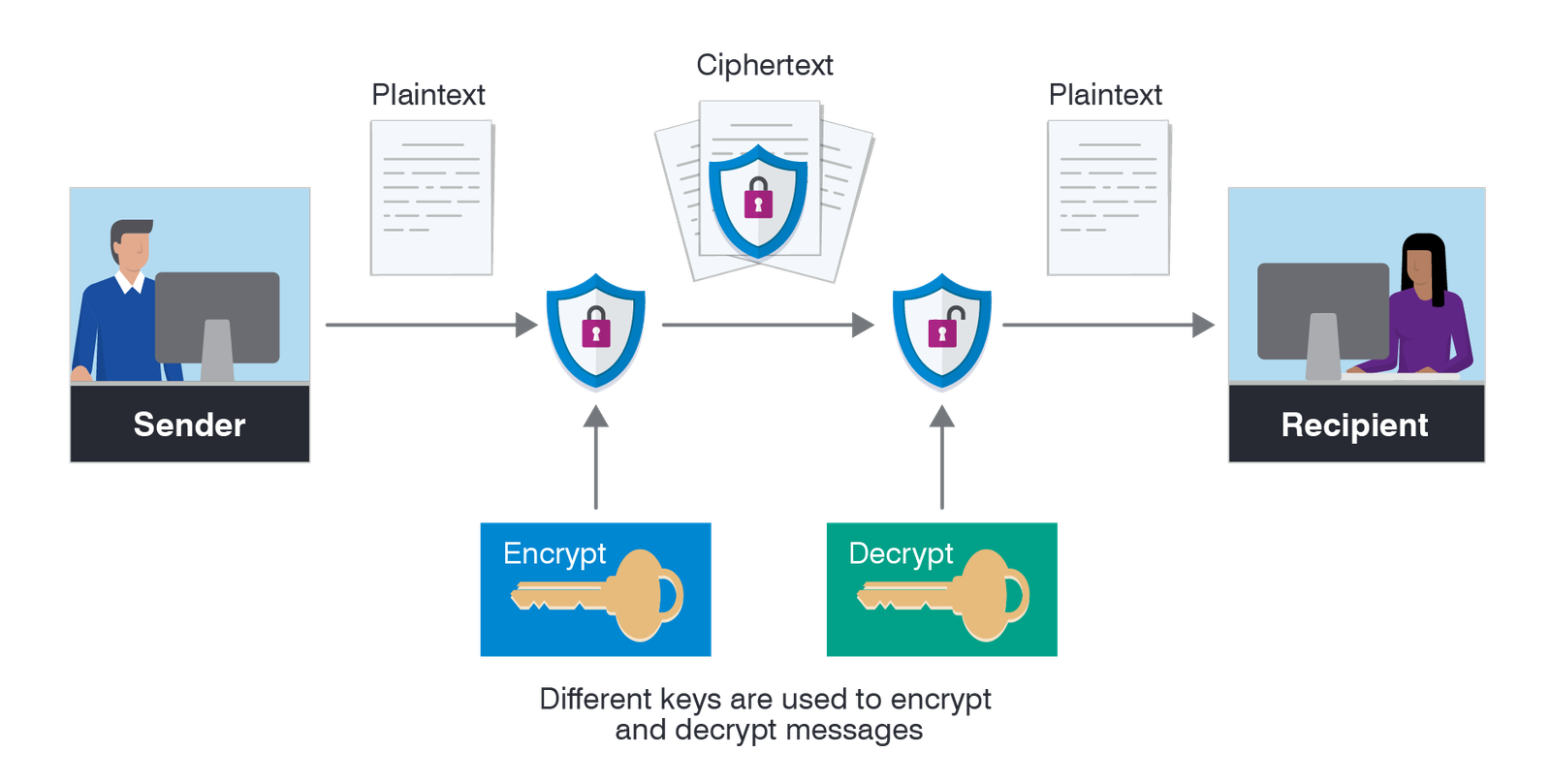
Category: Info | Date: 7th February 2023
Encryption is a process of converting plaintext into an unreadable ciphertext to protect the confidentiality and integrity of data during transmission or storage. The process of encryption uses an algorithm, known as a cipher, to perform the transformation, and a secret key that is used to encrypt....
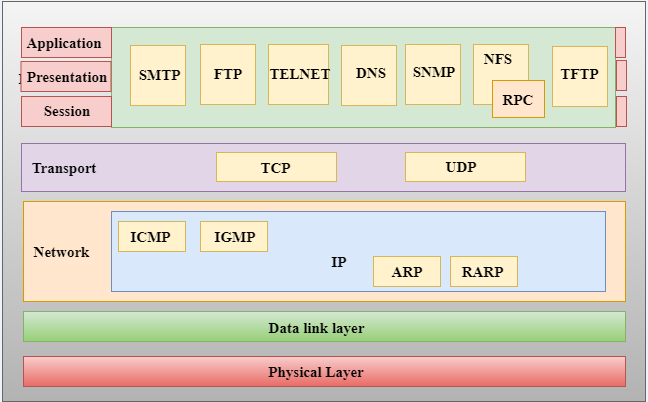
Category: Info | Date: 7th February 2023
TCP/IP (Transmission Control Protocol/Internet Protocol) is a set of communication protocols used for