 Blog's Page
Blog's Page

GSB67OPS.NET ADS Is A Nasty Adware Program That Can Enter Your System Through Email Folders. GSB67OPS.NET ADS Has Been Created By The Cyber Criminals. GSB67OPS.NET ADS Is Work For adware In Front But Behind GSB67OPS.NET ADS May Assist ransomware Program To Target The Computer Resources. There Are Number Of Paths Where To Reach GSB67OPS.NET ADS Adware Program In Your Computer System.
GSB67OPS.NET ADS Was Not Easily Declared As A Malware Or computer Virus Program, Normally People Know About Them. There Are Sub Variant Of The Malware Program, Which Can Reside Inside The Computer System. GSB67OPS.NET ADS Would Not Immediately Show Off. GSB67OPS.NET ADS Algorithm Is Very Advance To Tackle The Security Credentials.
Who Are Infected By The GSB67OPS.NET ADS Adware Program, Then He Or She Will Explain To What Happens After GSB67OPS.NET ADS Malware Can Compromise The Computer System And How To React. According To The Experience Of The Victim, The Web Browser Will Not Work Impeccably. GSB67OPS.NET ADS Malware May Annihilate The Update Files, Which Associated With Internet. The Security Software Already Shows Malfunction.
The Small Tools, Application Or Software Will Be Contaminated By The GSB67OPS.NET ADS Malware Program. You Cannot Report The Trouble Through Internet, Because Internet Data Sharing Capability Would Be Shrunk.
Steps Are Many But Precaution Is Better Than Cure – Is Good Indication To Control The Computer System Failure While Malware May Invade. You Must Apply The Security Software To Scan The Infected Files And Quarantine Them To Other Folders. It Is A Good Tactics To Sabotage The Gsb67ops.net Ads Malware Program. But Sometime Malware Program Initialize Itself Through Small Code Or Tiny Size File.
Be Careful From GSB67OPS.NET ADS Malware Application, That Can Not Friendly For The Computer System. GSB67OPS.NET ADS Malware Would Possible To Destroy Some Indispensable File, Which Can Be Restored By The Data Recovery Software.
Google Chrome
Mozilla Firefox
Microsoft Edge
Safari
Even After Jingle With The Web Browser, Malware Malign Code May Still Display Up. In That Situation, An Advertisements Is Related With Malware Program, Which May Be The Issues Of This. Malware May Occur As A Consequence Of A Skeptical Application Installed In The Computer System. If The User Is Not Sure Which Software Is Causing The Troubling, Exploit Task Manager To Figure It Out The Next Time The Pop-ups Appear.
Method 1: Manual Removal
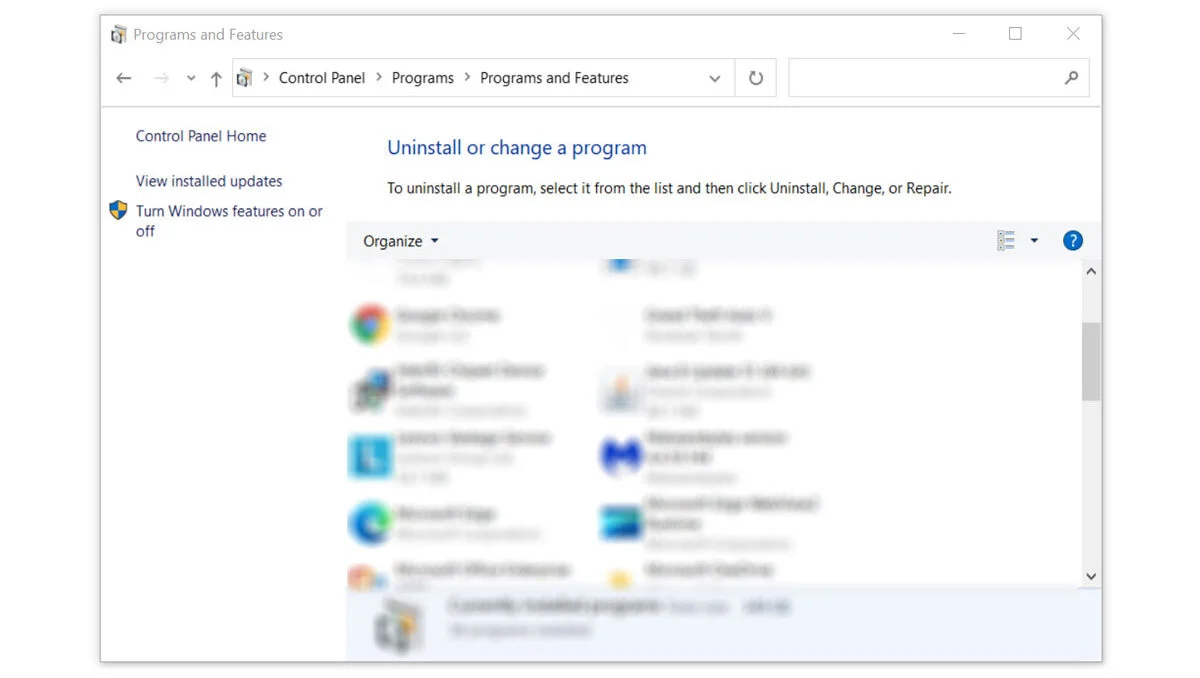
Method 2: Remove Suspicious Extension From Browser
Malign Code Or Malign Adware And Malware May Sometimes Be Found As Web Plugin Inside The Web Browser. If You Do Not Watch Any Skeptical Applications On Your Computer System, The Malware Program Will Most Likely Be Conceal Within The Internet Browser Itself.
