 Blog's Page
Blog's Page
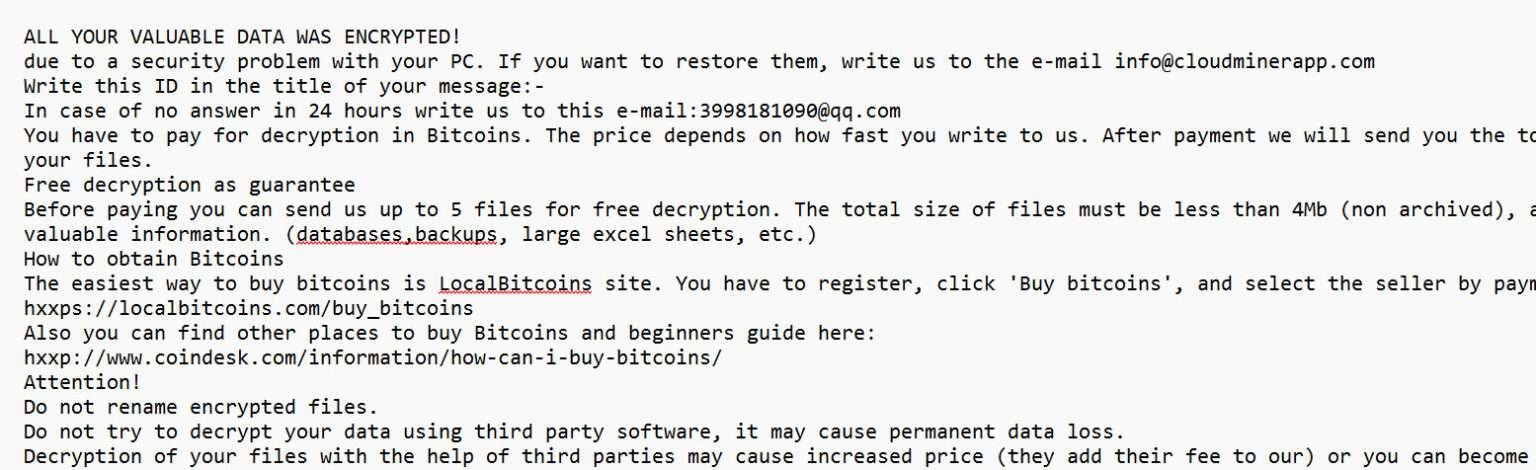
JETT Ransomware Is A Type Of Malicious Software Designed To Encrypt Files On A Victim’s Computer And Demand A Ransom Payment In Exchange For A Decryption Key. It Typically Infiltrates Systems Through Phishing Emails, Malicious Attachments, Or Vulnerabilities In Outdated Software.
Once Installed, JETT Encrypts Valuable Files, Appending A Distinct Extension—usually “.jett”—to Them. It Then Drops A Ransom Note, Instructing The Victim To Pay A Ransom In Cryptocurrency, Such As Bitcoin, To Recover Access To Their Files. The ransomware May Also Attempt To Disable Security Software, Delete Backups, And Spread Laterally Across Networks.
JETT Ransomware Primarily Targets Windows Systems And Poses A Significant Threat To Both Individuals And Organizations. Security Experts Strongly Advise Against Paying The Ransom, As It Does Not Guarantee Data Recovery And Encourages Further Criminal Activity. Instead, Victims Should Isolate The Infected Machine, Report The Incident, And Use Backup Solutions Or Professional Cybersecurity Tools To Attempt Data Recovery.
JETT Ransomware Infects Systems Primarily Through Deceptive And Malicious Methods Aimed At Tricking Users Or Exploiting Vulnerabilities. The Most Common Infection Vectors Include:
Phishing Emails: These Emails Often Contain Malicious Attachments Or Links Disguised As Legitimate Content. When Opened, They Download And Execute The Ransomware Payload.
Malicious Attachments: Infected Word, Excel, Or PDF Documents With Embedded Macros Can Trigger The Ransomware Once A User Enables Content.
Drive-by Downloads: Visiting Compromised Or Malicious Websites Can Silently Download JETT Ransomware If The Browser Or Plugins Are Unpatched.
Cracked Software And Keygens: Downloading Pirated Software Or Fake Activation Tools May Bundle JETT Ransomware With The Installation Files.
Exploiting Vulnerabilities: Unpatched Operating Systems And Applications Can Be Targeted Through Remote Desktop Protocol (RDP) Attacks Or Software Exploits.
Once Active, JETT Ransomware Encrypts Files, Disables Security Tools, And Demands Ransom, Often Spreading Across Networks For Wider Impact.
The JETT Ransomware Encryption Process Is A Systematic And Stealthy Operation Designed To Lock Victims Out Of Their Data And Extort Payment. Here’s How It Typically Works:
Execution And Initialization: Once The Malicious Payload Is Executed—often Via A Phishing Email Or Exploit—the Ransomware Runs In The Background, Avoiding Detection.
System Scan: It Scans The Infected System And Connected Drives (including Network Shares) For Targeted File Types Such As Documents, Images, Videos, Databases, And Backups.
File Encryption: Using Strong Encryption Algorithms (typically AES For File Data And RSA For Key Protection), It Encrypts Files And Appends A Unique Extension, Usually “.jett”.
Ransom Note Creation: A Ransom Note (e.g., readme.txt Or HOW_TO_RECOVER.txt) Is Dropped In Affected Directories, Instructing Victims To Pay Cryptocurrency To Receive A Decryption Key.
