 Blog's Page
Blog's Page
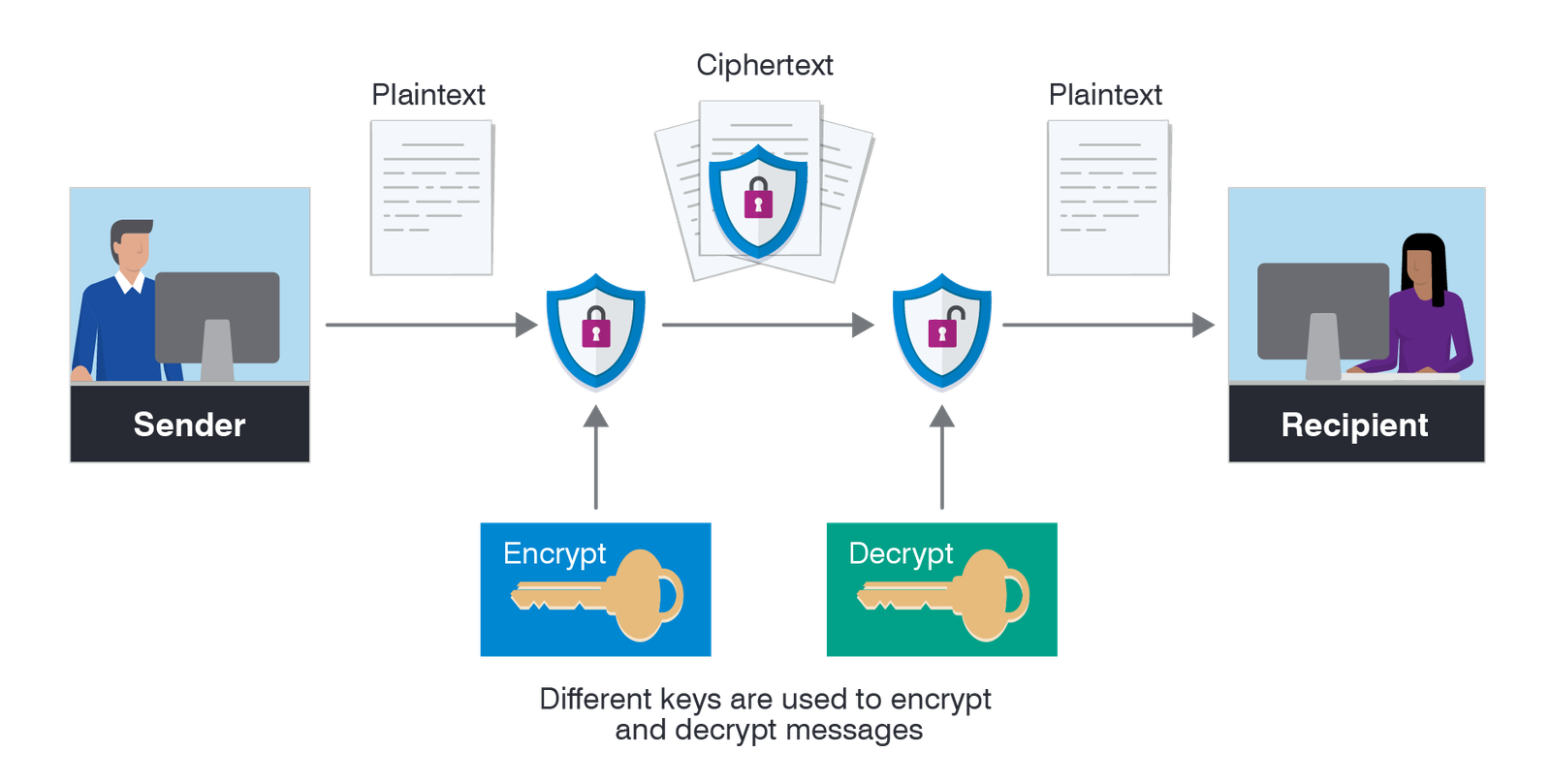
Encryption Is A Process Of Converting Plaintext Into An Unreadable Ciphertext To Protect The Confidentiality And Integrity Of Data During Transmission Or Storage. The Process Of Encryption Uses An Algorithm, Known As A Cipher, To Perform The Transformation, And A Secret Key That Is Used To Encrypt And Decrypt The Data.
The Main Benefits Of Encryption Include:
Confidentiality: Encryption Protects Sensitive Information From Unauthorized Access, By Converting The Data Into An Unreadable Format That Can Only Be Deciphered Using The Secret Key.
