 Blog's Page
Blog's Page
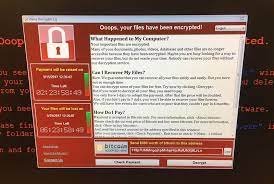
The Globe3 Ransomware Belongs To The Globe Ransomware Family And Draws Inspiration From The Popular Movie 'The Purge.' This Variant Employs A Ransom Note And Desktop Picture Themed After The Movie, Appending The Extension '.purge' To Each Affected File During The Attack.
Functioning As A Typical Encryption Ransomware Variant, The Globe3 Ransomware Encrypts Victims' Files Using A Robust Encryption Method. Subsequently, It Presents A Ransom Note Demanding A Substantial Payment In Exchange For The Decryption Key Required To Restore The Affected Files. Fortunately, PC Security Analysts Have Developed A Decryption Utility That Facilitates The Recovery Of Files After A Globe3 Ransomware Infection.
The Globe3 Ransomware Is Likely Propagated Through Spam Email Attachments. Upon Infecting A Computer, It Initiates A Check To Ensure It Is Not Operating Within A Virtual Machine Or Sandbox Environment Typically Utilized By PC Security Researchers For Controlled Threat Testing.
Once Confirmed To Be In A Non-sandbox Operating System, The Globe3 Ransomware Commences Its Assault By Encrypting Files On Local Drives, Shared Network Folders, And External Memory Devices Connected To The Compromised Computer.
Targeting Nearly A Thousand File Types, It Scans For Files Matching A Predefined List Of Extensions In Its Configuration Settings, Encrypting Them Using Blowfish Encryption. Post-encryption, The Globe3 Ransomware Appends The Extension '.purge' To The End Of The File Names, Facilitating Identification Of The Affected Files.
The Globe3 Ransomware Issues Its Ransom Note Through An HTA File Named 'How To Restore Files.hta,' Strategically Placed In Numerous Directories Where Encryption Has Occurred. To Ensure Automatic Execution Upon Windows Startup, The Globe3 Ransomware Modifies The Settings On The Affected Computer. The Ransom Note, Featuring An ID For The Infected Computer And The Creator's Email Address, Is Incorporated Into This HTA File.
Below Is The Full Text Of The Globe3 Ransomware Ransom Note:
'Your Files Are Encrypted!
Your Personal ID
{{IDENTIFIER}}
Your Documents, Photos, Databases, Save Games And Other Important Data Has Been Encrypted.
Data Recovery Is Required Interpreter.
To Get The Interpreter Should Pay Its Costs: 3 Bitcoin (3 BTC).
Cash Must Be Translated Into Bitcoin-purse: 18XXV3h9zzzJ1R4v6DiGmfgcooG1Vk9B1m
If You Have No Bitcoin
Create A Wallet Bitcoin: Https://blockchain.info/ru/wallet/new
Get Cryptocurrency Bitcoin:
https://localbitcoins.com/ru/buy_bitcoins (Visa/MasterCard, QIWI Visa Wallet \xE8 \xE4\xF0.)
https://ru.bitcoin.it/wiki/\xCF\xF0\xE8\xEE\xE1\xF0\xE5\xF2\xE5\xED\xE8\xE5_\xE1\xE8\xF2\xEA\xEE\xE9\xED\xEE\xE2(instruction For Beginners)
Send 3 BTC Bitcoin Address 18XXV3h9zzzJ1R4v6DiGmfgcooG1Vk9B1m
After The Payment, Send An E-mail Address Decrypt2017@india.com. In A Letter To Indicate Your Personal Identifier.
In A Response Letter You Will Receive A Program To Decrypt.
After Start-interpreter Program, All Your Files Will Be Restored.
Attention!
Do Not Attempt To Remove The Program Or Run The Anti-virus Tools
Attempts To Self-decrypting Files Will Result In The Loss Of Your Data
Decoders Are Not Compatible With Other Users Of Your Data Because Each User's Unique Encryption Key.'
Interestingly, The Globe3 Ransomware Comes With A Debug Mode, Which Has Proven Beneficial For PC Security Analysts In Comprehending Its Operations. Leveraging This Insight, Analysts Have Developed A Decryption Utility To Assist Users Affected By The Globe3 Ransomware.
