 Blog's Page
Blog's Page

Scientists Have Discovered A Novel Form Of ransomware Called Blackoutware. This malicious Threat Is Designed To Encrypt Data On Compromised Devices, Forcing Individuals To Pay A Ransom In Exchange For The Decryption Key.
After Infiltrating A Device, Blackoutware Secures The Files Stored On It. Significantly, Each Impacted File Undergoes A Change In Its Filename, Marked By The Addition Of The '.blo' Extension. For Example, A File Initially Named '1.jpg' Is Altered To '1.jpg.blo,' And '2.png' Transforms Into '2.png.blo.' This Extension Acts As A Clear Sign Of The Encryption Applied To The Files.
Once The Encryption Process Is Finished, A Ransom Note Titled '!!!WARNING!!!.txt' Is Left In The 'C:\Users[username]' Folder. This Note Usually Includes Instructions From The Attackers, Detailing The Necessary Steps For The Victim To Fulfill The Ransom Payment And Obtain The Decryption Key. The Use Of Such Ransom Notes Is A Prevalent Tactic Employed By Cybercriminals To Instill Fear And Pressure Victims Into Meeting Their Demands.
The Ransom Communication From Blackoutware Ransomware Explicitly States That The Victim's Files Have Been Encrypted, And The Sole Method Of Decryption Is Through Payment. Non-compliance With The Ransom Demand Poses The Risk Of Exposing Sensitive Data Extracted From The Compromised Device, Encompassing Files, Login Credentials, Credit Card Numbers, And Other Confidential Information.
The Designated Ransom Sum Is 5000 Euros, To Be Paid In Either LTC (Litecoin) Or BTC (Bitcoin) Cryptocurrencies. The Victim Is Given A 72-hour Deadline To Fulfill The Payment Conditions. The Ransom Note Warns Against Attempting To Alter The Encrypted Files Or Employing Third-party Decryption Tools, As Such Actions May Lead To Irreversible Data Loss.
Achieving Decryption Without The Involvement Of Cybercriminals Is Generally Unfeasible. Moreover, Even If Victims Do Adhere To The Ransom Demands, There Is No Assurance Of Receiving The Pledged Decryption Keys Or Software. Consequently, It Is Highly Recommended Not To Pay The Ransom, As Such Actions Not Only Do Not Guarantee Data Recovery But Also Contribute To The Unlawful Activities Of The Perpetrators.
To Prevent Ongoing Data Encryption, It Is Advisable To Eliminate The Blackoutware Ransomware From The Operating System. It Is Crucial To Acknowledge That The Removal Process Does Not Automatically Restore Access To The Encrypted Files, Underscoring The Significance Of Preventive Measures And The Adoption Of Secure Computing Practices.
This Black Friday VPN Deals 2023, Fortify Your Online Security With Exclusive VPN Deals! Unlock Discounts On Top-tier Services, Ensuring Private And Unrestricted Internet Access. Black Friday VPN Deals 2023, Browse Anonymously, Safeguard Sensitive Data, And Enjoy Seamless Streaming With Lightning-fast Speeds. Don't Miss Out On These Limited-time Offers—invest In Your Digital Privacy This Black Friday VPN Deals 2023 And Enjoy A Safer Online Experience. Read More...
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:



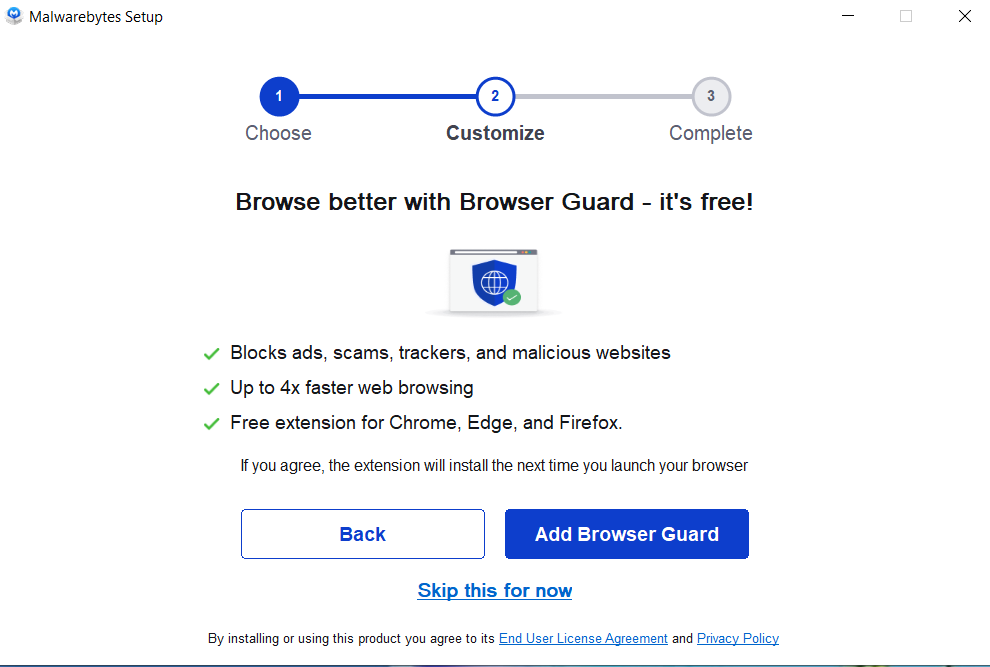

If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
Blackoutware Ransomware, Remove Blackoutware Ransomware, Uninstall Blackoutware Ransomware, Delete Blackoutware Ransomware, Blackoutware Ransomware Re