 Blog's Page
Blog's Page

CDTT Ransomware Is A Malicious Software Program Designed To Encrypt Files On A Victim's Computer And Demand A Ransom Payment For Their Release. CDTT Ransomware Type Of Malware Is Classified As Ransomware, A Form Of Cyber Attack That Has Become Increasingly Prevalent In Recent Years.
CDTT Ransomware Specifically Targets Files On Windows-based Systems, Encrypting Them With A Strong Cryptographic Algorithm To Render Them Inaccessible To The Victim. Once CDTT Ransomware Infects A Computer, It Scans The System For Various Types Of Files, Including Documents, Images, Videos, And More.
It Then Encrypts These Files Using A Unique Encryption Key, Which Is Stored Securely On The Attacker's Servers. During The Encryption Process, CDTT Ransomware Appends A Specific File Extension To The Encrypted Files, Making Them Easily Identifiable To The Victim.
After Encrypting The Files, CDTT Ransomware Typically Leaves A Ransom Note On The Victim's Desktop Or In The Folders Containing The Encrypted Files. CDTT Ransom Note Usually Contains Instructions On How To Contact The Attackers, As Well As Details On How To Pay The Ransom To Receive The Decryption Key.
The Ransom Demand Is Usually Made In Bitcoin Or Another Cryptocurrency To Help Maintain The Anonymity Of The Attackers. The Ransom Note May Also Include Threats Or Warnings To Pressure The Victim Into Paying The Ransom Quickly.
Attackers Often Use Scare Tactics, Such As Threatening To Delete The Decryption Key Or Permanently Destroy The Encrypted Files If The Ransom Is Not Paid Within A Certain Timeframe. Additionally, The Note May Provide Details On How To Access A Decryption Tool Or Service Provided By The Attackers After Payment Is Made.
Victims Of CDTT Ransomware Face A Difficult Decision When Confronted With The Ransom Demand. Paying The Ransom May Seem Like The Quickest Way To Regain Access To Their Files, But It Also Encourages And Funds Further Criminal Activity.
Moreover, There Is No Guarantee That The Attackers Will Provide The Decryption Key Or That It Will Successfully Decrypt The Files Once The Ransom Is Paid.
On The Other Hand, Refusing To Pay The Ransom Means Losing Access To Important Files And Potentially Suffering Significant Data Loss. In Some Cases, Victims May Be Able To Restore Their Files From Backups If They Have Been Regularly Backing Up Their Data.
However, This Is Not Always Possible, Especially If Backups Are Not Up-to-date Or If The Ransomware Has Also Targeted Backup Files. Preventing CDTT Ransomware Infections Requires A Combination Of Proactive Measures And Security Best Practices.
These May Include:
In Conclusion, CDTT Ransomware Is A Dangerous Form Of Malware That Encrypts Files On A Victim's Computer And Demands A Ransom Payment For Their Release. Victims Of Ransomware Attacks Face Difficult Decisions And May Suffer Significant Data Loss If They Are Unable To Recover Their Files.
Preventing Ransomware Infections Requires A Combination Of Proactive Measures And Security Best Practices To Protect Against This Evolving Threat.
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
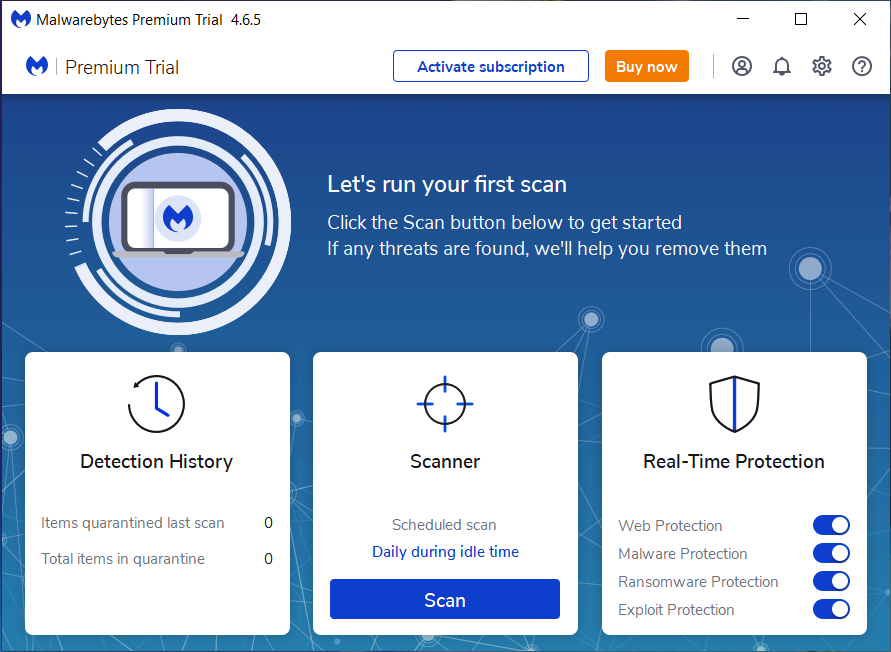
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:




If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
CDTT Ransomware, Remove CDTT Ransomware, Uninstall CDTT Ransomware, Get Rid Of CDTT Ransomware, CDTT Ransomware Removal| Links1 | Links2 | Links3 | Products | Social Links |
|---|---|---|---|---|
| Home | Blog | Sitemap | Email Checker Tool | |
| About | CSI Links | ISRO Project Code: AA0802 | Offers | |
| Disclaimer | Gallery | Contact Us | Antivirus | |
| Privacy Policy | Software Downloads |