Cleanup And Persistence: It May Delete Shadow Copies And Backups, Disable Recovery Tools, And Modify Registry Entries For Persistence, Making Recovery More Difficult Without Paying The Ransom.
Detecting An Ongoing JETT Ransomware Attack Early Can Significantly Reduce Its Impact. Here Are Key Signs And Methods For Detection:
Unusual System Activity: Sudden System Slowdowns, High CPU Or Disk Usage, Or Unknown Processes (e.g., Suspicious .exe Files) Running In Task Manager.
File Renaming And Extensions: Files Across The System Quickly Being Renamed Or Appended With The “.jett” Extension.
Ransom Note Appearance: Ransom Notes Like HOW_TO_RECOVER.txt Or Similar Appearing In Multiple Directories.
Disabled Security Tools: Antivirus Or Endpoint Protection Tools Being Unexpectedly Turned Off Or Unresponsive.
Blocked File Access: Users Receive Errors When Trying To Open Previously Accessible Files, Or Files Appear Corrupted.
Unusual Network Behavior: Spikes In Outbound Traffic, Especially To Unfamiliar IP Addresses Or TOR Networks.
Log Analysis Alerts: Security Information And Event Management (SIEM) Tools May Flag Suspicious Logins, Privilege Escalation, Or Abnormal File Access Patterns.
Early Detection Tools Like EDR (Endpoint Detection And Response) Solutions Can Help Flag Such Anomalies For Immediate Action.
If You Become Infected With JETT Ransomware, It's Critical To Act Quickly And Carefully To Minimize Damage And Increase The Chances Of Recovery. Here's What To Do:
Isolate The Infected System: Immediately Disconnect The Infected Device From The Internet And Internal Networks To Prevent The Ransomware From Spreading.
Do Not Pay The Ransom: Paying Does Not Guarantee File Recovery And Encourages Further Criminal Activity. It Also Marks You As A Potential Target For Future Attacks.
Identify The Ransomware: Confirm It's JETT Ransomware By Examining The Ransom Note And File Extensions. Use Online Tools Like ID Ransomware For Verification.
Notify Authorities: Report The Incident To Law Enforcement Or A Cybercrime Agency (e.g., FBI IC3 Or Local CERT).
Use Backups: If Available, Restore Your Files From A Clean And Secure Backup After Ensuring The System Is Fully Cleaned.
Clean The System: Use Trusted Antivirus Or Anti-malware Tools To Remove The Ransomware. A Complete System Wipe May Be Necessary In Severe Cases.
Consult Cybersecurity Professionals: For Large-scale Infections Or Sensitive Data, Involve Experts For Thorough Analysis, Containment, And Recovery.
Review And Strengthen Security: Patch Vulnerabilities, Update Software, And Revise Security Protocols To Prevent Future Attacks.
To Remove JETT Ransomware And Recover Files, Follow These Steps:
Isolate The Infected System: Disconnect The Infected Device From The Network And The Internet To Prevent The Ransomware From Spreading.
Use Antivirus Or Anti-Malware Tools: Run A Full System Scan With Up-to-date Antivirus Or Anti-malware Software To Remove The Ransomware. Tools Like Malwarebytes Or Bitdefender Can Detect And Eliminate JETT Ransomware.
Restore From Backup: If You Have Secure, Up-to-date Backups Stored Offline Or In The Cloud, Restore Your Files From There. Ensure The Ransomware Is Fully Removed Before Restoring To Avoid Reinfection.
Decrypt Files (if No Backup): If You Don't Have A Backup, Do Not Pay The Ransom. Seek Out Decryption Tools. Some Security Vendors Or Online Communities Like No More Ransom May Offer Free Tools For Specific Ransomware Strains.
Reinstall Operating System: In Some Cases, A Clean OS Installation Is Necessary To Ensure Complete Removal Of The Ransomware.
Improve Security: After Recovery, Update Software, Use Strong Passwords, And Deploy Endpoint Protection To Prevent Future Infections.
Preventing JETT Ransomware Infections Requires A Multi-layered Cybersecurity Approach. Here Are Key Prevention Strategies:
Email Security: Use Advanced Email Filtering To Block Phishing Emails, Malicious Attachments, And Suspicious Links—common Entry Points For JETT Ransomware.
Regular Updates: Keep Your Operating System, Software, Browsers, And Plugins Fully Updated To Patch Known Vulnerabilities.
Antivirus & EDR: Deploy Reputable Antivirus And Endpoint Detection And Response (EDR) Solutions With Real-time Protection And Behavioral Analysis.
User Awareness: Train Employees And Users To Recognize Phishing Attempts And Avoid Clicking On Suspicious Links Or Downloading Untrusted Files.
Access Controls: Apply The Principle Of Least Privilege—limit Admin Rights And Restrict RDP Access With Strong Passwords And Two-factor Authentication (2FA).
Data Backups: Regularly Back Up Important Data To Secure Offline Or Cloud Storage, And Test Recovery Procedures Frequently.
Network Segmentation: Divide Networks Into Zones To Contain Infections And Prevent Lateral Movement.
Disable Macros: Turn Off Macros In Office Files Unless Absolutely Necessary.
By Implementing These Measures, Organizations Can Significantly Reduce The Risk Of JETT Ransomware Infections.
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:









If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
JETT Ransomware, Remove JETT Ransomware, Delete JETT Ransomware, Uninstall JETT Ransomware, Get Rid Of JETT Ransomware, JETT Ransomware Removal