 Blog's Page
Blog's Page

Locky Is A Notorious ransomware Strain That Emerged In Early 2016. It Gained Widespread Attention Due To Its Large-scale And Aggressive Distribution Methods. Like Other Ransomware, Locky Encrypts Files On The Victim's Computer And Demands A Ransom Payment In Bitcoin Or Other Cryptocurrencies To Decrypt The Files And Restore Access.
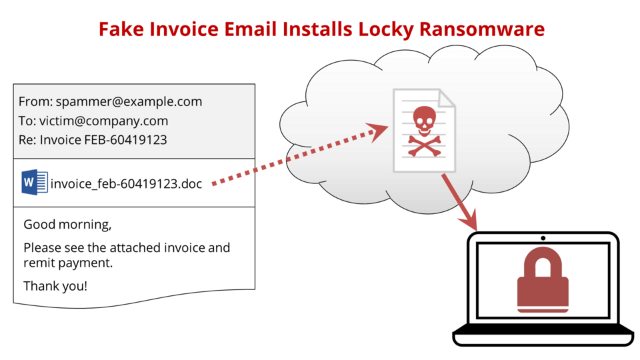
Here Are Key Characteristics Of Locky Ransomware:
File Encryption: Locky Encrypts A Wide Range Of Files On The Infected Computer Using Strong Encryption Algorithms. Once Encrypted, The Victim Cannot Access Their Files Without The Decryption Key, Which The Attackers Claim To Provide Upon Ransom Payment.
Ransom Note: After Encrypting The Files, Locky Displays A Ransom Note On The Victim's Desktop. This Note Contains Instructions On How To Pay The Ransom, Usually In The Form Of A Pop-up Message Or Text Files Dropped In Each Folder Containing Encrypted Files.
Payment In Cryptocurrency: The Ransom Demanded By Locky Is Typically In Bitcoin Or Other Cryptocurrencies, Making It Difficult To Trace The Transactions Back To The Attackers.
Distribution Methods: Locky Is Commonly Spread Through Malicious Email Attachments, Especially In The Form Of Word Or Excel Documents With Malicious Macros. These Attachments Often Contain Social Engineering Tactics To Convince Users To Enable Macros, Which Then Download And Execute The Ransomware.
Evolution And Variants: Over Time, Locky Has Evolved Into Different Variants, Each With Its Unique Characteristics And Distribution Methods. Some Variants Use JavaScript Files Attached To Emails, While Others Use Compromised Websites To Deliver The Malicious Payload.
Volume Of Attacks: Locky Has Been Responsible For A Significant Number Of Ransomware Attacks Worldwide, Targeting Individuals, Businesses, And Even Government Organizations.
As With All Ransomware, Prevention Is Key. Regularly Updating Software, Being Cautious With Email Attachments And Links, Using Reputable Antivirus And Anti-malware Solutions, And Maintaining Up-to-date Backups Are Essential Practices To Protect Against Locky And Other Ransomware Threats.
Locky Ransomware Infection Exhibits Several Distinctive Symptoms On Affected Computer Systems:
File Encryption: Locky Encrypts A Wide Variety Of Files On The Victim's Computer, Including Documents, Images, Videos, And More. Encrypted Files Often Have Their File Extensions Changed Or Have A Specific Extension Added To Indicate They Have Been Compromised.
Ransom Note: After Encrypting The Files, Locky Typically Displays A Ransom Note On The Victim's Desktop. This Note Contains Instructions On How To Pay The Ransom To Decrypt The Files. The Ransom Note May Appear As A Pop-up Window Or As Text Files Dropped In Each Folder Containing Encrypted Files.
Changed File Extensions: Encrypted Files Often Have Their Extensions Changed To A Random Combination Of Letters And Numbers, Making Them Unrecognizable And Inaccessible.
Desktop Wallpaper Changes: Locky May Change The Victim's Desktop Wallpaper To Display The Ransom Note Or A Warning Message, Indicating That The Files Have Been Encrypted And Providing Instructions On How To Pay The Ransom.
Inability To Open Files: Encrypted Files Cannot Be Opened Or Accessed Without The Decryption Key. Attempts To Open These Files Result In Error Messages Or Corrupted File Notifications.