Google Chrome
Click The three Dot Buttons In The Right-hand Corner Of Chrome Browser. Find And Click More Tools From The Drop Menu, Then Select Extensions.
A New Tab Will Appear With All Your Installed Extensions. Find Which Extension Is Suspicious And Delete It. In Order To Deactivate The Extension, toggle The Blue Switch To Disable The Program. Then Click The remove Button To Fully Uninstall It From Google Chrome.
If The Switch Is Disabled: You Must Remove The Extension From Within The Extensions Folder Manually. Go To The Google Chrome Extensions Folder By Using The Following Directory:
C:\Users\YOUR NAME\AppData\Local\Google\Chrome\User Data\Default\Extensions
You Will See A List Of Folders With Different Hashes, To Find What You Need To Delete, Tick The Developer Mode In The Google Chrome Extensions Tab To Show The Id Of Downloaded Plugins.
Find The One Matching The Id Of The Extension You Wish To Remove To The One In The Folder Then Delete It. Restart Google Chrome And The Extension Should Be Gone.
Mozilla Firefox
Click The Menu Button In The Right Corner Of Firefox Once It’s Open. Then Go To Add-ons And Themes Then Select Extensions.
Toggle The Blue Switch To Disable The Suspicious Extension After Finding It. Click Remove From The Three Dots Icon On The Right Side Of The Extension You Want To Remove.
Microsoft Edge
Open Microsoft Edge Application Then Click On The Three Dots On The Upper Right. A Drop-down Menu Will Show Then Click Extensions.
New Tab Will Open And Show All Installed Extensions On The Browser. Find The Suspicious Extension That You Might Have Not Installed.
Slide The Blue Switch To Disable The Use Of The Extension. Click On The remove Button Just Below The Extension.
Safari
Open The Safari Browser Then Click On Safari On The Menu Bar On Top. Choose Preferences From The Drop Menu. A Window Should Appear, Then Click The Extensions Tab.
Search For Suspicious Extensions You Did Not Install. Click The Unwanted Extension Then Select The remove Button.
Method 3: Google Chrome Cleanup Tool
If You Are Using Google Chrome As A Default Browser Program, Then You May Utilize The Cleanup Tool Feature That Came With The Application.

Note:
When The Malicious Program Is Uninstalled, Malware Should Not Come Back. If The Adware Infection Still Remains, A Good Antivirus Program Should Be Able To Eliminate The Threat.
It Is Much Easier To Rely On An Antivirus Application When Dealing With Malware Because It Is Lot Easier To Use Since Not Everyone In The Web Is A Tech Savvy. Please Follow The Instructions On The Next Section.
