 Blog's Page
Blog's Page
In Today’s Digital World, Ransomware Attacks Have Become One Of The Most Dangerous And Disruptive Cyber Threats Targeting Individuals, Businesses, And Critical Institutions Alike. Among The Many Ransomware Strains, REvil (also Known As Sodinokibi) Has Gained Infamy For Its Sophisticated Techniques, High-profile Attacks, And Large Ransom Demands. This Blog Post Delves Into The Origins Of REvil, How It Operates, Notable Incidents, And Tips To Protect Against Such Ransomware.
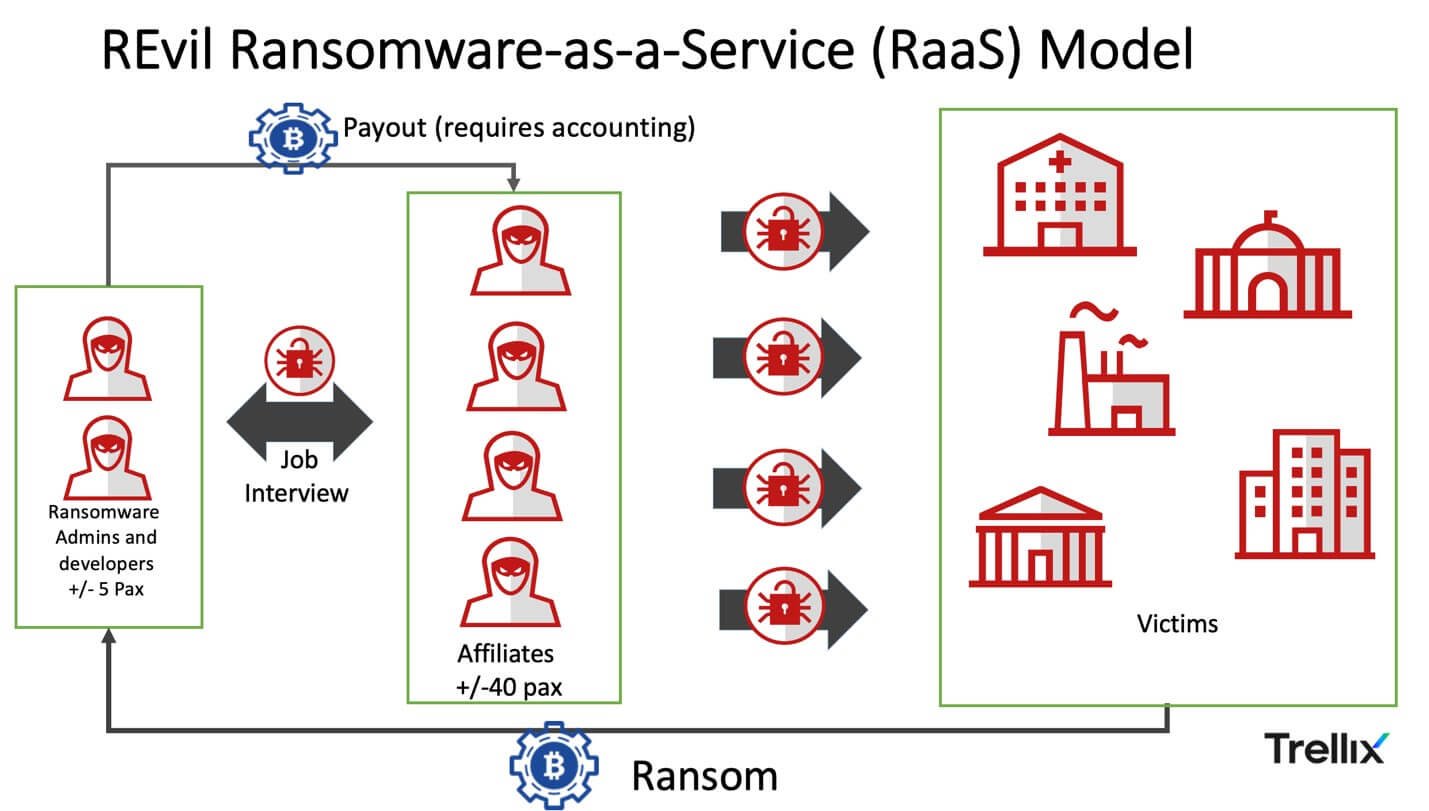
REvil Is A Type Of ransomware-as-a-service (RaaS) Malware First Identified In April 2019. It Operates By Encrypting Victims’ Files And Demanding Payment In Cryptocurrency (usually Bitcoin Or Monero) To Provide The Decryption Keys.
The Name REvil Is Believed To Be Derived From “Ransomware Evil.”
It Is Also Known As Sodinokibi In Cybersecurity Circles.
It Is Designed, Maintained, And Distributed By A Cybercriminal Group Offering The Ransomware As A Service To Affiliates.
Affiliates Infect Victims And Share A Percentage Of The Ransom With The Developers.