Ransom Payment Instructions: The Ransom Note Contains Detailed Instructions On How To Make The Payment In Bitcoin Or Another Cryptocurrency. It Includes Information On Where To Send The Payment And How To Obtain The Decryption Key.
Countdown Timer: Some Variants Of Locky Display A Countdown Timer, Indicating The Time Remaining Before The Ransom Amount Increases Or The Files Are Permanently Deleted.
Access Denied Messages: Victims Might Receive "access Denied" Messages When Attempting To Open Encrypted Files, Indicating That The Files Are No Longer Accessible.
If You Suspect Your Computer Is Infected With Locky Ransomware, It Is Essential To Disconnect From The Network Immediately, Seek Professional Assistance, And Avoid Paying The Ransom, As It Does Not Guarantee The Recovery Of Your Files And Encourages Cybercriminals To Continue Their Malicious Activities.
Locky Ransomware Typically Infects Computer Systems Through Malicious Email Attachments, Exploiting Vulnerabilities In Software, Or Using Malicious Scripts On Compromised Websites.
Here's How Locky Can Reside In A Computer System:
Malicious Email Attachments: Locky Often Spreads Through Phishing Emails That Contain Malicious Attachments, Such As Word Documents Or ZIP Files. These Attachments Are Designed To Trick Users Into Enabling Macros, Which Then Download And Execute The Ransomware Payload.
Malicious Links: Phishing Emails May Also Contain Links To Compromised Or Malicious Websites. Clicking On These Links Can Lead To Drive-by Downloads, Where Locky Is Automatically Downloaded And Executed On The Victim's System Without Their Knowledge Or Consent.
Exploiting Software Vulnerabilities: Locky Can Exploit Vulnerabilities In Outdated Or Unpatched Software. This Includes Vulnerabilities In Operating Systems, Browsers, Or Plugins. Once A System Is Compromised, Locky Can Be Downloaded And Executed Through These Security Holes.
Compromised Websites: Locky Can Be Distributed Through Compromised Websites That Host Malicious Scripts Or Exploit Kits. Visitors To These Websites May Unknowingly Download The Ransomware While Browsing.
Network Propagation: Once Inside A Network, Locky Can Spread To Other Computers And Servers. It Can Use Common Network Protocols And Brute-force Attacks To Gain Unauthorized Access To Other Devices On The Same Network, Encrypting Files On Shared Drives And Network Resources.
Malicious Advertisements (Malvertising): Cybercriminals May Use Malicious Advertisements Displayed On Legitimate Websites To Distribute Locky. Clicking On These Ads Can Lead To The Download And Execution Of The Ransomware.
Social Engineering: Attackers May Use Social Engineering Tactics, Such As Impersonating Trusted Entities Or Using Enticing Messages, To Trick Users Into Downloading And Executing Malicious Files Or Clicking On Malicious Links, Leading To Locky Infections.
To Protect Your Computer System From Locky Ransomware And Similar Threats, Practice Caution When Opening Email Attachments, Avoid Clicking On Suspicious Links, Keep Your Software Up-to-date With The Latest Security Patches, Use Reliable Antivirus Software, And Implement Email Filtering Solutions To Detect And Block Phishing Emails Containing Malicious Content.
Regular Security Awareness Training For Users Is Also Essential To Recognize And Avoid Social Engineering Attempts.
To Prevent Your Computer System From Locky Ransomware And Similar Threats, Follow These Essential Prevention Measures:
Keep Software Updated: Regularly Update Your Operating System, Software Applications, And Security Software. Enable Automatic Updates Whenever Possible To Ensure You Receive The Latest Security Patches.
Be Cautious With Email: Avoid Opening Email Attachments Or Clicking On Links From Unknown Or Suspicious Senders. Be Particularly Vigilant With Emails That Appear Unexpected, Contain Attachments, Or Have A Sense Of Urgency.
Enable Email Filtering: Use Email Filtering Solutions To Detect And Block Phishing Emails Containing Malicious Attachments Or Links. Effective Filtering Can Prevent Many Ransomware-laden Emails From Reaching Your Inbox.
Disable Macros: In Microsoft Office Applications, Disable Macros By Default. Macros Are Commonly Used By Ransomware To Deliver Their Payloads. Only Enable Macros In Documents From Trusted Sources And Known Senders When Necessary.
