 Blog's Page
Blog's Page
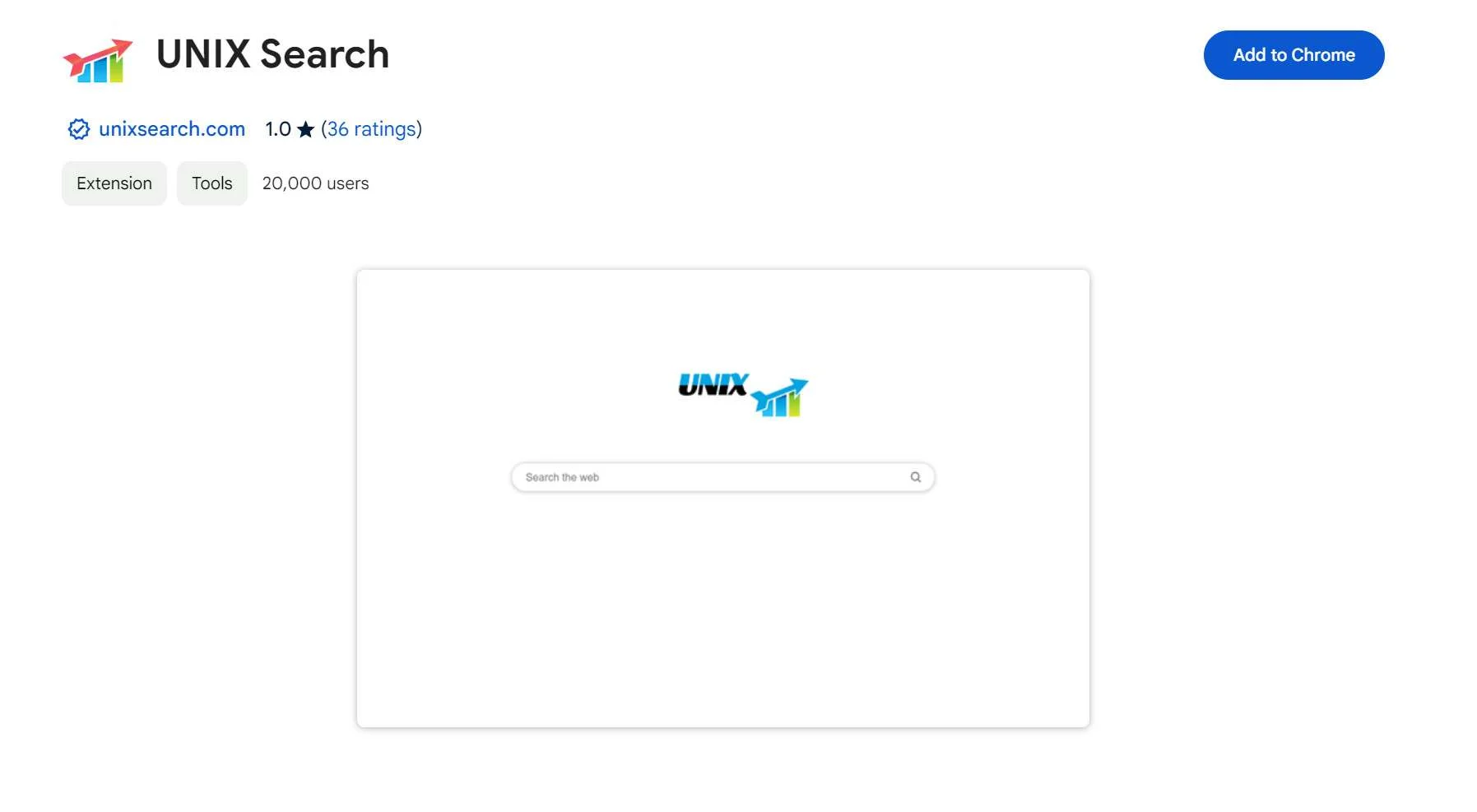
Following An In-depth Analysis Of The UNIX Search Application, Cybersecurity Researchers Have Categorized It As A browser Hijacker. The Application Promotes A Dubious Search Engine, Unixsearch.com, And Asserts Control Over Users' Browsers By Altering Their Settings, Granting Access To And Manipulation Of Diverse Data Types.