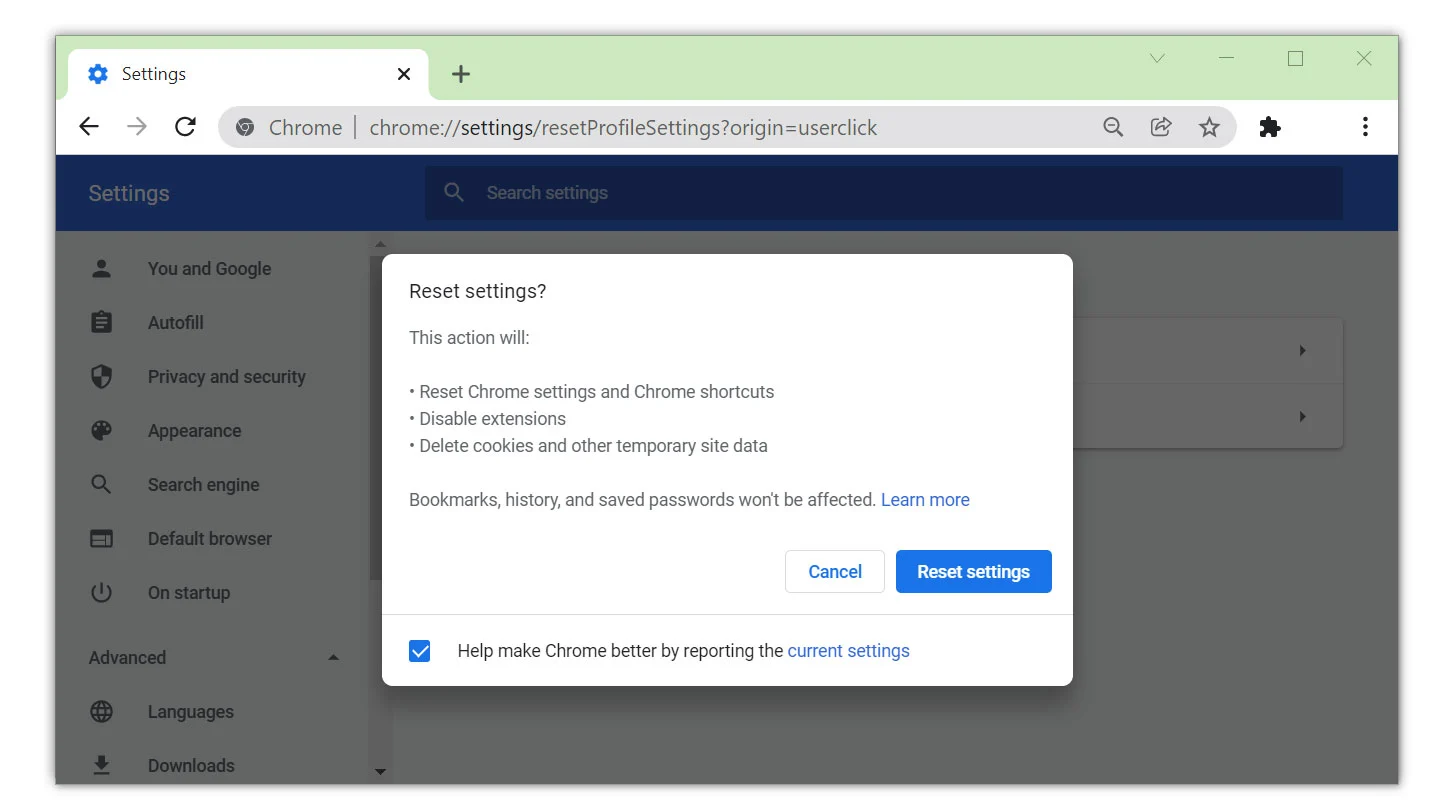
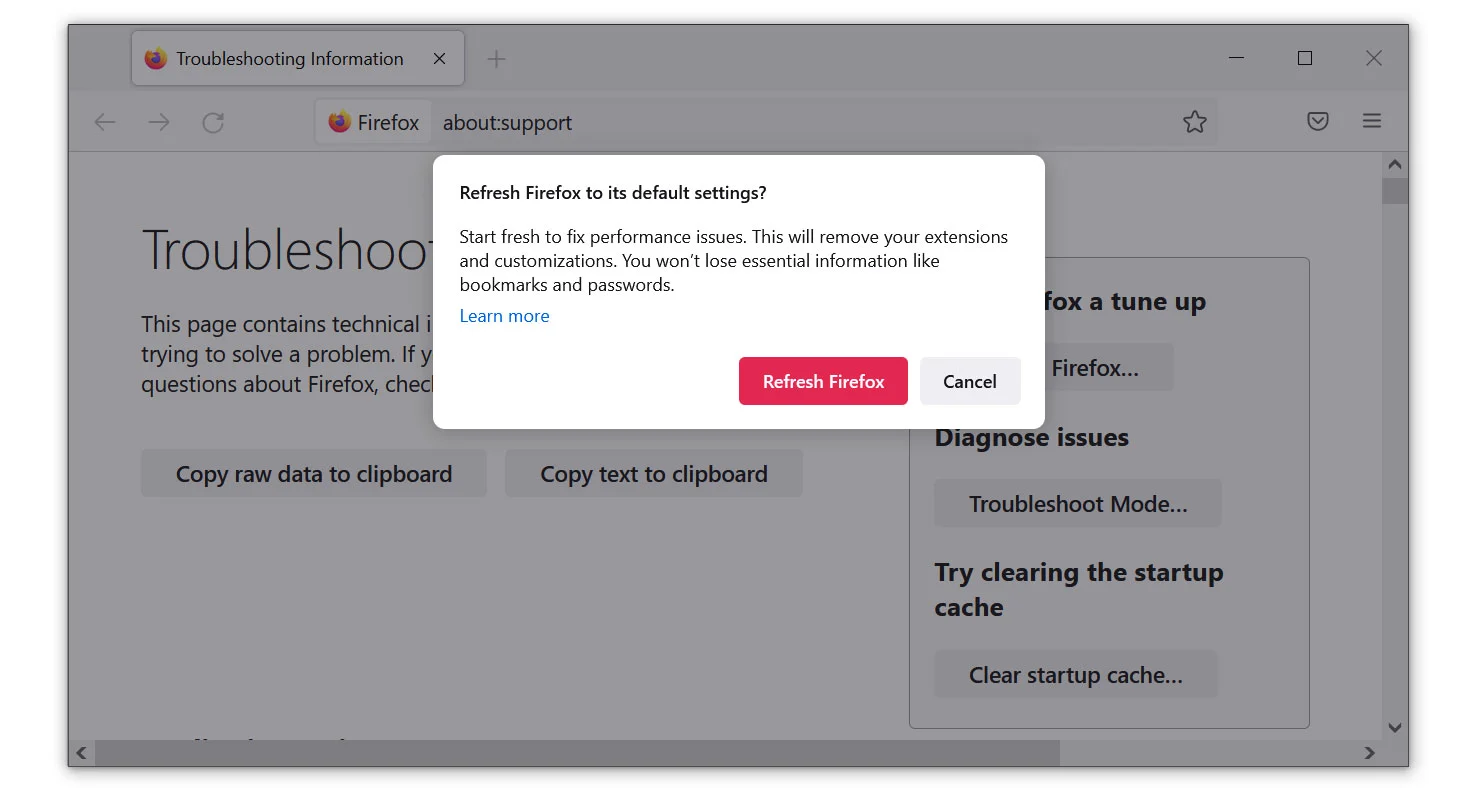
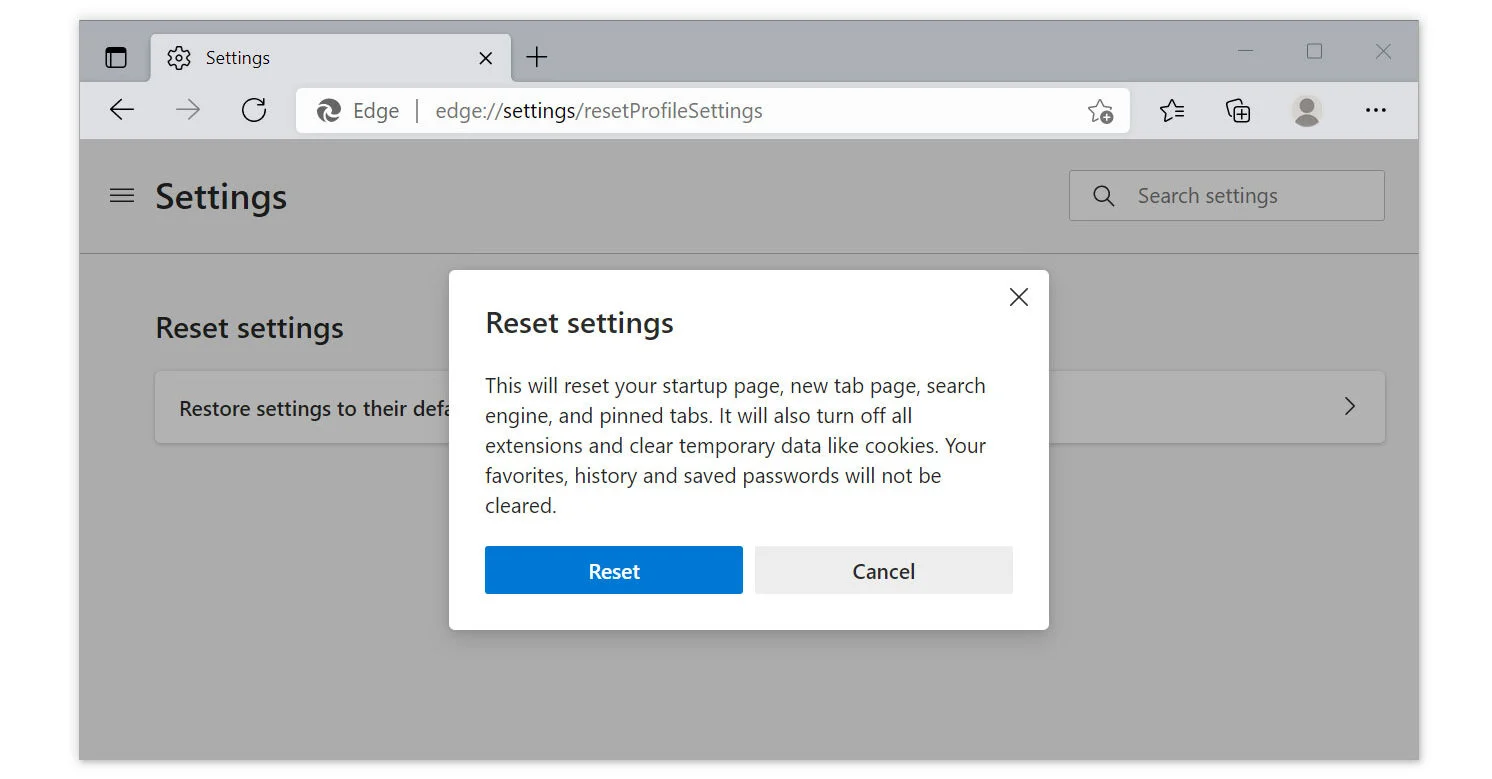
If The Malware Deceit Web Site Is Still Not Eliminated After The Previous Steps, Resetting The Browser Program Should Do The Trick. It Is Also Worth To Note That The Reset Will Not Erase Your Saved Bookmarks And Passwords.
Reset Google Chrome