transmitting data over the internet and other computer networks. It is the foundation of the internet and the most widely used network protocol in the world. The TCP/IP protocol suite consists of....
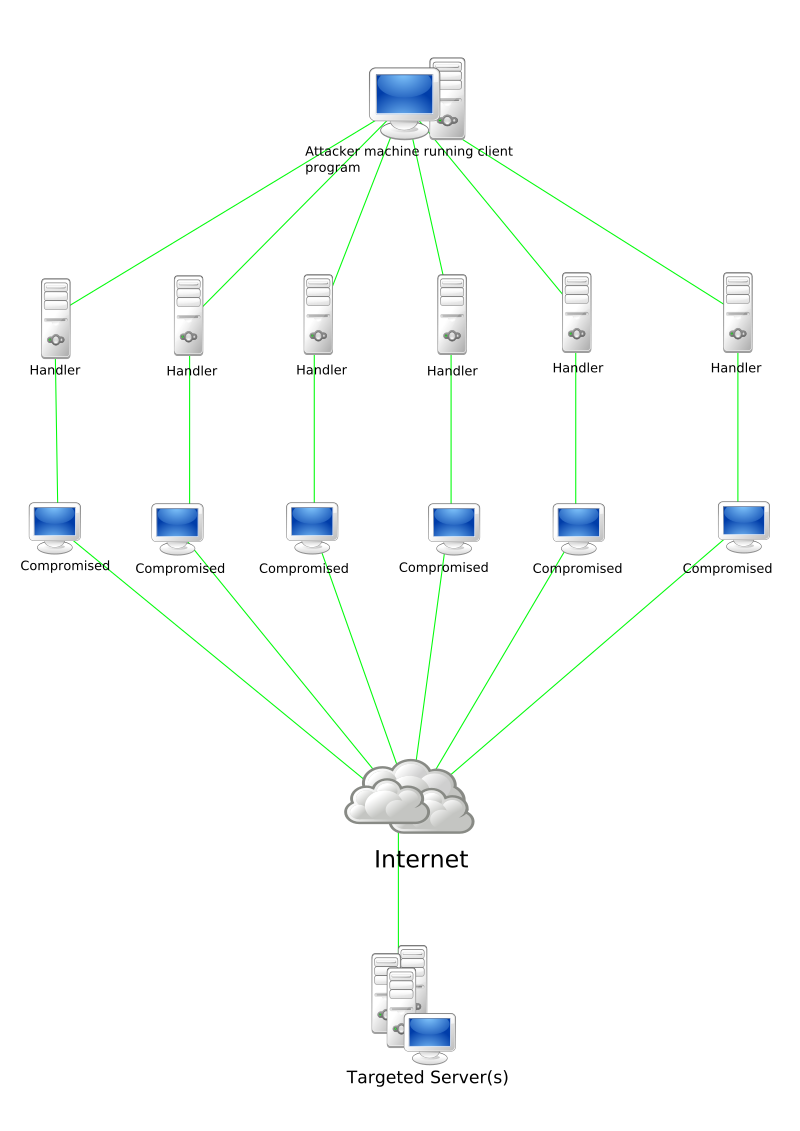
Category: Info | Date: 7th February 2023
DDoS stands for Distributed Denial of Service, which is a type of cyber attack where multiple compromised computers are used to flood a target system with traffic, overwhelming it and making it unavailable to users. The goal of a DDoS attack is to disrupt the normal functioning of a website,....

