 Blog's Page
Blog's Page
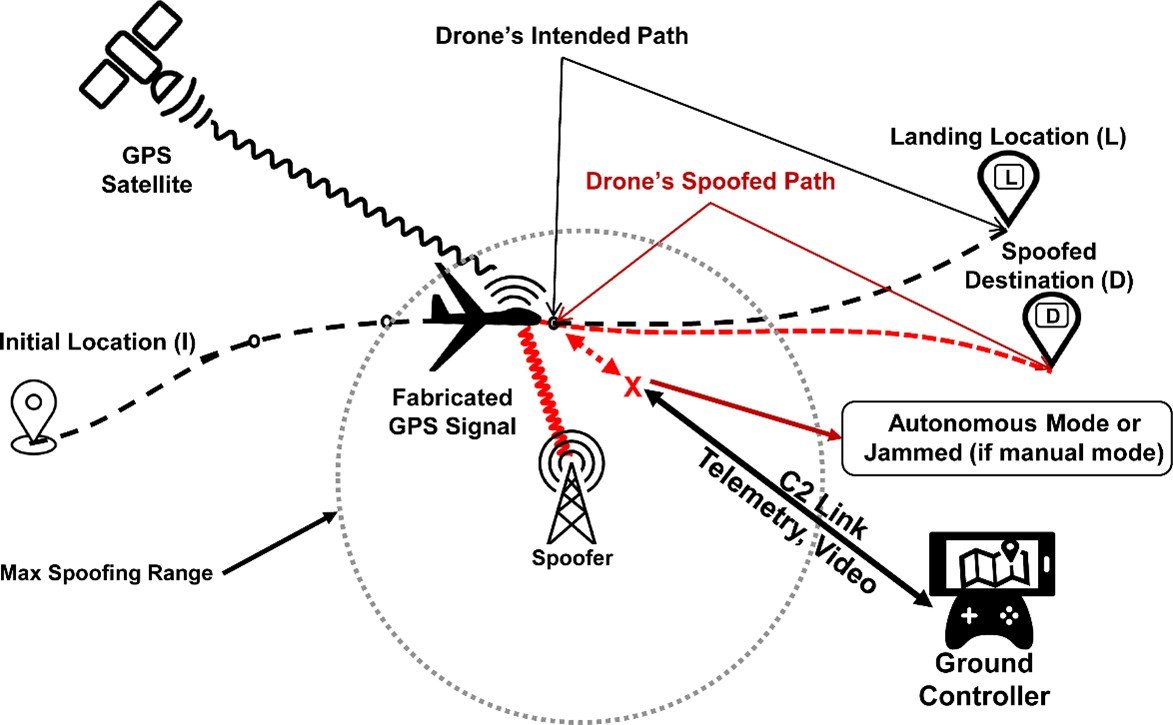
Introduction
Global Positioning System (GPS) Spoofing Is The Deliberate Transmission Of Counterfeit GNSS (Global Navigation Satellite System) Signals To Deceive A Receiver About Its Position, Velocity, Or Time. Unlike Jamming, Which Denies Service By Overwhelming Receivers With Noise, Spoofing Provides Plausible — But False — Navigation Data. Spoofing Has Attracted Attention Across Academia, Industry And Policy Because Modern Society Depends Heavily On GNSS For Navigation, Timing, And Critical Infrastructure.
High-level Technical Overview
GNSS Receivers Compute Position And Time By Measuring The Arrival Times Of Signals From Multiple Satellites. A Spoofing Attack Works By Presenting A Fake Set Of Signals That A Victim Receiver Treats As Authentic, Causing It To Compute An Incorrect Solution. Conceptually, Spoofing Exploits Two Facts: Receivers Often Trust Signals They Can Lock Onto, And Many Consumer Receivers Perform Limited Checks Of Signal Authenticity And Plausibility.
From A Study Perspective, The Important Technical Concepts Are: Satellite Ephemeris (where Satellites Are Supposed To Be), Signal Structure And Modulation (what Receivers Decode), Time-of-arrival And Pseudorange Calculations (how Ranges Are Derived), And The Receiver’s Internal Filters (e.g., How It Merges New Measurements With Prior Estimates). Spoofed Signals Can Be Designed To Be Consistent With Expected Satellite Geometry And Timing, Thereby Slowly “pulling” The Receiver Away From The True Solution In A Way That Is Harder To Detect Than Abrupt Jumps.
Types Of Spoofing Attacks (categorical, Not Procedural)
Simple/fixed-offset Spoofing: Providing A Consistent False Offset To Position/time. Often The Easiest To Conceptualize.
Meaconing/relay Attacks: Rebroadcasting Legitimate GNSS Signals After A Delay Or From A Different Location To Create Misleading Timing/positional Information.
