 Blog's Page
Blog's Page
Malicious Cryptomining—also Known As Cryptojacking—has Rapidly Become One Of The Most Widespread And Profitable Cyber Threats In The Digital Ecosystem. As Cryptocurrencies Continue To Evolve, Cybercriminals Have Shifted Significantly From Ransomware And Data Theft To Stealthy Cryptomining Attacks That Exploit Computing Resources Without The Knowledge Or Consent Of The Owner. Unlike Traditional Malware Threats That Seek To Damage Or Destroy Systems, malicious Cryptomining Focuses On Stealing Processing Power To Mine Cryptocurrencies Such As Monero, Bitcoin, And Ethereum.
This Long-form Guide Explains What Malicious Cryptomining Is, How It Works, How Attackers Infect Machines, The Symptoms Users Should Look For, And The Best Cybersecurity Practices To Prevent Such Attacks. The Article Also Explores How Businesses, Cloud Environments, And IoT Infrastructures Face Increased Risk From Cryptomining Malware.
Malicious Cryptomining Is The Unauthorized Use Of A Device’s Computing Resources To Mine Cryptocurrencies. It Can Occur On Virtually Any System, Including desktops, Servers, Cloud Instances, IoT Devices, Smartphones, And Web Browsers.
In Legitimate Cryptomining, A System Owner Voluntarily Uses Computing Resources To Solve Complex Mathematical Problems And Earn Cryptocurrency Rewards. However, In Malicious Cryptomining:
The Stealthy Nature Of Cryptomining Malware Makes It A Preferred Tool For Cybercriminals, Especially When Compared To Noisy Attacks Like Ransomware.
The Rise Of Malicious Cryptomining Can Be Attributed To Several Factors:
1. Low Risk, High Reward
Unlike Ransomware—which Immediately Alerts The Victim—cryptomining Malware Stays Hidden, Mining Cryptocurrency For Months Or Even Years. The Longer The Malware Stays Undetected, The More Money Attackers Earn.
2. No Need For Sensitive Data
Cryptojacking Does Not Rely On Stealing Financial Information, Login Credentials, Or Databases. As Long As The Victim’s CPU Power Is Available, The Attacker Can Profit.
3. Difficult To Detect
Cryptomining Malware Mimics Normal System Activity. Many Users Attribute System Slowdown To Aging Hardware, Not Malicious Activity.
4. Cloud Adoption
With More Companies Migrating To AWS, Azure, And Google Cloud, Attackers Have Access To massive, Scalable Computing Power when They Compromise Cloud Credentials.
5. IoT Device Vulnerabilities
IoT Devices Often Run Outdated Firmware And Weak Authentication, Making Them Easy Targets For Mining Bots.
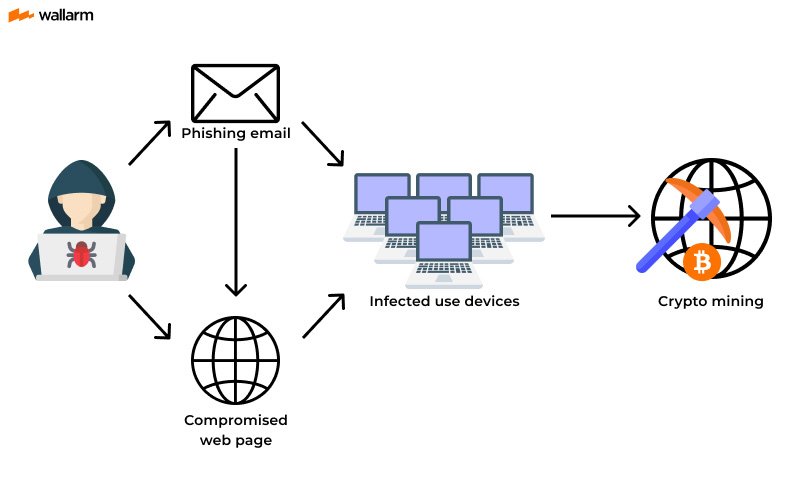
Malicious Cryptomining Typically Follows A Predictable Sequence:
Step 1: Initial Infection
The Attacker Compromises A System Using:
Step 2: Malware Installation
A Lightweight Cryptomining Payload Is Installed, Usually Disguised As A System Process Or Legitimate Application.
Step 3: Connection To A Mining Pool
The Malware Connects To A Remote Mining Pool Under The Attacker’s Control. Mining Pools Combine Processing Power From Multiple Infected Devices To Maximize Earnings.
Step 4: Resource Hijacking
The Malware Begins Mining Cryptocurrency By Consuming:
Step 5: Stealth Mechanisms
To Avoid Detection, The Malware:
1. Browser-Based Cryptomining
Attackers Embed Mining Scripts—often JavaScript Based—into Websites. When Users Visit The Site, Their CPU Starts Mining. Although Less Effective Today Due To Browser Protections, It Remains A Threat In Unpatched Systems.
2. File-Based Cryptomining Malware
This Involves Executable Malware Installed Through Phishing, Software Cracks, Or Malicious Downloads. It Runs Continuously In The Background And Is Harder To Detect.