This Decryptor Has Been Verified For Compatibility With Globe3 Ransomware Variants Utilizing The Extensions .decrypt2017 And .hnumkhotep To Identify Encrypted Files. While It Is Highly Probable That The Decryption Utility May Also Work With Other Globe3 Ransomware Variants, PC Security Analysts Emphasize The Importance Of Maintaining Backups For All Files.
This Proactive Measure Helps Mitigate The Potential Impact Of Future Ransomware Attacks, Particularly Those Lacking An Available Decryption Utility.
This Black Friday VPN Deals 2023, Fortify Your Online Security With Exclusive VPN Deals! Unlock Discounts On Top-tier Services, Ensuring Private And Unrestricted Internet Access. Black Friday VPN Deals 2023, Browse Anonymously, Safeguard Sensitive Data, And Enjoy Seamless Streaming With Lightning-fast Speeds. Don't Miss Out On These Limited-time Offers—invest In Your Digital Privacy This Black Friday VPN Deals 2023 And Enjoy A Safer Online Experience. Read More...
Removing Malware From A Windows Computer Involves A Combination Of Using Antivirus Or Anti-malware Tools, Performing System Scans, And Taking Manual Actions To Eliminate The Malicious Software. Here's A Step-by-step Guide:
Ctrl + Shift + Esc To Open Task Manager.Win + R To Open The Run Dialog, Type cleanmgr, And Press Enter.Remember To Maintain Good Security Practices, Such As Keeping Your Operating System And Software Up-to-date, Using A Reputable Antivirus Program, And Being Cautious When Clicking On Links Or Downloading Files From The Internet. Regularly Backing Up Your Important Data Is Also Crucial To Mitigate The Impact Of Potential Infections.
If You Have Malwarebytes Installed On Your Computer And It Has Detected Malware, Follow These Steps To Remove The Malware:
Open Malwarebytes:
Update Malwarebytes:
Run A Threat Scan:
Review Scan Results:
Quarantine Or Remove Threats:
Reboot Your Computer:
Check For Persistence:
Monitor For Issues:
Clear Browser Data:
Reset Browser Settings:
Review Installed Programs:
Change Passwords:
Update Operating System:




If The Malware Persists Or If You Encounter Difficulties During The Removal Process, You May Want To Seek Assistance From The Malwarebytes Support Community Or Consider Running Additional Scans Using Other Reputable Antivirus Or Anti-malware Tools. Remember To Keep Your Security Software Updated And Practice Safe Computing Habits To Minimize The Risk Of Future Infections.
Malwarebytes Is A Leading Cybersecurity Solution Dedicated To Protecting Users From The Ever-evolving Landscape Of Digital Threats. With A Proven Track Record In Malware Detection And Removal, Malwarebytes Offers Cutting-edge Technology To Safeguard Computers And Devices Against Viruses, Ransomware, And Other Malicious Software.
Boasting A User-friendly Interface, Malwarebytes Provides A Seamless Experience For Both Novice And Advanced Users. Its Real-time Protection Capabilities, Coupled With Powerful Scanning Algorithms, Ensure That Users Are Shielded From The Latest Cybersecurity Threats. Malwarebytes Continually Updates Its Extensive Malware Database, Enabling Users To Stay Ahead Of Emerging Risks And Vulnerabilities.
Beyond malware Detection, Malwarebytes Offers Additional Features Such As Web Protection And Anti-exploit Technology, Fortifying Defenses Against Malicious Websites And Zero-day Exploits. The Software's Lightweight Footprint Ensures Minimal Impact On System Performance, Delivering Robust Security Without Compromising Speed.
Whether Used As A Standalone Solution Or In Conjunction With Other Cybersecurity Tools, Malwarebytes Remains A Trusted Ally In The Battle Against Cyber Threats. As A Proactive And Responsive Cybersecurity Partner, Malwarebytes Empowers Users To Navigate The Digital World With Confidence, Knowing That Their Data And Devices Are Safeguarded Against The Latest And Most Sophisticated Threats.
Globe3 Ransomware, Remove Globe3 Ransomware, Globe3 Ransomware Removal, Uninstall Globe3 Ransomware, Delete Globe3 Ransomware