REvil Employs Several Sophisticated Tactics To Infiltrate Systems And Maximize Damage:
REvil Typically Gains Access To Victim Networks Through:
Exploiting Software Vulnerabilities (e.g., Unpatched Security Flaws).
Phishing Emails Containing Malicious Links Or Attachments.
Compromising Remote Desktop Protocol (RDP) With Brute Force Or Stolen Credentials.
Supply Chain Attacks Via Compromised Third-party Vendors.
Once Inside A Network, REvil:
Scans The Victim’s System And Connected Devices For Valuable Data.
Encrypts A Wide Range Of File Types Including Documents, Images, Databases, And System Files.
Uses Strong Encryption Algorithms Making Decryption Impossible Without The Private Key.
A Notable Characteristic Of REvil Is Its double Extortion Tactic:
Before Encrypting Files, REvil Steals Sensitive Data From Victims.
After Encryption, The Attackers Threaten To publish Or Sell The Stolen Data If The Ransom Is Not Paid.
This Adds Pressure On Victims To Pay Quickly, Even If They Have Backups.
Victims Receive A Ransom Note With Instructions On How To Pay, Typically Demanding Millions Of Dollars In Cryptocurrency.
REvil Has Been Involved In Many High-profile Ransomware Attacks Globally. Some Key Incidents Include:
JBS Foods, One Of The World's Largest Meat Processing Companies, Was Hit By REvil In May 2021.
The Attack Disrupted Operations In North America And Australia.
JBS Paid An $11 Million Ransom To Prevent Further Disruption And Data Exposure.
In July 2021, REvil Exploited Vulnerabilities In Kaseya’s VSA Software Used By Managed Service Providers (MSPs).
This Supply Chain Attack Infected Up To 1,500 Businesses Globally.
The Attackers Initially Demanded A $70 Million Ransom, One Of The Largest Ever.
The Attack Forced Many Businesses To Shut Down Operations Temporarily.
REvil Targeted Multiple Government Agencies, Healthcare Providers, Law Firms, And Educational Institutions.
Their Ransom Demands Have Ranged From Thousands To Millions Of Dollars.
REvil Attacks Cause Severe Consequences:
Encrypted Systems Halt Business Processes.
Critical Services, Especially In Healthcare Or Infrastructure, Face Downtime Risking Public Safety.
Ransom Payments Can Reach Millions.
Additional Costs Include System Restoration, Incident Response, Legal Fees, And Reputational Damage.
Stolen Data Can Include Personal Information, Trade Secrets, Or Confidential Communications.
Victims Face The Risk Of Public Exposure Or Blackmail.
Organizations May Violate Data Protection Regulations.
They Might Face Penalties For Inadequate Cybersecurity Measures.
While REvil Remains A Significant Threat, Organizations And Individuals Can Take Proactive Steps To Reduce Risk.
Keep Operating Systems, Applications, And Security Software Up To Date.
Apply Patches Promptly To Fix Known Vulnerabilities.
Use Strong, Unique Passwords For Remote Desktop Protocol (RDP) Accounts.
Enable Multi-factor Authentication (MFA).
Limit RDP Access Via VPNs Or Firewalls.
Educate Staff About Phishing Emails And Social Engineering Tactics.
Promote Vigilance When Opening Attachments Or Clicking Unknown Links.
Maintain Regular Backups Of Critical Data.
Store Backups Offline Or In Immutable Storage.
Test Recovery Procedures Frequently.
Limit Lateral Movement Within Networks By Segmenting Sensitive Systems.
Restrict User Privileges To The Minimum Necessary.
Use Endpoint Detection And Response (EDR) Solutions.
Employ Network Monitoring And Intrusion Detection Systems.
Develop And Rehearse Ransomware Response Plans.
Establish Communication Protocols And Roles.
If A System Is Compromised By REvil:
Isolate Infected Devices To Prevent Spread.
Do Not Pay Ransom Immediately—consult Cybersecurity Experts And Law Enforcement.
Report The Attack To Authorities Like CERT-In Or FBI.
Use Backups To Restore Systems If Available.
Conduct A Thorough Forensic Investigation To Identify Vulnerabilities.
REvil Ransomware Represents A Modern, Highly Organized Cybercrime Model That Combines Technical Prowess With Psychological Manipulation Through Double Extortion. Its High-profile Attacks Serve As A Wake-up Call For Organizations Worldwide To Prioritize Cybersecurity.
Investing In Layered Defenses, Employee Training, And Robust Incident Response Can Help Mitigate The Risk Posed By REvil And Other Ransomware Variants. In An Increasingly Digital And Connected World, Preparedness Against Ransomware Is Not Just IT’s Responsibility But A Critical Business Imperative.
REvil Ransomware, Delete REvil Ransomware, Remove REvil Ransomware, How To Remove REvil Ransomware, REvil Ransomware Removal, Get Rid Of REvil Ransomw