 Blog's Page
Blog's Page
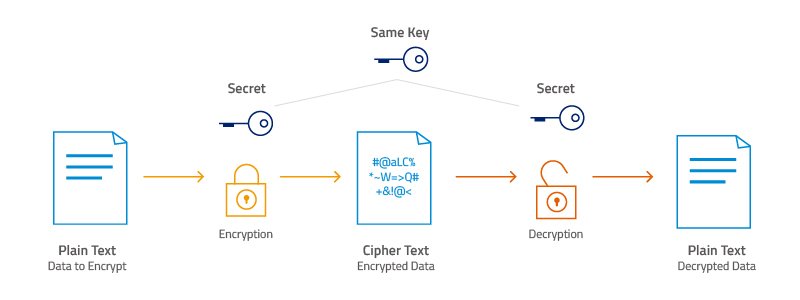
AES-256 Is A Symmetric Encryption Algorithm That Is Widely Used For Secure Data Encryption. AES Stands For Advanced Encryption Standard And It Was Developed By The U.S. National Institute Of Standards And Technology (NIST) As A Replacement For The Previously Used Data Encryption Standard (DES).
In AES Encryption, The Same Secret Key Is Used For Both Encryption And Decryption Of Data. AES-256 Refers To The Key Length, Which Is 256 Bits Long, Making It One Of The Strongest Encryption Algorithms Available. AES-256 Provides A High Level Of Security By Using Complex Mathematical Operations To Encrypt And Decrypt Data. It Is Used In A Variety Of Applications, Including Secure Communication, Data Storage, And Online Transactions.
The AES-256 Encryption Algorithm Is Fast, Efficient, And Widely Trusted, Making It A Popular Choice For Securing Sensitive Data In Many Industries, Including Government, Finance, And Healthcare.
Here Are Some Of The Features Of AES-256 Cryptography:
Key Length: AES-256 Uses A 256-bit Key Length, Which Provides A High Level Of Security By Making Brute-force Attacks Computationally Infeasible.
Symmetric Encryption: AES-256 Uses The Same Key For Encryption And Decryption, Making It Easier To Manage Than Asymmetric Encryption Algorithms.
Block Cipher: AES-256 Operates On Fixed-size Blocks Of Data (128 Bits) And Uses A Substitution-permutation Network (SPN) Structure To Encrypt Each Block.
Widely Adopted: AES-256 Has Been Adopted As A Standard Encryption Algorithm By Many Organizations And Industries, Including The U.S. Government, Financial Institutions, And Healthcare Providers.
Efficient Implementation: AES-256 Can Be Implemented In Hardware Or Software And Is Designed To Be Fast And Efficient, Making It Suitable For Use In A Variety Of Applications, Including Real-time Communication.
Secure: AES-256 Has Been Thoroughly Analyzed And Tested By The Cryptography Community, And No Significant Vulnerabilities Have Been Found.
Adaptive: AES-256 Can Be Easily Adapted To Changing Security Requirements By Simply Increasing The Key Length.
AES-256 Cryptography Works By Transforming Plaintext Into Ciphertext Using A Secret Key. The Process Of Encryption And Decryption Is Performed Using A Series Of Mathematical Operations, Including Substitution And Permutation, On Fixed-size Blocks Of Data (128 Bits).
Here's A High-level Overview Of How AES-256 Cryptography Works:
Key Generation: A Secret Key Is Generated, Which Will Be Used For Both Encryption And Decryption. The Key Length For AES-256 Is 256 Bits.
Initialization: The Plaintext Is Divided Into Fixed-size Blocks Of 128 Bits.
Key Expansion: The Secret Key Is Expanded Into A Larger Key Schedule To Be Used In The Encryption Process.
Encryption: The Encryption Process Involves Several Rounds Of Substitution And Permutation Operations Using The Expanded Key. Each Round Transforms The Plaintext Into Ciphertext, Making It More Difficult For An Attacker To Uncover The Original Data.
Decryption: The Decryption Process Is The Reverse Of The Encryption Process, And Involves Several Rounds Of Substitution And Permutation Operations Using The Expanded Key. The Resulting Plaintext Is Identical To The Original Input.
AES-256 Cryptography Provides A High Level Of Security By Using Complex Mathematical Operations To Encrypt And Decrypt Data. The Use Of A Fixed-size Block Of 128 Bits And A 256-bit Key Length Makes It Difficult For An Attacker To Break The Encryption, Even With Advanced Methods Such As Brute-force Attacks.
Here Is A Disadvantage Of AES-256 Cryptography:
Key Management: One Of The Disadvantages Of AES-256 Cryptography Is The Difficulty Of Managing The Secret Key. Since AES-256 Uses Symmetric Encryption, Both The Sender And The Recipient Must Have The Same Secret Key, Making Key Distribution And Management A Critical Aspect Of Its Implementation.
Performance: AES-256 Can Be Computationally Intensive, Making It Less Suitable For Resource-constrained Devices Such As Smartphones Or Internet Of Things (IoT) Devices.
Limited Use For Digital Signatures: AES-256 Is A Symmetric Encryption Algorithm, Which Means It Cannot Be Used For Digital Signatures. Asymmetric Encryption Algorithms Such As RSA Or Elliptic Curve Digital Signature Algorithm (ECDSA) Must Be Used Instead.
Vulnerable To Side Channel Attacks: AES-256, Like All Encryption Algorithms, Is Vulnerable To Side Channel Attacks, Where An Attacker Attempts To Extract Information From The Implementation, Such As Power Consumption Or Electromagnetic Radiation.
While These Disadvantages Exist, AES-256 Remains A Widely Used And Trusted Encryption Algorithm Due To Its High Level Of Security And Wide Range Of Applications. It Is Important To Carefully Consider The Specific Requirements Of An Application Before Choosing An Encryption Algorithm, And To Implement AES-256 Or Any Encryption Algorithm Securely And Properly.
AES-256 Cryptography, Describe AES-256 Cryptograph| Links1 | Links2 | Links3 | Products | Social Links |
|---|---|---|---|---|
| Home | Blog | Sitemap | Email Checker Tool | |
| About | CSI Links | ISRO Project Code: AA0802 | Offers | |
| Disclaimer | Gallery | Contact Us | Antivirus | |
| Privacy Policy | Software Downloads |