Category: Info | Date: 6th February 2023
A protocol is a set of rules and standards that define how data is transmitted between devices and systems over a network. The purpose of these protocols is to ensure the reliable and efficient communication of data between different devices and systems. Examples of commonly used protocols include....

Category: Info | Date: 6th February 2023
Phishing is a form of cyber attack that involves tricking individuals into providing sensitive information such as passwords, credit card numbers, and other personal details. This is typically done through a phishing email, which is an email that appears to come from a trustworthy source, such as a....
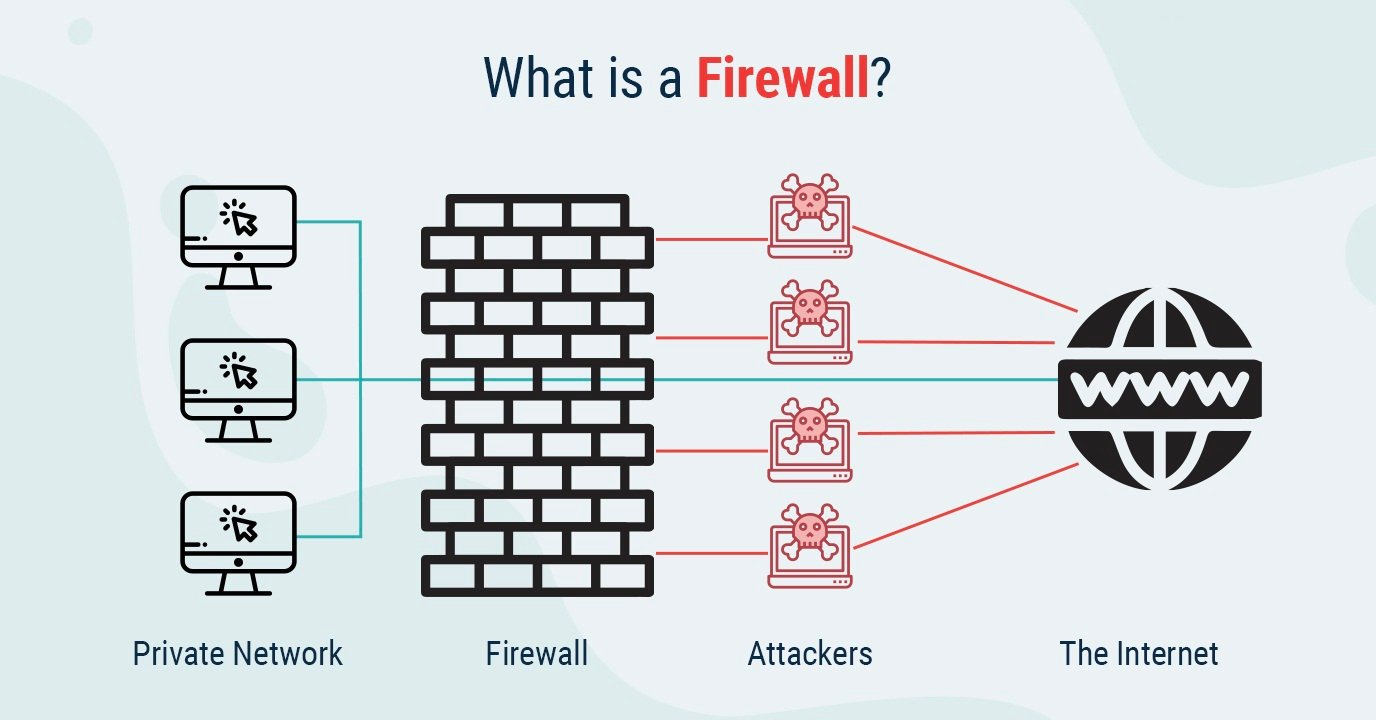
Category: Info | Date: 6th February 2023
A firewall is a security system designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. It is a network security device that sits between a private network and the internet, and acts as a barrier to prevent unauthorized access to the private....

