 Blog's Page
Blog's Page

BHO Stands For "Browser Helper Object". It Is A Type Of Plug-in Or Extension That Can Be Installed In Web Browsers, Such As Internet Explorer, To Add Additional Functionality Or Modify The Behavior Of The Browser.
BHOs Were First Introduced With Internet Explorer 4, And They Are Implemented As Dynamic Link Libraries (DLLs) That Are Loaded By The Browser At Startup. BHOs Can Perform A Wide Range Of Functions, Such As Providing Additional Toolbars, Integrating With Other Software, Blocking Or Redirecting Web Content, And Monitoring User Activity.
BHOs Have Been The Subject Of Some Controversy In The Past, As They Can Be Used For Malicious Purposes, Such As Collecting User Data Or Injecting Unwanted Ads. Some Security Experts Advise Against Using BHOs, Or Recommend That Users Be Cautious When Installing Them, As They Can Potentially Pose A Security Risk.
BHOs Are Specific To Internet Explorer And Are Not Used In Other Web Browsers, Such As Chrome Or Firefox, Which Use Different Extension Mechanisms.
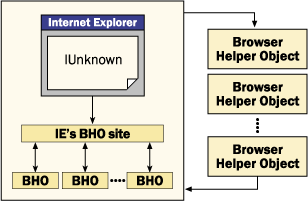
A Browser Helper Object (BHO) Is A Type Of Plug-in Or Extension That Can Be Installed In Internet Explorer (IE) To Add Additional Functionality Or Modify The Behavior Of The Browser. Here Is An Overview Of How BHOs Work:
DLL Registration: A BHO Is Implemented As A Dynamic Link Library (DLL) That Must Be Registered With The Windows Operating System. The DLL Provides The Code And Resources Needed To Implement The BHO's Functionality.
Automatic Loading: Once The DLL Is Registered, Internet Explorer Will Automatically Load The BHO When It Is Launched. The BHO Is Loaded Into The Same Process As IE, Which Allows It To Access And Modify The Browser's Internal Data Structures.
BHO Initialization: Once The BHO Is Loaded, It Will Perform Any Necessary Initialization Steps, Such As Registering Event Handlers Or Modifying The Browser's User Interface.
Browser Integration: The BHO Can Interact With The Browser In A Number Of Ways, Such As By Injecting Additional Code Into Web Pages, Intercepting And Modifying HTTP Requests And Responses, Or Modifying The Browser's User Interface.
Data Collection And Processing: The BHO Can Collect Data From The Browser, Such As User Activity Or Browsing History, And Process It In Various Ways. This Data Can Be Used To Provide Additional Functionality, Such As Customized Search Results Or Targeted Advertising.
User Interaction: The BHO Can Interact With The User In Various Ways, Such As By Displaying Additional Toolbars, Dialogs, Or Notifications.
Overall, BHOs Provide A Way To Extend The Functionality Of Internet Explorer And Integrate It With Other Software And Services. However, As BHOs Can Potentially Pose A Security Risk, Users Should Exercise Caution When Installing And Using Them, And Be Aware Of The Potential Risks And Consequences.
The Key Features Of Browser Helper Objects (BHOs) Are:
Customization: BHOs Allow Developers To Customize The Behavior Of The Web Browser By Adding New Features Or Modifying Existing Ones. For Example, A BHO Can Add A New Toolbar, Block Pop-ups, Or Provide Additional Search Capabilities.
Integration: BHOs Are Integrated Into The Web Browser's Address Space And Can Interact With Other COM Objects And The Browser Itself. This Allows BHOs To Perform Various Actions, Such As Capturing Keystrokes, Injecting Code Into Web Pages, Or Modifying The Browser's Settings.
Event Handling: BHOs Can Respond To Events Triggered By The Web Browser, Such As Page Load Or Navigation Events. This Allows BHOs To Perform Actions Or Modify The Behavior Of The Browser In Response To Specific Events.
Cross-site Scripting: BHOs Can Inject Code Into Web Pages That The User Visits, Which Can Potentially Lead To Cross-site Scripting (XSS) Attacks If The Injected Code Is Malicious.
Security Implications: BHOs Can Pose Security Risks If They Are Not Implemented Properly Or If They Are Used For Malicious Purposes. For Example, A Malicious BHO Can Capture The User's Keystrokes, Steal Sensitive Information, Or Modify The User's Browser Settings Without Their Knowledge Or Consent.
It Is Important To Note That The Use Of BHOs Has Declined In Recent Years Due To Security Concerns And The Availability Of Alternative Methods For Extending Browser Functionality, Such As Browser Extensions And Add-ons.
In Security, BHO Stands For "Browser Helper Object", Which Is A Type Of Plug-in Or Extension That Can Be Installed In Web Browsers, Such As Internet Explorer. BHOs Can Be Used To Add Additional Functionality Or Modify The Behavior Of The Browser, But They Can Also Be Used For Malicious Purposes, Such As Collecting User Data Or Injecting Unwanted Ads.