Sophisticated Adaptive Spoofing: Gradually Changing The Spoofed Signals To Mimic Normal Dynamics, Minimizing Sudden Anomalies And Bypassing Simple Plausibility Checks.
Record-and-replay Variants: Capturing Real GNSS Signals And Replaying Them With Controlled Timing Offsets To Manipulate Receivers.
Motivations & Impacts
Safety-critical Navigation: Maritime, Aviation, And Autonomous Vehicles Can Be Misled, Leading To Collisions, Groundings, Or Loss Of Situational Awareness.
Timing Attacks: GNSS Provides Precise Time For Telecoms, Financial Exchanges, And Power-grid Synchronization. Altered Time Can Cause Data Corruption, Outages, Or Financial Errors.
Privacy & Criminal Misuse: Attackers May Try To Mask Locations Of Assets, Conceal Illicit Movements, Or Create Plausible False Logs.
Military & Strategic Uses: Spoofing Is An Instrument Of Electronic Warfare And Deception.
Research & Testing: Researchers Use Controlled Spoofing In Labs To Evaluate Receiver Resilience (when Ethically And Legally Authorized).
Notable Consequences
Real-world Consequences Reported In Literature Include Maritime Vessels Deviating From Shipping Lanes, Denial Of Critical Timing To Base Stations, And Demonstrations Where Consumer Drones Were Induced To Land. These Underscore That Spoofing Can Have Tangible, Sometimes Dangerous, Real-world Effects Whenever GNSS Is A Primary Source Of Navigation Or Timing.
Detection Strategies
Signal-level Monitoring: Look For Inconsistencies In Signal Strength, Doppler Shifts, Unexpected Handshake Behavior, Or Abrupt Changes In Satellite Geometry. Receivers That Track Low-level Observables Have More Options To Detect Anomalies.
Consistency Checks: Cross-validate GNSS-derived Position/time Against Independent Sensors — Inertial Measurement Units (IMUs), Odometry, Barometric Altimeters, Visual Odometry, Or Cellular/Wi-Fi Positioning. Large, Unexplained Discrepancies Trigger Alerts.
Multi-constellation & Multi-frequency Use: Using Multiple GNSS Constellations And Frequencies Makes It Harder For An Attacker To Forge A Complete And Coherent Set Of Signals, Though It Is Not A Panacea.
Cryptographic Authentication: Some GNSS Systems Now Provide Or Are Planning Authenticated Signals; Verifying Cryptographic Signatures Prevents Many Classes Of Spoofing. Note: Availability Varies Across Systems And Receiver Support.
Networked Verification: Receivers Can Compare Their Solutions Via Secure Networks To Detect Outliers (useful For Fleets Or Infrastructure).
Anomaly Scoring & Machine Learning: Statistical Models Can Learn Normal Signal Behavior And Flag Deviations, But These Must Be Careful To Avoid False Positives In Benign But Unusual Conditions.
Mitigation & Hardening
Design For Redundancy: Critical Systems Should Not Rely Solely On GNSS; Ensure Alternative Navigation/timing Sources And Graceful Degradation Modes.
Operational Procedures: For Manned Operations, Train Operators To Recognise GNSS Anomalies And Follow Fallback Procedures. For Automated Systems, Define Safe States To Enter Upon Suspected Spoofing.
Regulatory & Industry Standards: Certification And Testing Regimes For Safety-critical Receivers Should Require Spoofing-resilience Evaluations.
Secure GNSS Adoption: Encourage Uptake Of Authenticated GNSS Signals And Firmware Updates For Receivers To Support Them.
Monitoring & Incident Response: Maintain GNSS Interference/spoofing Monitoring Stations And Incident Reporting Channels So Anomalies Can Be Correlated And Addressed At Scale.
Ethics, Legality And Research Conduct
Deliberate Spoofing Of Operational GNSS Services Can Be Illegal And Dangerous. Ethical Research Uses Controlled Testbeds, Isolated Shielded Ranges, Or Simulation, And Obtains Regulatory Approvals And Coordination With Spectrum Authorities And Affected Parties. When Studying Spoofing, Emphasize Defensive Outcomes, Avoid Publishing Step-by-step Exploit Techniques That Would Meaningfully Lower Barriers For Malicious Actors, And Follow Responsible Disclosure Practices If Vulnerabilities Are Found In Deployed Systems.
Open Research Directions
Robust Authentication Mechanisms That Balance Security With Receiver Cost And Backwards Compatibility.
Lightweight On-device Detection Algorithms Suitable For Consumer Hardware With Limited Resources.
Sensor Fusion Techniques That Gracefully Handle Degraded Or Conflicting Inputs.
System-level Resilience Models That Quantify Risk For Entire Infrastructure (telecom, Power, Transport) When GNSS Is Compromised.