Consequently, Users Are Strongly Cautioned Against Utilizing The UNIX Search Application Due To The Inherent Risks It Poses, Including Potential Breaches Of Privacy And Security.
The UNIX Search Application Takes Command Of Web Browsers, Compelling Users To Utilize Unixsearch.com As Their Primary Search Tool. By Altering Default Settings Such As The Search Engine, Homepage, And New Tab Page, It Directs Users Towards Unixsearch.com. Users Are Advised To Avoid Such Dubious Search Engines Endorsed By Browser Hijackers.
These Search Engines Often Lack Credibility And Reliability, Prioritizing Ads And Sponsored Content Over Accurate And Relevant Search Results. Consequently, Users Face The Risk Of Being Directed To Unsafe Or Deceptive Websites, Exposing Them To Potential Security Threats Like malware Or phishing.
Moreover, Reliance On Such Search Engines May Degrade The Browsing Experience With Intrusive Ads Or Unwanted Website Redirects. Additionally, These Search Engines Often Gather User Information For Potential Misuse In Marketing Or Other Purposes.
Furthermore, The UNIX Search Can Block Content On Web Pages, Interfering With Users' Online Access. It May Also Exert Additional Control Over Browsing Experiences, Potentially Restricting Access To Specific Websites Or Information.
It's Important To Note That This Extension Exploits The 'Managed By Your Organization' Feature In Chrome Browsers. While Typically Used For Managing Policies In Organizational Settings, This Feature Can Be Abused By Browser Hijackers To Modify Settings, Inject Extensions, Or Control Website Access. Users Should Remain Vigilant And Consider The Risks Associated With Using UNIX Search.
Potentially Unwanted Programs (PUPs) And Browser Hijackers Often Employ Dubious Distribution Tactics To Infiltrate Users' Systems, Relying On Deception Or Coercion To Unintentionally Install These Unwanted Software Entities.
Here Are Common Methods Utilized By PUPs And Browser Hijackers:
Bundled Software: PUPs Are Frequently Bundled With Seemingly Legitimate Software During Installation. Users May Overlook Or Hastily Click Through Installation Prompts, Inadvertently Agreeing To Install Additional Programs Bundled With The Desired Software. This Method Capitalizes On Users' Inattentiveness During The Installation Process.
Deceptive Advertising: PUPs And Browser Hijackers May Be Promoted Through Deceptive Advertisements Encouraging Users To Click On Misleading Links Or Download Seemingly Harmless Applications. These Ads Can Appear On Dubious Websites, Pop-up Windows, Or Masquerade As Legitimate Software Updates.
Freeware And Shareware Downloads: PUPs Often Hitch A Ride On Free Or Shareware Applications Downloaded From The Internet. Users Might Unknowingly Consent To Install Additional Software Components During The Installation Of The Primary Application.
Fake Software Updates: Browser Hijackers May Disguise Themselves As Fake Software Updates, Exploiting Users' Trust In Legitimate Update Notifications. Clicking On These Deceptive Update Prompts Can Lead To Unwittingly Downloading And Installing The Unwanted Browser Hijacker.
Phishing Emails And Social Engineering: PUPs And Browser Hijackers May Be Distributed Via Phishing Emails Or Social Engineering Tactics. Users May Receive Seemingly Authentic Emails Containing Malicious Links Or Attachments, Tricking Them Into Downloading And Installing The Unwanted Software.
To Mitigate The Risk Of Falling Victim To These Shady Distribution Practices, Users Should Exercise Caution When Downloading And Installing Software, Especially From Unfamiliar Sources.
It's Vital To Carefully Read Installation Prompts, Avoid Clicking On Suspicious Links Or Ads, Keep Software Updated, And Use Reputable Security Software To Detect And Remove Potential Threats.
Additionally, Staying Informed About Current Cybersecurity Threats And Practicing Safe Browsing Habits Can Help Prevent The Inadvertent Installation Of PUPs And Browser Hijackers.
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:




If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
UNIX Search Browser Extension, Remove UNIX Search Browser Extension, Uninstall UNIX Search Browser Extension, Delete UNIX Search Browser Extension