Integrity: Encryption Provides Protection Against Unauthorized Changes To Data, As Any Alterations To The Encrypted Data Will Result In An Incorrect Decryption.
Authentication: Encryption Can Be Used To Provide Authentication, By Including A Digital Signature That Verifies The Authenticity Of The Sender And The Integrity Of The Message.
Encryption Is Widely Used In Various Applications, Such As Email, File Transfers, And VPNs (Virtual Private Networks), To Protect Sensitive Data From Unauthorized Access And Tampering. There Are Various Types Of Encryption Algorithms, Including Symmetric Encryption (where The Same Key Is Used For Encryption And Decryption) And Asymmetric Encryption (where Different Keys Are Used For Encryption And Decryption).
Encryption Is An Essential Tool For Ensuring The Security And Privacy Of Data In Computer Networks, And Plays A Critical Role In Protecting Sensitive Information From Unauthorized Access, Tampering, And Theft.
There Are Two Main Types Of Encryption: Symmetric Encryption And Asymmetric Encryption.
Symmetric Encryption: In Symmetric Encryption, The Same Key Is Used For Both Encryption And Decryption. This Makes Symmetric Encryption Fast And Efficient, But Also Requires That Both The Sender And Recipient Of The Data Have Access To The Same Secret Key.
Asymmetric Encryption: In Asymmetric Encryption, Also Known As Public Key Cryptography, Two Different Keys Are Used For Encryption And Decryption. A Public Key Is Used To Encrypt The Data, And A Private Key Is Used To Decrypt The Data. Asymmetric Encryption Is Slower Than Symmetric Encryption, But Provides A Higher Level Of Security, As The Private Key Is Kept Secret And Cannot Be Easily Compromised.
Other Types Of Encryption Include:
Block Cipher: A Block Cipher Encrypts Data In Fixed-size Blocks, Typically 64 Or 128 Bits At A Time.
Stream Cipher: A Stream Cipher Encrypts Data One Bit Or Byte At A Time, And Is Used For Real-time Communications, Such As Video And Audio Streaming.
Substitution Cipher: A Substitution Cipher Replaces Each Character Of The Plaintext With A Different Character Or Symbol.
Transposition Cipher: A Transposition Cipher Rearranges The Order Of The Characters In The Plaintext.
Hash Functions: A Hash Function Is A Type Of Encryption That Takes An Input (or "message") And Returns A Fixed-size String Of Characters, Which Is Typically Used For Data Integrity And Authentication.
Different Types Of Encryption Algorithms Have Different Strengths And Weaknesses, And The Choice Of Encryption Depends On The Specific Requirements Of The Application. The Most Common Encryption Algorithms Include AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), And Blowfish.
Symmetric Encryption, Also Known As Shared Secret Encryption Or Secret Key Encryption, Is A Type Of Encryption Where The Same Key Is Used For Both Encryption And Decryption Of The Data. It Is Called "symmetric" Because The Same Key Is Used To Both Encrypt And Decrypt The Data.
In Symmetric Encryption, The Sender And The Recipient Of The Data Must Both Have Access To The Same Secret Key, Which Is Used To Encrypt And Decrypt The Data. The Key Is Typically Shared Between The Sender And Recipient Through A Secure Communication Channel, Such As A Personal Meeting Or A Secure Key Exchange Protocol.
Symmetric Encryption Is Widely Used For Its Simplicity And Speed, And Is Well-suited For Encrypting Large Amounts Of Data, Such As Files And Messages. Some Of The Most Widely Used Symmetric Encryption Algorithms Include AES (Advanced Encryption Standard), DES (Data Encryption Standard), And Blowfish.
Symmetric Encryption Is Also Commonly Used In Combination With Other Types Of Encryption, Such As Asymmetric Encryption, To Provide A Secure End-to-end Communication Channel. For Example, Symmetric Encryption Is Often Used To Encrypt The Data, While Asymmetric Encryption Is Used To Securely Exchange The Secret Key Between The Sender And Recipient.
Asymmetric Encryption, Also Known As Public Key Cryptography, Is A Type Of Encryption That Uses Two Different Keys For Encryption And Decryption Of The Data. In Asymmetric Encryption, A Public Key Is Used To Encrypt The Data, And A Private Key Is Used To Decrypt The Data.
The Public Key Is Made Available To Anyone Who Needs To Send Encrypted Messages, While The Private Key Is Kept Secret By The Owner And Is Used To Decrypt Messages That Have Been Encrypted Using The Corresponding Public Key. The Private Key Is The Critical Element In Ensuring The Security Of The Encryption, As It Is Used To Decrypt Sensitive Information And Must Be Kept Confidential At All Times.