Policy And Economics Research Into Incentives For Operators To Adopt Resilient Practices And For Authorities To Monitor GNSS Integrity.
Conclusion
GPS/GNSS Spoofing Is A Real And Evolving Threat That Exploits Trust In Satellite-based Signals. Effective Mitigation Combines Technical Defenses (signal Authentication, Anomaly Detection, Redundancy), Engineering Practices (fail-safe Modes, Sensor Fusion), Policy Measures (standards, Monitoring) And Ethical Research. For Anyone Studying The Topic, Focus On Understanding The Underlying Measurement Principles, System Dependencies, And Defensive Techniques — And Always Avoid Operational Details That Could Facilitate Harmful Misuse.
In Today’s World, GPS (Global Positioning System) Technology Is Everywhere — From Navigation Apps And Delivery Tracking To Banking And Emergency Services. But What If Someone Could manipulate Your GPS Location Without You Knowing?
That’s Where GPS Spoofing Comes In — A Form Of Cyberattack That Tricks Devices Into Believing They’re Somewhere Else. While It Sounds Like Something That Only Affects Soldiers Or Spies, GPS Spoofing Can Have real Consequences For Ordinary People Too.
GPS Spoofing Is A Technique Where Fake Satellite Signals Are Broadcast To Mislead GPS Receivers. Your Smartphone, Car, Or Smartwatch Relies On Signals From Satellites To Calculate Your Location And Time. A Spoofer Sends Counterfeit Signals That Appear Real, Making Your Device Calculate A false Position Or Time.
Unlike GPS Jamming — Which Blocks Signals — Spoofing feeds Fake Data. This Means Your Phone Still “works,” But It’s Showing You The Wrong Place. The Scariest Part? You Might Not Even Notice.
Most People Use Google Maps, Apple Maps, Or Waze To Get Around. If Spoofed Signals Are Present, These Apps Can Lead You Astray.
You Might Take The Wrong Route, Miss Turns, Or End Up Miles Away From Your Destination.
Ride-sharing Drivers On Apps Like Uber Or Ola May Appear In Fake Locations, Leading To Pickup Confusion.
Delivery Apps Such As Zomato, Swiggy, Or Amazon May Show Incorrect Driver Locations Or Delivery Times.
Even Small Errors In GPS Positioning Can Waste Time, Fuel, And Patience — Showing How Deeply Everyday Navigation Depends On Signal Integrity.
Your smartphone Uses GPS Not Only For Maps But Also For Several Hidden Background Functions. A Spoofed Location Can Affect:
Photo Location Tags: Images Saved With Wrong Geotags Confuse Memories And Social Media Posts.
Find My Phone Features: If Someone Spoofs The Signal, Your Lost Phone Could Appear To Be Miles Away.
Fitness And Travel Apps: Running Or Cycling Routes May Record Inaccurate Distances Or Fake Achievements.
Spoofing Apps Are Sometimes Used By Gamers To “teleport” In Location-based Games Like Pokémon GO — But This Opens The Door To malicious Uses When Misused By Attackers.
GPS Spoofing Can Cause Serious Disruptions In gig-economy Platforms:
Drivers May Appear Closer Than They Really Are To Attract More Customers.
Fraudsters Can Simulate Fake Trips Or Rides To Exploit Payment Systems.
Customers May Face Delays, Wrong Deliveries, Or Failed Pickups.
For Both Drivers And Users, Spoofed GPS Signals Lead To loss Of Trust And Financial Waste.
You Might Wonder What GPS Has To Do With Banking. The Answer: time Synchronization.
Banks, ATMs, And Financial Servers Rely On The Precise Timing That GPS Provides. If Attackers Spoof This Timing Information, It Can Cause:
Transaction Errors Or Mismatched Timestamps
Payment Network Delays
Data Synchronization Issues Across Servers
Even A Small GPS Timing Error Can Ripple Through Global Financial Systems, Affecting millions Of Digital Transactions.
When You Call 112 (in India) Or 911 (in The U.S.), Dispatchers Depend On GPS To Pinpoint Your Location. If GPS Spoofing Occurs, Emergency Responders Could Be sent To The Wrong Address.
This Delay Can Be Catastrophic In Medical, Fire, Or Criminal Emergencies.
Additionally, Apps That Track Women’s Safety Or Children’s Locations May Show false Positions, Making It Harder For Families Or Authorities To Respond Quickly.
Many People Use drones For Photography, Farming, And Recreation. Drones Depend Heavily On GPS For Stability And Navigation. Spoofing Attacks Can Cause Drones To:
Fly Off Course Or Crash
Land In Unauthorized Or Unsafe Areas
Be “hijacked” By Attackers Faking Location Data
Drone Enthusiasts, Content Creators, And Even Farmers Using Precision Agriculture Tools Are Increasingly Aware Of GPS Spoofing Risks.