Mozilla Firefox
Microsoft Edge
Sometimes, Malicious Website May Come Appear To The Computer Once Again That Is Why Users Should Take Advantage Of The Pop-up Blocker Within The Browser Itself. Web Browsers Typically Have A Pop-up Blocker System Installed In Their Program.
If You Do Not Need Browser Notifications At All, You Should Enable This Feature. It Will Get Rid Of The Pop-up Advertisements As Well As Future Risks.
For Google Chrome

For Mozilla Firefox
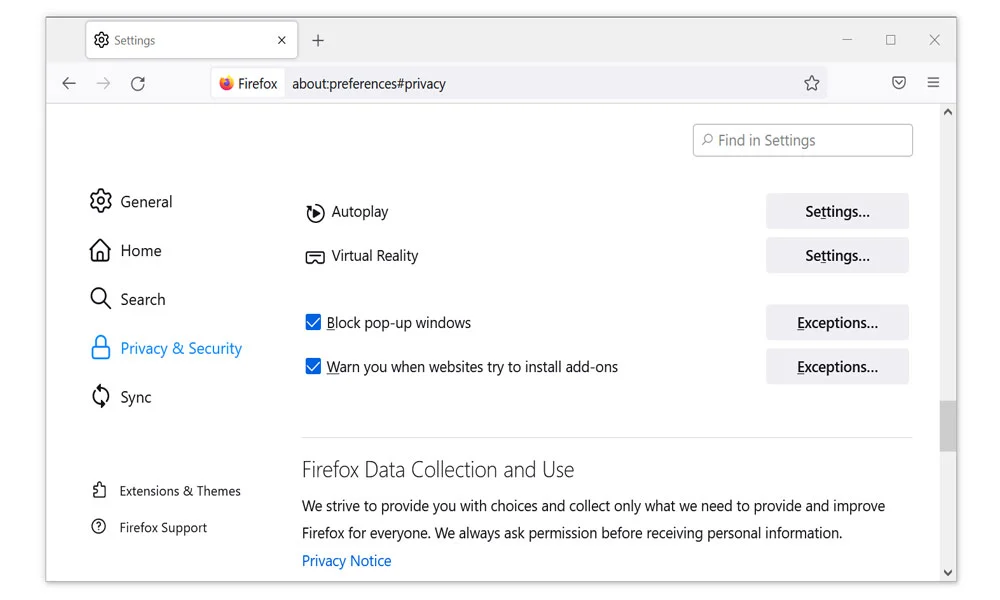
For Microsoft Edge

For Safari
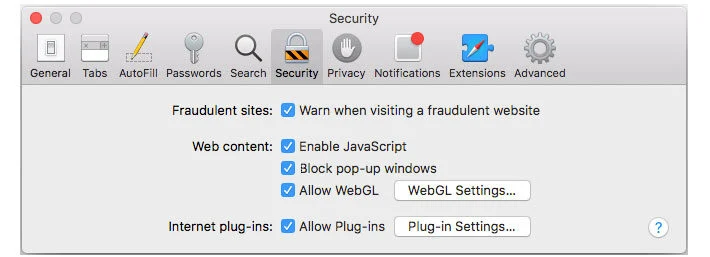
This Will Stop All Pop-ups And Notifications From Appearing On Any Website You Visit, Regardless Of Whether It Is Harmful Or Not.