One Of The Main Benefits Of Asymmetric Encryption Is That It Provides A High Level Of Security, As The Private Key Is Kept Secret And Cannot Be Easily Compromised. It Also Provides A Convenient Way For Users To Securely Exchange Encrypted Messages Without Having To Share Secret Keys In Advance.
Examples Of Popular Asymmetric Encryption Algorithms Include RSA (Rivest-Shamir-Adleman), DSA (Digital Signature Algorithm), And Elliptic Curve Cryptography (ECC). These Algorithms Are Widely Used In Applications Such As Digital Signatures, Secure Email, And Secure Web Browsing.
A Block Cipher Is A Method Of Encrypting Data That Operates On Fixed-size Blocks Of Data, Typically With A Fixed Block Size Of 64 Or 128 Bits. It Works By Taking A Plaintext Message And Dividing It Into Blocks, Which Are Then Encrypted One Block At A Time Using A Secret Key.
In A Block Cipher, The Same Key Is Used For Both Encryption And Decryption, And The Same Encryption Algorithm Is Used For Each Block. The Encryption Process For Each Block Is Performed Independently, Meaning That The Encryption Of One Block Does Not Depend On The Encryption Of Any Other Block.
Block Ciphers Can Be Used In Several Modes Of Operation, Such As ECB (Electronic Codebook), CBC (Cipher Block Chaining), And CFB (Cipher Feedback), To Provide Different Levels Of Security And Encryption Features.
Block Ciphers Are Widely Used In Symmetric Encryption, As They Are Simple, Fast, And Can Be Implemented Efficiently In Hardware Or Software. Some Of The Most Widely Used Block Cipher Algorithms Include AES (Advanced Encryption Standard), DES (Data Encryption Standard), And Blowfish.
Block Ciphers Are Also Commonly Used In Combination With Other Encryption Techniques, Such As A Message Authentication Code (MAC) Or A Hash Function, To Provide Additional Security And To Ensure The Authenticity And Integrity Of The Encrypted Data.
A Stream Cipher Is A Type Of Encryption That Encrypts Data One Bit Or Byte At A Time, As Opposed To Encrypting It In Blocks Like A Block Cipher. Stream Ciphers Generate A Keystream, Which Is A Sequence Of Random Numbers, And XOR The Keystream With The Plaintext To Produce The Ciphertext.
In A Stream Cipher, The Same Key Is Used For Both Encryption And Decryption, And The Encryption Process For Each Bit Or Byte Depends On The Previous Bit Or Byte. This Means That A Change In The Plaintext Will Result In A Corresponding Change In The Ciphertext.
Stream Ciphers Are Typically Faster And More Efficient Than Block Ciphers For Encrypting Data In Real-time, As They Do Not Require The Data To Be Divided Into Blocks. They Are Well-suited For Applications That Require Low Latency And Real-time Encryption, Such As Secure Communication Over The Internet Or In Wireless Networks.
Examples Of Stream Ciphers Include RC4 (Rivest Cipher 4), Salsa20, And ChaCha20. Stream Ciphers Are Often Used In Combination With Other Encryption Techniques, Such As A Message Authentication Code (MAC) Or A Hash Function, To Provide Additional Security And To Ensure The Authenticity And Integrity Of The Encrypted Data.
A Substitution Cipher Is A Type Of Encryption Technique Where Each Letter Or Symbol In The Plaintext Is Replaced By Another Letter Or Symbol To Form The Ciphertext. The Mapping Between The Plaintext And Ciphertext Is Determined By A Fixed Key, Which Is Used To Encrypt And Decrypt The Data.
Substitution Ciphers Can Be Either Monoalphabetic Or Polyalphabetic, Depending On The Type Of Substitution Used. In A Monoalphabetic Substitution Cipher, Each Letter Of The Alphabet Is Replaced By Another Letter In A Consistent And Deterministic Way, Such As Replacing 'A' With 'Z', 'B' With 'Y', Etc. In A Polyalphabetic Substitution Cipher, Multiple Substitutions Are Used, Making It More Secure Than A Monoalphabetic Substitution Cipher.
Substitution Ciphers Are One Of The Earliest Forms Of Encryption And Are Relatively Simple To Implement, But Are Also Relatively Easy To Break, As Patterns In The Ciphertext Can Be Used To Determine The Underlying Plaintext.