Category: Info | Date: 6th February 2023
Spam is unwanted or unsolicited email. It is typically sent in bulk to a large number of email addresses, often without the recipient's permission. Spam mail often contains advertisements for products or services, but can also contain phishing scams, malware, or other harmful content. Spam mail can....

Category: Info | Date: 6th February 2023
A computer network is a collection of computing devices connected together through communication channels to facilitate communication and resource-sharing among devices. A computer network allows devices to exchange data, share resources, and communicate with one another. Computer networks can be....
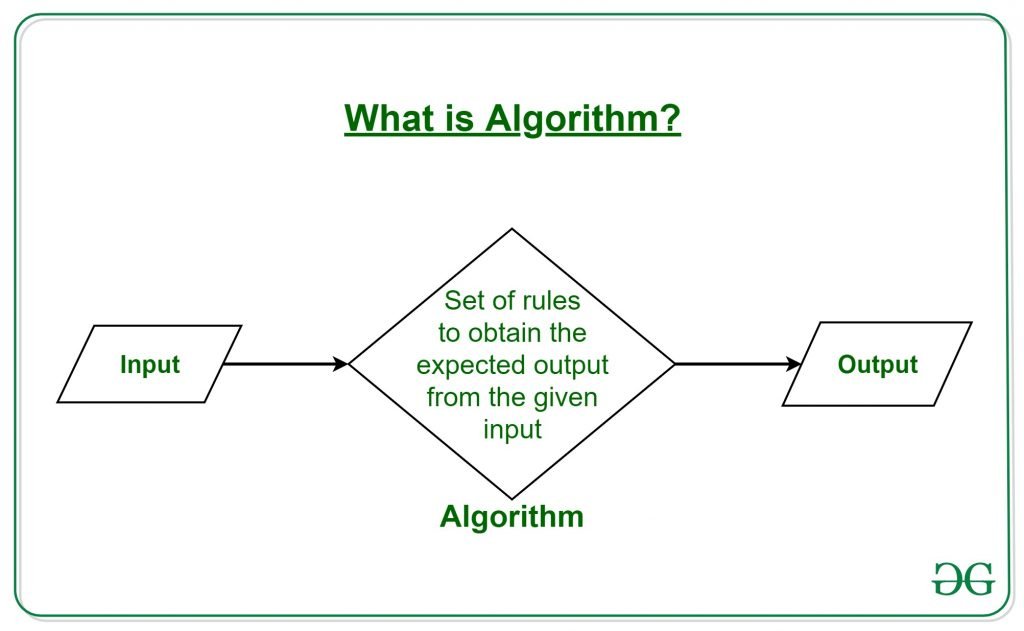
Category: Info | Date: 6th February 2023
An algorithm is a set of well-defined instructions or steps that specify how to perform a task or solve a specific problem. It is a step-by-step procedure for solving a problem or accomplishing a specific task, and is typically expressed in a programming language or mathematical notation. An....
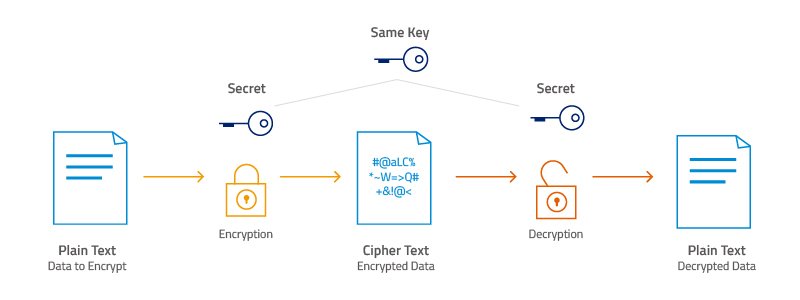
Category: Info | Date: 6th February 2023
AES-256 is a symmetric encryption algorithm that is widely used for secure data encryption. AES stands for Advanced Encryption Standard and it was developed by the U.S. National Institute of Standards and Technology (NIST) as a replacement for the previously used Data Encryption Standard (DES). In....
Category: Info | Date: 19th January 2023
VPN (a virtual private network) is a service that encrypts your internet traffic on unsecured networks to protect your online identity, hide your IP address, and shield your online data from third parties. VPNs use real-time encryption and send user internet data through a secure VPN tunnel to....