BHOs Can Pose A Security Risk Because They Can Access And Modify The Browser's Internal Data Structures, Which Can Include Sensitive Information Such As Login Credentials, Browsing History, And Personal Information. Malicious BHOs Can Also Inject Unwanted Ads, Redirect Users To Malicious Websites, Or Perform Other Unauthorized Actions.
To Mitigate The Risks Associated With BHOs, Some Security Experts Recommend Avoiding Their Use Altogether Or Being Cautious When Installing Them. Users Should Only Install BHOs From Trusted Sources, And Should Review The Permissions And Capabilities Of Each BHO Before Installing It. Additionally, Users Can Use Anti-malware Software That Can Detect And Remove Malicious BHOs.
Browser Helper Objects (BHOs) Are Implemented As Dynamic Link Libraries (DLLs) That Must Be Registered With The Windows Operating System. Here Are The Steps Involved In Implementing A BHO:
Once The BHO Is Registered, Internet Explorer Will Automatically Load It When It Is Launched. The BHO Will Be Loaded Into The Same Process As IE, Which Allows It To Access And Modify The Browser's Internal Data Structures. The BHO Can Then Interact With The Browser, Collect Data, And Modify Its Behavior As Needed.
It Is Important To Note That The Use Of BHOs Can Pose A Security Risk If They Are Not Implemented Properly Or Are Used For Malicious Purposes. Users Should Exercise Caution When Installing And Using BHOs And Should Only Install Them From Trusted Sources. Additionally, Users Can Use Anti-malware Software That Can Detect And Remove Malicious BHOs.
Here Are Some Tips To Help Protect Your Computer And Your Browser From Malicious Browser Helper Objects (BHOs):
Keep Your Operating System And Browser Up-to-date With The Latest Security Patches And Updates. This Will Help Protect Against Known Vulnerabilities That Can Be Exploited By BHOs.
Be Cautious When Installing New Software Or Browser Extensions. Only Install Software Or Extensions From Trusted Sources And Read Reviews To Ensure They Are Legitimate.
Use Anti-malware Software That Can Detect And Remove BHOs, Such As Antivirus Software Or Anti-malware Tools.
Configure Your Browser To Prompt You Before Installing Any New Browser Extensions Or Add-ons. This Can Help Prevent Malicious BHOs From Being Installed Without Your Knowledge.
Use A Browser With Built-in Security Features That Can Help Protect Against Malicious BHOs. For Example, Google Chrome And Microsoft Edge Both Have Built-in Security Features That Can Detect And Block Malicious Extensions And Add-ons.
Be Aware Of The Permissions And Capabilities Of Any BHOs You Install. Avoid BHOs That Require Excessive Permissions Or That Request Access To Sensitive Data.
Regularly Scan Your Computer For Malware And Remove Any Suspicious Files Or Programs.
By Following These Steps, You Can Help Protect Your Computer And Your Browser From Malicious Browser Helper Objects.
No, It Is Not Compulsory To Use Browser Helper Objects (BHOs) In Any Web Browser. BHOs Are A Type Of Browser Extension That Can Be Used To Add New Features Or Modify The Behavior Of The Browser, But They Are Not Necessary For Browsing The Web.
While Some Users May Find BHOs Useful, Others May Not Need Or Want To Use Them. Additionally, The Use Of BHOs Can Pose Security Risks If They Are Not Implemented Properly Or Are Used For Malicious Purposes. Therefore, It Is Important To Use Caution When Installing And Using BHOs, And To Only Install Them From Trusted Sources.
Most Modern Web Browsers Provide Other Ways To Extend Their Functionality, Such As Through Browser Extensions, Add-ons, Or Plug-ins. These Alternative Methods Can Offer Similar Functionality To BHOs, But May Be More Secure Or Easier To Use.
Browser Helper Objects (BHOs) Were First Introduced By Microsoft In 1997 As A Way To Extend The Functionality Of Their Internet Explorer Web Browser. BHOs Are Essentially COM (Component Object Model) Objects That Are Loaded Into The Browser's Address Space And Can Interact With The Browser And Other COM Objects To Provide Additional Features Or Modify The Behavior Of The Browser.
BHOs Were Designed To Be Used By Developers To Add Features Such As Toolbars, Pop-up Blockers, Or Ad Blockers To Internet Explorer. However, They Quickly Became Popular Among Third-party Developers, Who Used BHOs To Develop Various Types Of Browser Extensions, Including Adware And Spyware.
The Use Of BHOs For Malicious Purposes Led To Growing Concerns About Their Security And Privacy Implications. In Response, Microsoft Introduced New Security Features In Internet Explorer, Such As A Warning Prompt For BHO Installation And Tighter Restrictions On The Permissions And Capabilities Of BHOs.
Over Time, The Popularity Of BHOs Declined As Web Browsers Evolved And Alternative Methods For Extending Browser Functionality Became Available, Such As Browser Extensions, Add-ons, And Plug-ins. However, BHOs Are Still Supported By Some Legacy Versions Of Internet Explorer And Can Still Be Found In Some Software Applications That Rely On Internet Explorer's Rendering Engine.
Definition Of Browser Helper Object, What Is BHO,