Examples Of Substitution Ciphers Include The Caesar Cipher, The Atbash Cipher, And The Vigenère Cipher. Substitution Ciphers Are Considered To Be Relatively Weak Encryption Techniques, As They Can Be Easily Broken By Modern Encryption Algorithms And Techniques. They Are Typically Used For Educational Purposes Or As An Introduction To Cryptography.
A Transposition Cipher Is A Type Of Encryption Technique Where The Positions Of The Letters In The Plaintext Are Rearranged To Form The Ciphertext. The Rearrangement Of The Letters Is Determined By A Fixed Key, Which Is Used To Encrypt And Decrypt The Data.
In A Transposition Cipher, The Letters Of The Plaintext Are Rearranged In A Specific Order Determined By The Key, Such As Rearranging The Letters In Reverse Order, Shifting Them To The Right Or Left, Or Rearranging Them In A Specific Pattern. The Resulting Ciphertext Is A Rearranged Version Of The Plaintext, But The Letters Themselves Remain Unchanged.
Transposition Ciphers Are Relatively Simple To Implement, But Are Also Relatively Easy To Break, As Patterns In The Ciphertext Can Be Used To Determine The Underlying Plaintext. They Are Typically Used In Combination With Other Encryption Techniques, Such As Substitution Ciphers, To Provide Additional Security.
Examples Of Transposition Ciphers Include The Columnar Transposition Cipher, The Rail Fence Cipher, And The Route Cipher. Transposition Ciphers Are Considered To Be Relatively Weak Encryption Techniques, As They Can Be Easily Broken By Modern Encryption Algorithms And Techniques. They Are Typically Used For Educational Purposes Or As An Introduction To Cryptography.
A Hash Function Is A Mathematical Function That Takes An Input (or "message") And Returns A Fixed-size String Of Bytes. The Output Of The Hash Function Is Often Referred To As A "hash" Or A "message Digest".
The Hash Function Has Several Important Properties:
Deterministic: Given The Same Input, The Hash Function Will Always Produce The Same Output.
Irreversible: Given The Hash Value, It Is Computationally Infeasible To Determine The Original Input.
Fixed-Size Output: The Size Of The Hash Value Is Typically Small And Fixed, Usually 128 Or 256 Bits.
Collision-resistant: It Is Computationally Infeasible To Find Two Different Inputs That Produce The Same Hash Value (i.e., Hash Collisions).
Hash Functions Are Widely Used In Cryptography And Computer Science For Several Purposes, Including:
Digital Signatures: To Ensure The Integrity And Authenticity Of A Message, The Sender Can Compute The Hash Of The Message And Encrypt It With Their Private Key. The Recipient Can Then Use The Sender's Public Key To Verify That The Hash Of The Received Message Is The Same As The Decrypted Hash.
Password Storage: To Store Passwords Securely, The Hash Of The Password Is Stored Instead Of The Password Itself. When A User Logs In, The Entered Password Is Hashed And Compared To The Stored Hash.
Data Integrity: To Ensure That A Large Amount Of Data Has Not Been Tampered With, The Hash Of The Data Can Be Computed And Stored. Later, The Hash Of The Data Can Be Recomputed And Compared To The Stored Hash To Check If The Data Has Been Changed.
Some Common Hash Functions Include SHA-1, SHA-256, And SHA-3 (SHA Stands For Secure Hash Algorithm). The Hash Functions Used For Security Purposes Should Be Secure, Fast, And Efficient, And It Is Important To Choose A Hash Function That Is Appropriate For The Intended Use Case.
In Conclusion, Encryption Is A Critical Component Of Modern Computer Security And Is Used To Protect Sensitive Information From Unauthorized Access. There Are Many Types Of Encryption, Including Symmetric, Asymmetric, Block Ciphers, Stream Ciphers, Substitution Ciphers, And Transposition Ciphers. Each Type Of Encryption Has Its Own Advantages And Disadvantages And Is Suitable For Different Use Cases.
In Addition To Encryption, Hash Functions Play An Important Role In Ensuring The Integrity And Authenticity Of Data. They Are Used In A Variety Of Applications, Including Digital Signatures, Password Storage, And Data Integrity Checking.
It Is Important To Choose The Right Encryption Method And Hash Function For Each Use Case, As Well As To Implement Them Correctly, In Order To Ensure The Security Of Sensitive Information. With The Increasing Sophistication Of Cyber Attacks, It Is More Important Than Ever To Prioritize Encryption And Use It In A Manner That Maximizes Its Effectiveness.
Types Of Encryption, What Is An Encryption, Differ