Category: Info | Date: 9th January 2023
Date Recovery Software is very popular among computer users. Date Recovery Software has been developed by the lot of manufacturer to retrieve the lost files and data in the hidden place in the computer system. Date Recovery Software was initially active the application. Date Recovery Software is....
Category: Info | Date: 5th January 2023
Run more than 200,000 Windows application on a Mac, including Microsoft Office for Windows. Download as well as an Install Windows Operating System on your Intel or Apple M-series Mac computer. Seamlessly copy and paste text or drag-and-drop files between Mac and Windows. Develop and test across....

Category: Info | Date: 4th January 2023
The cyber threat landscape is evolving all the time and attack patterns are becoming even more sophisticated. It’s not just organizations that are being targeted by cybercriminals – individuals and their home PCs are on the radar as well. It’s time to move from legacy antivirus....

Category: Info | Date: 4th January 2023
Cylance smart antivirus is a smart application to attach with latest technology AI. Cylance Smart AV is a next generation antivirus software to protect the device from the malware, adware, browser hijacker, ransomware, trojan virus and more. Cylance Smart Antivirus is the first next-generation....

Category: Info | Date: 13th June 2022
When Running A Development Project To Create A Digital Product, Companies Need To Have A Management System To Ensure Deadlines Are Met And Progress Is On Track. However, The Development Team Usually Doesn’t Have Good Communication With The Operations Team. This Delays The Whole Process Of....

Category: Info | Date: 13th June 2022
Data Science Is Another Tech Skill That Covers A Lot Of Ground In Several Industries. This Profession Helps Companies Solve Problems Through Data Analysis. Data Scientists’ Work Is To Collect Data That Will Be Filtered And Come Up With Meaningful Insights That Could Help Prove A....

Category: Info | Date: 13th June 2022
Machine Learning Refers To A Computerit’s Ability To Learn Actions Without The Need Of Human Command. Machine Learning Engineers Are The Professionals That Make Sure This Process Is Done Properly. To Put It In Simple Words, It’s Like Training A Child To Learn A Lesson. You’ll....

Category: Info | Date: 13th June 2022
Software Development, Or software Engineering, Refers To The Discipline That Allows You To Create Web And Mobile Software, Including Apps. Software Developers Are Vital To A Software Company. To Others, Software Development Allows Businesses To Automate Processes And Create Digital Products....

Category: Info | Date: 13th June 2022
There’s An Increased Demand For Tech Workers In Every Industry, Not Just Technology Development Companies. In Fact, Companies That Don’t Work With Tech Talents Are At Risk Of Falling Behind Industry Trends. However, The Supply Of Tech Professionals In Certain Sectors Is Lower Than....
Category: Info | Date: 3rd February 2022
404 Error Or "page Not Found" Error In The Website Will Happen When Page Does Not Run In The Web Server. 404 Error Is Pertaining With Hyper Text Transfer Protocol Standard Response Code That Sign The Server Was Not Able To Detect What Was Requested By The Client. Whenever Website Page Is Not....