1. Award-winning Security
The Same Malware That Attacks Fortune 500 Companies Attacks Private Users, Too. Sophos Home Uses The Same Award-winning Security Features That Keep Those Companies Safe.
New Features Of The Sophos Home
You Have Been Infected. Well, Not You, But Your Computer Has. It’s Slow. You Need A No-nonsense Malware Cleaner To Get Your Computer Back Up To Speed. HitmanPro Is The Malware Remover Of Choice For Tens Of Millions Of People.
It’s Really Small
You Can Download HitmanPro In Two Seconds (unless You Still Have Dial-up Internet). It’s Only 10MB. Plus, You Do Not Have To Install It – Just Run It After It’s Downloaded.
It Scans For Bad Behavior
A Standard Antivirus Program Misses Stuff. It’s Focused On Finding Malware Signatures That Virus Firms Have Identified As Malicious. But What About New, Zero-day Threats That Have Not Been Researched? That’s Why HitmanPro Looks At Behaviors When Scanning For Trojans And Other Malware. Bad Behavior Is Caught, With Or Without A Malware Signature.
It Uses Multiple Experts
Two Heads Are Better Than One. So We Have Four. HitmanPro Leverages Malware Databases From Four Security Labs, Including SophosLabs, To Be Incredibly Thorough When Scanning For And Cleaning Up Spyware And Malware. More Research Means More Powerful Cleaning.
It Cleans Up After Itself
Malware Piggybacks On Various Programs To Gain Access To Your Computer. HitmanPro Removes That Malware – And It Does Not Stop There. Damaged Windows Resources Are Brought Back To Their Safe, Original Versions.
It Goes Deep To Clean
Resilient Malware Can Also Affect Critical System Files And Boot Records To Manipulate The Windows Operating System And Installed Antivirus Software. This Is Even Before The Operating System Boots. HitmanPro Can Remove These Persistent Threats From Within The Running Operating System And Its Boot Records.
Cylance Smart Antivirus Is The First Next-generation Antivirus Available To Consumers And Provides Families With The Only Enterprise Class Security Software Designed For Personal Use. Using Artificial Intelligence, Cylance Smart Antivirus Eliminates The Need For Updates And Pop-ups While It Protects You And Your Loved Ones Against The Latest Cybersecurity Threats.
| Smart Antivirus For US | Smart Antivirus For UK |
| Smart Antivirus For Ireland | Smart Antivirus For Canada |
| Smart Antivirus For New Zealand | Smart Antivirus For Australia |
An Antivirus That Works Smarter, Not Harder, From BlackBerry. Lightweight, Non-intrusive Protection Powered By Artificial Intelligence.
Traditional Antivirus Can’t Keep Up
Traditional Antivirus Typically Uses A Signature Based Model, Which Is Reliant On Capturing New Viruses In The Wild And Creating A Master List Of Malware For Users To Download. This Makes It Especially Vulnerable To Zero-day Attacks And Modern Threats Which Can Alter Themselves Too Quickly For Signature Updates To Catch.