Backup Regularly: Create Regular Backups Of Your Important Files To An External, Offline Storage Device Or A Secure Cloud Service. Automated Backups Ensure You Can Restore Your Data Without Paying A Ransom If You Fall Victim To An Attack.
Use Reputable Security Software: Install Reputable Antivirus And Anti-malware Software. These Programs Can Detect And Block Known Ransomware Threats, Including Locky.
Network Segmentation: Divide Your Network Into Segments To Restrict The Spread Of Ransomware. Limit User Access Rights And Only Provide Necessary Privileges To Prevent Lateral Movement Within The Network.
Strong Passwords: Enforce The Use Of Strong, Complex Passwords For All Accounts And Systems. Implement Multi-factor Authentication For An Additional Layer Of Security.
Regular Security Audits: Conduct Periodic Security Audits Of Your Systems And Networks. Identify And Address Vulnerabilities Proactively To Prevent Exploitation By Ransomware Threats.
By Following These Preventive Measures And Promoting A Security-conscious Environment, You Can Significantly Reduce The Risk Of Falling Victim To Locky Ransomware And Other Similar Cyber Threats.
1. Award-winning Security
The Same Malware That Attacks Fortune 500 Companies Attacks Private Users, Too. Sophos Home Uses The Same Award-winning Security Features That Keep Those Companies Safe.
New Features Of The Sophos Home
You Have Been Infected. Well, Not You, But Your Computer Has. It’s Slow. You Need A No-nonsense Malware Cleaner To Get Your Computer Back Up To Speed. HitmanPro Is The Malware Remover Of Choice For Tens Of Millions Of People.
It’s Really Small
You Can Download HitmanPro In Two Seconds (unless You Still Have Dial-up Internet). It’s Only 10MB. Plus, You Do Not Have To Install It – Just Run It After It’s Downloaded.
It Scans For Bad Behavior
A Standard Antivirus Program Misses Stuff. It’s Focused On Finding Malware Signatures That Virus Firms Have Identified As Malicious. But What About New, Zero-day Threats That Have Not Been Researched? That’s Why HitmanPro Looks At Behaviors When Scanning For Trojans And Other Malware. Bad Behavior Is Caught, With Or Without A Malware Signature.
It Uses Multiple Experts
Two Heads Are Better Than One. So We Have Four. HitmanPro Leverages Malware Databases From Four Security Labs, Including SophosLabs, To Be Incredibly Thorough When Scanning For And Cleaning Up Spyware And Malware. More Research Means More Powerful Cleaning.
It Cleans Up After Itself
Malware Piggybacks On Various Programs To Gain Access To Your Computer. HitmanPro Removes That Malware – And It Does Not Stop There. Damaged Windows Resources Are Brought Back To Their Safe, Original Versions.
It Goes Deep To Clean
Resilient Malware Can Also Affect Critical System Files And Boot Records To Manipulate The Windows Operating System And Installed Antivirus Software. This Is Even Before The Operating System Boots. HitmanPro Can Remove These Persistent Threats From Within The Running Operating System And Its Boot Records.
Cylance Smart Antivirus Is The First Next-generation Antivirus Available To Consumers And Provides Families With The Only Enterprise Class Security Software Designed For Personal Use. Using Artificial Intelligence, Cylance Smart Antivirus Eliminates The Need For Updates And Pop-ups While It Protects You And Your Loved Ones Against The Latest Cybersecurity Threats.
| Smart Antivirus For US | Smart Antivirus For UK |
| Smart Antivirus For Ireland | Smart Antivirus For Canada |
| Smart Antivirus For New Zealand | Smart Antivirus For Australia |
An Antivirus That Works Smarter, Not Harder, From BlackBerry. Lightweight, Non-intrusive Protection Powered By Artificial Intelligence.
Traditional Antivirus Can’t Keep Up
Traditional Antivirus Typically Uses A Signature Based Model, Which Is Reliant On Capturing New Viruses In The Wild And Creating A Master List Of Malware For Users To Download. This Makes It Especially Vulnerable To Zero-day Attacks And Modern Threats Which Can Alter Themselves Too Quickly For Signature Updates To Catch.
