 Blog's Page
Blog's Page

The Invisible Empire Ransomware Is A Ransomware Trojan Currently Circulating On The Dark Web. It Represents A Recent Iteration Of The Jigsaw Ransomware, A Threat That Emerged Just A Few Weeks Prior. Remarkably, There Are Minimal Distinctions Between The Invisible Empire Ransomware And Its Predecessor, Including A Flaw In The Original Code.
Invisible Empire Ransomware Flaw Enabled PC Security Researchers To Develop A Decryption Utility, Aiding Victims Of This Threat. Fortunately, The Same Decryption Utility Designed For Recovering From The Jigsaw Ransomware Infection Can Also Be Applied To Counter The Effects Of The Invisible Empire Ransomware.
The Invisible Empire Ransomware Adopts An Invisible Empire Theme In Both Its Lock Screen And Ransom Note, Inspired By An Art Installation By Juha Arvid Helminen. Invisible Empire Ransomware Installation Highlights How Uniforms Can Conceal Individuals, Even When Engaged In Atrocities Or Crimes. Invisible Empire Ransomware Infection Follows The Typical Ransomware Attack Pattern, Utilizing AES Encryption To Encrypt The Victim's Files.
After Encryption, The Invisible Empire Ransomware Issues A Ransom Demand Through Files Dropped On The Victim's Computer And A Wallpaper Image. Payment Is Requested In BitCoins, With The Ransom Note Providing A BitCoin Address And An Interface Where Victims Can Confirm Their Payment By Clicking On 'I Made A Payment' To Obtain The Decryption Key.
Caution Is Advised, As The Invisible Empire Ransomware Is Programmed To Delete Files Upon System Restart Or When An Embedded Timer Reaches Zero, Similar To The Jigsaw Ransomware Attack That Progressively Deletes Data As The Timer Counts Down.
Notably, PC Security Analysts Have Identified Only One Visible Discrepancy Between The Invisible Empire Ransomware And The Jigsaw Ransomware Attack— The Former Uses The Extension '.payransom' To Designate Encrypted Files. Otherwise, The Invisible Empire Ransomware Remains Identical To Its Precursor.
While It Is Theoretically Possible To Decrypt Files Affected By The Invisible Empire Ransomware, The Practicality Of Such Recovery Is Limited In Most Cases. Decryption Is Achievable In This Instance Due To An Existing Flaw In The Ransomware's Programming, A Flaw That, As Of Yet, Remains Unaddressed But May Be Rectified In Subsequent Versions Of The Attack.
Given The Uncertainty Of File Recovery, The Most Effective Approach To Counter Threats Like The Invisible Empire Ransomware Is Through Preventive Measures. Employing A Fully Updated Anti-malware Program Serves As A Crucial Defense Against Potential Attacks.
Adhering To Fundamental Online Safety Practices Is Equally Vital To Mitigate Exposure To The Invisible Empire Ransomware And Other Similar Threats. Additionally, PC Security Researchers Strongly Recommend Regular File Backups On External Memory Devices Or Cloud Storage. Even The Most Comprehensive Backup Solutions Are Considerably More Affordable Than The Ransom Amounts Demanded By These Threats.
This Black Friday VPN Deals 2023, Fortify Your Online Security With Exclusive VPN Deals! Unlock Discounts On Top-tier Services, Ensuring Private And Unrestricted Internet Access. Black Friday VPN Deals 2023, Browse Anonymously, Safeguard Sensitive Data, And Enjoy Seamless Streaming With Lightning-fast Speeds. Don't Miss Out On These Limited-time Offers—invest In Your Digital Privacy This Black Friday VPN Deals 2023 And Enjoy A Safer Online Experience. Read More...
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
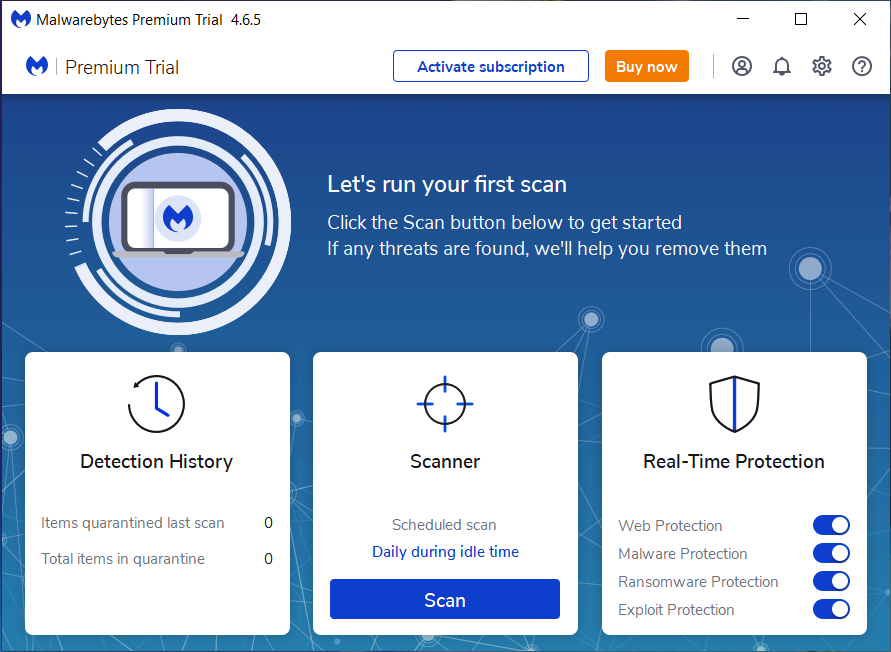
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:




If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
Invisible Empire Ransomware, Remove Invisible Empire Ransomware, Uninstall Invisible Empire Ransomware, Invisible Empire Ransomware Removal, Delete In