A Different Approach
Cylance Uses Cutting-edge Algorithms And Artificial Intelligence To Proactively Protect You, Preventing Threats Like Malware, Hackers, Viruses, Ransomware, And Malicious Websites. It Does This Whilst Being Lightweight And Easy To Use. Cylance’s AI Has Been Demonstrated As Effective Against Threats -- Even Without Updates -- Over 2 Years Into The Future.
Advanced AI Training
We Use Cloud-based Supercomputers And Millions Of Examples Of Malicious Programs To Train A Neural Net, A Kind Of Digital Brain, To Recognise Threats.
Download And Protect
When You Purchase Cylance, This Is What You Download Onto Your Computer - A Superlightweight ’brain’, Trained To Catch And Quarantine Viruses.
Detection In Milliseconds
Cylance Sits In The Background, Instantly Recognising Threats The Moment They Occur And Reacting In Milliseconds – Unlike Other Antivirus Software Which Must Constantly Scan For Threats.
Complete Protection
Our AI Quarantines Files It Identifies As Threats, Allowing You To Review Individual Threats On You And Your Family’s Computers.
Cutting Edge Protection Without The Bloat Of Traditional Antivirus
Cylance Sits In The Background, Instantly Recognising Threats The Moment They Occur And Reacting In Milliseconds - Unlike Other Antivirus Software Which Must Constantly Scan For Threats.
1. Stops Infections Before They Can Attack
Traditional Antivirus Waits For You To Be Infected Before It Can Act. Cylance Observes The Behaviour Of Programs In Real-time, Detecting Threats In Milliseconds - Before They Can Execute.
2. Protects Against Never-before Seen Malware
Proactive AI Provides Protection From All Types Of Malware - Existing Threats And Those Yet To Be Developed. Cylance Prevents Attacks Before They Happen Rather Than Relying On Other Users Becoming Infected To ’discover’ Threats.
3. Unobtrusive Protection
We Know You Just Want Your Antivirus To Keep Your Safe - Not Waste Your Time. That’s Why We Guarantee To Never Bother You With Unwanted Alerts Or Pop-up Ads. Promise.
4. Light On RAM And CPU
We’ve Done All The Computational Heavy Lifting In The Cloud. As A Result, Cylance Uses Much Less RAM And CPU Than Other AV Solutions - Making It Perfect For Gamers Or Alongside Other Intensive Processes. You Won’t Even Notice We’re There.
Cylance Protects Devices On All Major Platforms And With Remote Protection, Cloud-based Support, Simple Set-up, It’s Never Been Easier To Be The Expert.
Easy To Install And Use
It’s Easy To Get Started With Cylance. Simply Download And Install, And You Have The Power Of An AI Supercomputer On Your Device. The Intuitive Interface Allows You To Manage Devices Centrally, Modify Settings, And Check Which Files Cylance Has Quarantined.
Remote Management
Cloud Based Support And Remote Management And Protection Means No More Worried Calls From Mom. Remotely View The Quarantine List Of All Devices To Keep Your Family Secure And Take The Work Out Of Being The Expert.
Operating Systems:
Memory
Internet Browser Support:
Cylance Uses Artificial Intelligence To Deliver Prevention-first, Predictive Security Products And Specialized Security Services That Change How Organizations Approach Endpoint Security. Cylance’s Security Solutions Provide Full Spectrum Predictive Threat Prevention And Visibility Across The Enterprise, Combatting Threats Such As Malware, Ransomware, File Less Malware, Malicious Scripts, Weaponized Docs, And Other Attack Vectors.
| Smart Antivirus For US | Smart Antivirus For UK |
| Smart Antivirus For Ireland | Smart Antivirus For Canada |
| Smart Antivirus For New Zealand | Smart Antivirus For Australia |
With AI Based Malware Prevention, Application And Script Control, Memory Protection, Device Policy Enforcement, Root Cause Analysis, Threat Hunting, Automated Threat Detection And Response, Coupled With Expert Security Services, Cylance Can Protect Endpoints Without Increasing Staff Workload Or Costs.
The Essential PC & Internet Security Solution
1. Antivirus & Anti-Spyware Engine
Detects And Removes Viruses, Spyware, Trojan Horses, Worms, Bots And More. Independently Tested To Provide Superior Protection.
2. Advanced Real-Time Antivirus
Provides Access To The Up-to-date Database Of Antivirus Signatures To Protect Against Newly Emerging Threats. Real-Time Cloud Database Contains Up-to-date Reputation Of Files, Web Resources And Software Enhancing Traditional Antivirus + Firewall Protection
Checks Files Against Real-time Cloud Database To Ensure That Even The Latest Threats Are Not Missed.