A Different Approach
Cylance Uses Cutting-edge Algorithms And Artificial Intelligence To Proactively Protect You, Preventing Threats Like Malware, Hackers, Viruses, Ransomware, And Malicious Websites. It Does This Whilst Being Lightweight And Easy To Use. Cylance’s AI Has Been Demonstrated As Effective Against Threats -- Even Without Updates -- Over 2 Years Into The Future.
Advanced AI Training
We Use Cloud-based Supercomputers And Millions Of Examples Of Malicious Programs To Train A Neural Net, A Kind Of Digital Brain, To Recognise Threats.
Download And Protect
When You Purchase Cylance, This Is What You Download Onto Your Computer - A Superlightweight ’brain’, Trained To Catch And Quarantine Viruses.
Detection In Milliseconds
Cylance Sits In The Background, Instantly Recognising Threats The Moment They Occur And Reacting In Milliseconds – Unlike Other Antivirus Software Which Must Constantly Scan For Threats.
Complete Protection
Our AI Quarantines Files It Identifies As Threats, Allowing You To Review Individual Threats On You And Your Family’s Computers.
Cutting Edge Protection Without The Bloat Of Traditional Antivirus
Cylance Sits In The Background, Instantly Recognising Threats The Moment They Occur And Reacting In Milliseconds - Unlike Other Antivirus Software Which Must Constantly Scan For Threats.
1. Stops Infections Before They Can Attack
Traditional Antivirus Waits For You To Be Infected Before It Can Act. Cylance Observes The Behaviour Of Programs In Real-time, Detecting Threats In Milliseconds - Before They Can Execute.
2. Protects Against Never-before Seen Malware
Proactive AI Provides Protection From All Types Of Malware - Existing Threats And Those Yet To Be Developed. Cylance Prevents Attacks Before They Happen Rather Than Relying On Other Users Becoming Infected To ’discover’ Threats.
3. Unobtrusive Protection
We Know You Just Want Your Antivirus To Keep Your Safe - Not Waste Your Time. That’s Why We Guarantee To Never Bother You With Unwanted Alerts Or Pop-up Ads. Promise.
4. Light On RAM And CPU
We’ve Done All The Computational Heavy Lifting In The Cloud. As A Result, Cylance Uses Much Less RAM And CPU Than Other AV Solutions - Making It Perfect For Gamers Or Alongside Other Intensive Processes. You Won’t Even Notice We’re There.
Cylance Protects Devices On All Major Platforms And With Remote Protection, Cloud-based Support, Simple Set-up, It’s Never Been Easier To Be The Expert.
Easy To Install And Use
It’s Easy To Get Started With Cylance. Simply Download And Install, And You Have The Power Of An AI Supercomputer On Your Device. The Intuitive Interface Allows You To Manage Devices Centrally, Modify Settings, And Check Which Files Cylance Has Quarantined.
Remote Management
Cloud Based Support And Remote Management And Protection Means No More Worried Calls From Mom. Remotely View The Quarantine List Of All Devices To Keep Your Family Secure And Take The Work Out Of Being The Expert.
Operating Systems:
Memory
Internet Browser Support:
Cylance Uses Artificial Intelligence To Deliver Prevention-first, Predictive Security Products And Specialized Security Services That Change How Organizations Approach Endpoint Security. Cylance’s Security Solutions Provide Full Spectrum Predictive Threat Prevention And Visibility Across The Enterprise, Combatting Threats Such As Malware, Ransomware, File Less Malware, Malicious Scripts, Weaponized Docs, And Other Attack Vectors.
| Smart Antivirus For US | Smart Antivirus For UK |
| Smart Antivirus For Ireland | Smart Antivirus For Canada |
| Smart Antivirus For New Zealand | Smart Antivirus For Australia |
With AI Based Malware Prevention, Application And Script Control, Memory Protection, Device Policy Enforcement, Root Cause Analysis, Threat Hunting, Automated Threat Detection And Response, Coupled With Expert Security Services, Cylance Can Protect Endpoints Without Increasing Staff Workload Or Costs.
The Essential PC & Internet Security Solution
1. Antivirus & Anti-Spyware Engine
Detects And Removes Viruses, Spyware, Trojan Horses, Worms, Bots And More. Independently Tested To Provide Superior Protection.