Modern Vehicles Rely On GPS Not Only For Maps But Also For advanced Driver-assistance Systems (ADAS), Theft Tracking, And Navigation Safety.
Spoofed Signals Can Result In:
Wrong Directions During Driving
Incorrect Vehicle-tracking For Owners Or Law Enforcement
Malfunctioning Autonomous Systems
If Your Car’s Tracker Shows It’s Parked Miles Away — When It’s Not — GPS Spoofing Could Be One Possible Reason.
Commercial Airplanes, Ships, And Cargo Fleets All Depend On GPS For Navigation And Tracking. While Professionals Have Backup Systems, Spoofing Can Still Cause:
Temporary Loss Of Location Awareness
Flight Or Route Deviations
Increased Travel Time Or Fuel Consumption
Passengers May Not Notice, But GPS Spoofing Can Indirectly Lead To flight Delays Or Maritime Route Detours, Affecting Schedules And Logistics Chains.
You Might Be Surprised To Know That cell Towers And Internet Servers Use GPS For Time Synchronization. Spoofed GPS Signals Can Cause:
Temporary Mobile Network Outages
Internet Lag Or Desynchronization
Misaligned Data In Cloud Applications
That’s Why, When GPS Disruptions Happen, People May Experience Slow Connections Or Dropped Calls — Even If They’re Nowhere Near A Spoofing Source.
In The Age Of Smart Cities, Devices Such As delivery Robots, Connected Vehicles, And Streetlights Use GPS-based Automation. Spoofing Can Cause Them To Malfunction, Creating:
Traffic Signal Errors
Robot Delivery Delays
Energy Inefficiency In Smart Lighting Systems
For Ordinary Users, This Can Mean Delayed Deliveries, Confusing Navigation Apps, Or Even Safety Hazards In Public Spaces.
GPS Spoofing Can Be Used By Criminals To hide Their Real Locations Or Frame Innocent People.
Someone Could Fake A GPS Location To Commit Fraud.
Thieves May Spoof Vehicle Trackers To Mislead Owners.
Fraudsters Can Fake Location-based App Data To Exploit Location-sensitive Services.
For The Average User, This Raises Privacy Concerns: How Do You Trust Your Location Data If It Can Be Faked?
Beyond Direct Technical Effects, GPS Spoofing Causes economic And Social Ripples:
Lost Fuel And Time Due To Misnavigation
Delayed Online Orders And Taxi Rides
Erosion Of Trust In Digital Navigation Systems
The Global Economy Depends On Precise Positioning And Timing — And Spoofing Introduces Costly Inefficiencies That Affect Consumers Indirectly Through Higher Prices Or Slower Services.
While You Can’t Control Satellite Signals, You Can Take Steps To Reduce The Risks:
Keep Devices Updated: Modern Smartphones Use Multiple GNSS Constellations (GPS, GLONASS, Galileo, BeiDou), Making Spoofing Harder.
Cross-check Your Location: Use Wi-Fi Or Cell Tower-based Maps To Confirm GPS Accuracy.
Avoid Fake Location Apps: Many Free “spoofing Apps” Can Compromise Your Security.
Use A-GPS (Assisted GPS): It Combines Satellite Data With Network Information For Better Accuracy.
Choose Trusted Devices: Newer Cars, Drones, And Wearables Have Built-in Spoofing Detection Or Authentication Mechanisms.
For Businesses, Using multi-sensor Navigation (GPS + IMU + Visual Tracking) And authenticated GNSS Signals Provides Better Resilience.
Governments And Researchers Are Developing authenticated GPS Signals That Include Cryptographic Verification, Making Spoofing Nearly Impossible. Until These Become Mainstream, Awareness Remains The Best Defense.
Public Monitoring Systems Can Also Help Detect Spoofing Regions And Warn Users In Real Time — Similar To Weather Or Air-quality Alerts.
GPS Spoofing Is No Longer A Far-fetched Hacker Story — It’s A real Threat That Can Disrupt Daily Life In Subtle But Significant Ways. Whether It’s Your Food Delivery Arriving Late, Your Phone Showing The Wrong Location, Or Your Bank Transaction Failing, Spoofing Can Touch Almost Everyone In The Modern World.
For Normal Users, The Key Takeaway Is Simple: stay Alert, Use Verified Apps, Update Your Devices, And Double-check Location Accuracy. As Technology Advances, Protecting The Integrity Of GPS Signals Is Just As Crucial As Securing Our Data Online.
GPS Spoofing Impact, GPS Spoofing Risks, GPS Spoofing On Smartphones, GPS Spoofing In Daily Life, GPS Manipulation Threats, GPS Security Awareness, GN