Contains The Latest Antivirus Signatures, Web Resources And Software To Ensure Up-to-date Protection.
3. Two-way Firewall
Stops Internet Attacks At The Front Door And Even Catches Thieves On Their Way Out. Our Two-way Firewall Proactively Protects Against Inbound And Outbound Attacks While Making You Invisible To Hackers.
4. Advanced Firewall
No Product Is 100% Effective Against Viruses Or Spyware. ZoneAlarm’s Advanced Firewall Monitors Behaviors Within Your Computer To Spot And Stop Even The Most Sophisticated New Attacks That Bypass Traditional Antivirus And Security Suites.
5. Additional Layers
Multiple Layers Of Advanced Protection Provide Unsurpassed Security.
Anti-Phishing
Protects You Against Phishing Attacks.
Antivirus/Anti-Spyware Engine
Detects And Remove Viruses, Spyware, Trojan Horses, Worms, Bots And Rootkits.
Advanced Real-Time Antivirus
Enhances Protection By Checking Against An Always Up-to-date Cloud Database Of Antivirus Signatures.
Advanced Firewall
Monitors Programs For Suspicious Behavior Spotting And Stopping New Attacks That Bypass Traditional Anti-virus Protection.
Two-way Firewall
Makes Your PC Invisible To Hackers And Stops Spyware From Sending Your Data Out To The Internet.
Identity Protection
Helps To Prevent Identity Theft By Guarding Your Personal Data.
Browser Protection
Protects Your Computer From Web Threats Before They Reach Your Browser.
1. Anti-Phishing Add-on
Google® Chrome All Versions
2. Microsoft® Windows® 10
3. Microsoft® Windows 7 SP1 All Versions
4. Microsoft .NET Framework
Version 3.5 Or Later
Note: If A Supported Microsoft .NET Framework Is Not Installed, It Will Be Installed With ZoneAlarm

Secure Your Digital Life Completely. True Cybersecurity Needs To Be Proactive, Not Reactive.
Support
Special Features Of Heimdal Premium Security Home
ANTIVIRUS IS NOT ENOUGH IN TODAY'S EVER EVOLVING ONLINE THREATSCAPE
Heimdal Premium Security Home Is The Ultimate Cybersecurity Suite, Combining A True Proactive Threat Prevention Solution With A Next-gen Antivirus With Market Leading Detection Rates So You Can Enjoy The Internet Freely!
Secure Your Digital Life Completely
Next-gen Threat Prevention Based On Machine Learning Meets A Powerful Antivirus With Market-leading Detection, So Your Online Security Is Flawless
Discover Actual Security In An Ever-changing Threat Landscape.
Heimdal™ Premium Security Home Brings The Unique Threat Prevention Layer Of Heimdal™ Threat Prevention Home On Top Of A Flawless, Market-leading Detection Heimdal™ Next-Gen Antivirus Home Antivirus To Stop Ransomware, Data Leakage, Viruses, APTs, Exploits & Other Advanced Online Threats.
Enjoy A Next Gen Multi-layered Security Suite.
Heimdal™ Premium Security Home Prevents Unknown Threats And Stops The Known Attacks. Browse Online Without The Fear Of Ransomware, Cryptojacking And Other Malware Strains, Connect Devices Without Worrying They’re Compromised.
Prevention Is The Best Cure.
Heimdal™ Premium Security Home Eliminates Vulnerabilities In Your System And Protects The Valuable Data That Makes Up Your Digital Life. Seamlessly Installs And Patches Your Other Software, So Your System Is Always Updated And Always Secure.
Data Recovery Is An Important Software To Retrieve The Lost Data As Well As The Files Inside The Computer System. However, Data Is Loss Due To Malware Invasion, Crafting The Malicious Code, Which May Delete The File Without Information Or Permission By The User. Data Recovery Is Retrieve Lost File From Inside The Hard Disk Drive To Prior Location. There Are Number Of Data Recovery Software Are Available In The Internet Market Or Online Shop.
You Can Try To Download As Well As An Install The Data Recovery Software To Recovery The Lost Files, Such As Images, Vidoes, Music And Other Text Files Via DRS Application.
Gsb67ops.net, Remove Gsb67ops.net, Gsb67ops.net Re