2. Advanced Real-Time Antivirus
Provides Access To The Up-to-date Database Of Antivirus Signatures To Protect Against Newly Emerging Threats. Real-Time Cloud Database Contains Up-to-date Reputation Of Files, Web Resources And Software Enhancing Traditional Antivirus + Firewall Protection
Checks Files Against Real-time Cloud Database To Ensure That Even The Latest Threats Are Not Missed.
Contains The Latest Antivirus Signatures, Web Resources And Software To Ensure Up-to-date Protection.
3. Two-way Firewall
Stops Internet Attacks At The Front Door And Even Catches Thieves On Their Way Out. Our Two-way Firewall Proactively Protects Against Inbound And Outbound Attacks While Making You Invisible To Hackers.
4. Advanced Firewall
No Product Is 100% Effective Against Viruses Or Spyware. ZoneAlarm’s Advanced Firewall Monitors Behaviors Within Your Computer To Spot And Stop Even The Most Sophisticated New Attacks That Bypass Traditional Antivirus And Security Suites.
5. Additional Layers
Multiple Layers Of Advanced Protection Provide Unsurpassed Security.
Anti-Phishing
Protects You Against Phishing Attacks.
Antivirus/Anti-Spyware Engine
Detects And Remove Viruses, Spyware, Trojan Horses, Worms, Bots And Rootkits.
Advanced Real-Time Antivirus
Enhances Protection By Checking Against An Always Up-to-date Cloud Database Of Antivirus Signatures.
Advanced Firewall
Monitors Programs For Suspicious Behavior Spotting And Stopping New Attacks That Bypass Traditional Anti-virus Protection.
Two-way Firewall
Makes Your PC Invisible To Hackers And Stops Spyware From Sending Your Data Out To The Internet.
Identity Protection
Helps To Prevent Identity Theft By Guarding Your Personal Data.
Browser Protection
Protects Your Computer From Web Threats Before They Reach Your Browser.
1. Anti-Phishing Add-on
Google® Chrome All Versions
2. Microsoft® Windows® 10
3. Microsoft® Windows 7 SP1 All Versions
4. Microsoft .NET Framework
Version 3.5 Or Later
Note: If A Supported Microsoft .NET Framework Is Not Installed, It Will Be Installed With ZoneAlarm

Secure Your Digital Life Completely. True Cybersecurity Needs To Be Proactive, Not Reactive.
Support
Special Features Of Heimdal Premium Security Home
ANTIVIRUS IS NOT ENOUGH IN TODAY'S EVER EVOLVING ONLINE THREATSCAPE
Heimdal Premium Security Home Is The Ultimate Cybersecurity Suite, Combining A True Proactive Threat Prevention Solution With A Next-gen Antivirus With Market Leading Detection Rates So You Can Enjoy The Internet Freely!
Secure Your Digital Life Completely
Next-gen Threat Prevention Based On Machine Learning Meets A Powerful Antivirus With Market-leading Detection, So Your Online Security Is Flawless
Discover Actual Security In An Ever-changing Threat Landscape.
Heimdal™ Premium Security Home Brings The Unique Threat Prevention Layer Of Heimdal™ Threat Prevention Home On Top Of A Flawless, Market-leading Detection Heimdal™ Next-Gen Antivirus Home Antivirus To Stop Ransomware, Data Leakage, Viruses, APTs, Exploits & Other Advanced Online Threats.
Enjoy A Next Gen Multi-layered Security Suite.
Heimdal™ Premium Security Home Prevents Unknown Threats And Stops The Known Attacks. Browse Online Without The Fear Of Ransomware, Cryptojacking And Other Malware Strains, Connect Devices Without Worrying They’re Compromised.
Prevention Is The Best Cure.
Heimdal™ Premium Security Home Eliminates Vulnerabilities In Your System And Protects The Valuable Data That Makes Up Your Digital Life. Seamlessly Installs And Patches Your Other Software, So Your System Is Always Updated And Always Secure.
Locky Ransomware, Locky Ransomware Removal, Remove Locky Ransomware, Uninstall Locky Ransomware, Delete Locky Ransomware