3. Cloud Cryptomining
Compromising Cloud APIs Or Keys Enables Attackers To Spin Up Thousands Of Virtual Machines, Costing Organizations Millions In Cloud Bills.
4. Container-Based Cryptomining
Attackers Target Kubernetes Clusters, Unsecured Docker APIs, And Container Orchestration Platforms To Run Mining Containers.
5. IoT Cryptomining
Smart Devices Such As Routers, Smart TVs, CCTV Cameras, And Home Automation Systems Offer Easy Entry Points For Botnet-driven Mining Attacks.
Several Well-known Malware Families Dominate The Cryptojacking Landscape:
Most Of These Target Monero (XMR) because Of Its Privacy Features And CPU-friendly Mining Algorithm.
1. Significant System Slowdown
High CPU And GPU Usage Significantly Reduces Performance, Causing:
2. High Electricity Bills
Cryptomining Consumes Substantial Power, Leading To Increased Monthly Costs.
3. Overheating And Hardware Damage
Prolonged Mining Accelerates:
4. Business Downtime
For Enterprises, Cryptomining Malware Can Slow:
5. Cloud Billing Exploitation
In Cloud Environments, Cryptomining Can Cause:
6. Network Congestion
Constant Communication With Mining Pools Consumes Bandwidth And Affects Corporate Productivity.
Organizations And Individuals Should Monitor For The Following Indicators:
Monitoring Tools Such As Task Manager, Activity Monitor, Top/htop, Nagios, Zabbix, And Cloud Monitoring Dashboards Often Reveal These Anomalies.
Cryptojacking Spreads Through Various Infection Vectors:
1. Phishing Campaigns
Attackers Deliver Mining Payloads Through Malicious Email Attachments Or Links.
2. Software Cracks And Pirated Tools
Cracks, Activators, And Pirated Installers Often Bundle Mining Malware.
3. Exploiting Unpatched Systems
Older Systems Vulnerable To EternalBlue, CVE-2019-19781, Log4j, And Other Exploits Are Common Entry Points.
4. Compromised Websites
Drive-by Mining Scripts Run Automatically When Victims Load A Compromised Webpage.
5. Misconfigured Cloud Services
Publicly Exposed S3 Buckets, Docker APIs, Or Kubernetes Dashboards Allow Attackers To Deploy Mining Tools.
6. Botnets
Botnets Like Mirai Have Been Extended To Include Cryptomining Modules.
Effective Prevention Requires A Combination Of endpoint Security, Cloud Hardening, And User Awareness.
1. Use Robust Endpoint Protection
Install Reputable Antivirus And Anti-malware Tools Such As:
Modern Security Tools Can Detect Cryptomining Signatures And Block Suspicious Processes.
2. Patch Operating Systems And Software
Apply Regular Updates To:
Patching Eliminates Vulnerabilities Exploited By Cryptomining Malware.
3. Secure Cloud Infrastructure
Follow Cloud Security Best Practices:
4. Implement Browser Security Controls
Use Browser Features Or Extensions That Block:
Examples Include NoCoin, UBlock Origin, And MinerBlock.
5. Monitor Network And System Performance
Security Teams Should Deploy Monitoring Tools To Detect:
6. Disable Unnecessary Services
Turn Off:
This Reduces Attack Surfaces.
7. Enforce Strong Password Policies
Use Strong, Unique Passwords And Enable Multi-factor Authentication To Prevent Unauthorized Access.
8. Educate Employees And Users
User Awareness Is Crucial For Avoiding:
9. Deploy Web Application Firewalls (WAF)
WAFs Block Drive-by Cryptomining Scripts Embedded In Compromised Websites.
1. Incident Response Steps
If Cryptomining Malware Is Detected:
2. Cloud-Specific Response
For Cloud Mining Attacks:
The Threat Landscape For Cryptojacking Is Expected To Evolve In The Following Ways:
1. AI-Powered Malware
Attackers Will Use AI To Evade Detection More Effectively.
2. Mining On GPU-Powered AI Clusters
As Businesses Deploy AI Servers, Attackers Will Attempt To Exploit GPUs With Massive Parallel Processing Capabilities.
3. Increased Cloud Exploits
Cloud-based Cryptojacking Is Projected To Become The Most Profitable Form Of This Cybercrime.
4. Targeting Of Edge Devices
Routers, POS Devices, Industrial IoT Sensors, And Smart Home Ecosystems Will See Increased Attacks.
5. Covert Mining In Mobile Apps
Fake Apps On Third-party Stores May Run Mining Scripts In The Background.
Malicious Cryptomining Is A Silent Yet Powerful Cyber Threat Impacting Individuals, Enterprises, Cloud Infrastructures, And IoT Ecosystems. While It May Not Steal Personal Data Directly, The Long-term Financial, Operational, And Hardware Damage Caused By Cryptomining Malware Is Significant. By Implementing Strong Cybersecurity Practices—such As Endpoint Protection, Cloud Hardening, Patching Routines, And Employee Education—organizations Can Greatly Reduce The Risks Associated With Cryptojacking.
Staying Informed And Proactive Is The Key To Protecting Your Digital Environment From The Constantly Evolving World Of Malicious Cryptomining.
Malicious Cryptomining, Malware, Cybersecurity, Malicious Program